Cybercriminals don’t clock out at 5 p.m.
So why should your intel?
SpyCloud just flipped the script: instead of uploading new, recaptured data once a day, we’re now delivering it continuously. Nonstop. We recapture it, you get it.
This isn’t just faster – it’s a new tempo in how we deliver real-time identity intelligence. When attackers can weaponize stolen credentials and malware logs in hours, “daily” is basically ancient history.
What’s New (and Why It’s Awesome)
Threat actors act quickly, often within hours of gaining access to credentials or exfiltrated browser data. To match that pace, we’ve set new performance standards:
- Third-party breach and phishing datasets will now be processed and delivered within two hours of collection, and
- Malware data will hit our console and APIs in under an hour from when we get it - often, in seconds.
This acceleration translates into:
Fresh intel in real time
No waiting for tomorrow’s update. The second something hits, it’s visible.
Malware intel with teeth
We’ve ditched record-only deduplication and gone event-based. Every infection event is captured, so you see the full story.
Sharper context
Exact timestamps, “in-flight” breach status, and additional malware assets supported.
Speed + fidelity
We’re using AI and nearly a decade of human expertise to crank up the pipeline without compromising accuracy.
Precision Timestamps: Down to the Second
One of the biggest behind-the-scenes changes is how we handle publishing timing. Instead of vague, day-only stamps, every record now carries an exact collection timestamp. That means when you see an exposure, you know the precise moment it was published into SpyCloud’s pipeline. No rounding, no guesswork. This level of granularity unlocks cleaner investigations, tighter incident timelines, and smarter correlation across tools – because in security, timing is everything.
Why “Duplicate” Malware Records Aren’t Always Duplicates
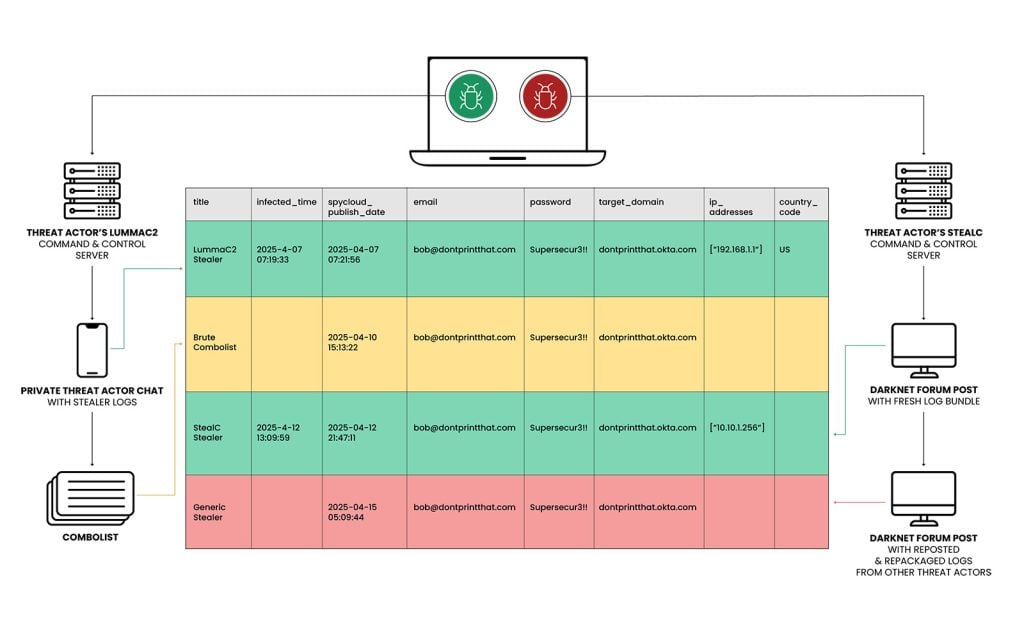
To help understand why event-based deduplication is so critical, let’s walk through a simplified (and unfortunate) story about Bob, a fictional employee at a company called DontPrintThat. Bob unknowingly downloads infected software twice, leading to multiple infostealer malware infections. Here’s how that plays out:
Infection Timeline
- Monday morning: Bob downloads what he thinks is a free photo editing tool. In reality, it’s infostealer malware (LummaC2). SpyCloud detects the infection almost immediately by monitoring the criminal’s data-sharing channel.
- Thursday afternoon: Another criminal buys the same stolen data and adds Bob’s credentials to a large list of stolen usernames and passwords – what’s commonly known as a combolist. SpyCloud detects and ingests this second copy of the same data, as reproduced by the second criminal.
- Friday afternoon: Still on the hunt for a photo app, Bob tries again – and gets infected a second time, this time by a different infostealer malware (StealC). The infection data is delayed, but SpyCloud picks it up the next day.
- Following Tuesday: A new criminal downloads that same infection log, removes key system info, and reposts it with their branding. SpyCloud collects this altered version, too.
What Does This Mean?
All four records captured Bob’s same login credentials – email, password, and company domain – but each one tells a different story:
- One shows the first infection of Bob’s computer from LummaC2.
- Another is a combolist reuse of that stolen data, showing the data is circulating in criminal communities.
- A third shows a second infection from a completely different malware.
- The fourth is a tampered version of the second infection.
The Bigger Picture
New research & insights from SpyCloud
Bad actors move fast. Now, defenders can move faster.
This pivotal update to SpyCloud’s capabilities marks a transformative shift, propelling us from a reactive posture of “knowing soon” to a proactive stance of knowing now. This change empowers security teams with an unparalleled proactive advantage, enabling them to mitigate critical exposures with unprecedented speed and efficiency.
Beyond the sheer acceleration of identity intelligence, this enhancement delivers significantly enriched clarity and context surrounding breached, malware-exfiltrated, and phished data. No longer are security professionals forced to contend with ambiguous or incomplete information. Instead, they gain a granular, in-depth view that precisely answers the critical questions of “who, what, when, and where”.
In a world where stolen identity data is rapidly and relentlessly leveraged for subsequent, more sophisticated attacks, the provision of immediate, actionable insights isn’t merely beneficial – it is absolutely crucial. This empowers organizations to move beyond mere detection and into swift, strategic remediation, minimizing the potential for damage and safeguarding their digital ecosystems from persistent and evolving threats.
Bottom Line
One Upgrade, All Solutions
This continuous delivery model isn’t limited to a single product – it spans every SpyCloud solution area: Enterprise Protection APIs, Consumer ATO Prevention APIs, and Investigations APIs & Modules. Whether you’re tracking employee malware infections, preventing consumer account takeovers, or diving deep into criminal infrastructure, the pipeline powering your data is now live and always-on. It’s the same foundation of recaptured intelligence, now supercharged across the board.
SpyCloud’s new continuous delivery is a leap forward in outsmarting cybercriminals:
Faster intel.
Smarter intel.
Always-on intel.