Imagine you’re actively tracking down adversaries trying to bypass your security measures and exploit compromised access within your network. How do you quickly identify enough information about the threat actor’s identity to take down an active threat and prevent future malicious activity?
Or, consider other types of risks that can be prevented, like an ex-employee, whether malicious or negligent, with active shadow IT access. Or a third-party vendor with privileged access who has been compromised due to a malware infection.
In each of these threat hunting or analysis scenarios, your teams need comprehensive answers, ideally faster than traditional OSINT or threat intelligence feeds provide.
SpyCloud Investigations puts the power in the hands of your analysts and investigators to get answers about threat actors faster. After all, having the right tools and techniques is what makes the difference in effective investigations.
About SpyCloud Investigations
Designed as a user-friendly, SaaS-based portal, SpyCloud Investigations unravels the complexity of cybercriminal threats to your organization. The tool gives analysts access to SpyCloud’s more than 600 billion recaptured data assets and powerful cybercrime analytics capabilities, which in turn provide the speed and depth that intel analysts need to shorten investigation timelines. SpyCloud specifically designed Investigations for analysts of all skill levels – no endpoint or advanced querying skills are required.

"SpyCloud is the best service in their industry and I really don't know why you would use another vendor or competitor."
– Manager, IT Security & Risk Management
Building a profile with cybercrime data for threat actor attribution
Let’s explore the threat actor scenario to showcase how SpyCloud Investigations unlocks value for analysts and investigators committed to safeguarding their organization and employee identities from cybercriminals.
Oftentimes, analysts have nothing more than a username or social handle to start tracking down a criminal actor, with scattered clues from the criminal underground. SpyCloud offers analysts extensive details with multiple paths to explore – even if you have just a single asset type to start with – unlocking the ability to conduct a comprehensive investigation.
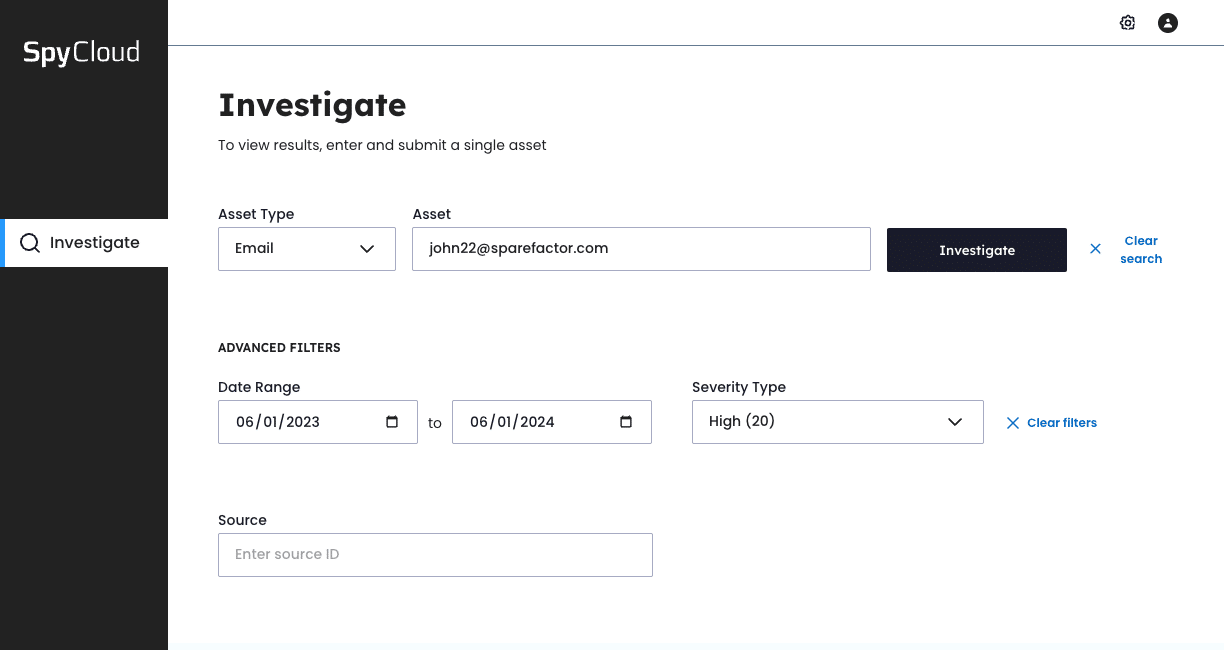
How do you profile and attribute threat actors when your team has differing experience levels and limited data at their disposal? SpyCloud makes it easy to start a number of different asset types.
Investigate using these data points, and more
Domain
Email addresses
Password (hashed)
Phone numbers
Infected machine ID
Social media handle
User name
SSN (hashed)
Drivers license numbers (hashed)
Understanding the full scope of an actor’s digital exhaust requires more than just isolated PII or scattered records. With your first search, you’re able to see how much SpyCloud knows about the potential threat to start building a profile and attribute the actor’s identity.
Querying a single email or social handle often returns multiple asset types, each with a count of the most represented assets within SpyCloud’s database. To focus on the most relevant and insightful records, SpyCloud makes it easy to filter down to the appropriate time range or severity.
From here your teams can interact with formatted tables which include domains, IPs, target paths, and other record types recaptured by SpyCloud.
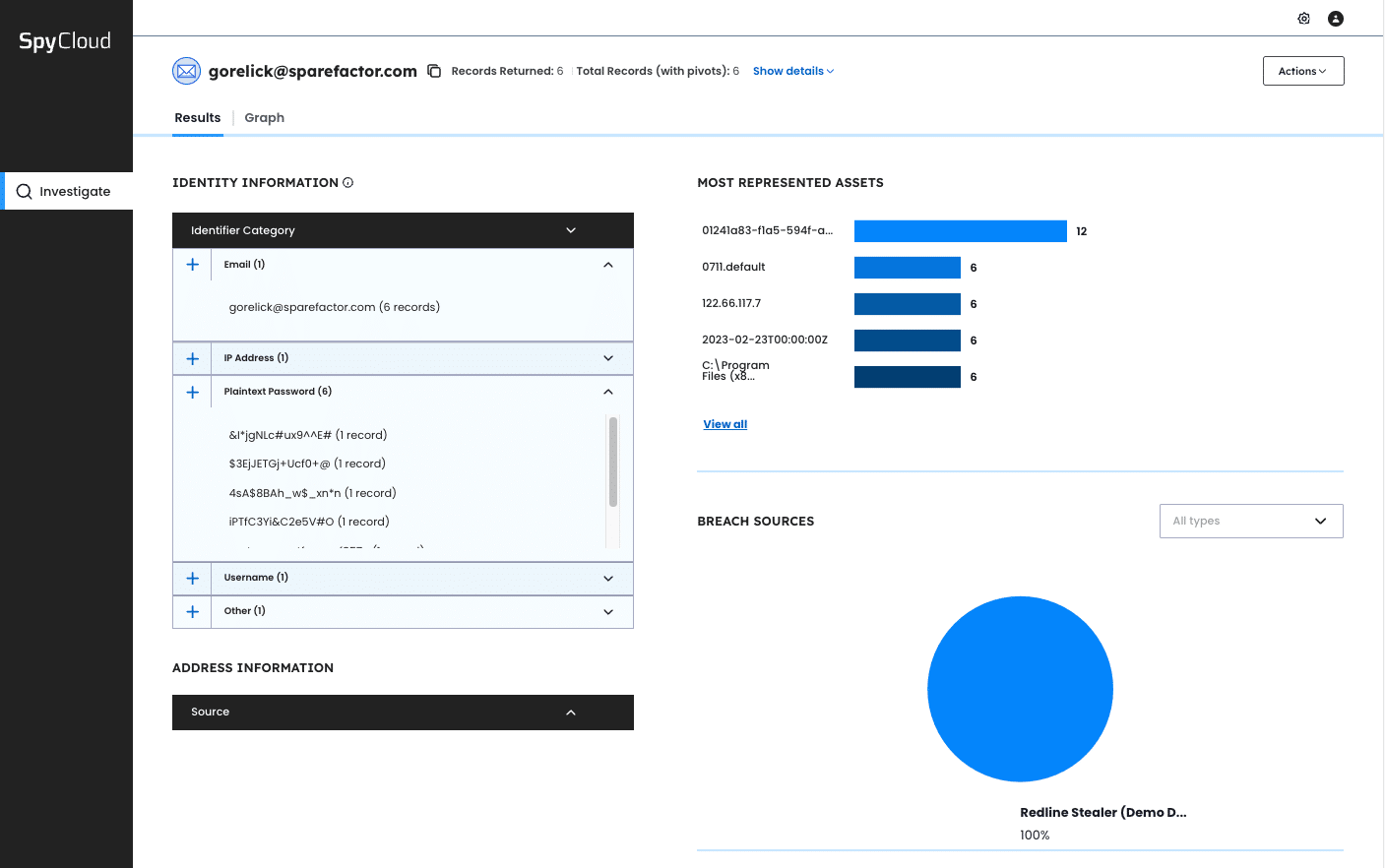
Curated identity intelligence for every query makes it easy to begin profiling the threat actor.
This first step of reviewing results within SpyCloud’s structured intelligence helps unravel clues and identify patterns. Are there repeating patterns in the naming structure of emails? Are there hidden identifiers within the PII that provide further insight? SpyCloud sets up your analysts to easily pivot off various data types and explore more related records.
Pivot with the link analysis graph to explore hidden records
Continuing with the threat actor example, SpyCloud can connect the string from one username to find more recaptured records and asset types, including some geolocation information and even an email associated with an actual name.
SpyCloud Investigations unlocks more pathways within an easy-to-use link analysis graph that supports pivoting to quickly build a larger picture of the search target with previously unknowable connections.
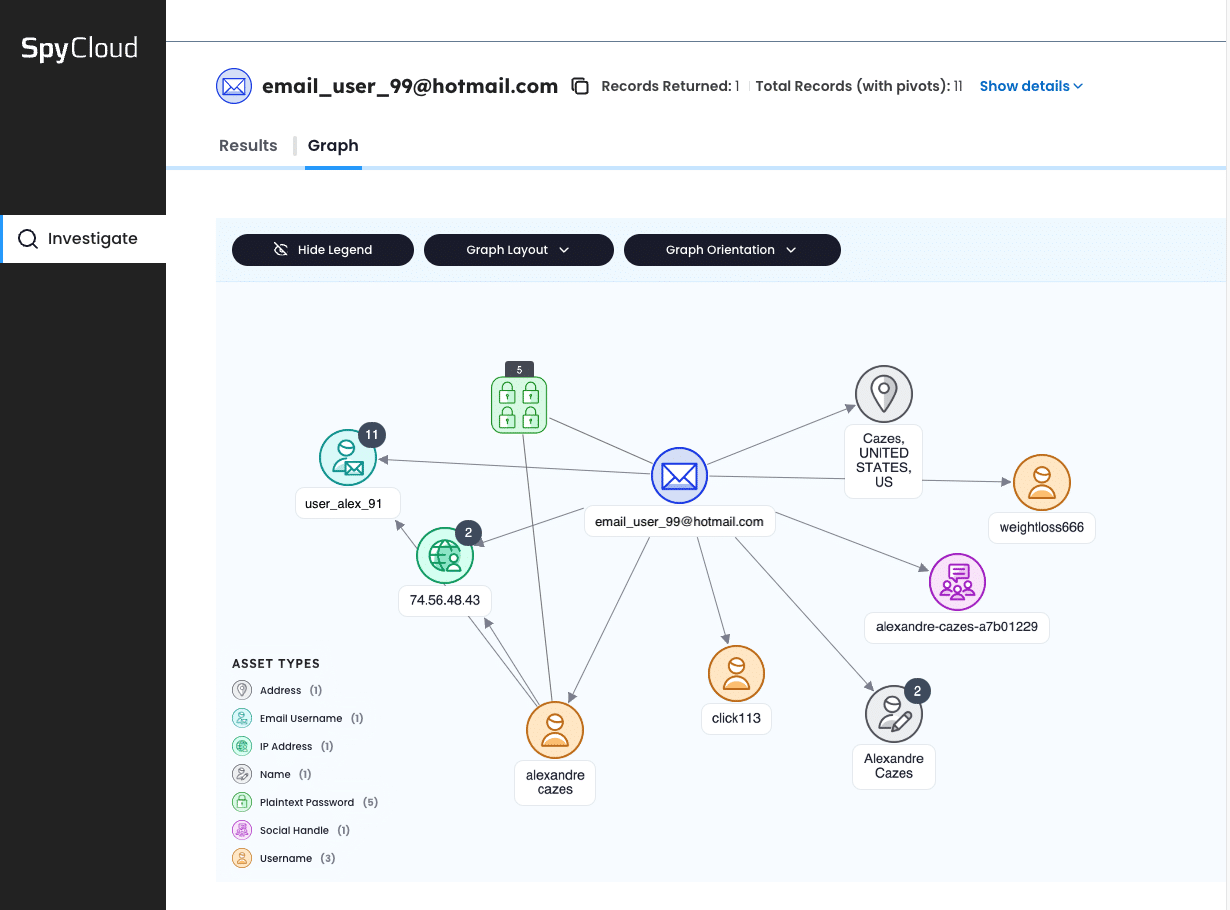
The SpyCloud Investigations graphing function visualizes the connections between different data points, such as linked emails, passwords, and physical locations.
Now when your analysts see a graphical node of 10+ recaptured passwords or 5+ usernames they have more clues to dive into the data.
You can pivot on almost every asset type to easily see relationships between entities and pull threads to understand connections, expanding the view of connected darknet records and identity information.
SpyCloud also supports fuzzy pivoting for common assets like passwords and email addresses that cybercriminals often use to create similar asset types (things that are often lost in the noise of raw OSINT data feeds). Expanding the records within each node or and changing the graph layout and orientation continues your profiling.
SPYCLOUD PRO TIP:
A great jumping-off point is to explore related passwords within the dataset. Unlike emails and usernames, the types, frequency, and patterns within passwords tell us a little bit more about a user. Because passwords, by their very nature, are not visible or shared, exploring the frequency of password phrases or combinations adds more connection points to the threat actor profile.
Connecting the cybercrime dots: Complete investigations to attribute threat actors
…and beyond
There are few limits to how your teams can use SpyCloud Investigations to identify, detect, prevent, investigate, and respond to high-pressing cybercrime threats and risks. Searching, pivoting, and graphing to enrich a threat profile is just one workflow. It doesn’t stop there – teams can protect their enterprise and analyze exposed access and credentials from hidden malware infections, investigate financial crimes using stolen data, or improve supply-chain relationships by evaluating risky vendor security practices.See SpyCloud Investigations in action
SpyCloud Investigations acts as a force multiplier for your analysts, opening up new angles for investigations and ways to pinpoint connections that help you pull the string forward. Unlimited querying within the SaaS portal unblocks your team to optimize your response and improve your success. Get pricing or watch the demo below to learn more.
Watch a demo
See what’s possible with SpyCloud Investigations.



