SOLUTIONS
Enterprise Protection
from Identity-Based Attacks
Every user connected to your business – from employees to contractors to third parties – represents an entry point for cybercriminals. SpyCloud Enterprise Protection closes identity exposure gaps before attackers can exploit them in ATO, session hijacking, and ransomware attacks.
Automated enterprise identity threat protection for overburdened defenders
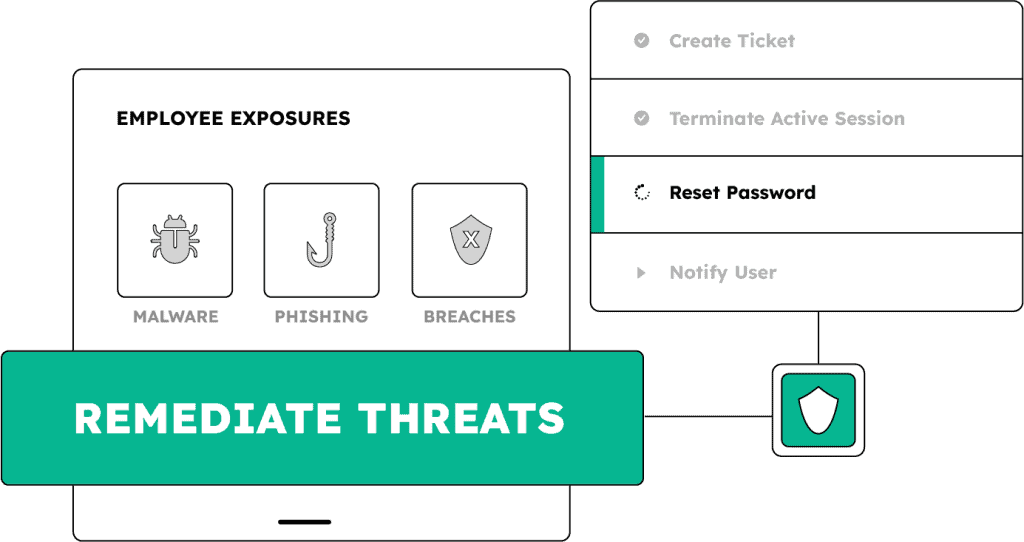
Continuously monitor for identity exposures stemming from data breaches, malware infections, and phishing campaigns – using the industry’s most comprehensive recaptured data – and take action before bad actors strike.
Get early warning of risks stemming from employees’ holistic exposure history – including personal device infections and credential reuse – that could compromise access to your critical business systems.
Turn high-risk exposures into immediate remediation actions, cutting detection, investigation, and response time from weeks to minutes.
EXPLORE PRODUCTS
SpyCloud Enterprise Protection Products
Don’t just detect identity threats – dismantle them. SpyCloud surfaces exposed identity data across your workforce and automates remediation to block criminals from exploiting it.
Prevent session hijacking from compromised authentication cookies
Act on malware-exposed devices, users, and applications that can lead to ransomware
We don’t have to do any manual processing of breaches anymore, which took a lot of time with the constant stream of new breaches. SpyCloud allows us to automate the entire process.
EXPLORE WHO USES SPYCLOUD
Defenders
we help
SpyCloud is the trusted partner for security and identity teams who must protect employee identities to secure corporate access.
Security operations
Accelerate detection and remediation of identity threats using SpyCloud with your SIEM, SOAR, and EDR tools
Identity
Identify exposed credentials and password reuse – and remediate exposures within 5 minutes from discovery
Integrations
SpyCloud integrates with your existing security tools and workflows so you can accelerate incident response and shut down hidden entry points. Easily add SpyCloud as a plug-and-play option for identity threat protection with top security vendors: IdPs, EDRs, SOARs, SIEMs, and TIPs.






Next steps
Start remediating exposed identities in minutes with SpyCloud