Stolen credentials remain the No. 1 entry point used by malicious actors to gain access to secure networks and wreak havoc within organizations—and potentially up the supply chain.
Recent SpyCloud research shows that 4.5 million credentials for corporate accounts at the 95 largest companies in the Defense Industrial Base (DIB) are on the dark web and in the hands of cybercriminals. That staggering number doesn’t account for compromised credentials from hundreds of thousands of smaller businesses that contract with government agencies. Securing these companies in the defense supply chain from cyberattacks is critical to protecting controlled unclassified information that resides on industry systems and networks.
The U.S. Department of Defense (DoD) developed the Cybersecurity Maturity Model Certification, or CMMC, to “reinforce the importance of DIB cybersecurity for safeguarding the information that supports and enables our warfighters.” Eventually, all contractors and suppliers doing business with the DoD must meet a minimum level of requirements for a given security level and undergo a certification process based on review by an accredited assessment organization.
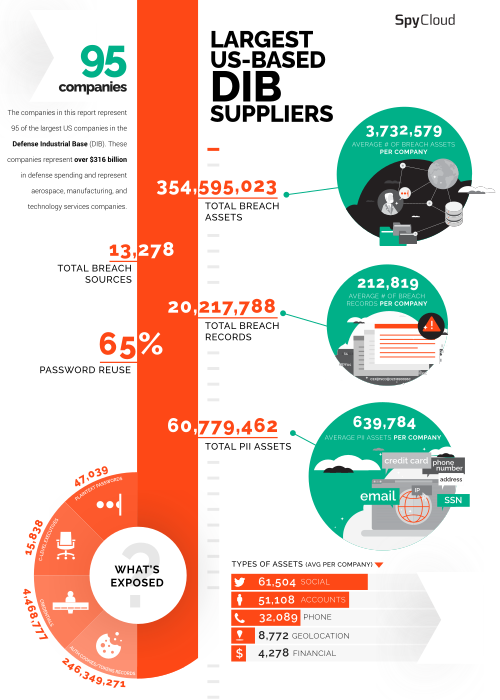
How much employee data from DIB suppliers is in criminal hands?
View our infographic.
Keeping up with Credentials: A Criminal's Direct Line into Your Network
A critical domain of the new certification standards is access control, requiring appropriate tools and processes be in place to prevent unauthorized individuals from accessing sensitive networks and company information. The Verizon 2022 Data Breach Investigations Report said that credentials are “one of the most tried-and-true methods to gain access to an organization for the past four years” and indicated an almost 30% increase in stolen credentials since 2017.
Corporate passwords, particularly for government contractors, should be strong given the assets they protect and organizations involved, but problems arise when employees reuse their company credentials for personal accounts. SpyCloud researchers found an average password reuse rate at the largest defense industrial base suppliers of 65% and almost 100,000 employees reusing passwords, putting these organizations at risk of account takeover attacks that can lead to follow-on ransomware attacks.
New breaches happen every day, and the spoils from these breaches will become available to anyone who wants to buy them. Password reuse is a gift to cybercriminals because once someone acquires exposed login credentials from one breach, they could use it to unlock more lucrative accounts.
Another concerning trend with DIB companies is the amount of malware-infected devices aligned to these domains: 27,748 employees at these companies are using machines with malware infections. Infostealer malware exfiltrates more than just credentials from a device – it siphons authentication information such as web session cookies that can be used to bypass multi-factor authentication and allow bad actors to gain unfettered access to a network. While stolen credentials are an easy access point into an organization, malware infections create an even easier point of entry because there is no guessing involved when credentials are stolen directly from a device.
Do you work with government agencies? Check your darknet exposure to protect your organization and the agencies you support from identity exposure that can lead to account takeover, ransomware, and online fraud.
To protect controlled unclassified information in industry systems and networks, defense contractors must take strong measures to continuously detect and remediate credential exposures due to data breaches and malware infections, both of which can lead to full-blown security incidents that have the potential to have significant impacts on national security. Implementing MFA and password managers just isn’t enough.
Tips to Reduce Risk and Help Achieve Certification Requirements
To truly prevent cyber threats that lead to ransomware attacks, organizations must stop criminals before they act. Here are three best practices suppliers can implement to meet CMMC requirements and manage risk within the government supply chain:

Enforce strong password policies.
One of the first things you can do to enhance your security posture is to enforce strong password policies that take into account human behavior. Ensure employees are using strong, complex 16+ character passwords that are unique for each account. And don’t mix business passwords with personal passwords. Be sure to check out our tips for strong passwords.

Implement Post-Infection Remediation to properly address exposures caused by malware infections.
Criminals continue to come up with creative ways to convince unsuspecting users to download and install credential-stealing malware. While antivirus and endpoint protection solutions can help detect infections on corporate systems, some malware strains can slip through the cracks, such as when an employee accesses corporate accounts on a malware-infected personal device.
Since malware can siphon credentials, browser data, system information, and files that may contain corporate data or sensitive information, simply removing the infection from a device doesn’t address the longer term effects resulting from stolen authentication data. Additional steps as part of Post-Infection Remediation must be taken to properly remediate malware infections, including identifying the full scope of the applications impacted by the malware infection, resetting stolen passwords, and invalidating compromised web sessions.
Download SpyCloud’s Post-Infection Remediation Guide for an in-depth look at our new, critical addition to malware infection response.

Continuously monitor your darknet exposure.
While criminals often use breach and malware data to access accounts, organizations can use that same information to protect themselves and their employees. To do so, we recommend continuously checking whether employee and customer data show up on underground marketplaces from third-party breaches or malware infections, so you can quickly secure your accounts and prevent criminals from monetizing the data at the cost of your business.
Cybercrime continues on an upward trajectory and government supply chains have become a lucrative target. The CMMC is a good start to encourage DoD suppliers to get security in proper shape, but regardless of regulation, every organization should strive to attain the highest level of protection possible.
Learn how SpyCloud Government Solutions use insights from the dark web that can enhance DIB cybersecurity.
Keep reading
Our Director of Federal, Douglas Lingenfelter, originally wrote this post in 2020 for NextGov. We updated it in April 2023.