If you’re at all familiar with our work and philosophy on cyber investigations, you know we feel that data without context is a dead end. Our team of investigators has experienced firsthand how important context is in order to execute investigations effectively to get where you’re trying to go. Miss this key element, and you’re set up for failure.
For years – just like many CTI, SOC, and fraud analysts – our in-house investigators have chased connections, run pivots, and stitched together indicators. Fortunately, they’ve had context to guide the way, thanks to their decades of experience combined with the power of SpyCloud Investigations. And still a lot of their investigative work has been manual and involved some driving in the dark.
But we knew there was a better way for every bleary-eyed analyst and investigator also pitted against the speed and scale of cybercriminal activity.
So what did we do? We used our expertise and reimagined our Investigations solution for you. We made something that:
- Is sophisticated enough that even the most seasoned investigators would want to use, but intuitive enough for any analyst to use
- Delivers AI-powered insights to you immediately, whenever you need them, day or night
- Is robust enough to tackle common use cases like identity resolution, attribution, and fraud schemes – as well as emerging threats like detecting state-sponsored malicious insiders like DPRK IT workers
For all these reasons, we’re so happy to share the story behind the new SpyCloud Investigations experience – now with AI Insights.
I certainly see the benefit…80% of the investigative legwork is done out-of-the-box with SpyCloud.
AI-powered intelligence: SpyCloud Investigations reimagined for speed and precision
SpyCloud Investigations is built to find hidden identity connections and correlate fragmented data from the criminal underground to surface answers for analysts. Since introducing IDLink analytics last year, and now with the addition of AI Insights and other enhancements, we’re making the tradecraft and thought process of a veteran investigator accessible to analysts of every experience level.
Our latest improvements give analysts a strategic leap forward in disrupting cybercrime while saving hours in the process, helping you turn data into clarity faster by way of three major new features:
- Robust Source Catalog: Grounds your investigation in contextual understanding, with details for the malware, phish, breach, and combolist records we publish daily
- Flexible Graphing: Visualizes complex identity relationships and patterns, with options for laying out, hiding, and grouping your findings with your preferred investigative style
- Fast AI Insights: Built on SpyCloud’s investigative methodologies, AI Insights analyzes and transforms exposure data into actionable intelligence within seconds, formatted for you in shareable summaries
Together, these enhancements turn sprawling underground identity data into finished intelligence your team can act on to get ahead of threats.
“SpyCloud Investigations with AI Insights meaningfully enhances our ability to detect, understand, and respond to dark web threats in real time. By combining speed, clarity, and depth of intelligence, it sets a new benchmark for how modern security teams should approach threat investigations. I see this as a major step forward in making our security operations more proactive, efficient, and impactful.”
Turn identity data in AI-driven intelligence for investigative clarity
Every investigation begins with a question – and to answer it, you need data you can trust at scale. And what we do best at SpyCloud is data.
We recapture exposed identity data from phishing campaigns, infostealer malware, combolists, and third-party breaches, now totaling over 800+ billion identity assets to tell the real size of compromise. With near-real-time updates to publish data within hours of discovery, your team can operate within the critical window of advantage to prevent attacks.
With direct access to the new Source Catalog, analysts can frame queries with rich, real-time exposure data.
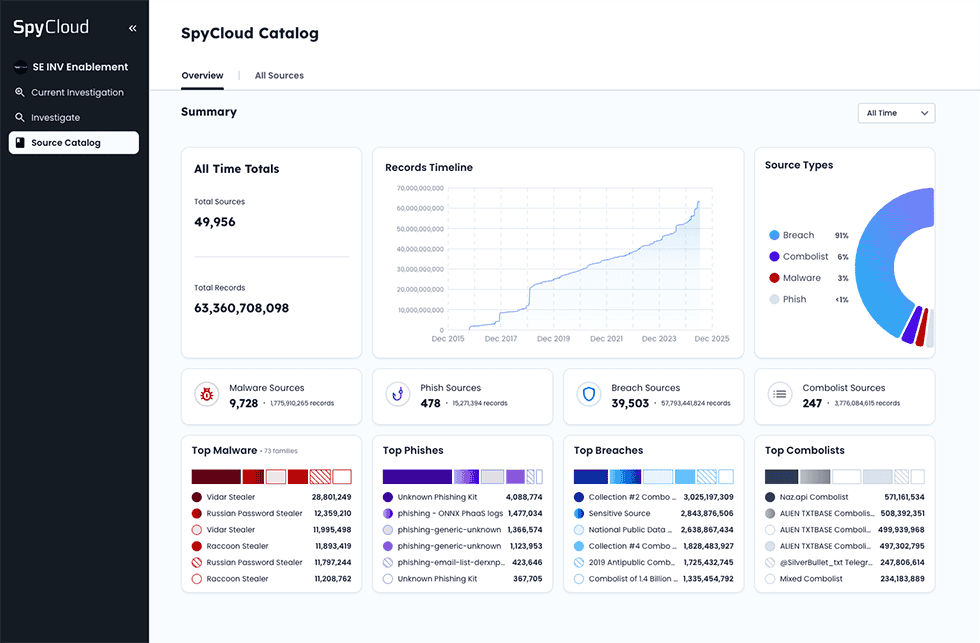
Explore the details of top malware families, large-scale breaches, recent phishing campaigns, and more that fuel your investigative queries.
Within the Source Catalog, you can browse the most recent recaptured records for:
- Quick Reference: Ingestion timing, record volume, and source origin to understand the freshness and scope of the data
- Asset Snapshot: Detailed breakdowns of notable identity assets exposed in each source – usernames, emails, cookies, and more – plus summaries of the underlying identity data
- Context Insights: Clear, digestible summaries that surface what matters most to frame your investigation
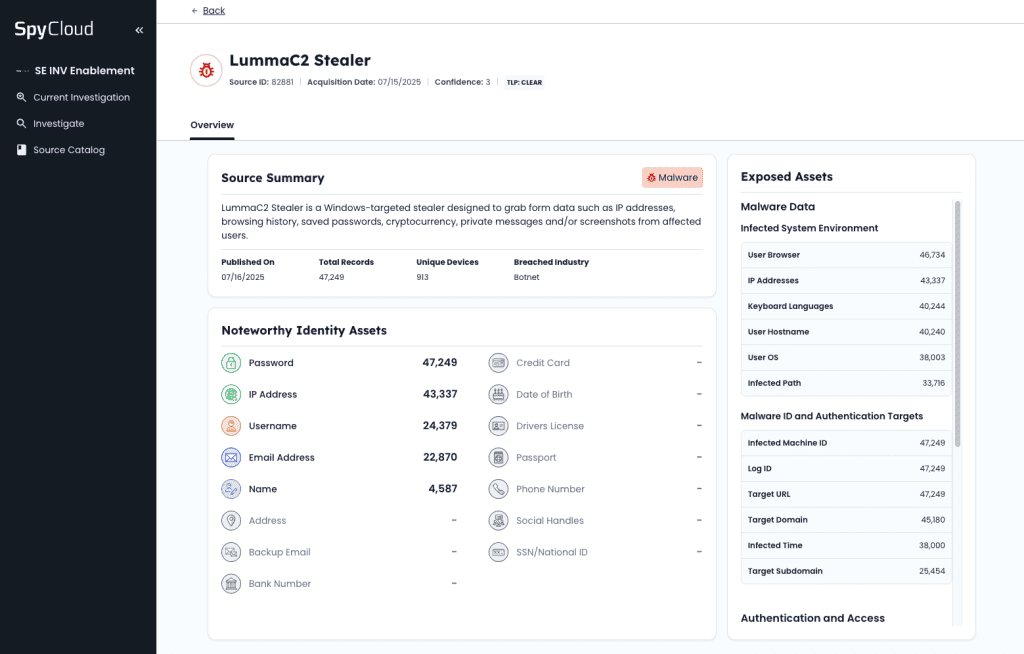
Explore details within each published source, like a recent set of exposed assets from a stealer infection, showing everything from the infection scale to which identity assets were compromised.
The Source Catalog becomes your starting point for understanding SpyCloud’s latest recaptured data, with context that grows richer over time. Once you’ve identified source details that advance your investigation, the next step is visualizing how that exposure connects across identities, infrastructure, and digital behavior.
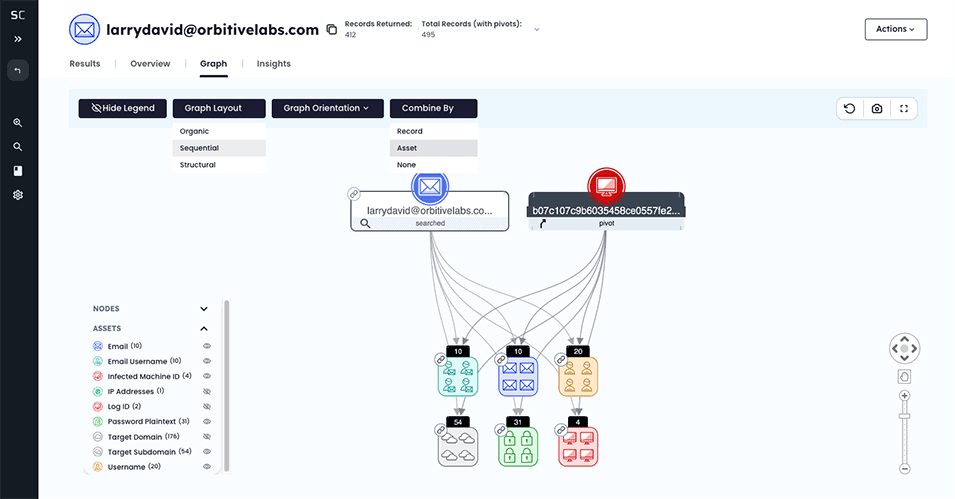
Visualize data relationships in new ways
Piecing together connections with exposed identity assets is where SpyCloud Investigations come to life. Our overhauled Graph View cuts through complexity by visualizing the relationships between exposed identity data points, helping you rapidly construct holistic digital identities reveal and uncover connections that would remain hidden.
Control how you want to visualize exposed assets for a given investigation. Filter out asset types that don’t help, change the layout, and trace your steps.
The Graph View makes it simple to focus on accelerating your investigation, giving you advanced controls with the layout of the data. Our team of investigators realized our customers needed more flexibility to find clues within large datasets, so now the graph offers multiple ways to arrange the data, including:
- Combine by Asset: Consolidate similar assets, like passwords, to remove noise and collapse repetitive data points (such as multiple credentials from the same infected device), revealing macro-patterns across large datasets
- Combine by None: Display every asset individually without grouping, letting you step back and expand the full scope for identity patterns across the entire dataset (like recurring aliases)
- Asset Filtering: Instead of grouping, selectively hide or show specific data types (like emails or usernames) that either advance your investigation or slow you down
The Graph View preserves the path of your investigation, so you can easily see where you started your investigation along with each pivot. This makes it easier to retrace your methodology across even the most complex identity investigations. The result? You can move from scattered data points into a coherent storyline for your research subject.
Automate investigative analysis using AI Insights for less time spent searching
From scattered data points to actionable intelligence – our new AI Insights feature reveals the threats hiding in plain sight. Having a view of the right data is critical, but analysts need more than just visibility. They need the ability to look for patterns and identity threats before it’s too late.
That’s where SpyCloud AI Insights comes in, spotting threats by identifying patterns in identity misuse that would slip past human analysis. Built on SpyCloud’s investigative tradecraft, it automates the final step of the investigation process and turns complex identity exposures into actionable summaries without requiring manual analysis.
With one click, users can tap into our decades of investigative expertise as AI Insights applies advanced logic and correlation to pinpoint the identities and highlight patterns across all the exposed assets in context. The output is a stakeholder-ready report, summarizing what’s been exposed into finished intelligence.
What would normally require hours of painstaking analysis from a senior investigator, SpyCloud’s AI Insights delivers in just a few seconds:
- Identities hiding in plain sight - comprehensive identity profiles discovered within the exposure data, detailed enough to know who’s who and understand enough details of their online activities
- Connected relationship webs - hidden connections between identities through shared aliases, emails, passwords, and other identity data that expose coordinated campaigns
- Patterns of digital behavior - notable patterns across emails, usernames, password habits, and that warn of insider risks and external threats before they mature
- Categorized digital activity – browser behavior summaries organized by domain type to quickly spot concerning engagement with crypto exchanges, underground forums, or other high-risk websites and communities
What makes this feature powerful isn’t just the speed – it’s the scope. Everything generated represents what an expert investigator would uncover with unlimited time, plus the ability to spot patterns across vast datasets that no human could easily process. SpyCloud’s AI Insights examines everything from your queries, recognizing the identities, the method of exposure, related infrastructure, and unique signatures and actions linked to insider threats. And with exportable, exec-friendly reports, you can move from investigation to action without additional steps.
“SpyCloud Investigations with AI Insights has cut our threat investigation times dramatically – from hours (or sometimes days) down to minutes. The efficiency gains are undeniable and have freed our analysts to concentrate on higher-value tasks.”
Get summarized findings in seconds with AI Insights
In seconds, AI Insights applies curated logic and correlation to identify the research subject, surfaces key exposures, organizes thoughts into clear patterns and sections, and builds a comprehensive report that would take hours to compile manually.
Built for analysts at every skill level
AI Insights, paired with the Source Catalog and revamped Graph View, are just some of what makes SpyCloud Investigations faster, more accessible, and more valuable for analysts than ever before. Whether you’re a Tier 1 analyst triaging alerts or a senior investigator tracking sophisticated threat actors, this new experience gives you the tools to get from alerts to intel with more confidence and in a fraction of the time.
So how does this translate into everyday workflows? Accessing the SaaS-based module is designed to serve every team responsible for defending your assets and preventing identity-based threats. It gives your CTI, SOC, Incident Response, Fraud & Risk, and Trust & Safety teams exposed identity data and AI-driven context to investigate with speed and precision:
- Cyber threat intel teams: Attribute adversaries and map digital identities across campaigns and infrastructure.
- SOC teams: Accelerate investigations and enrich security event analysis to pivot faster from detection to decisive action.
- Incident response teams: Understand the initial point-of-compromise and the associated impact to your enterprise faster with identity-focused analytics.
- Fraud & risk teams: Uncover compromised identities and stop fraud tied to hard-to-detect phishing and malware exposures.
- Trust & safety teams: Protect users and platforms by identifying identity abuse and account compromise early.
Threat actor attribution
Unmask who you’re up against by connecting threat actor monikers and aliases to their real identities using SpyCloud’s recaptured dataset and identity analytics
Insider threats
Reveal malicious and unwitting insiders early with AI Insights using behavioral context and exposed credentials. Even the quiet ones leave a trail
Hard-to-detect fraud & financial crimes
Detect signs of fraud faster by validating identities, discovering synthetic identities, and uncovering suspicious online activity and identity reuse across accounts
Supply chain exposures
Investigate third-party vendors or partners for compromised access from infostealer malware that could impact your organization with unauthorized access
Infected host identification
Quickly determine which devices were compromised by malware and what access to corporate applications remains open, for comprehensive post-infection remediation steps
Platform abuse
Prevent fake signups, bots, and abuse identifying individuals who operate multiple accounts or use synthetic identities for malicious activity
Pattern of life analysis
Understand how exposed identities behave over time – connecting all digital exhaust to build a full profile across campaigns
Know Your Customer (KYC)
Validate customer identity and risk – at onboarding and beyond – using recaptured data to detect impersonation, anomalies, and synthetic identities
Trust & safety escalations
Investigate and resolve escalations by identifying users operating multiple abusive accounts, revealing the identity behind problem accounts, and connecting abuse patterns to known exposure data
VIP exposures
Protect high-value targets with visibility into exposed credentials across personal and professional accounts and signs of underground activity
Identity resolution
Connect fragmented exposure data by linking every connected asset connected that makes up a digital identity
Remote worker & contractor fraud
Uncover hidden risks by detecting fake or misrepresented identities before granting access to sensitive systems
Investigate faster and defend smarter with AI intelligence from SpyCloud
Identity threats aren’t slowing down – and you can’t afford to either. With access to the world’s largest collection of recaptured darknet data, improved visuals to connect the relationships, and finished intel with AI-powered insights, SpyCloud Investigations delivers what your team needs most: speed, clarity, and intelligence you can act on today.
It’s everything our own investigators want from their tools. Less time chasing noise. Faster insights. More time stopping real threats. See how AI Insights can accelerate your investigations, get started with SpyCloud today.
See SpyCloud Investigations in action
Want to explore the new capabilities of SpyCloud Investigations? Book a demo for a hands-on exploration and see how it can save your analysts time.
FAQs
Investigations usually require analysts to pivot across multiple datasets manually. AI automates this process, correlating exposed credentials, digital behavior, and infrastructure links in seconds. Instead of spending hours stitching together evidence, analysts can move straight to decision-making.
No. AI accelerates investigations by handling repetitive, time-consuming tasks like clustering related identities or summarizing exposure data — but human expertise is still essential for judgment, attribution, and response. AI extends analysts’ reach; it doesn’t replace it.
Spycloud Investigations now includes AI Insights, which automatically analyzes exposed identity data to uncover hidden connections, digital behavior patterns, and threat actor relationships. This reduces manual work and turns raw data into actionable intelligence within seconds.
Investigations that previously took hours, or even days, can now be summarized in minutes. AI Insights automates up to 80% of the investigative legwork, freeing analysts to focus on high-value analysis and response.