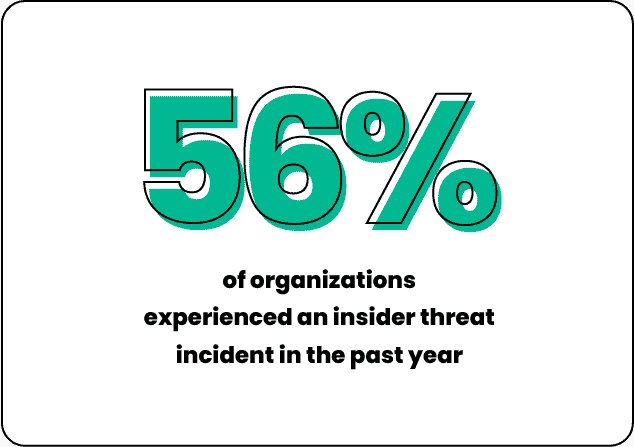
Insider threats have moved from theoretical to unavoidable. SpyCloud’s Insider Threat Pulse Report 2025, based on a survey of 100 security leaders, reveals that over half of organizations (56%) experienced at least one insider-related incident in the past year. It’s pretty clear that insider risks are now the rule rather than the exception.
Across the board, leaders express concern. Nearly all (97%) point to negligent insider threats as a concern, and 93% are concerned about malicious insider threats.
Yet despite the level of risk, the gap between intent and action remains wide. Many organizations claim to have insider threat programs, but the research shows that these efforts are often reactive, fragmented, and overly dependent on late-stage behavioral detection.
This article takes a deep dive into some of the report’s most significant findings and explains why identity-first detection is the missing piece in most insider risk strategies.
Insider risk is evolving and programs are not keeping up
The definition of “insider threat” has broadened. It no longer refers only to a disgruntled employee leaving a company on bad terms.
Today it can include:
- Malicious insiders who intentionally abuse access for personal, financial, or ideological gain.
- Negligent insiders who unintentionally put the business at risk through mistakes such as reusing weak passwords or mishandling sensitive data.
- Compromised insiders whose legitimate accounts are stolen by attackers through malware, phishing, or third-party breaches.
Compromised insiders are often the hardest to detect. Their actions look legitimate until a hijacked account is used to escalate privileges or move laterally inside the network. Traditional behavioral tools often struggle to catch these cases in time.
Although 64% of organizations say they have insider threat programs, most rely heavily on behavioral analytics. These tools only alert defenders after risky activity has started, which is too late to prevent damage.
Why today’s insider threat signals come too late
Anomalous behavior
Unusual logins, deviations from baseline activity, or data exfiltration attempts
Excessive downloads
Unauthorized access attempts
Suspicious network activity
Behavioral changes
Hostility, emotional outbursts, or erratic behavior during transitions
Some organizations also track background check anomalies or stressors such as financial hardship, but these are viewed as secondary indicators.
The problem is that these signals usually appear after an insider has already acted. A terminated employee showing hostility or a contractor suddenly accessing sensitive systems is not the beginning of a problem. It is proof that the threat is already active.
Where insider threat programs stall: detection, visibility, and response
Even with insider threat programs in place, organizations face persistent challenges that keep them from responding quickly and effectively:
- Alert fatigue and false positives: Analysts are overwhelmed by noisy alerts and often chase false leads while real threats slip by
- Limited visibility: Risk data is scattered across HR, identity, IT, and security systems, making it difficult to form a clear picture
- Manual processes: About 60% of organizations coordinate HR-security workflows manually through ad hoc emails or chats
- Tooling blind spots: SIEM and UEBA platforms add context but are not built to deliver the earliest warning
- Cultural resistance: In some organizations, employees and executives push back on insider threat monitoring due to privacy concerns. In other regions, privacy laws and works councils create additional barriers
- Resource constraints: Insider investigations are time-intensive and often require input from multiple teams, further stretching resources
“Teams are inundated with telemetry and overwhelmed by noisy alerts, making it difficult to piece together a coherent picture.”
These barriers explain why insider programs remain reactive. Without earlier signals and stronger collaboration, defenders often find themselves playing catch-up.
Infostealer malware silently fuels compromise
One of the pressing threats facing organizations today is the rise of fraudulent IT worker campaigns linked to North Korea. These operations involve state-sponsored actors applying for remote jobs using stolen or fabricated identities. Once inside, they can exfiltrate intellectual property, generate revenue for sanctioned regimes, or enable broader cyber operations.
SpyCloud research confirmed this trend by uncovering self-infection data from DPRK IT workers who inadvertently exposed their own activities through commodity infostealer malware. This analysis revealed the extent of the campaign – reaching into Fortune 500 companies and beyond – and showed how traditional HR and security processes often fail to detect fraudulent applicants.
The Insider Threat Pulse Report 2025 highlights the challenge organizations face in responding to this threat:
- A strong majority of organizations (87%) involve HR in insider defense
- Yet 60% admit HR–security coordination is manual and informal
- Very few have automated workflows to stop fraudulent applicants before they are onboarded
Charles Carmakal, CTO of Mandiant Consulting, describes the scale of the problem:
“Nearly every CISO that I’ve spoken to about the North Korean IT worker problem has admitted they’ve hired at least one North Korean IT worker, if not a dozen or a few dozen.”
This trend proves that insider risk is not only a workforce issue. It is a geopolitical security concern that requires tighter screening and identity-first detection.
For additional research on identity-based threats, visit the SpyCloud resource hub.
Identity exposure: the missing early warning signal
Behavioral analytics like UEBA and DLP are useful, but they are late-stage tools. They flag anomalies only once suspicious actions are visible.
The earliest warning signs of insider threats often come not from behavior but from identity misuse. Malware infections and stolen credentials typically surface on the darknet well before any red flags appear inside the enterprise.
SpyCloud’s identity intelligence equips security teams with the earliest possible warning. With access to recaptured data, teams can:
- Detect fraudulent job applicants before they gain access
- Surface malicious insiders with hidden links to criminal infrastructure
- Identify compromised employees and vendors weeks or months before accounts are abused
This approach transforms insider defense from reactive monitoring into proactive prevention.
Four priorities for closing the insider threat defense gap
- Prioritize high-fidelity signals that cut through noise and reduce false positives
- Strengthen background checks with darknet intelligence to verify new hires and contractors
- Automate HR–security workflows to eliminate delays caused by manual coordination
- Build a shared playbook so that insider risk monitoring spans the entire employee lifecycle
Final thoughts: Spot risks sooner. Defend smarter.
Insider threats extend from compromised identities, to fraudulent applicants, to state-sponsored infiltration campaigns. The Insider Threat Pulse Report 2025 makes three things clear:
- Insider risk is widespread, with more than half of organizations already affected
- Current programs are reactive and slow to act
- The earliest and most actionable warning signals come from identity exposure
SpyCloud provides security leaders with identity intelligence that enables earlier detection, reduces noise, and connects HR and security workflows. Instead of reacting to insider threats after they emerge, organizations can finally get ahead of them.
The future of insider defense is proactive, identity-first, and automated. SpyCloud helps you get there.
FAQs
The report draws on a survey of 100 security leaders, including 50 CISOs and 50 security managers or directors, from organizations with 500 or more employees. It explores how these professionals perceive, detect, and respond to insider threats.
SIEM platforms remain the backbone of most programs. Leaders also use DLP, UEBA, and EDR tools for added visibility. HR and identity data sources are sometimes included, but integration is usually inconsistent and often manual. Security teams should incorporate identity intelligence to strengthen their toolkit.
Most insider threat programs are not enough because they wait until it is too late. Behavioral analytics only flag activity after it becomes suspicious, leaving teams stuck in reaction mode. With analysts already facing noisy alerts, limited resources, and resistance from within the organization, prevention is almost impossible.
SpyCloud introduces identity intelligence as an early warning system. By analyzing recaptured data from malware infections, phishing campaigns, and breaches, SpyCloud uncovers compromised identities and fraudulent applicants before behaviors turn risky. This fills the gap left by traditional behavioral tools.
The report provides credible survey-backed data. It highlights the scale of the problem, the shortcomings of current programs, and the impact on security teams. These statistics give leaders the evidence they need to secure executive and board-level buy-in for investment in earlier detection and automation.