Summer is winding down, but there doesn’t seem to be any chill in the forecast for underground cybercrime activity. August delivered its share of drama, disruption, and emerging threats. In this month’s recap, we’re covering;
- The latest chapter of what we've dubbed the "Forum Wars" – including the apparent final demise of BreachForums and the ongoing fallout from XSS takedowns that have left threat actors scrambling for new homes,
- The rise of Warlock Ransomware and their creative (if questionable) marketing tactics designed to generate maximum hype,
- The chaotic world of ShinyHunters' scattered operations and their endless stream of provocatively-named Telegram channels, and
- A fascinating leak that exposed suspected North Korean APT infrastructure, complete with attribution puzzles that blur the lines between nation-state actors
We’re also taking a closer look at how generative AI is making its way into malware decision-making – spoiler alert: it’s more like using a calculator than creating digital sentience, but it’s still worth understanding how threat actors are closing skill gaps with LLM assistance.
From forum feuds to fake Chuckys, and from AI-powered malware to geopolitical cyber espionage, August kept our team busy tracking the always-shifting threat landscape. Let’s get into it!
The Forum Wars: BreachForums & XSS aftermath
BreachForums went dark in mid-April 2025 after a series of arrests and takedowns led by French authorities, leaving a chaotic power vacuum in the data breach forum ecosystem. [For a full breakdown of major developments in the cybercriminal forum world since April, you can check out our cybercrime updates from April, May, June, and July.]
Is BreachForums finally gone for good?
From late July into early August, BreachForums briefly came back online, instantly sparking rumours from criminal actors claiming that it must be a law enforcement-controlled honeypot. The ShinyHunters account on Telegram posted a long announcement stating that BreachForums, its PGP signing key, and all administrator accounts on the forum had been compromised by law enforcement. They went on to state that “if BreachForums remains online following this notice, it is operating as a honeypot under the control of multiple international law enforcement agencies.”
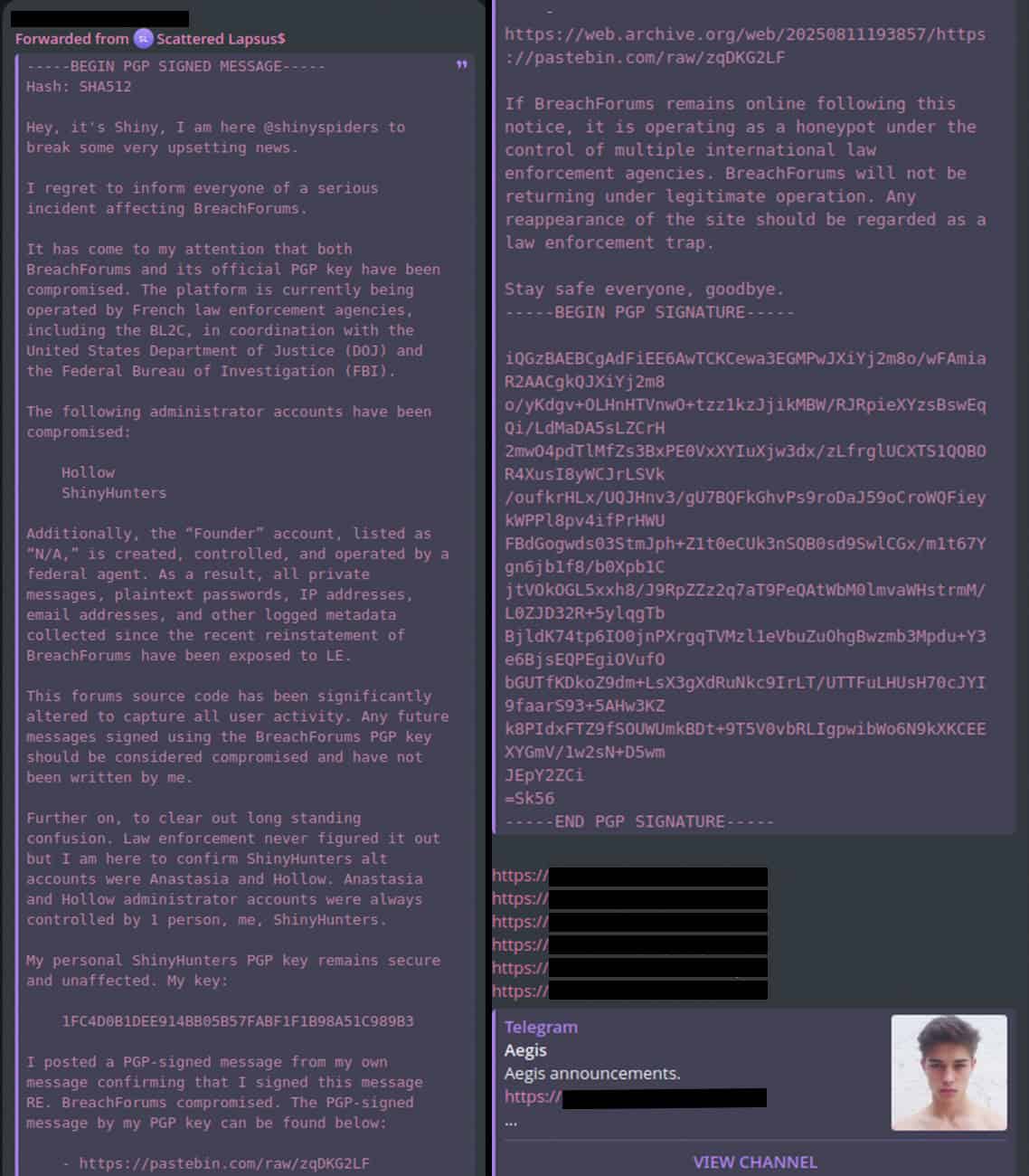
Announcement from the @shinyspiders account on Telegram stating that BreachForums had been compromised by law enforcement.
The briefly revived site has since gone dark again without any more law enforcement announcements or additional fanfare, leaving us cybercrime watchers to believe that BreachForums might finally be gone for good.
XSS disruption aftermath
XSS – a prominent Russian cybercriminal forum – was disrupted by law enforcement on July 22. The forum’s administrator, who went by the handle Toha, was also reportedly arrested in Ukraine alongside the takedown action. The XSS site appears to have been able to quickly reconstitute and is currently back online at xss[.]pro. However, some former XSS moderators have splintered off to form a new site – DamageLib – claiming that XSS was compromised and is now a law enforcement honeypot.
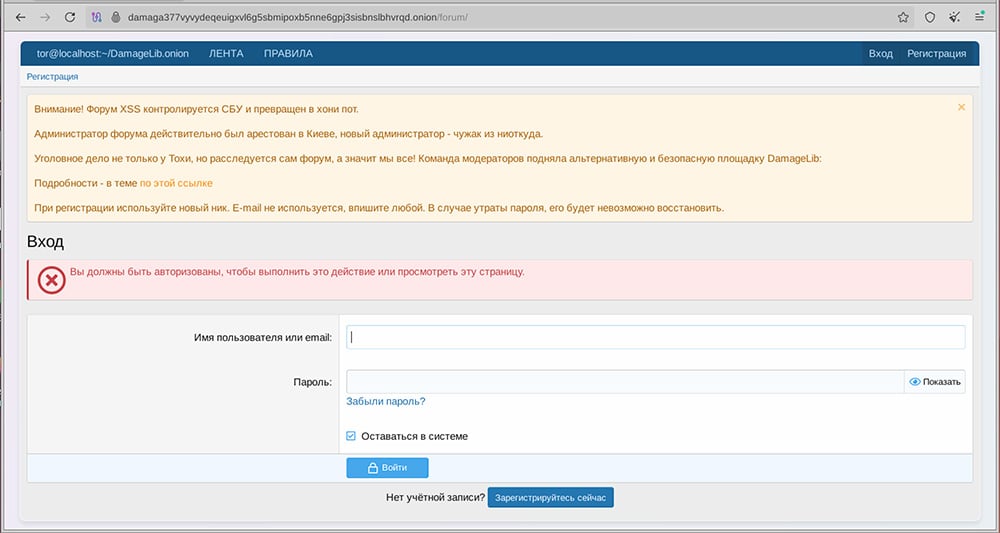
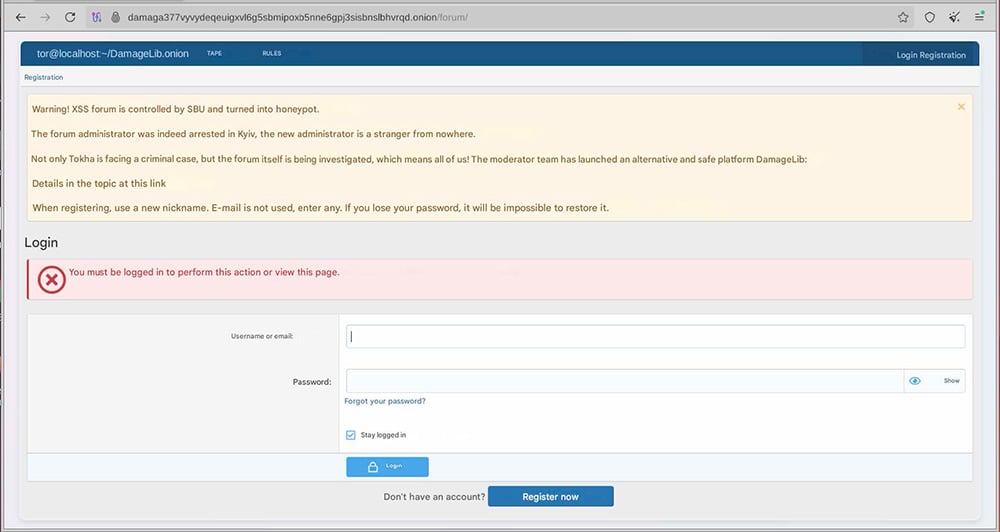
Login portal for the new DamageLib website including a message that XSS is controlled by the SBU and is now a honeypot. The message urges users to use a new nickname for their accounts on this new forum.
Other skids, scammers, & copycats
As the forum ecosystem continues to experience major disruptions, enterprising threat actors are attempting to capitalize on the situation by creating their own forums. Some recent developments in this vein include:
- BreachStars: A new forum called breachsta[.]rs, has added itself into the mix. In our initial pivoting around the site, we found a lot of glitches, dead links, and broken functionality. [We talk a little more about the BreachStars forum down below in the Shiny Scattered Lapsu$ Hunters Holding Spiders section.]
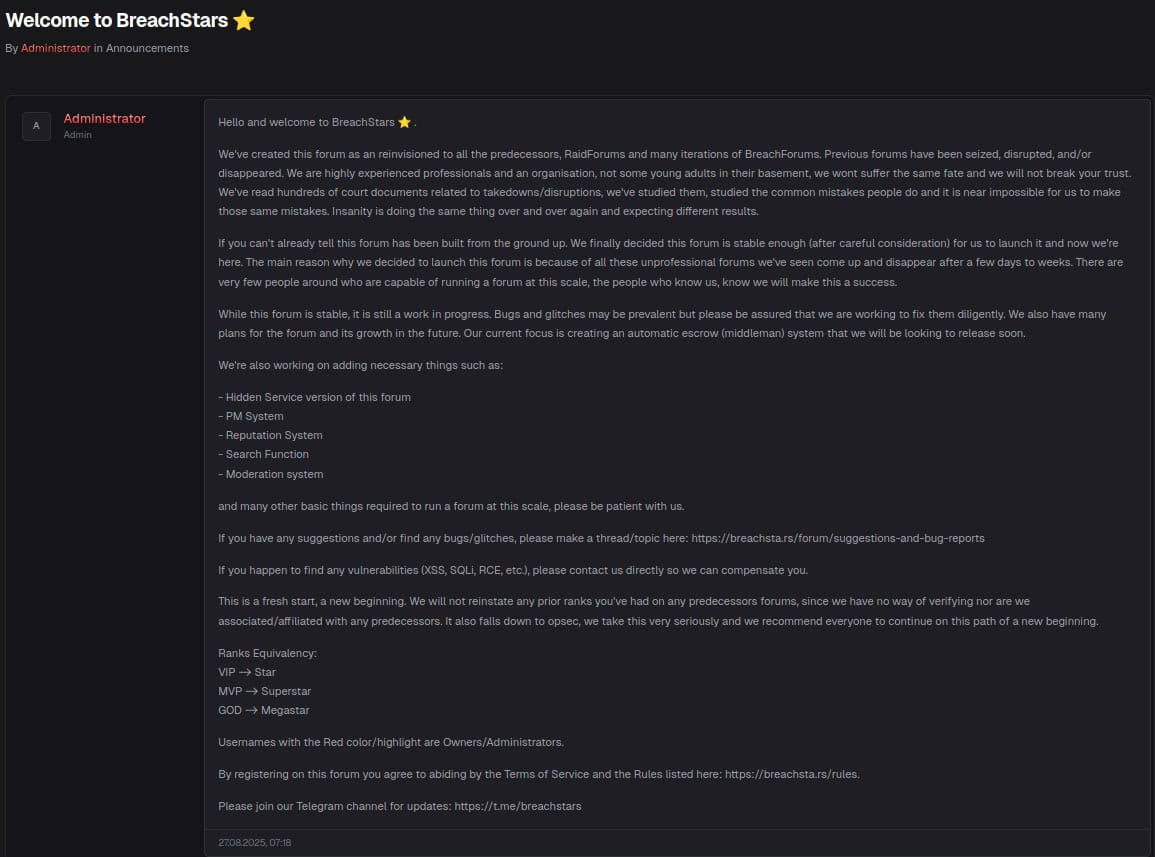
- Fake Chucky’s new forum: An actor that appears to be attempting to masquerade as Chucky – the owner of the LeakBase forum – has also claimed they are going to be creating their own forum. This actor started their own Telegram channel “chucky_lucky download” and has attempted to sell data on forums like DarkForums using the alias Chucky_BF. Multiple threat actors including Chucky himself have called him out as a scammer, and he has since been banned from DarkForums.
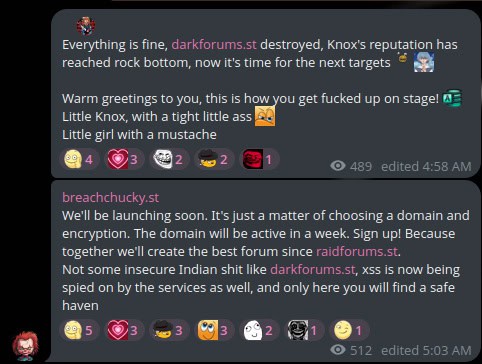
Telegram post from the fake Chucky’s account stating that their new forum will be launching soon.
- UmbraForums: This forum was launched in August by an actor with the moniker Nicotine. At first glance, it appears to have quite a few reposts from LeakBase.
![Screenshot of the homepage for umbraforums[.]net.](https://spycloud.com/wp-content/uploads/2025/09/blog-img-umbra-forums.jpg)
Screenshot of the homepage for umbraforums[.]net.
Warlock ransomware group generates hype
The Warlock ransomware group made headlines after hitting two different large telecommunications companies with ransomware and then threatening to leak their data online. The group was relatively unknown prior to these incidents, but they appear to have leveraged a few interesting strategies that helped them drum up significant hype about these breaches:
- Forum posts to drive people to their site: This group actively announced breaches and forthcoming data leaks on the RAMP forum, driving any curious users back to their data leak site (DLS). This is a somewhat unusual use of the RAMP forum, which is more known for facilitating exchanges between ransomware operators that sit at different stages of the attack cycle (for example, initial access brokers often advertise corporate network access for sale on RAMP).
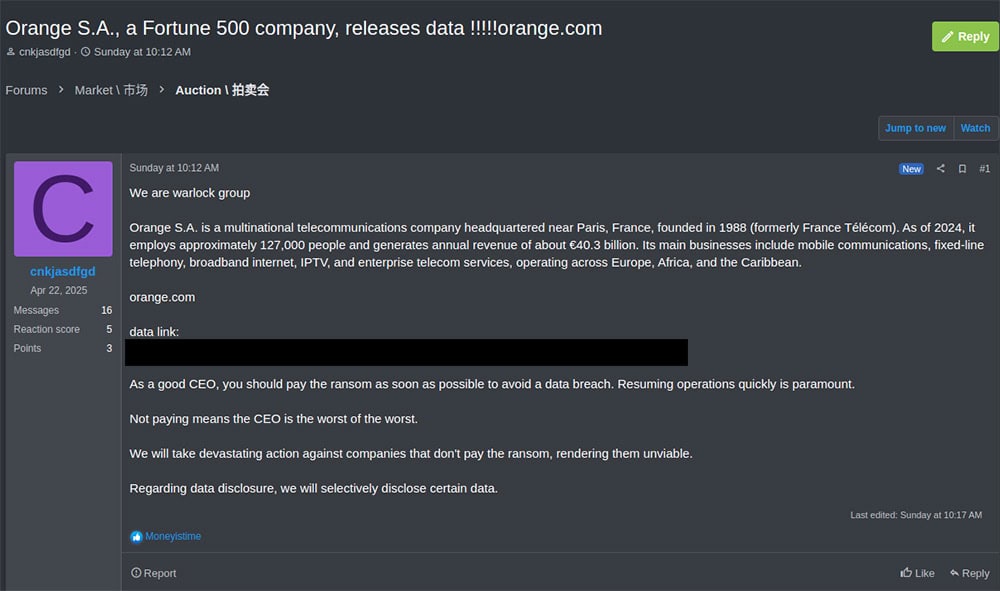
Post on the RAMP forum by the Warlock ransomware group about a telecommunications company they claim to have breached.
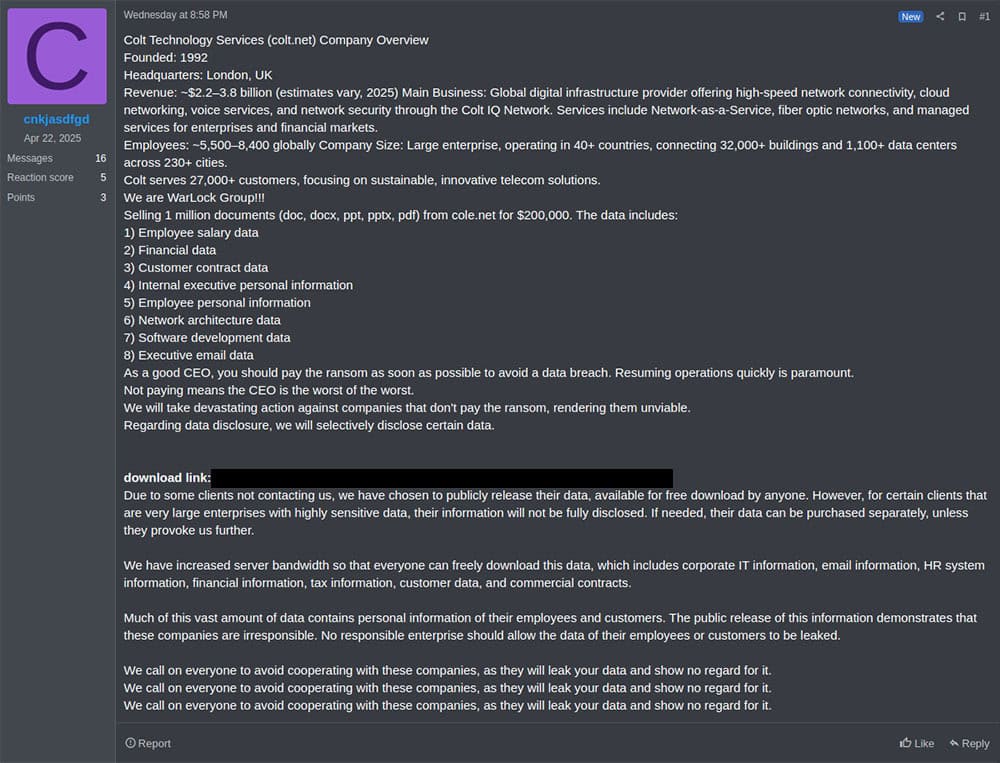
Another Warlock post on the RAMP forum about a different telecommunications company they claim to have breached.
- Promising data auctions and secondary sales: The group also continues to make vague statements about selling datasets either through auctions or directly, with no clear instructions or indications of these sales or auctions actually happening. Some posts also contain unclear messages to affected third parties (such as customers or vendors of the breached entities who believe their data might appear in the breached datasets) implying that they can purchase their data separately to prevent it from being leaked online.
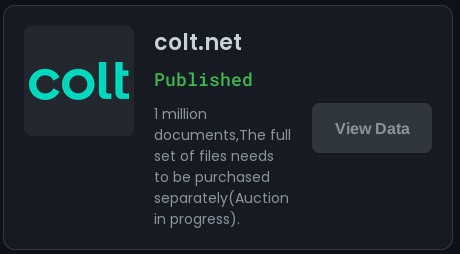
Post on the Warlock DLS stating that an auction for the full dataset is in progress.
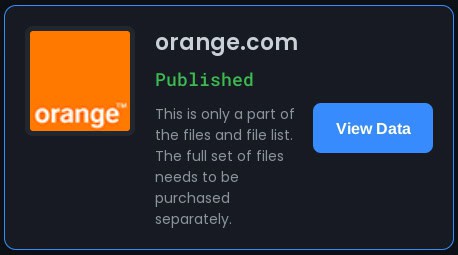
Post on the Warlock DLS stating that “the full set of files needs to be purchased separately.”
- Drip-feeding data: In general, so far this group appears to be promising more than they are delivering with regards to the data they claim to have breached. Like other ransomware groups, they have countdown timers set for when breached data will be leaked publicly, but continue changing the parameters of what data will be leaked. For one of the breached telcos mentioned above, Warlock posted a list of files they claimed to have stolen from the victim, but most of those files are still yet to be made available anywhere for download. Even for the limited number of files they do appear to have available on their site for each victim, the site simply shows users an error message stating that the file is too big to download when they attempt to download anything larger than 1GB.
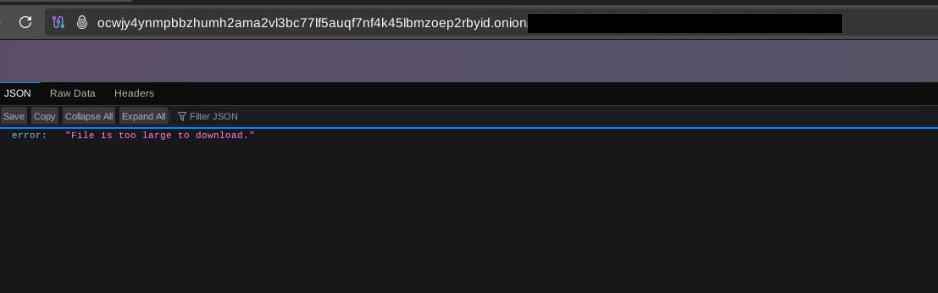
Error message on the Warlock DLS stating that the file is too large to download.
Our team here at SpyCloud Labs will continue to monitor the situation with the Warlock group. It remains to be seen whether they are intentionally overhyping and exaggerating what they actually have in order to scam people into buying worthless data, or they are simply bad at efficiently sharing large files.
Shiny Scattered Lapsu$ Hunters holding spiders
ShinyHunters, or what is left of them after BreachForums-related arrests, has continued their campaign of loudly boasting about large and noteworthy breaches over the past month. To facilitate these claims, the group has been creating open Telegram channels with elaborate and often crude usernames and titles. These channels are somewhat overwhelming, full of boisterous claims, lies, memes, questionable language, and – occasionally – sensitive data.
scattered lapsu$ hunters
Here are some examples of these Telegram channel usernames and channel titles (with some regexes thrown in because there’s just SO MANY channels):
- scattered [lapsus$|lapsu$] hunters (v?[2|3|4|5\.0])? \-? (The Com HQ SCATTERED SP1D3R HUNTERS)?
- Scattered Lapsus$ (Hunter)? (5\.0)? (Group)?
- (Groups)? ShinyHunters (Lapsus$)?
- sp1d3rlapsushunters
- scatteredlapsusp1d3rhunters
- leavemealone[BL2C|feds|fbi|cybern.gger]
- sc4ttered
- shinycorpgroup
- f.ckmandiantunit221bcr0wdshart
- Aegis Hunters Announcement
It is unclear why ShinyHunters sequentially created all of these open channels only to delete them directly or wait for them to get banned. Eventually, after much strife, the group appeared to have landed on a private, invite-only Telegram channel called “Scattered Lapsus$ Hunter 5.0” which has remained up for a few weeks now.
These channel names appear to be directly mocking law enforcement and the cyber threat intelligence industry by making their own amalgamations of ShinyHunters, Lapsus$, Scattered Spider, and more.
We believe the point is to show that the identification and attribution of these actors is murky at best, and completely off at worst, its targeted trolling against their adversaries. Since a good deal of some of the original conspirators in these groups are now in LEA custody, we also believe the actions of late represent a bit of a lashing out by the remaining members of these groups.
Some members of these channels even appear to be demanding that authorities free arrested Com-affiliated actors, but even their threats are so tinged with irony and trolling that it’s unclear whether or not they are jokes.
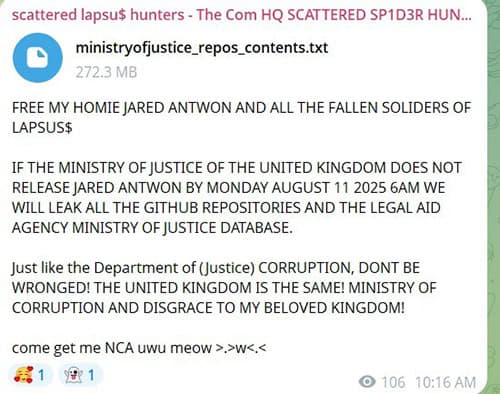
Screenshot from one of the scattered lapsu$ hunters channels on Telegram, which we obtained from an article on databreaches.net.
BreachStars
Recently, ShinyHunters also appeared to be promoting a new forum called BreachStars. However, as with most things from ShinyHunters, they are relatively fickle. Days later, we started to see them openly criticize BreachStars on Telegram.
![Telegram post promoting the breachsta[.]rs forum](https://spycloud.com/wp-content/uploads/2025/09/blog-img-breachstars-rs-breachforums.jpg)
Telegram post promoting the breachsta[.]rs forum.
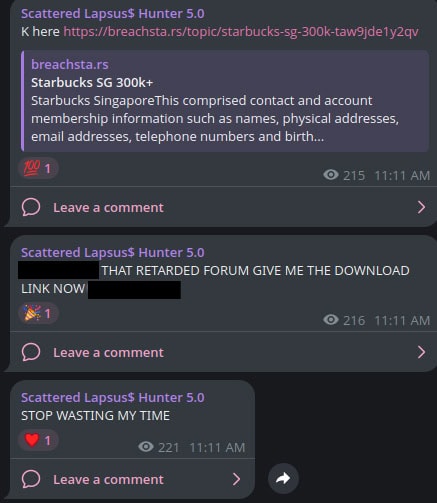
Telegram post criticizing the breachsta[.]rs forum.
Confusing claims
Within their array of scattered lapsu$ hunters channels, the ShinyHunters group has made grand claims about many of the most recent high profile breaches attributed to social engineering access to SalesForce installations at major companies. In some cases, ShinyHunters have offered scant evidence that they actually carried out the breaches they claim, and in others they have leaked significant datasets that appear to be actual bona fides of their involvement with a significant amount of proof to back them up. It’s unclear whether these muddled claims are ultimately motivated by clout chasing, trolling, obfuscation, or perhaps all three.
Within the last two weeks of August, the absurdity of the continued misattribution of unrelated activity to ShinyHunters came to the fore. ShinyHunters started to claim responsibility for a major supply chain attack on the SalesLoft Drift service that allowed attackers to gain access to hundreds of corporate Salesforce instances. While it is still unclear which threat actor is responsible for this sophisticated attack, ShinyHunters has provided no unique non-public evidence either in their channel or in interviews with cybersecurity journalists to prove that they were responsible for the attack.
Google Mandiant, who are assisting in incident response for the event, have assigned a different UNC cluster identifier to the previous social engineering database access hacks (UNC6040) and the more recent SalesLoft incident (UNC6395), casting further doubt onto any connection between the SalesLoft drift incident and whoever is currently operating the ShinyHunters persona.
Phrack and leak: Suspected DPRK APT leak raises attribution questions
In other news, two security researchers, Saber and cyb0rg, hacked an APT actor box, leaked the data via DDoSecrets, and published their findings in the newest issue of Phrack magazine. The dump contains data that they obtained from the APT-controlled workstation (as well as a VPS that the actor appeared to use for spear-phishing attacks) including tooling, backdoors, payloads, log files, and history files.
This data provides evidence of the threat actor’s targeting and successful intrusions into cyber espionage targets in both South Korea and Taiwan.

Note from Saber and cyb0rg to readers of their Phrack article
Based on artifacts found on the actor’s workstation, the researchers attribute this activity to the North Korean-aligned APT actor Kimsuky, even calling their findings “APT Down – The North Korea Files.”
However, they do note that the workstation also contained artifacts linked to Chinese-aligned state-sponsored threat actors (including a payload that Mandiant observed being used in the wild by a Chinese state-sponsored threat actor).
They also note that the actor can be frequently observed using Google to translate Korean error messages into Chinese. A couple of weeks later, Spur also published a blog pivoting off of this threat actor’s IP address to connect it to WgetCloud, Chinese-controlled Trojan proxy network that anyone can purchase a subscription to use.
Deeper into their analysis, Saber and cyb0rg ultimately conclude that they “cautiously believe that KIM is Chinese but fulfills the agenda of North Korea… and China… alike.”
GenAI in malware: Productivity boost, not paradigm shift
AI is everywhere we look these days, although to nobody’s real surprise, malware developers have written their code with the help of Generative AI (GenAI) going back at least as far as ChatGPT’s 2022 release. However, in 2025, security researchers observed GenAI being used as an inline decision engine in suspected nation-state attacks (LAMEHUG). In the same time frame, researchers at NYU created a similarly-architected experimental ransomware (PromptLock). While these examples illustrate a paradigm shift in flow control, it doesn’t change the way in which attacks are conducted, detected, and disrupted.
Programming logic gates for flow control is tedious and replacing it with a Large Language Model (LLM) prompt is convenient. However, LLMs also create a new class of problems in such decision trees that must be solved with prompt engineering or additional triaging architecture as new edge cases appear. Sometimes, it can be more optimal to use the more traditional AI approach (machine learning) for decision making instead of trusting a general-purpose language transformer.

As consumer-facing LLM products have continued to proliferate, grow, and gain popularity, LLM developers have continued to deploy and fine-tune guardrails. These guardrails, which limit consumer-facing models from answering prompts with content deemed potentially harmful or dangerous (such as generating a Cobalt Strike payload, for example) were often deployed in response to calls from policymakers, activists, and AI ethicists.
However, thanks to a plethora of red team tools, threat intelligence reports, and malware analysis available on the world wide web (the corpus of knowledge used for training LLM models), malware development capabilities inherently exist within the models. As these models continue to be iterated, the balance between guardrails and usability continue to be adjudicated by the major LLM developers.
Throughout this time, as experts across numerous fields and industries have started to embrace GenAI, there have been both gains in productivity and slip-ups. Without human review, LLMs can get out of control and hallucinations can interfere in unpredictable ways with any data flow based on GenAI. Blood, sweat, and tears are required to turn AI vibe coding slop into productive pieces of a pipeline. But it’s undeniable that, for those obsessed enough, Generative AI can cover skills gaps and make more advanced coding possible for those willing to test, run, and argue code over several sessions and VM rebuilds.
The same holds for cybercriminals. GenAI alone does not provide any significant change in the way attacks are carried out. In most cases, it simply closes the skills gap for a portion of the population. GenAI can also replace complicated logic gates in decision flow control – this fuzzy decision making can simplify pipeline diagrams. However, such a decision engine often requires further fine tuning (prompt engineering) as edge cases come up or bad assumptions are made.
Ultimately, no significant paradigm shift in the way attacks are detected and blocked has occurred – only some fractional increase in the productivity of cybercriminals. This mirrors the effect GenAI is having on legitimate business models, including the companies that disrupt cybercriminals.
At the end of the day, the advent of LLMs is no different than that of the calculator. Calculators don’t create any new math and they don’t answer any questions that humans can’t answer themselves, but the time to calculate an answer becomes much faster (at least in some cases suited towards using a calculator or a very very good chatbot).
In the case of assisted coding, GenAI isn’t creating new coding paradigms, it’s regurgitating things it’s learned from Github and Stack Overflow – human creations. It can mix and match pieces of things it’s learned, sometimes seamlessly and sometimes to disastrous effect. At the end of the day, an LLM is a static text transformer. It is not a living, learning thing – it’s just “spreadsheets on steroids.”
New research & insights from SpyCloud
Cybercriminals don’t clock out at 5 p.m. Threat actors act quickly, often within hours of gaining access to credentials or exfiltrated browser data. To match that pace, we’ve set new performance standards. Check them out >
SIEM, DLP, and UEBA solutions are great for pointing out anomalous behavior once an insider threat is operating inside your network. But what they can’t see are the threats already gathering momentum in the criminal underground, where stolen identity data fuels the opportunity for insider attacks. Here’s how to close the gap >
Find quick-starts, deep dives, and “didn’t-know-you-could-do-that” moments that help you get more from every SpyCloud product. Whether you’re learning about or integrating our APIs, fine-tuning security workflows, or chasing your next big use case, this is your roadmap. Explore now >
Recaptured data numbers for August
August monthly total
Total New Recaptured Data Records for August
796,543,441
New third-party breach data this month
Third-Party Breaches Parsed and Ingested
736
New Data Records from Third-Party Breaches
183,484,384
New recaptured phished data this month
Phished records
1,774,043
New infostealer malware data this month
Stealer Logs Parsed and Ingested
3,012,578
New Data Records from Stealer Infections
41,738,403
New Stolen Cookie Records
571,320,654
Stay in the loop
Our team at SpyCloud Labs keeps close tabs on the cybercrime ecosystem. Sign up to stay in the loop with our latest research.