On the heels of Halloween, we’re back with another spooky cybercrime update from the SpyCloud Labs team. The cybercrime world has been busy coming up with new tricks, but there are some treats for us defenders – we’re here to help you unpack it all.
This month we’re covering:
- Declining LummaC2 infostealer infection activity after someone doxxed their dev team and took over some of their Telegram accounts
- Homeless BreachStars, another BreachForums clone, as the latest addition to the ‘Forum Wars,’ along with the possible return of BreachForums
- Data theft extortion incidents from the Cl0p ransomware group & Scattered LAPSUS$ ShinyHunters
- New leaks from hacktivist groups CyberToufan and BlackMoon
Plus: Operation Endgame's Latest Takedown
Updated on November 14, 2025
We’re happy to report a notable takedown due to the diligent collaboration efforts of Operation Endgame. Get the details behind the joint effort that has effectively disrupted the Rhadamanthys infostealer, Remote Access Trojan VenomRAT, and the botnet Elysium here.
And follow along with our SVP of SpyCloud Labs, Trevor Hilligoss, as we track Rhadamanthys’ decline after the takedown.
Keep reading for details on this month’s updates.
LummaC2 doxxing and decline
On September 17, LummaC2 announced via various channels and underground forums that two of their Telegram accounts had been stolen. This activity seemed to coincide with other observable impacts to the LummaC2 operation, including:
- Takedowns of a few popular stealer log aggregator channels,
- An observable decline in LummaC2 infection attempts and new LummaC2 panel infrastructure (as reported by TrendMicro and corroborated by our team at SpyCloud Labs)
- A large doxxing campaign against LummaC2 developers and administrators on a site called Lumma Rats
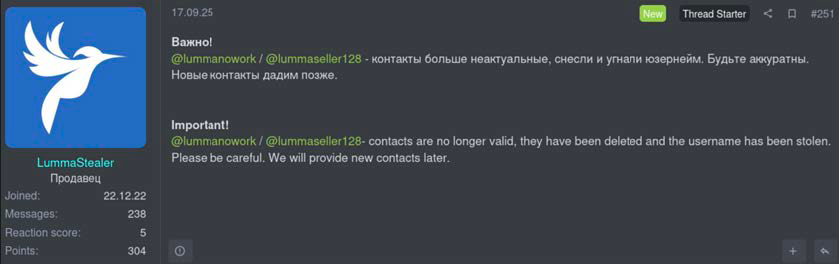
Forum post about two Lumma Telegram accounts having been stolen, as highlighted by Trend Micro in their blog
Decline in LummaC2 infections
In SpyCloud’s collection of infostealer malware logs, we can corroborate TrendMicro’s observation of a pretty significant decline in new LummaC2 infections starting on September 17, 2025 with this decreased volume continuing through the rest of September and October. While daily infection counts usually fluctuate from day-to-day, this type of sustained dip in infection counts is rare to see, and might indicate a real disruption to LummaC2’s operations. When we look at the counts of new LummaC2 logs we collected over the same date range, we still see a general downward trend, but the decline is much less drastic. This indicates that we are likely observing a decline in LummaC2 infections across the ecosystem versus a decline in collected logs due to takedowns affecting log distributors, like stealer log cloud channels.
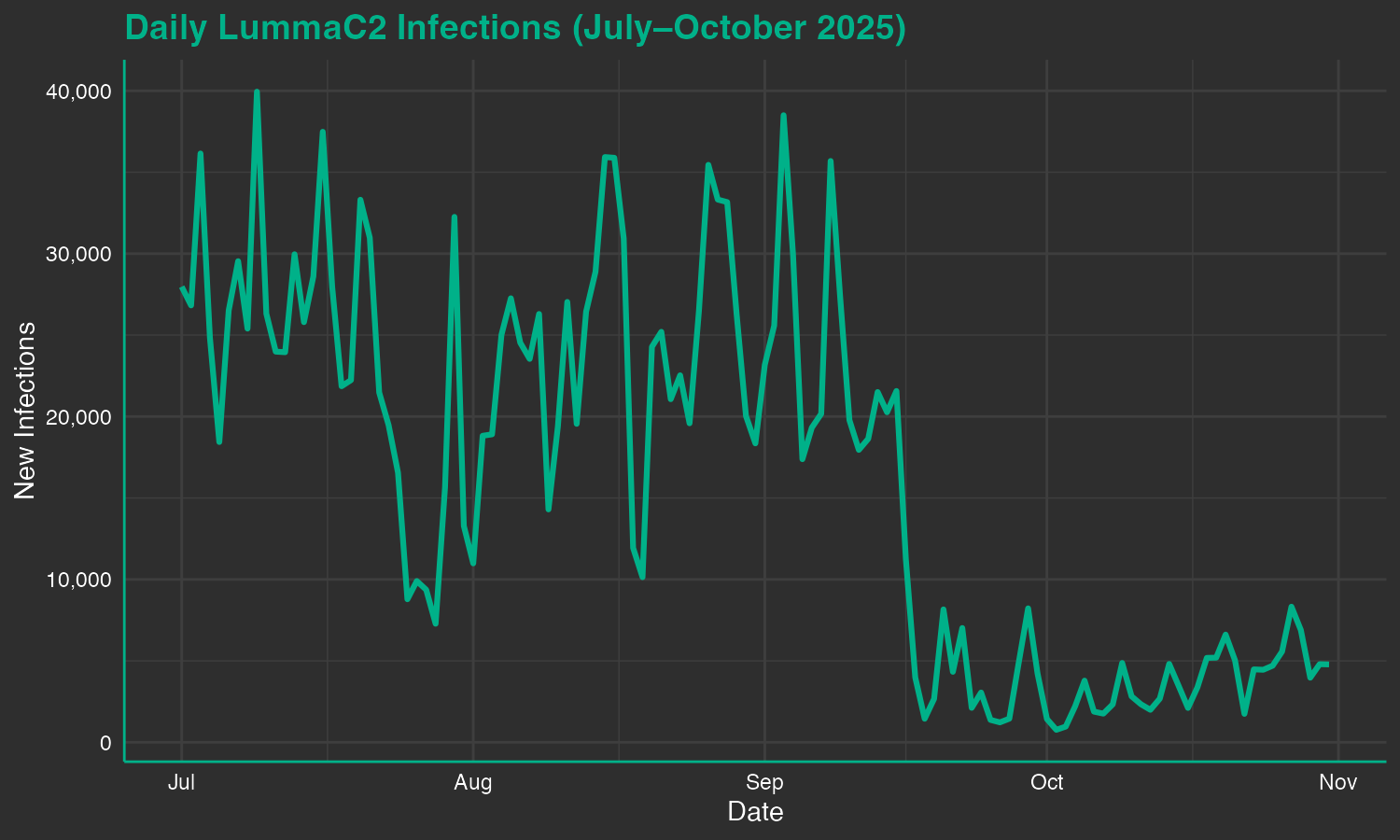
Plot of new daily LummaC2 infections from July through October 2025, with a clear drop observable in mid-September.
LummaC2 dox site
- We see a lot of the data across historical breaches and leaks we have already recaptured, and
- Some of the social media accounts for various digital platforms linked to the alleged real-life identities of these actors appear to be live and active and many have been recently taken down following the posted doxxes.
We will continue to monitor developments with LummaC2 and their operators – a permanent disruption to their operations would be pretty significant, as LummaC2 has been the most prolific infostealer on the market for the past year.
‘Forum Wars’ continues with Homeless BreachStars; BreachForums is (maybe) back?
The last month has produced some strange developments in the forum world as the shuffle to replace BreachForums continues.
First, there was a takedown of the reused breachforums[.]hn website that we covered last month.
Then, we saw multiple domain shutdowns for the new BreachStars forum, which changed domains four times in a week at the end of October. The progression went as follows:
- Prior to October 24, 2025 the domain was breachsta[.]rs
- From the 24th to the 27th it was bstars[.]st
- From the 27th to the 28th it was breachstars[.]st
- From the 29th on it is now homed at breachstars[.]hn
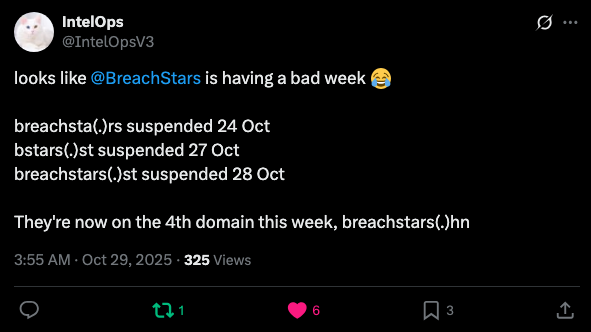
X Post by @IntelOpsV3 highlighting the progression of BreachStars domain takedowns
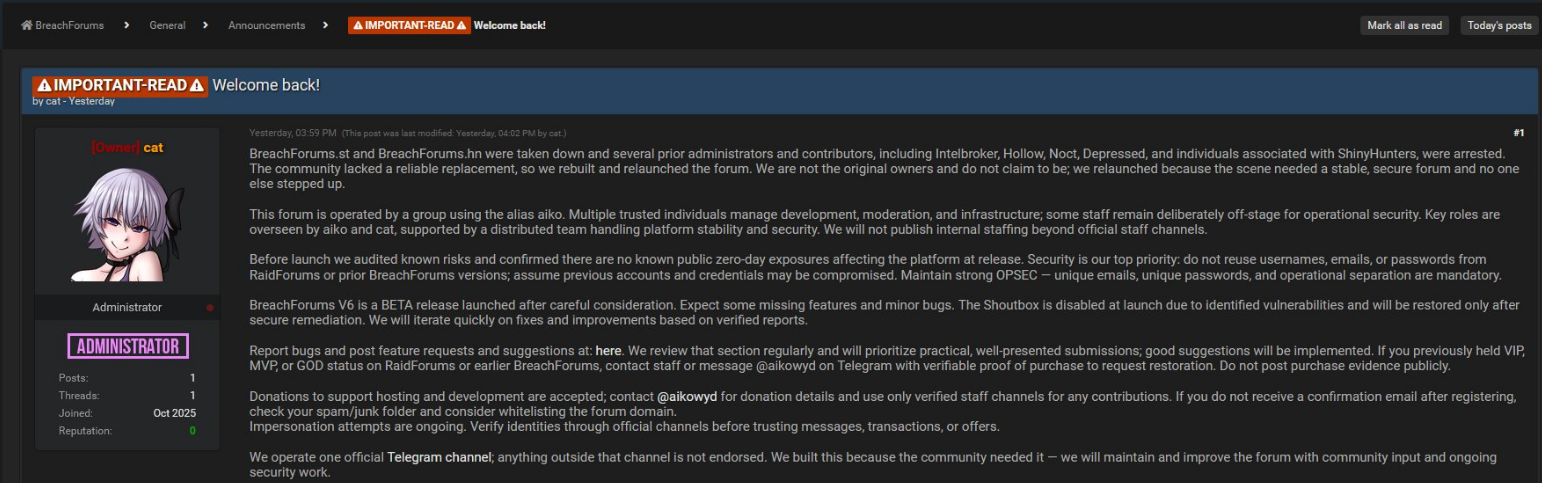
Picture showing the new site announcement by admin/own “cat”, screenshot from an X post by @larp1ngs.
Last but not least, as of October 20th, there appeared to be some sort of revival of the original BreachForums site, even after some of the community had stated it is not coming back.
We found that the domain breached[.]sh is hosting what seems to be the original site with some new and some old actors running the show. It appears an actor by the name of Trix is the new site owner, and some old mods like koko have come back to help with site administration.
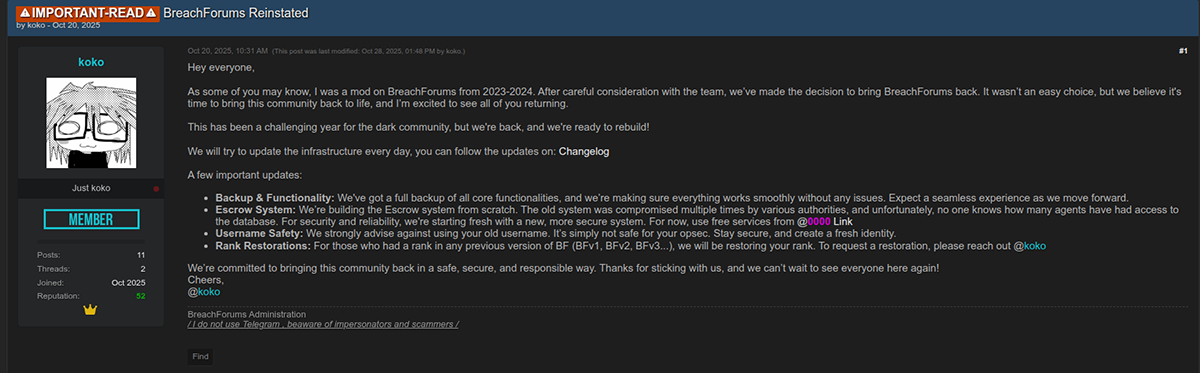
Post from an old BreachForums moderator named “koko” talking about BreachForums being reinstated.
It is not clear whether this is a real revival, a law enforcement honeypot, or something else entirely. There have been some suspicious oddities associated with the site’s return, such as a sales notification advertising the sale of the whole site for a few days. This event was documented here by @IntelOpsV3 on X.
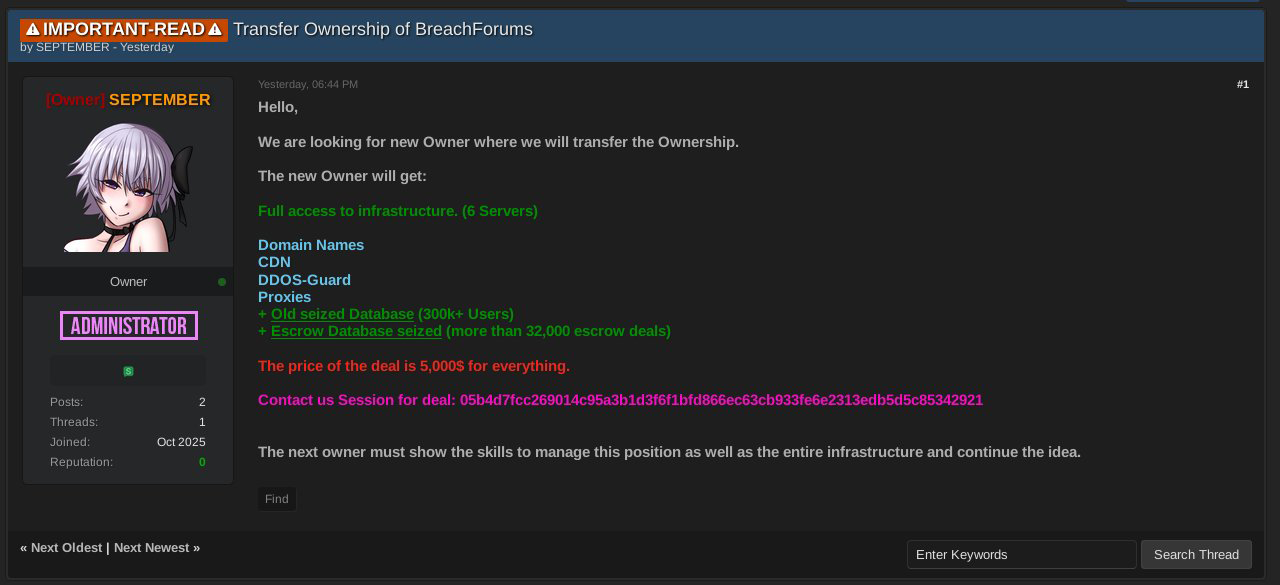
It should be noted that in this post, the site owner was listed as SEPTEMBER, but previously the owner role had been assigned to Trix. As of the time of writing in early November, this site is still functional and Trix is still listed as the owner. Time will tell what is really happening here and if it will all last more than a few weeks, as most of these clone sites tend to die fast.
Keeping up with Cl0p
Beginning in August 2025, the Cl0p ransomware group began exploiting a zero-day vulnerability in Oracle E-Business Suite (EBS), allowing them to successfully exfiltrate large amounts of data from multiple corporate EBS environments. Then, in late September, the group began attempting to extort victimized organizations through email campaigns directed at executives. Finally, in early October, Cl0p began to publicly list victims on their data leak site (DLS) and are – as of the time of this writing – continuing to leak full datasets from these EBS intrusions.
Like many of Cl0p’s campaigns, this most recent wave of activity has (allegedly) impacted quite a few big-name entities, including energy management companies, telecommunications companies, capital equipment manufacturers, universities, and a major airline.
This specific playbook – mass exploitation of a zero-day vulnerability to compromise a specific internet-facing appliance or application en masse and then follow up with data theft extortion – is not new for Cl0p. In May 2023, the group became somewhat notorious for it when they exploited a previously unknown vulnerability in the MOVEit file transfer software and conducted data theft extortion against hundreds of victims organizations. Since then, they have followed this process multiple times targeting different services (e.g. a campaign targeting Cleo file transfer software instances in December 2024).
The ShinyHunters DLS saga continues
Last month, we posted about a new DLS apparently created by some of the remaining members of ShinyHunters, a COM-linked threat actor group. In October, they did release some data to this new leaksite, but not at nearly the scale nor within the timetable that they promised. At the time of writing, the DLS was also linking users to breachsta[.]rs to download the leaks and requiring four credits to unlock each of the leaks. This infuriated some of the channel participants who saw this as a petty money grab by ShinyHunters. Eventually, ShinyHunters uploaded the leaks to Limewire, enabling data downloaders to bypass using BreachStars altogether. Some users then complained that they bought credits on BreachStars, but were never able to use them.
In the end, they released data from 6 different breached Salesforce instances via links to Limewire downloads without the BreachStars pass through – a much smaller number than the 39 different companies they had originally stated they were going to post data from on their Scattered LAPSUS$ ShinyHunters (SLSH) DLS. They have also stated that they have no additional planned releases.

Telegram post from SLSH stating that they “have nothing else to leak.”
Based on this released data, it still remains unclear if the individuals behind the DLS were actually involved in the Salesloft/Drift incident; all of the data released so far appears related to previous threat activity targeting Salesforce instances via vishing (phishing over voice calls). These limited releases led to criticism from others in their Telegram channels, who accused them of being frauds and script kiddies.

Telegram posts inside of the channel after the release of the limited data on Saturday, October 11, 2025.
The DLS breachforums[.]hn was also affected by a law enforcement takedown on October 9th which was then noted by the FBI on Sunday the 12th, but this only appears to have affected the main clearnet domain for the site; as the Onion instance still functioned. In apparent retaliation, SLSH began doxxing US government employees – posting spreadsheets of data containing work email addresses, phone numbers, and physical addresses of hundreds of government employees.
In the following weeks, the other Onion site and the newer shinyhunte[.]rs DLS mirrors were also taken down by an unknown entity. This entity would leave messages at the root of each site addressed to “James”. Both are currently down and not functional.
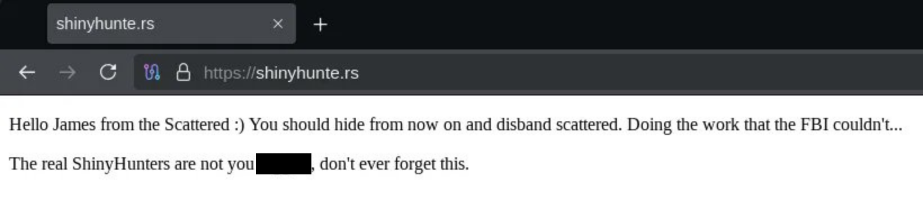
One of the text messages caught by @DailyDarkWeb.

One of the final messages written before the sites went down was caught by @AlvieriD.
Return of The Toufan
On October 13, 2025 after roughly a year of inactivity, the hacktivist group CyberToufan once again began posting with a Telegram message stating they would “respect the ceasefire.” CyberToufan had already allegedly compromised some companies in September, but appeared to refrain from dumping the information in the face of the ceasefire between Israel and Hamas.
Around October 18th, after combatants had appeared to violate the ceasefire, the CyberToufan account began posting large dumps of Israeli companies – some of which are alleged to have relationships with Israeli military and infrastructure – and the US embassy in Jerusalem.
This actor has demonstrated an ability to exfiltrate large amounts of sensitive data from key companies, similar to big game ransomware exfiltration, but with a geopolitical motive instead of financially-motivated extortion as their endgame. CyberToufan doesn’t appear to be concerned with money, so there is no countdown to publishing and no dangling of decryption keys. Data stolen is, barring any ceasefires, data dumped.

Post from CyberToufan stating that they will respect the Israeli-Palestinean ceasefire.
Throughout 2023, CyberToufan had demonstrated similar sophistication, motivation, and target selection. This earlier activity was tracked by Kevin Beaumont, who suggests the group may be of Palestinian or Iranian origin and designates them as fake hacktivists.
All we know for sure is that the architects of the CyberToufan account want it to be associated with Iran, given the moniker Toufan – a term that has a handful of meanings in the Iranian language. Canonically, it is an Iranian word cognate with English typhoon (e.g. a storm or a deluge). But culturally, its meanings include an Iranian combat helicopter, the labour party of Iran, and the labour party’s associated periodical. Whether CyberToufan’s namesake is meant to be a hat-tip to the Iranian military-political machinery or simply a reference to a deluge of data dumps is unclear.
The deluge of data dumps
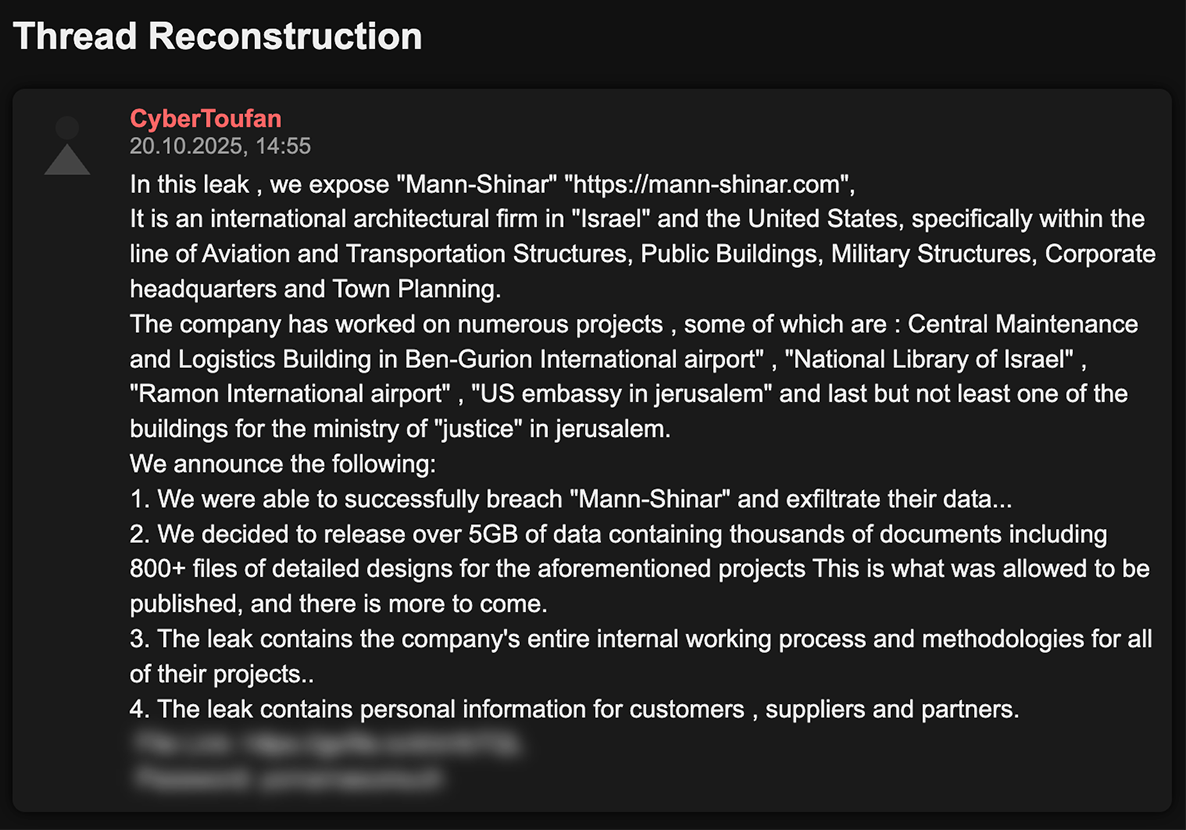
A reconstructed post by CyberToufan about a hack-and-leak operation targeting the Mann-Shinar architectural firm.
Five days later, amidst another data deluge possibly inflamed by the IDF’s bombing of Lebanon on the day before, the account shared 50 GB of data from Rational Solutions, who CyberToufan claims is “in the weapons business.” Note the grammatical error “they’s building” – indicating a non-native English speaker.
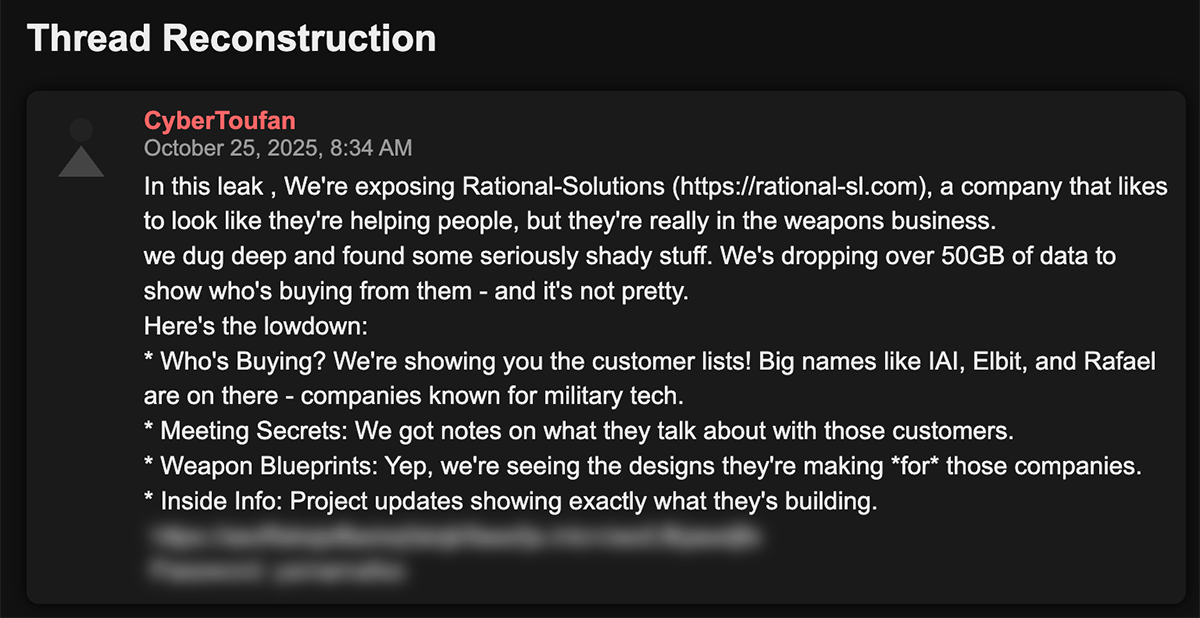
A reconstructed post by CyberToufan about a hack-and-leak operation targeting Rational-Solutions
But are they ‘real hacktivists’?
If we avoid the word hacktivism for a moment and consider electronics simply a tool of activism, not much has changed from 20th to 21st century activism. Activism is a social reaction to perceived political dangers. As a functional social behavior, activism increases in the context of some entity’s military or political escalations. Naturally, enemies of such entities will leverage activist movements to forward their own agendas under the guise of activism, blurring the lines. When these social dynamics are applied to the cybersphere, it is fundamentally the same activism, but with an evolved layer of anonymity and delivery thanks to information technology.
Ultimately, whether CyberToufan is a sophisticated nation-state sponsored actor or an Iranian teen hacktivist acting of their own patriotic volition is somewhat beside the point. A more generalizable assertion is that countries perceived to be the belligerents of warfare are among the most highly targeted for information warfare by all classes of cyber threat actors, from skiddies that see attacking belligerents as a morally acceptable training exercise to sophisticated state actors that have targeted agendas. This naturally includes some of the top global influencers and military spenders in the world, including the US, Russia, China, the UK, Israel, and Iran. Lots of data is regularly posted in underground forums for these countries free of charge, simply because they are each perceived, by someone somewhere, as the bad guys.
Consider, in contrast, a stereotypically neutral, but economically prosperous country like Switzerland. Cybercriminals may regularly compromise Swiss data, but seldom post it publicly as part of an information and reputation attack, instead leveraging it for their own financial gain or selling it on the black market. There is no CyberVoroshilov account decrying Switzerland and publicly dumping GB of highly sensitive data, free of charge (but if there was, it would likely be of Russian origin. Russian hacktivists have, in the past, DDoS’d Swiss infrastructure – likely in reaction to its sanctions against Russia).
BlackMoon hacktivists expose Russian-Chinese military collaboration
From July through September 2025, anti-Russian hacktivist group BlackMoon published a series of documents about the “sword 208” project – a military collaboration between Russia and China to help the latter launch a kinetic attack on Taiwan. BlackMoon – an anti-Russian hacktivist group – began posting to a Twitter/X account and Onion site in April 2025. Starting in July, they started to release documents specifically related to this sword 208 project, at first referring to as the #МЕЧ (sword) project, but soon switching to referring to it as “sword 208.”
In total, BlackMoon publicly leaked 10 small batches of sword 208 project documents via Proton Drive, including signed contractual agreements, presentations, timelines, and even photographs of in-person meetings between the collaborators. The independent Russian news outlet, The Insider, authenticated some of these documents in August. Security researchers at RUSI also published an analysis of the leaked data in September, concluding that the People’s Liberation Army (PLA) likely wants to take advantage of Russia’s recent experience launching successful air assaults on Ukraine by procuring equipment and training for a future amphibious assault on Taiwan.
Like CyberToufan, BlackMoon is ostensibly a ‘hacktivist’ operation, but with specific ideological goals that align them closely with the goals of a nation-state engaged in conflict (in this case, Ukraine and Ukrainian allies). They also exhibit a higher-than-usual level of sophistication and media savvy than most hacktivist operations, suggesting possible state-sponsorship.
New research and insights from SpyCloud
Our new research explores the YYlaiyu Phishing-as-a-Service (PhaaS) Panel, one of the dozens of Chinese-developed PhaaS kits used by financial fraud actors to target overseas users, primarily through smishing messages. In this blog, our team at SpyCloud Labs, in collaboration with the research team at urlscan, breaks down the YYlaiyu kit and the TTPs leveraged by many of these Chinese-language phishing operators to steal credit card information from victims around the globe.
How do we as defenders define “winning” when threat activity is so relentless? There are plenty of dark things lurking on the dark web, and it takes a certain kind of temperament to handle the ups and downs of fighting cybercrime.
Take a look at our conversation with three seasoned professionals at SpyCloud – Jason Lancaster, Tyson McAllister, and Duncan Edwards – and learn what keeps them going day after day in their pursuit of justice.
We like to share common passwords we’ve recaptured from breaches, successful phishes, and infostealer logs as a reminder for you to help users enforce good password hygiene. Because what’s easy for them to remember, is easy for threat actors to crack.
Power up your defenses by automatically blocking weak or banned user passwords, continuously monitor for newly exposed passwords, and automatically reset exposed passwords that could be an easy entry point for attackers to login to your systems.
Recaptured data numbers for October
October monthly total
Total New Recaptured Data Records for October
1,422,967,405
New third-party breach data this month
Third-Party Breaches Parsed and Ingested
988
New Data Records from Third-Party Breaches
910,099,238
New recaptured phished data this month
Phished Records
6,727,237
New infostealer malware data this month
Stealer Logs Parsed and Ingested
2,388,868
New Data Records from Stealer Infections
73,969,998
New Stolen Cookie Records
438,898,169
Stay in the loop
Our team at SpyCloud Labs keeps close tabs on the cybercrime ecosystem. Sign up to stay in the loop with our latest research.






