Two common methods criminals use to compromise users’ credentials and facilitate account takeovers are credential stuffing and password spraying. The two terms are sometimes used interchangeably, so let’s dig into the differences.
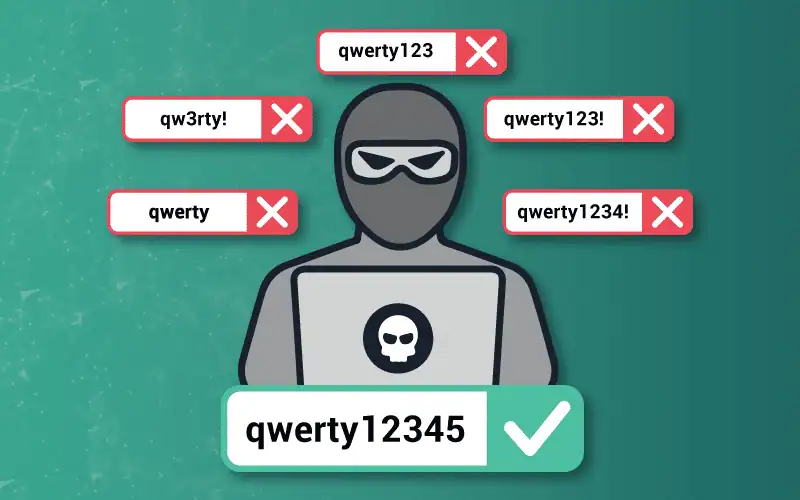
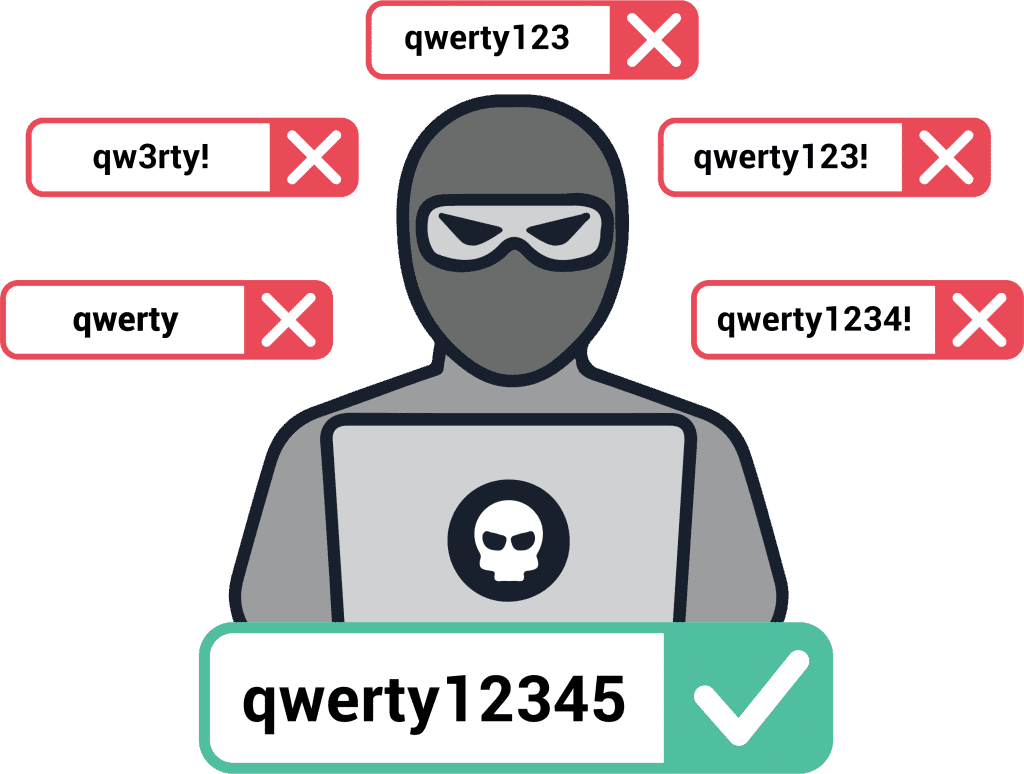
Credential stuffing is a type of brute-force attack that relies on automated tools to test large volumes of stolen usernames and passwords across multiple sites until one works. Credential stuffing preys upon two things:
- Many organizations still allow customers and employees to use password-only logins (without MFA).
- Users are so overwhelmed by the number of logins they have (upwards of 200 on average) that they resort to reusing passwords across multiple accounts.
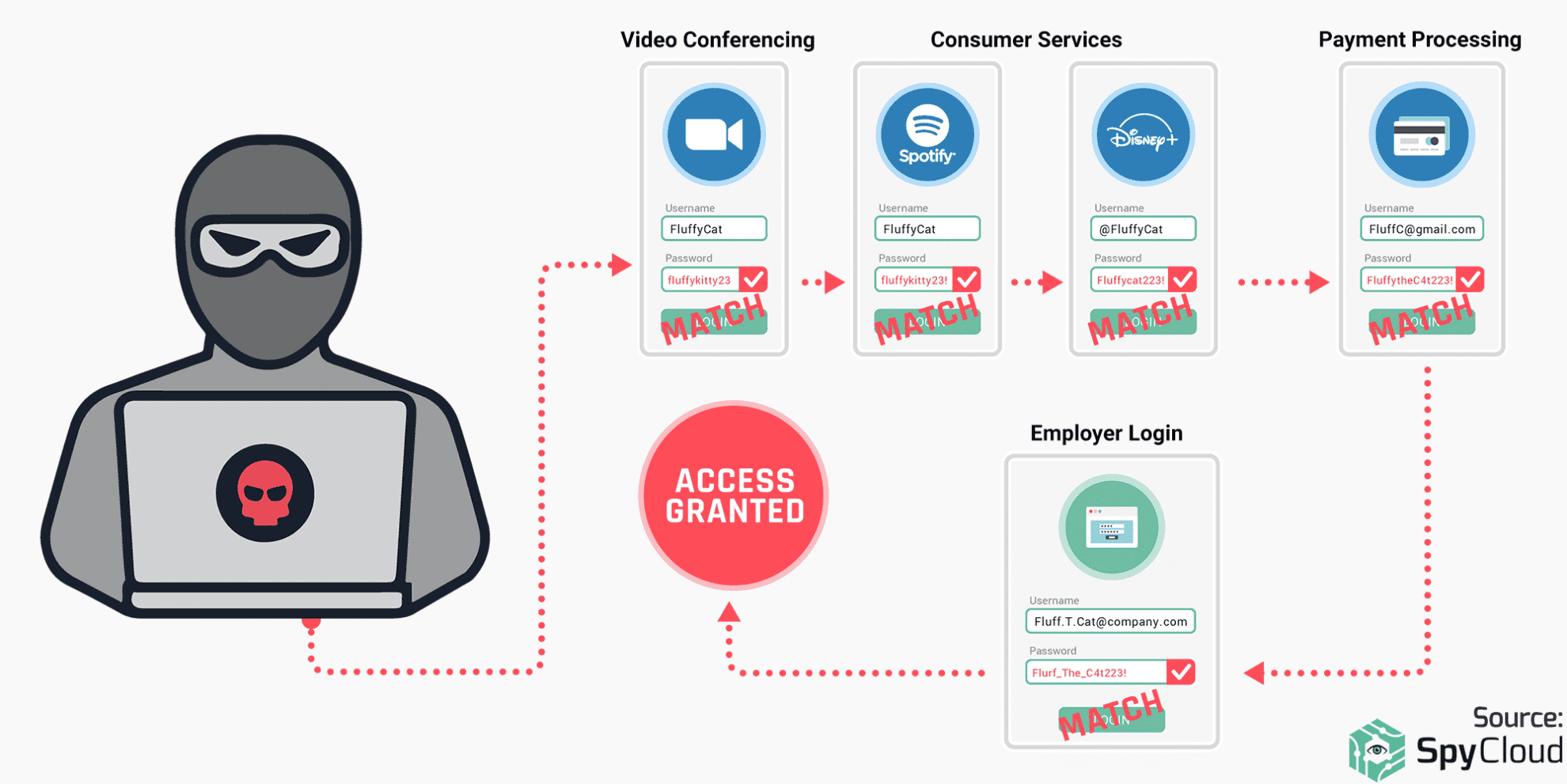
Credential stuffing is very popular among less experienced exploiters as they typically have little technical expertise and rely on easily downloadable account checker tools capable of testing large credential lists against various login portals to breach online services, systems, and networks.
In contrast, password spraying is an attack that attempts to access a large number of sites using known account identifiers (usernames) with a few commonly used passwords.
At first glance, you might question the efficacy of password spraying, but think of the many systems that rely on blocking accounts after ‘n’ failed login attempts but don’t actually prevent you from trying all known accounts with a single password, which can actually be the more successful given the larger the number of accounts involved.
In summary, while both methods can be extremely effective when it comes to account takeover, the key difference between the two is whether the password is known to be associated with the account or not. Both methods, however, can provide bad actors with illegitimate access to users’ accounts, leading to costly fraud and damage to your brand.
Many security leaders we talk to tell us their biggest blind spot is not knowing if employees are using compromised personal passwords across work accounts, so it’s something we’ve worked hard to solve for. SpyCloud Active Directory Guardian enables you to screen your AD accounts for any password that has ever appeared in SpyCloud’s breach database of billions of exposed passwords, and detect when employees select passwords that criminals are actively using in credential stuffing and password spraying attacks. You can not only check for exact user credential matches, but also fuzzy variations of those matches, alignment with NIST password guidelines, and more. The best part is you can remediate breached credentials with zero administrative effort.
Check your own personal account takeover exposure, and contact us for a demo of SpyCloud Active Directory Guardian