Recently, SpyCloud Labs researchers uncovered details about a cybercrime traffer team that is responsible for distributing various malware families to victims around the globe from June 2023 through early September 2023. This particular traffer team, with well over half a million infections globally, uses commodity software for tracking malware infections as well as commodity distribution services to spread their malware in campaigns.
In this blog, we’ll dig into our research on the traffer team, including the malware they used, team structure and roles, and other details we’ve analyzed relating to how the team deploys malware on a massive scale. Some details we discovered in our malware research have been censored to maintain our access to information.
Malware Traffer Team Structure
Traffers are organized cybercrime workers responsible for redirecting victims’ traffic to malicious content operated by others. The traffer team we highlight in this research is made up of at least five threat actors, nicknamed “Admin,” “Sleepy,” “Grumpy,” “Sleezey,” and “Dopey,” based on internal conversations analyzed by SpyCloud Labs. Sleepy, Grumpy, Sleezey, and Dopey appear to have been responsible for distributing the malware, with tasks like establishing sites for malicious ads, as well as making sure a certain threshold of victims were infected per day. Admin appears to be the one who procured the malware and sold the logs.
Team owner (Admin)
Based in Ukraine, “Admin” appears to have been in charge of the traffer team as a whole and carried out activities like procuring malware, finding and recruiting new teammates, checking on the status of campaigns, and more. Admin does not appear to fully speak or seemingly understand English, however, this actor used Google Translate to communicate with other actors on their team that do speak English. Based on internal communications analyzed by SpyCloud, Admin tasked other members of the team with creating multiple malware distribution domains, which all posed as cracked software distributions, with a goal of 15,000 victim clicks per day.
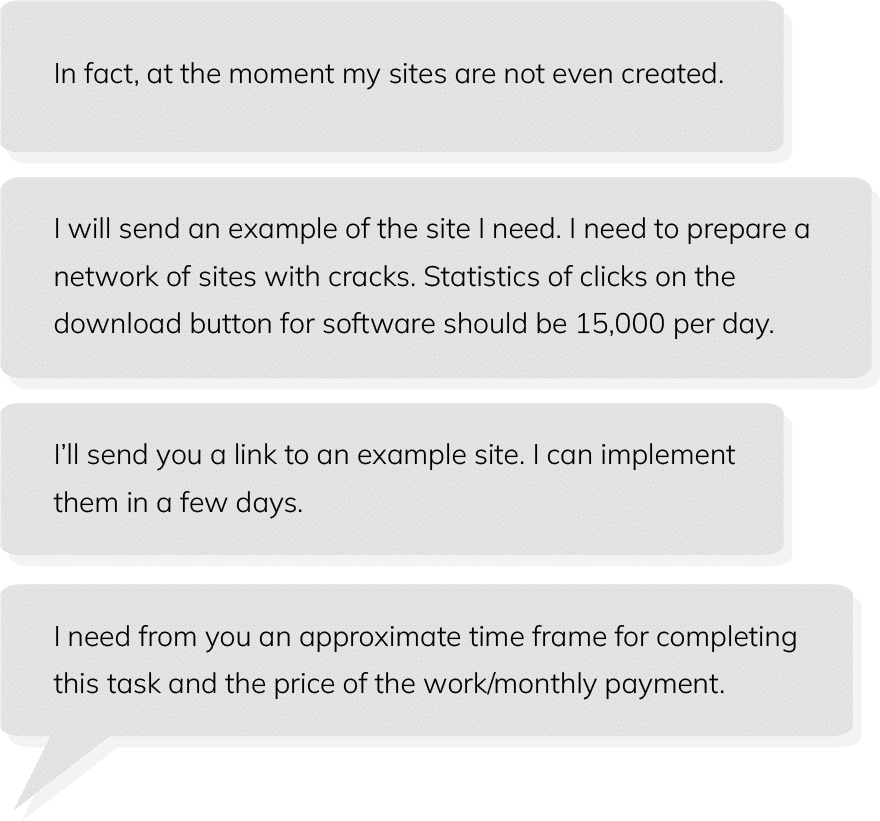
Image 1: Representation of communications from Admin, as observed by SpyCloud Labs.
Install team (The four dwarfs)
Sleepy
“Sleepy” was one of the traffer team members tasked by Admin to handle pay-per-install (PPI) distributions of the malware onto victims’ machines. Based on team communications obtained and analyzed by SpyCloud Labs, Sleepy was paid $10,000 USD for 6,000 installs maximum, averaging about $1.66 USD per install. However, based on additional internal conversations obtained by SpyCloud Labs, Admin was unhappy with the amount and quality of installs Sleepy was delivering and instead reached out to Sleepy’s peers to look for alternative solutions.
Grumpy
Grumpy, another PPI actor tasked with distributing the malware by Admin, and friends with Sleepy, was engaged by Admin when they became frustrated by the lack of Sleepy’s installs. Based on campaign spreadsheets obtained by SpyCloud Labs, it’s probable that Grumpy’s rates were $1.20 USD per install, which is notably lower than Sleepy’s rates, as shown here.
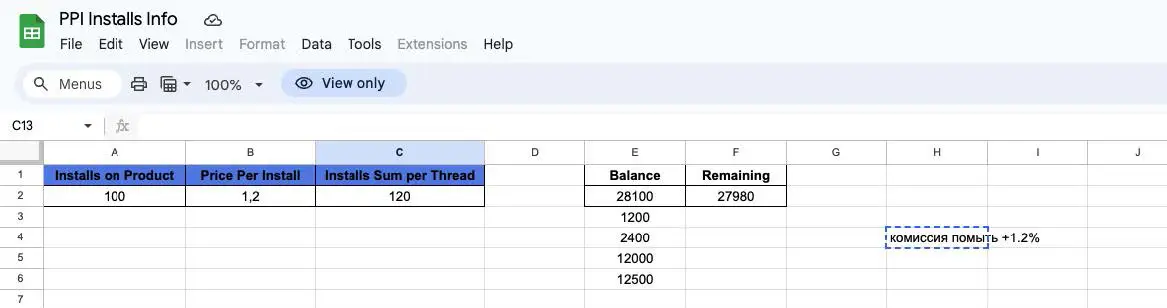
Image 2: A spreadsheet view containing info related to Grumpy’s installs, obtained through the SpyCloud Labs research team from the traffer team.
During internal conversations with Grumpy, Admin casually discussed that they were looking to expand their team to 56 members: 46 to create malicious websites each day and 10 to create content for the malicious websites. Admin asked Grumpy how much that would cost on average and what that would look like, outlining a minimum goal of at least 5,000 downloads per day.
Additional actors
There were additionally at least two other threat actors involved (Sleezey and Dopey); however, very little is known about their activities as SpyCloud Labs was unable to obtain the Google Sheets with campaign activities for these actors at the time of this publication.
Actors’ market and forum presence
Through continued SpyCloud Labs research, we uncovered a Telegram presence for this traffer team, in addition to a minimal forum presence.
Telegram
As observed below, the actors’ Telegram makes mention of the “Unique Installations” that they offer.
Image 3: Screenshot of one of the actors’ Telegram accounts.
SpyCloud Labs analysts found additional Telegram accounts associated with the traffer team; however, there were no interesting descriptions like we found with this first account.
XSS
As far as we can tell, the threat actors maintained a very minimal forum presence on XSS, using their XSS account to discuss their usage of one of the malware families they purchased, LummaC2, as observed in Image 4. This does not appear to be the forum where they sell their logs.
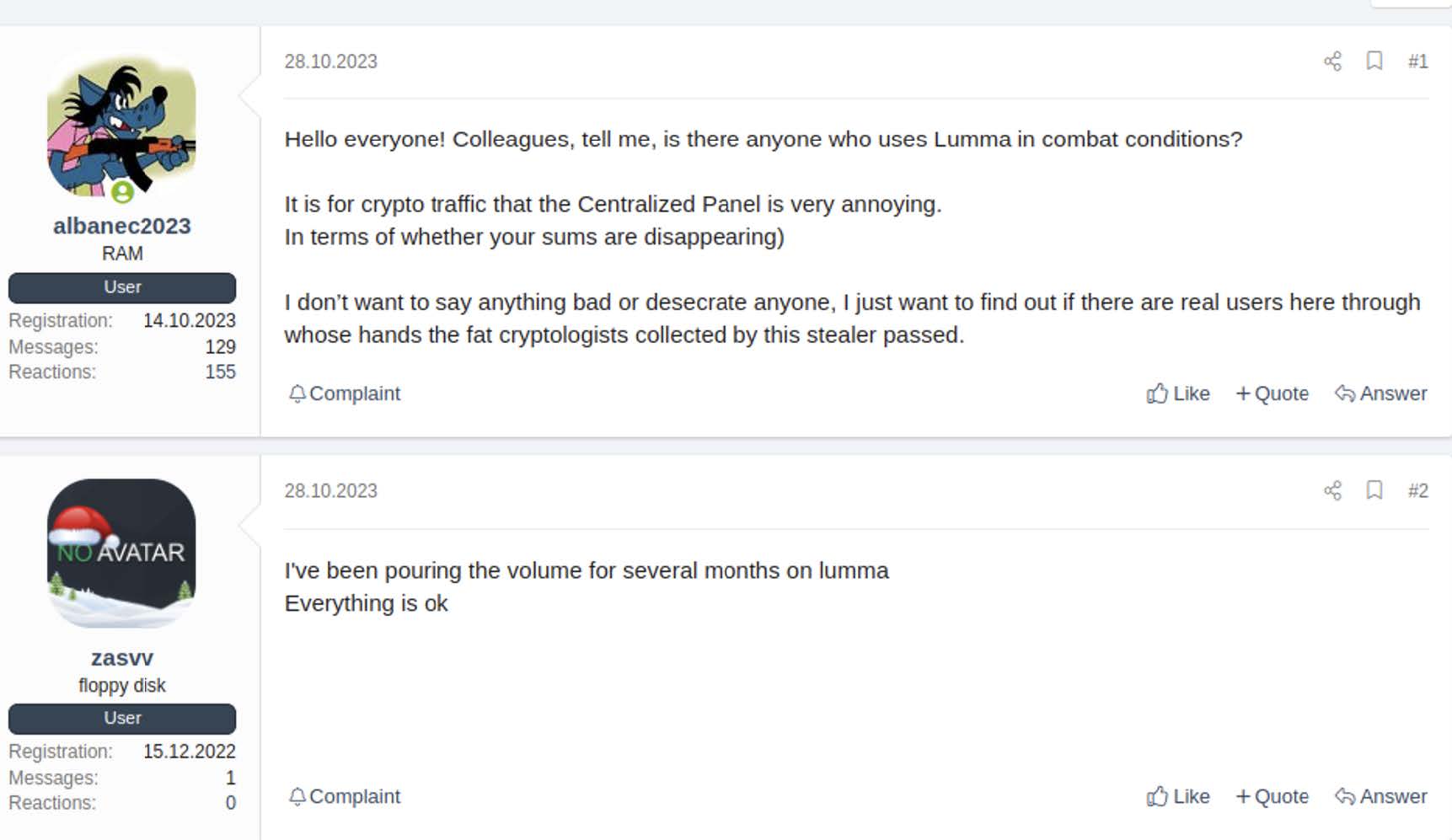
Image 4: Screenshots acquired by SpyCloud Labs of the actor “chizasvv” discussing their usage of LummaC2 on XSS.
Zelenka.guru
As observed in Image 5, the actors also maintained a fairly minimal forum presence on Zelenka.guru, with their only post being about troubleshooting a credential checker that they were using to validate credentials they stole.
Image 5: The actor “rage_installs” – associated with the traffer team – discussing their usage of credential checkers on zelenka.guru.
Malware families used by the traffer team
In our analysis, SpyCloud Labs was able to determine which specific malware families the traffer team used, including LummaC2, Vidar, Raccoon, StealC, and Lumar. From a review of the individual malware statistics panels for each account, and by analyzing malware logs recovered by SpyCloud Labs, we were also able to surface relevant statistics for some of these malware families, as outlined below.
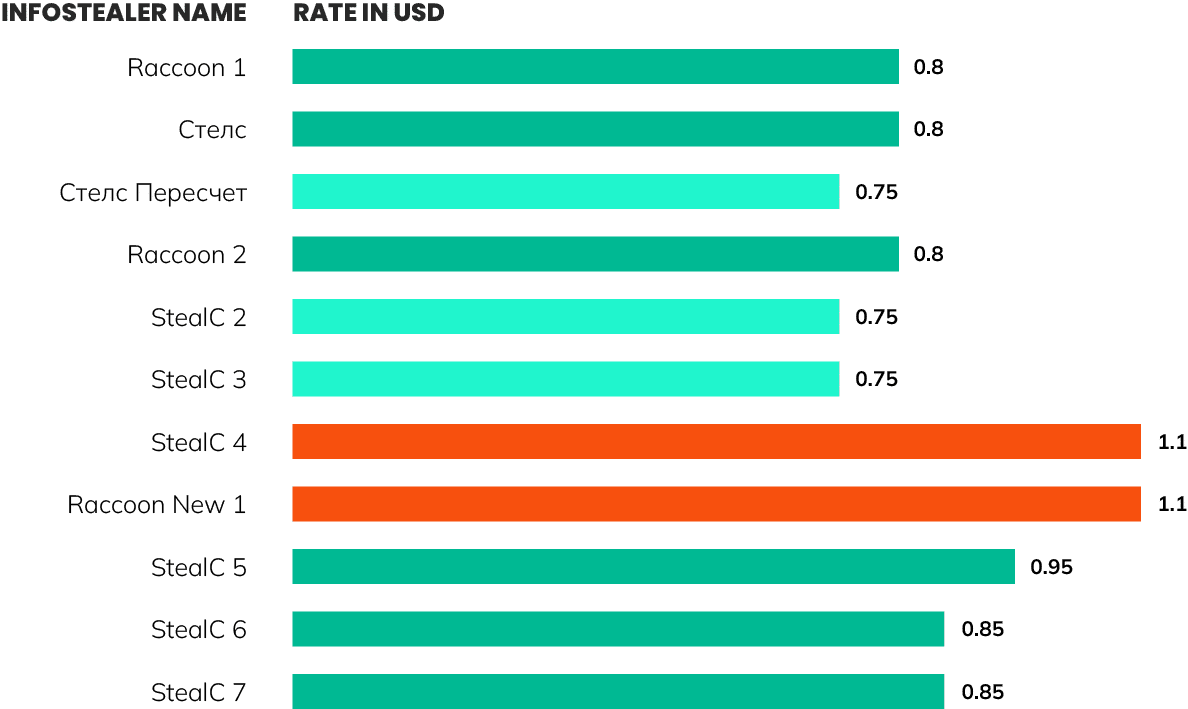
Graph showing the traffer team’s install prices for different malware families.
LummaC2
LummaC2 is an infostealer sold as Malware-as-a-Service (MaaS), with actors paying monthly for access to a control panel that provides the ability to build deployable versions of the malware, review infection statistics, export stolen information, and more. Using multiple individual LummaC2 accounts for distribution, the traffer team operated a LummaC2 bot to infect users. As observed in Image 4 above, one of their few XSS posts involved discussing their usage of LummaC2. Based on available data from our analysis of recovered malware logs, SpyCloud Labs believes these campaigns alone resulted in nearly half a million individual LummaC2 infections as of this writing.
Vidar
Vidar, another commonly used infostealer, is sold as MaaS, with actors paying monthly to be given access to the Vidar panel, which provides similar functions as LummaC2. Because Vidar makes its infection statistics panels public, SpyCloud Labs analysts were able to obtain a substantial amount of information relating to the actors’ various Vidar campaigns. These campaigns ran between June 29, 2023 and September 9, 2023, and resulted in approximately 23,000 infections globally. As observed in Image 6 and Image 7 below, the targeting regions were widespread across the world, with Russia noticeably absent.
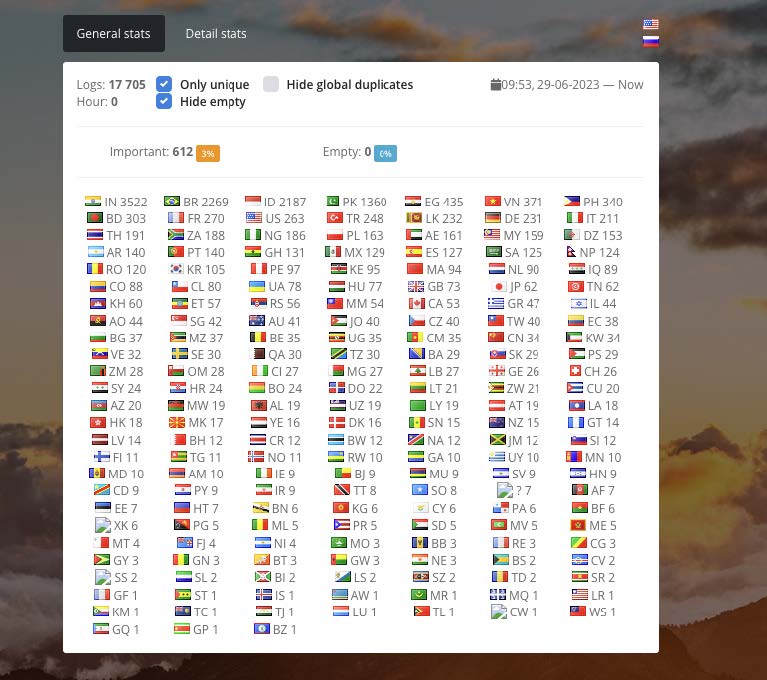
Image 6: The breakdown, by country, of Vidar infections associated with the traffer team.
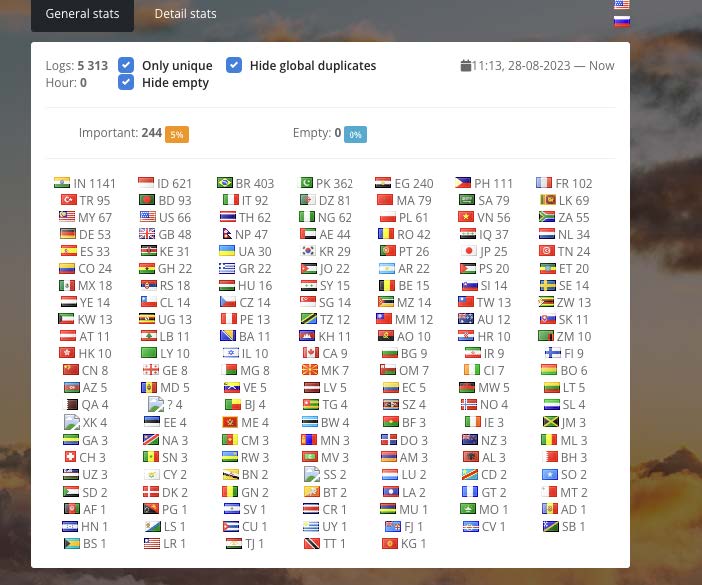
Image 7: The total breakdown, by country, of Vidar campaigns.
Raccoon
Raccoon, another fairly common infostealer that is sold as a service, was also used by the traffer team for malware infections. Raccoon also makes statistics public from its panel, so SpyCloud Labs was able to obtain statistics on infection counts. While the campaign date is unknown (most likely from June 2023 to September 2023, given these actors’ activity), the total infection count was around 78,000 infected victims based on the outputs from the rssrv Raccoon panel.

Image 8: One of the outputs from the rssrv Raccoon panel.
Additionally, based on a campaign spreadsheet obtained by SpyCloud Labs, the actors were paying between $0.80 and $1.10 USD per Raccoon install.
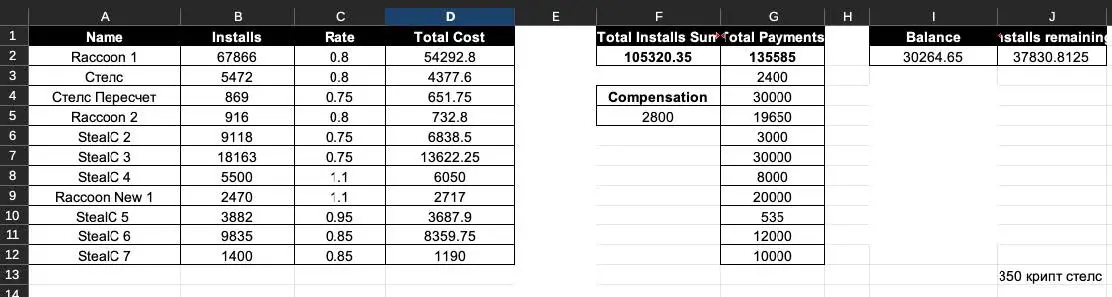
Image 9: A campaign spreadsheet used by the actors that accounts for ~70,000 of the Raccoon infections as well as StealC infections.
StealC
StealC, as described in public reporting as a “copycat of Vidar and Raccoon”, is another common infostealer that is sold as a service and was used by the traffer team for infections. While the stats panels for StealC were not accessible to SpyCloud Labs analysts, we were still able to get an estimate of infection counts for StealC using campaign spreadsheets. With the numbers in Image 9, the actors infected over 54,000 victims with StealC, paying between $0.75 and $1.10 USD per install. As shown in the campaign spreadsheet, the actors generated 350 crypts, or unique builds of the malware, that were modified to evade antivirus detection of StealC before they began distributing it.
Lumar
Yet another infostealer offered as a service and used by the traffer team for infections, Lumar did not have a public stats panel available, and there were no discussions or campaign spreadsheets made about the usages, so apart from confirming that the traffer team was indeed using Lumar for infections, SpyCloud Labs has no additional information for this malware family at the time of publishing.
Analyzing malware distribution methods
This traffer team paid several different services for malware installs, with a variety of successes.
Sleepy's service
This PPI service offered fairly high install rates and also was fairly unreliable, based on internal conversations obtained by SpyCloud Labs. The rates offered by this actor totaled to around $1.60 USD/install, although very rarely did the service deliver on installs, leading the traffer team to evaluate other options, including other services and even creating their own PPI network.
Grumpy’s service
Based on internal conversations obtained by SpyCloud Labs, following the disappointment with Sleepy’s service, the traffer team turned to Sleepy’s “friend”, Grumpy, to attempt to figure out how to trick more victims into installing their malware. During their conversation, Grumpy and Admin mentioned many interesting topics, such as Admin’s desire to expand their crew to 56 employees, Grumpy’s highly-ranked malicious websites, and a step-by-step guide on how to increase traffic to a malicious website, provided you have sufficient resources. Based on internal spreadsheets obtained by SpyCloud (as seen in Image 2 above), we can see that Grumpy was offering a rate of $1.20 USD/install, and that it is likely that this traffer team purchased at least 100 installs from them for a total of $120 USD.
InstallBank
An additional PPI network used by the traffer team, InstallBank, is a much larger operation with a publicly accessible homepage that explains their operation, as observed in Image 10 and Image 11.
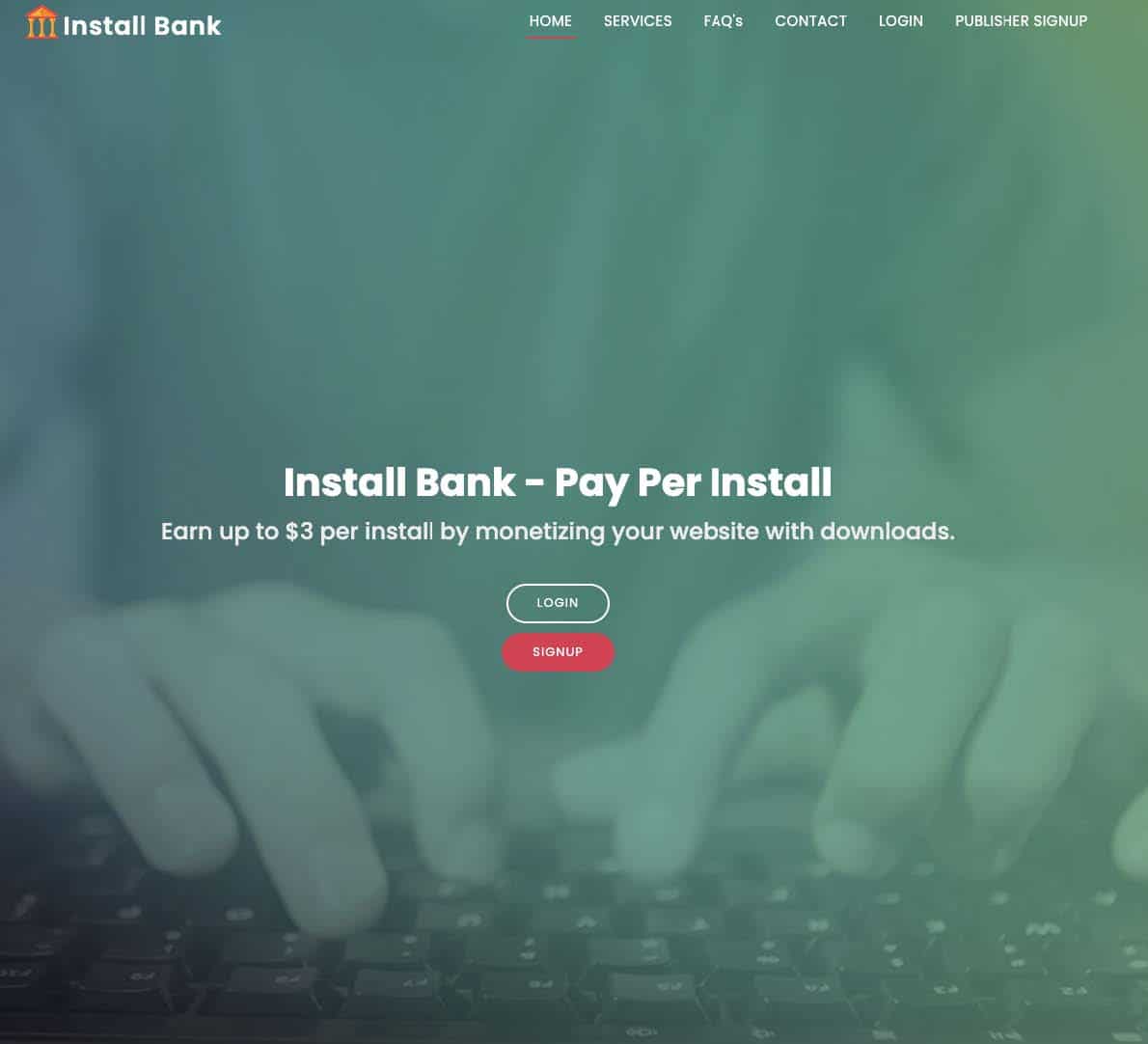
Image 10: The InstallBank homepage listing max payouts.
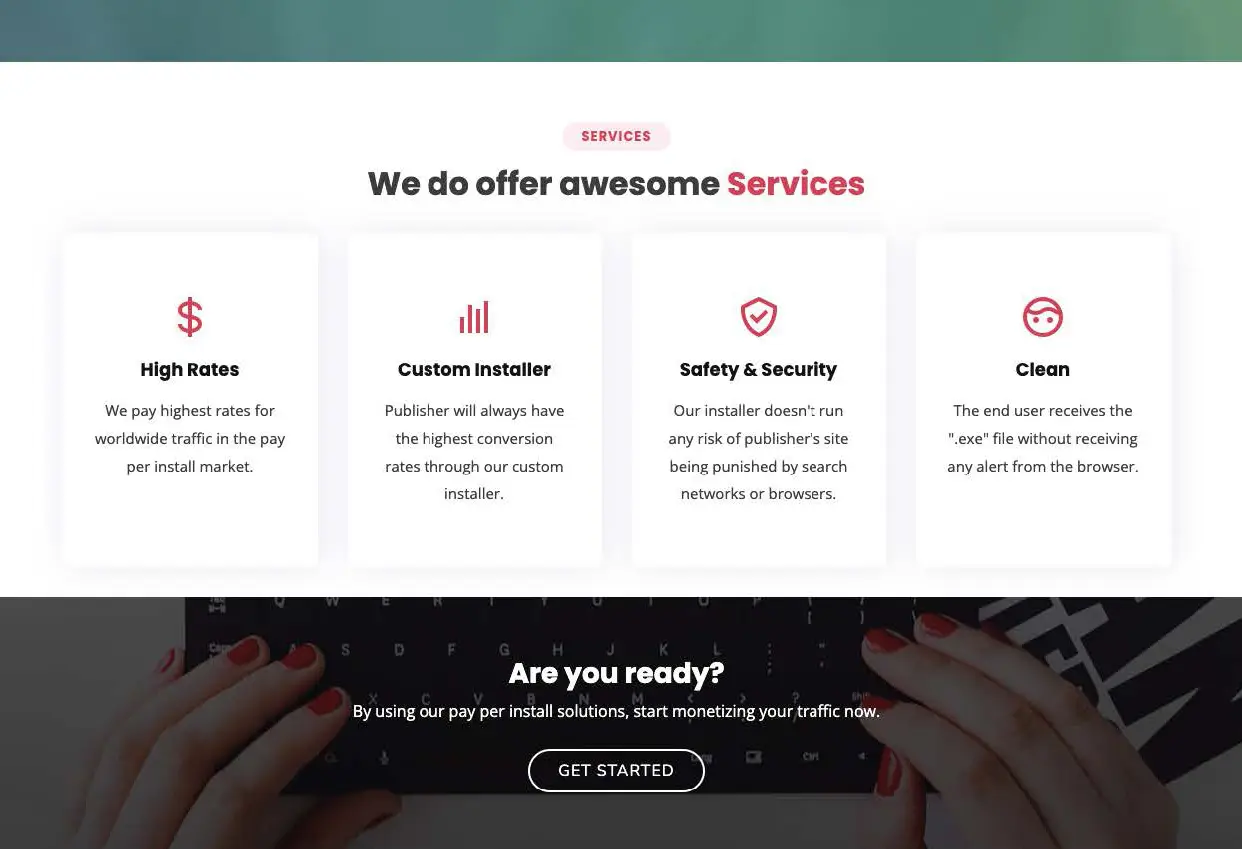
Image 11: Services offered by InstallBank.
Based on other internal conversations obtained by SpyCloud Labs, InstallBank’s price-per-install was at one point greater than $0.80 USD; however, this traffer team requested that InstallBank lower the price to right around that price point, and InstallBank appeared to respond in the affirmative to that proposal.
Based on infection traffic analyzed by SpyCloud Labs researchers, threat actors often use InstallBank distribution in conjunction with sites distributing cracked software. In this scheme, victims click a software download button on a site claiming to provide access to a sought-after program, and thereafter are redirected through a variety of websites (many ending in *.click or *.xyz), before eventually being presented with a file to download, which contains the malware.
Sehrish Hashmi/SpaxMedia
Another larger PPI network used by the traffer team, SpaxMedia, operated by the threat actor Sehrish Hashmi, offers “high-quality monetization to marketers,” and – based on internal communication analyzed by SpyCloud Labs – to this traffer team as well. As observed in Images 12 and 13, SpaxMedia’s website details its offerings:

Image 12: SpaxMedia homepage.

Image 13: List of SpaxMedia’s services.
Based on internal conversations obtained by SpyCloud Labs, Sehrish Hashmi/SpaxMedia offers install rates of as low as $0.90 USD/install.
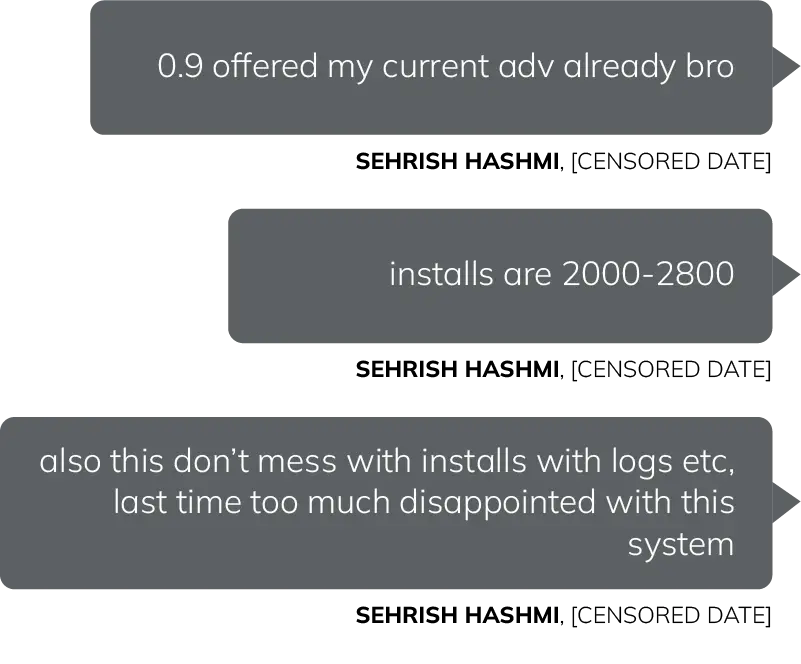
Image 14: Representation of communications from Sehrish Hashmi, as observed by SpyCloud Labs.
According to an analysis of infected traffic, when victims click cracked software download links that are linked up to SpaxMedia distribution, they are often redirected to .cfd websites before eventually being served the malware download.
Summary of research findings
Based on SpyCloud Labs research, due to the volume of infections and diversity in malware families being distributed, as well as the communications between team members and the degree to which individual campaigns were tracked, this traffer team appears to be well-established and highly successful.
While it was outside our scope in this blog to review potential follow-on attacks like ransomware that may have originated from infections by this team, the depth and breadth of infections identified in SpyCloud’s data and discussed here places the team in the higher echelons of traffer teams identified by SpyCloud Labs, and as a significant threat to the community at large.



