Here at SpyCloud, we’ve been busy expanding our collections of recaptured phished data, so we’re also exploring new insights we can find by looking at large datasets of successfully phished credentials.
In this blog, we dive into the Tycoon 2FA Phishing-as-a-Service (PhaaS) platform, a popular phishing tool used by bad actors to steal users’ email and cloud productivity portal credentials.
Specifically, we break down trends we observed by analyzing a dataset of successfully phished data stolen using Tycoon 2FA that SpyCloud recaptured over a six-week period, including targeted industries, geographic trends, and phished user behavior.
How does the Tycoon 2FA phishing service work?
Tycoon 2FA is a sophisticated PhaaS platform that has been active since August 2023. Tycoon specializes in bypassing multi-factor authentication (MFA) protections, particularly targeting Microsoft 365 and Gmail accounts.
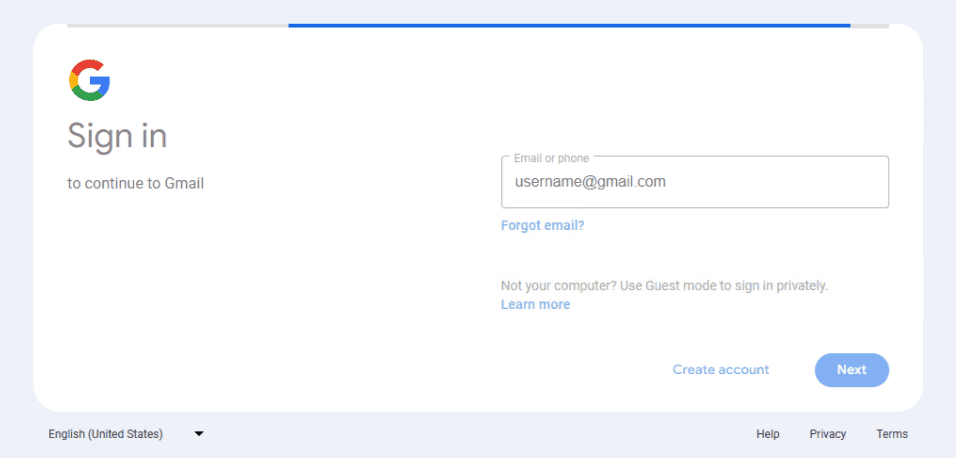
Tycoon phishing page impersonating a Gmail login page.
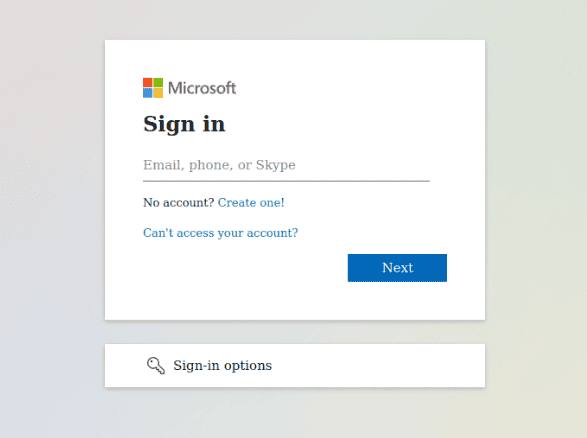
Tycoon phishing page impersonating a Gmail login page.
Instead of just targeting passwords like more traditional phishing kits, Tycoon also captures session cookies during the authentication process using an Adversary-in-the-Middle (AitM) technique.
Basically, Tycoon hosts a webpage that appears to the victim like their email and cloud services login page. After the victim inputs their credentials, Tycoon passes them to the legitimate website, relaying additional authentication steps like MFA back-and-forth between the phishing page and the legitimate service.
Once successful authentication has occurred, Tycoon captures the session cookie. These cookies can then be replayed, allowing attackers to access the account in the future without additional authentication checks.
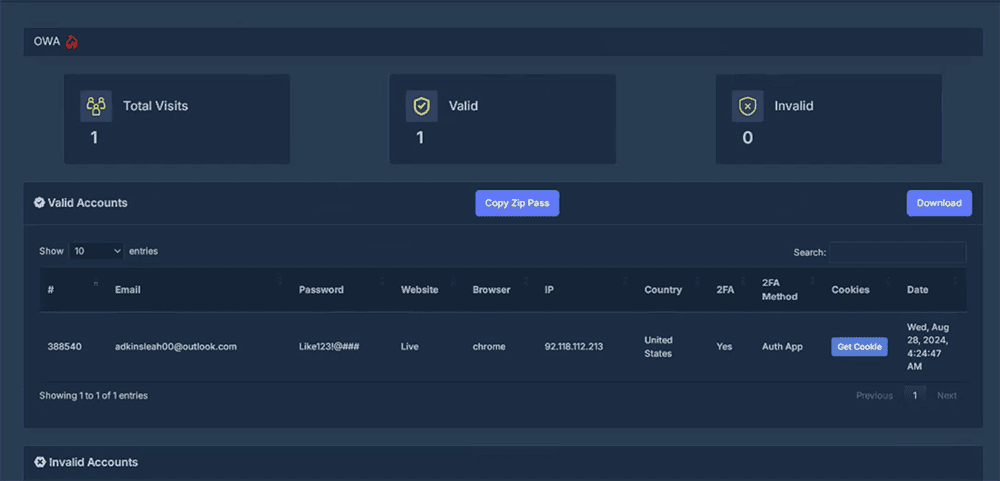
View of the Tycoon 2FA panel showing a phished OWA credential and a captured authentication cookie.
When the Tycoon 2FA PhaaS platform first surfaced, researchers at Sekoia noted its strong similarities with the Dadsec OTT phishing kit, speculating that Tycoon was likely created using the underlying source code from Dadsec. Since its first release in August 2023, Tycoon’s developers have made improvements to their code, adding features including code obfuscation and other anti-analysis techniques. Like many other AitM PhaaS kits, Tycoon uses CAPTCHA tests as an anti-bot measure to try and prevent the pages from being scraped by security researchers. The Tycoon 2FA kit is sold using a subscription model via the Telegram encrypted messaging service.
Tycoon 2FA victim trends and exposure insights
SpyCloud monitors active phishing campaigns, traces them back to phishing threat actor infrastructure, and recaptures successfully phished data, so that our customers can remediate their users’ exposure. This gives us a unique window into the phishing threat: we can analyze phishing actors, campaigns, and kits by looking at the data they were able to successfully phish from victims.
Example of a CAPTCHA gating access to a Tycoon 2FA phishing page.
In order to get a better sense of Tycoon’s victimology, we pulled a subset of credential data that was successfully phished using the Tycoon 2FA platform. We scoped this down to just the data that was recaptured by our team within a six-week timeframe, resulting in a dataset of 159,188 phished credentials.[1]
In addition to capturing valid session cookies, Tycoon collects the victim’s email address, password, browser, IP address, and the country where they are located, giving us more data points to analyze.
Geographic distribution
First, we looked at geographic locations for the victims. Unsurprisingly, most of the victims are concentrated in the United States: 54% of victims in our dataset are located in the US.
Since the data is so skewed towards the US, we used a logarithmic scale to visualize the data in a choropleth map, allowing us to see which other countries are most affected by Tycoon 2FA. The country with the second-highest number of Tycoon victims is the United Kingdom, followed by Canada, India, Australia, France, and Germany.
Overall, this geographic data highlights Tycoon 2FA’s heavy focus on users from English-speaking countries.
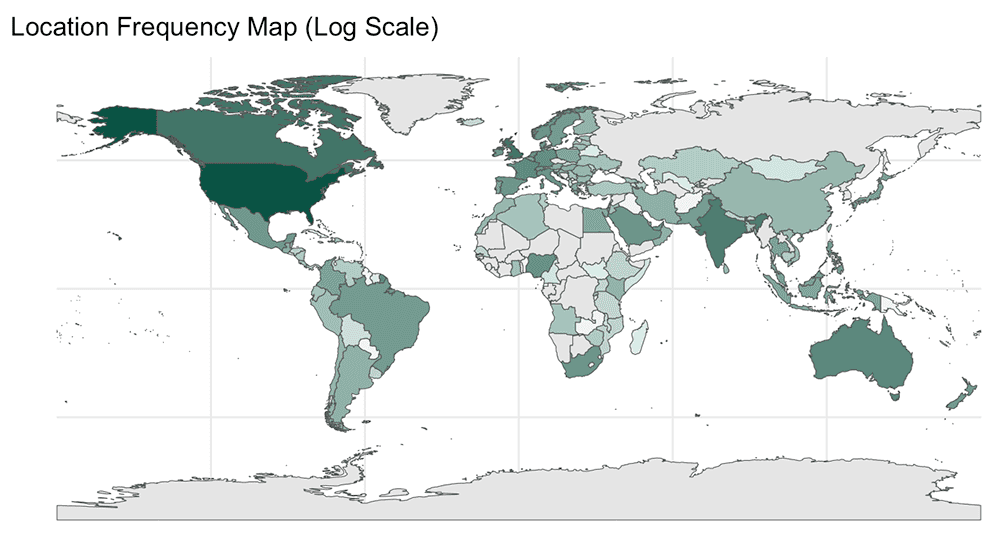
Chloropleth map showing countries with victims most affected by Tycoon 2FA phishing campaigns.
Login reattempts
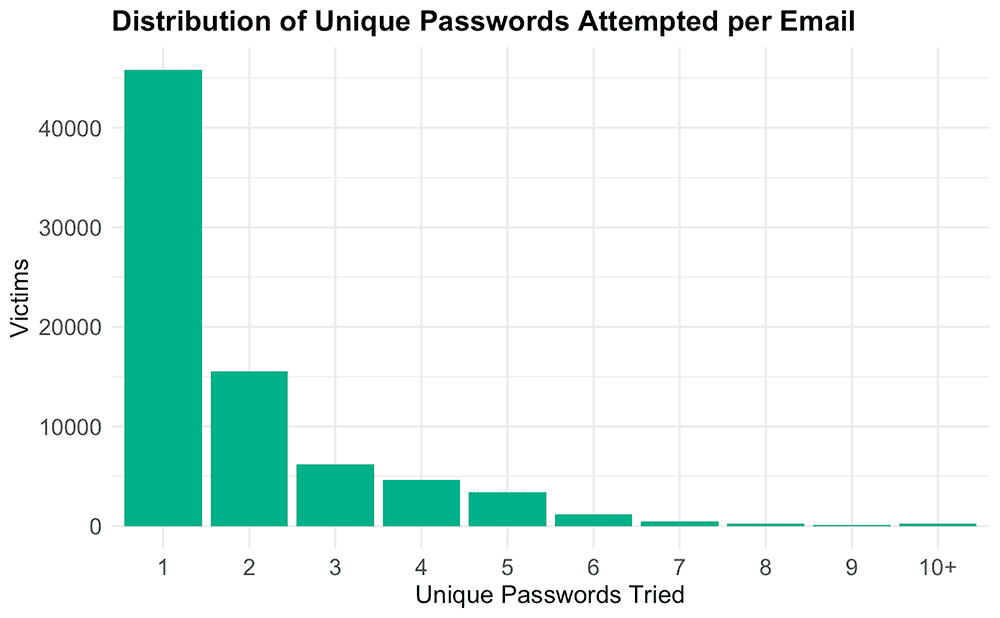
Next, we looked at login reattempts. Often when viewing successfully phished data, we will observe the same user try multiple different passwords in an attempt to login to the service that the phishing page is impersonating, thinking that they might have misremembered or mistyped their password the first time. Individuals often reuse only a few different passwords for all of their accounts, meaning that with each failed reattempt to login to the phishing page, a victim is potentially exposing a valid password that they use for other accounts.
To analyze login reattempts, we counted how many unique password values were present for each unique email address. We found that 41% of phished users attempted to use more than one unique password to log in to the Tycoon 2FA phishing page, potentially indicating that users believed they may have used the wrong password and tried another historical password to log in to their account.
This attempted login activity is significant as even historical passwords make up a part of a users’ holistic identity, and can be used by threat actors in a variety of ways to expand their scope of access.
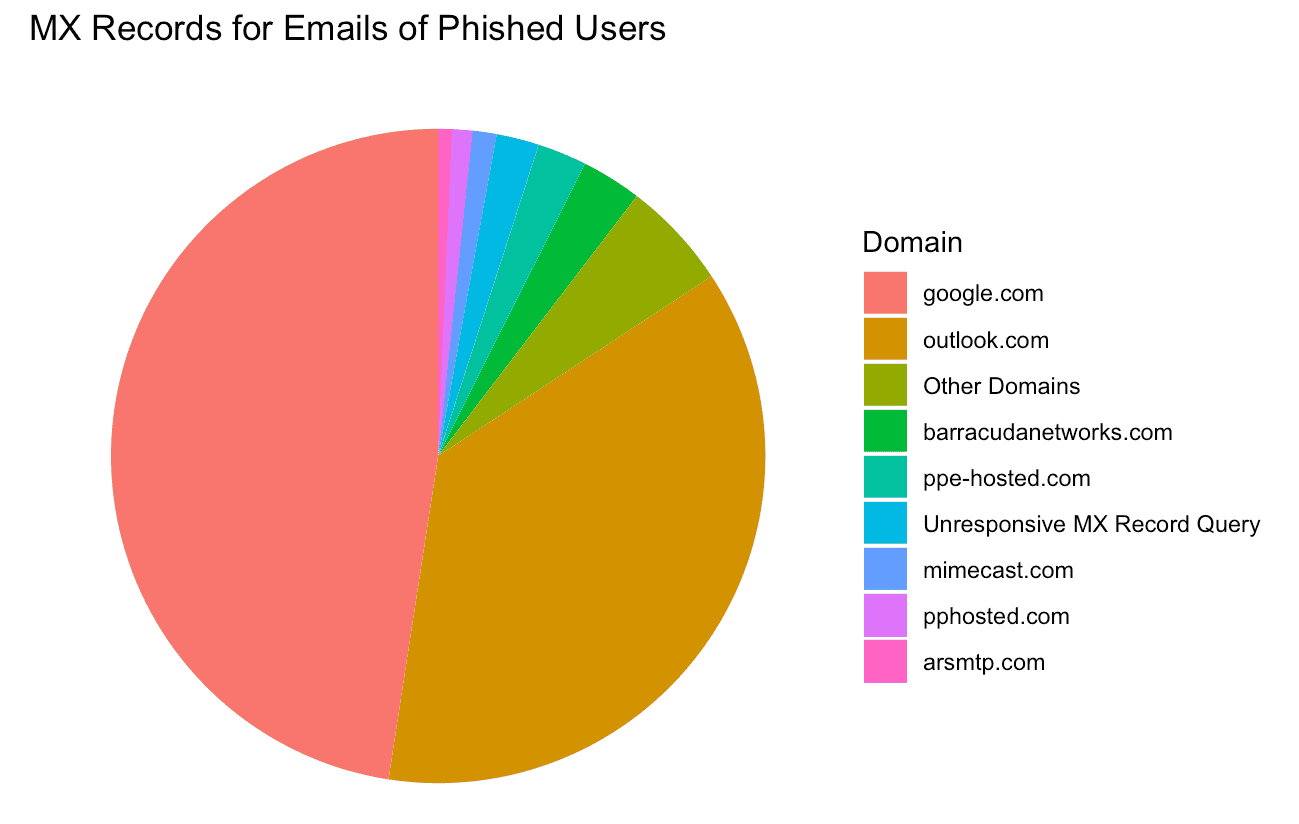
Mail services
Because Tycoon 2FA phishing pages impersonate webmail logins for Google and Microsoft 365, we also looked at the mail services each of the victims used. To find this data, we took the email domains from each phished user and queried the mail exchange (MX) records for those domains. Then, we counted the number of phished records associated with each base MX domain. As expected, almost all of the victim email addresses tie back to Outlook or Google webmail services: 48% for Google and 37% for Outlook.
All of the other top domains (domains with over 1,000 records in this dataset), appear to be for email filtering security services used to filter out spam and phishing emails. This doesn’t necessarily mean that these domains aren’t also using Google or Outlook as their email provider. It just means these organizations are using an additional service provider to filter out undesired emails before they get to users’ inboxes, meaning we can’t determine the underlying webmail provider by simply querying the MX record.
Because most of the Tycoon phishing lures are distributed via email, the presence of these domains in our dataset of successfully phished user credentials likely means that these records represent instances where Tycoon 2FA lures successfully evaded detection by email filtering security services.
Targeted industries
Finally, we took a look at targeted industries. Unlike some phishing kits that have a variety of phishing pages impersonating different major global brands, Tycoon 2FA only has pages that impersonate a few popular webmail service providers. Therefore, you either need email lure data or successfully phished victim data to understand which industries are most targeted by Tycoon.
In order to understand which industries were most represented in our data, we first had to classify domains into corresponding industry verticals:
- Using the Tranco List[2] of the 1 million most popular websites, we narrowed the list of unique phished domains from 42,301 down to the 4,784 that matched both lists.
- We then fed that list into Claude 3.7-Sonnet and requested it return information about each company, based on the domain name, which included information about industry and company size.
- Additionally, we classified some of the most popular free consumer webmail domains like gmail.com, icloud.com, yahoo.com, and outlook.com into their own “consumer webmail” category.
While this still left quite a few domains that we couldn’t classify into an industry vertical, we were still able to determine some general trends.
The majority of identified email domains in our compromised credentials matched the consumer webmail category, meaning that these credentials belong to individuals’ personal email accounts. Of all the email records in our dataset, 28% matched our shortlist of 33 popular free consumer email domains.
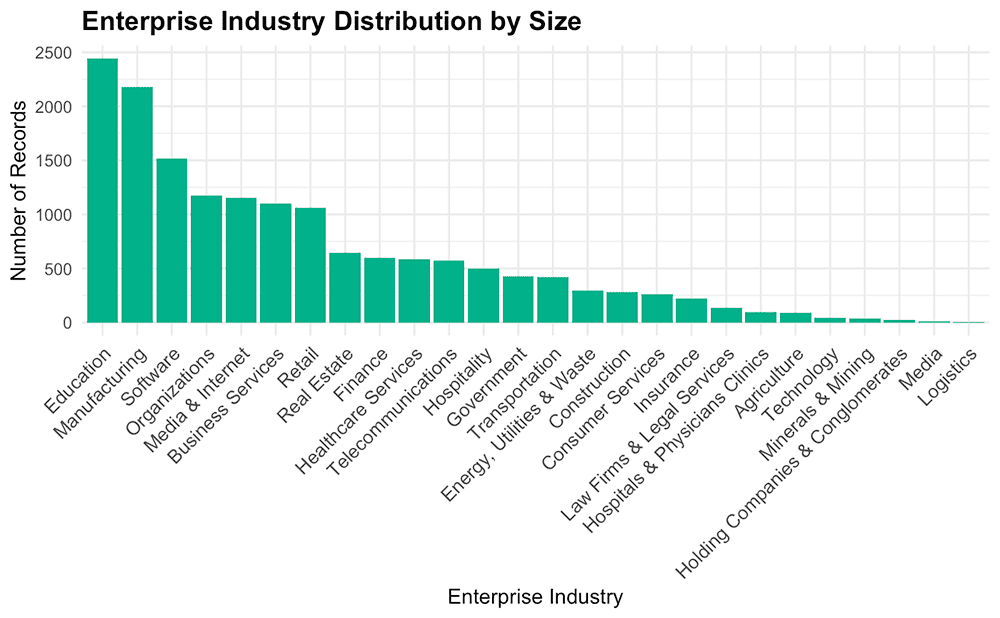
When we zoom in on just the identified email domains that were classified into industry verticals, you can see the top sectors that we observe being phished by Tycoon 2FA: education, manufacturing, software, organizations (including nonprofits, NGOs, and religious organizations), media & internet, business services, and retail.
Key takeaways for defenders
Tycoon 2FA is a sophisticated PhaaS platform that specializes in stealing users’ email and cloud productivity portal credentials and bypassing multi-factor authentication (MFA) protections. Defenders should be aware that:
- From our dataset of credentials that were successfully phished by Tycoon 2FA, we can see that Tycoon primarily targets users in English-speaking countries who use Google or Outlook for their email services. We also found thousands of successfully phished records that appear to belong to users whose emails sit behind popular email filtering security services.
- In our analysis, we observed that 41% of successfully phished users attempt more than one unique password when entering their login information into the Tycoon 2FA phishing page, potentially feeding bad actors more password data to leverage for unauthorized access.
- Within this sample of data, we identified certain industry verticals being phished more so than others, including the education, manufacturing, and software sectors.
Tycoon’s capabilities are a great reminder that MFA – while an important security mechanism – is not failproof.
How SpyCloud helps
At SpyCloud, we specialize in recapturing stolen data from phishing campaigns, malware infections, and third-party breaches to empower organizations with proactive defense levers. Phishing remains one of the most pervasive cyber threats to businesses, but understanding its mechanics can help your team neutralize its impacts. By adopting SpyCloud as part of your security strategy, you can reduce your exposure to identity-based attacks that use phished data.
SpyCloud is at the forefront of phishing mitigation, helping enterprises prevent costly follow-on attacks.
[1] The time cutoffs for this dataset were determined by the dates that SpyCloud collected this data and not necessarily the dates that the data was phished using Tycoon 2FA. This means that our dataset contains both historically phished data that we discovered and collected more recently, as well as newly phished data that was phished within the last six weeks.
[2] Victor Le Pochat, Tom Van Goethem, Samaneh Tajalizadehkhoob, Maciej Korczyński, and Wouter Joosen. 2019. “Tranco: A Research-Oriented Top Sites Ranking Hardened Against Manipulation,” Proceedings of the 26th Annual Network and Distributed System Security Symposium (NDSS 2019). https://doi.org/10.14722/ndss.2019.23386