USE CASE: THREAT ACTOR ATTRIBUTION
IDENTIFY THREAT ACTORS
with Holistic Identity Correlation
Unmask threat actors with SpyCloud + IDLink™
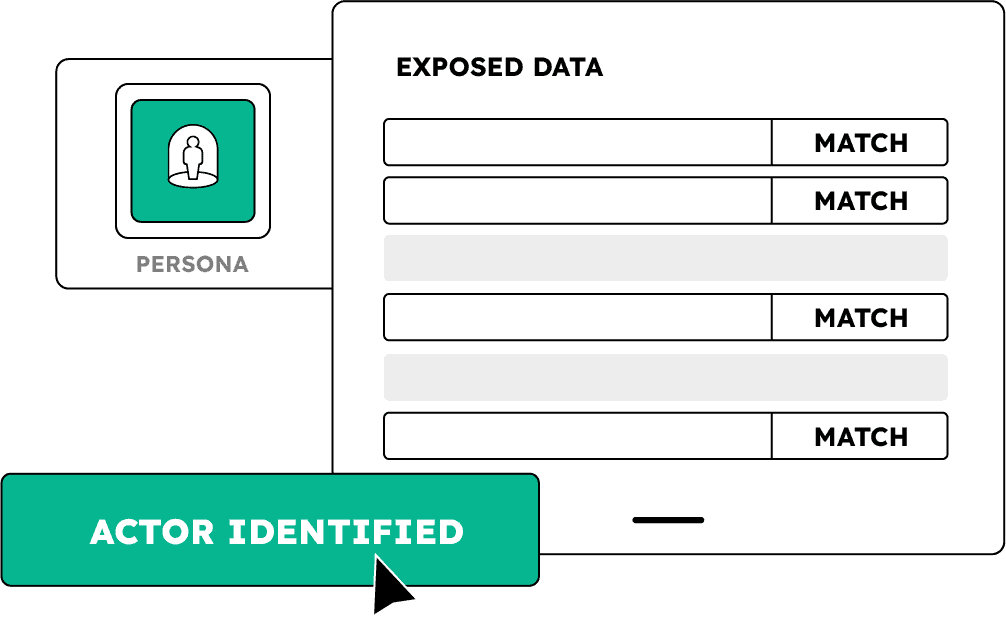
Begin with any selector – an email, IP, username, or password – and let IDLink trace connections across SpyCloud’s high-efficacy datasets
Turn raw exposure data into holistic, enriched profiles of criminal actors, campaigns, and infrastructure – empowering more analysts to contribute to attribution workflows
Use IDLink to correlate disparate identity fragments – even across TOR, VPNs, or aliases – to reconstruct threat actor personas and expose previously invisible overlaps
EXPLORE PRODUCTS
EXPLORE WHO USES SPYCLOUD
Defenders
we help
SpyCloud powers attribution workflows for teams working to reveal the criminals behind cybercrime – with holistic identity intelligence.
Threat intelligence analysts
Cybercrime units & law enforcement
NEED EXPERT HELP?
We offer analyst services & training
SpyCloud analysts offer tailored methodology training on how to use recaptured digital exhaust for effective pattern-of-life analysis and rapid identification of threat actors.
Integrations






Next steps
Turn digital exhaust into accurate attribution