Identity is the new battleground
Attackers weaponize massive troves of stolen identities exposed on the dark web that your defenses can’t see. SpyCloud pierces those blind spots by illuminating hidden exposures across employees, contractors, customers, and even non-human accounts. With automated remediation, security teams can neutralize these threats in minutes, shrinking the attack surface before damage is done.
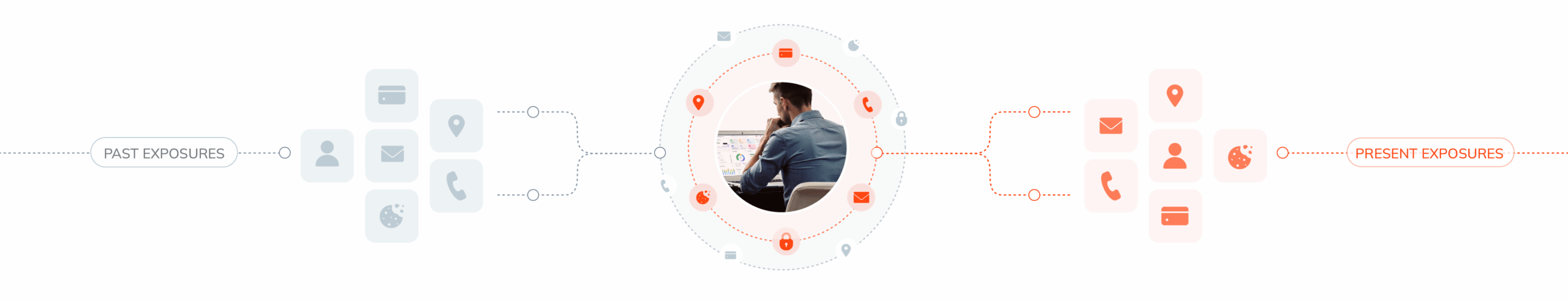
Identity security is at a breaking point – inaction is not an option
The attack surface now includes every user and identity, overwhelming even the most sophisticated defenders.
Employees, contractors, customers, and even non-human identities are tied to multiple accounts, cloud services, and SaaS apps – each one correlated to dozens of unique usernames and email addresses, hundreds of passwords, and potentially thousands of session cookies exposed on the dark web.
Identity data exposed in breaches, malware infections, phishing attacks, and recirculated in combolists becomes fuel for attackers, and creates failure points for defenders if not properly and proactively remediated.
Without a better way of operating, businesses face inevitable and costly consequences.
Financial
Stolen identities fuel fraud, ransomware, and supply chain attacks – costing businesses millions of dollars. Recovery takes years.
Reputational
Regulatory fines, lawsuits, and customer exodus cripple brands. Once you’re known for a breach, you never fully recover.
Operational
Identity-driven attacks don’t just disrupt operations. Persistent access means criminals stay inside your network, silently siphoning data and dismantling your defenses from within.
No more feeds – identity security requires a new mindset
The old paradigm of reactive, account-by-account defense and overreliance on threat intelligence can’t keep up. More data feeds and stale credential lists only add noise without solving the problem.
Winning teams are embracing a new proactive approach called holistic identity threat protection.
This new approach requires understanding the full scope of users’ darknet exposure – all the correlated data associated with corporate, supplier, contractor, and consumer identities across their current and past online personas.
It also means changing how security teams respond – moving away from slow, manual processes to automated, accelerated remediation so this knowledge of more exposures won’t slow you down.
The way to beat the odds is to make the shift now.
| OLD WAY | NEW WAY |
|---|---|
| ❌ Ingest another feed that adds noise and false positives | ✅ Rely on actionable exposed data that indicates an immediate identity threat |
| ❌ Treat each user account as an isolated perimeter | ✅ View identities holistically – as interconnected data points that attackers exploit across platforms |
| ❌ Monitor for leaked credentials and force password resets | ✅ Prevent the use of exposed passwords tied to past, present, professional and personal accounts |
| ❌ React to credential leaks after they’re found on dark web marketplaces | ✅ Remediate identity exposures – including stolen session cookies – before they’re weaponized |
| ❌ Force password resets for vulnerable corporate accounts | ✅ Correlate personal and corporate identity risks to prevent unseen threats |
| ❌ Rely on SIEM alerts and endpoint security to detect threats | ✅ Leverage recaptured darknet data to see exposures traditional tools can’t detect |
| ❌ Investigate ATO, fraud and ransomware attacks after they happen | ✅ Prevents attacks by cutting off access to compromised identities before criminals use them |
Adopt a holistic identity threat protection approach
1. See what criminals see
2. Share findings across teams
3. Act before the damage is done
Uncover, understand, and end identity threats
SpyCloud delivers the entire breadth of exposed identities so you understand how criminals view your organization and what’s making you a target – and eliminates the problem automatically.
SpyCloud has pioneered the holistic identity threat protection approach that illuminates previously hidden identity exposures across breaches, malware infections, and successful phishes – giving you the most comprehensive visibility into stolen identity data.
SpyCloud’s holistic identity matching yields 12-14x more exposed data versus traditional methods, linking dozens to hundreds of usernames, email addresses, passwords, IP addresses and other critical PII to reveal the full extent of user exposure that threatens your security.
By shifting to this broader view, you can identify unseen risk – from reused or recycled passwords to infected home systems accessing work applications.
Automatically remediate identity threats in real-time, giving you the speed and scale to protect your business from ATO, fraud, and ransomware.
Easy to deploy and use, SpyCloud was purpose-built to help you know more, but do less. SpyCloud integrates with your existing security tools (EDR, IdP, SIEM, SOAR) and consumer-facing applications to automate password resets, enhanced authentication, session terminations, and other identity risk mitigations before attackers cause harm.



ENTERPRISE PROTECTION
Safeguard employee identities
Secure employee's identities – protect, prevent, and remediate compromised credentials and malware-infected users to reduce your attack surface
CONSUMER PROTECTION
Protect consumer identities
Preserve consumer account integrity and protect your brand – combat account takeover and unauthorized access to reduce risk of monetary loss
INVESTIGATIONS
Connect identity assets
You can’t defend what you can’t see.
SpyCloud illuminates identity risks other miss – giving you clarity and control to stop cybercrimes before they happen.
Ready to step out of the dark? Let’s talk.