USE CASE: POST-INFECTION MALWARE REMEDIATION
Neutralize INFOSTEALER Malware Threats
Reimaging an infected device isn’t enough. Infostealer malware captures credentials and session cookies, giving attackers access to your systems. SpyCloud shows you exactly what was stolen from infected devices and enables automated remediation steps to revoke access, reset application credentials, and invalidate session cookies to eliminate post-infection risk.
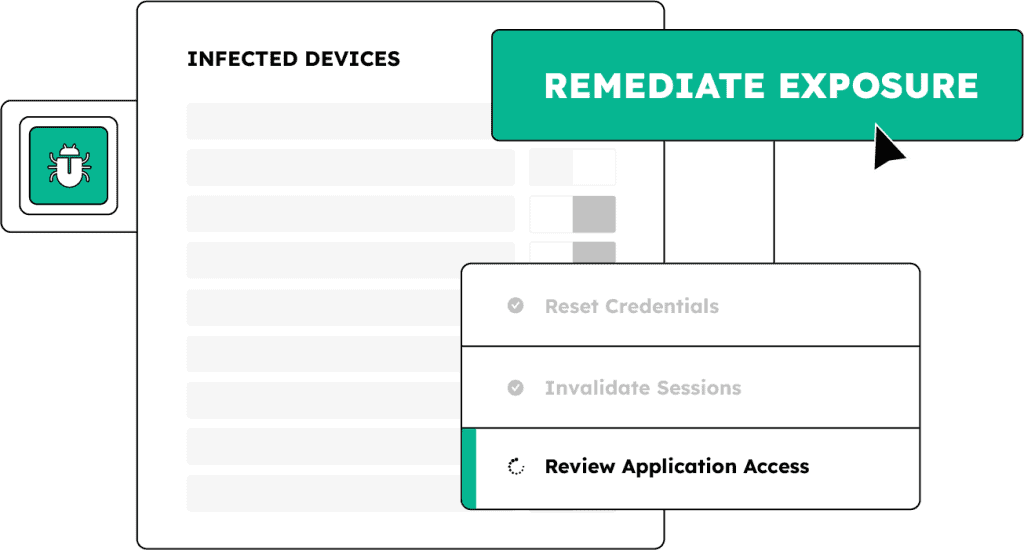
A more complete malware response workflow with SpyCloud
SpyCloud helps SOC and IR teams uncover the full impact of infostealer infections, even on unmanaged devices like contractors’ laptops. With SpyCloud’s comprehensive exposure data, you can act quickly and decisively to shut down every entry point to reduce ransomware risk and streamline response.
EXPLORE MORE PRODUCTS
Illuminate the infection – and erase the exposure with SpyCloud
EXPLORE WHO USES SPYCLOUD
Defenders
we help
CISOs
Enhance resilience to malware-based threats without expanding headcount or overhauling infrastructure
Integrations






Next steps
Turn infected devices into dead ends for attackers