Using the YYlaiyu Phishing Panel to Understand the Massive Chinese Phishing Ecosystem Fueling Global Financial Fraud
Over the past few years, we’ve seen an explosion in Chinese-language phishing actors targeting Western victims with smishing (phishing via text message). These actors typically use smishing over iMessage and RCS to distribute lures and cash out by committing financial fraud against their phished victims. Chinese-language criminal phishers have innovated some novel techniques both to send smishing messages and to cash out that have allowed them to be successful.
In this blog, our team at SpyCloud Labs, in collaboration with the research team at urlscan, breaks down the YYlaiyu Phishing-as-a-Service (PhaaS) Panel, one of the dozens of Chinese-developed PhaaS kits used by financial fraud actors to target overseas users, including Westerners.
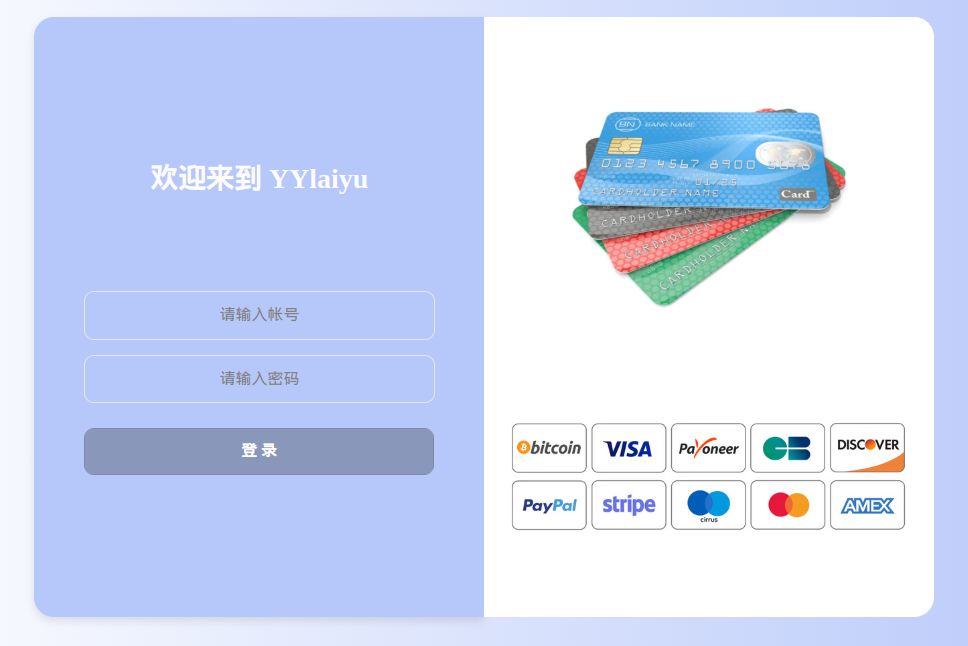
YYlaiyu logon page
Overview of Chinese smishing actors targeting Western users
Beginning around 2023, Chinese-language criminal phishing actors began aggressively targeting Western users with an onslaught of “missing package” smishing messages impersonating a variety of overseas postal service shipping brands. Popular campaign themes have continued to evolve over time. Another very popular lure used by these actors are the fake “toll violation” messages, in which the actors impersonate local or regional toll road authorities.
The actors conducting these campaigns are not all part of the same organized group, but are part of the same larger subculture with their own influencers, communications channels, marketplaces, and trends. Actors within this subculture also include a range of different service providers that specialize in different aspects of the phishing process, like sending text message lures, developing phishing kits, cashing out using mobile wallets, teaching others how to successfully phish, and managing online phishing communities and marketplaces.
Innovations in two key areas in particular have allowed these smishing operations to thrive:
01
The use of RCS and iMessage to send out encrypted messages in bulk. Phishers might operate their own setups, usually involving setting up physical mobile devices on racks and using automation to send RCS or iMessage lures in bulk. Alternatively, there is a range of underground bulk messaging service providers that will handle sending these messages for you. Researchers from Resecurity noted that many of these bulk messaging providers operate in a grey area, presenting themselves as digital marketing companies while also clearly advertising their services in communities focused on spam, fraud, and phishing.
The use of these encrypted messaging protocols also makes it more difficult for telecom operators to address the threat using traditional spam filtering methods. This is because iMessage and RCS allow for end-to-end encrypted messages; telecom operators generally can’t see the content of the messages, making it more difficult for them to detect and stop spam.
02
The use of novel cash-out methods, most of which revolve around loading payment information into mobile digital wallet applications. After loading the stolen card information into digital wallets, these actors have a variety of methods to monetize the cards including making fraudulent transactions using threat actor controlled POS terminals, purchasing gift cards for luxury companies for resale, relaying the NFC traffic to other phones using the “ghost tap” method, or simply selling phones that have been loaded up with stolen card data.
While many of these groups appear to have had success with mobile payment cash out methods, they don’t appear to exclusively cash out this way. One particularly interesting new cashout method – “ramp and dump” – involves phishing users for login credentials to popular brokerage services and using them to purchase positions in stocks that the threat actors own. This drives up the value of that stock, allowing the threat actors to “dump” their shares at an artificially inflated price.
A range of phishing kits – many of which share similar features, interfaces, and templates – are also bought and sold in marketplaces frequented by these actors. Without going into too much detail, some additional popular Chinese PhaaS panels that security researchers have previously shed light on include:
- Darcula/Magic Cat: The Darcula kit is particularly notable because of a new feature they deployed to allow phishers to use generative AI to rapidly generate new phishing templates impersonating whatever brand they want and in any language.
- Lighthouse: The Lighthouse kit has been used to distribute fake toll violation lures as well as impersonating ecommerce and banking brands.
- Haozi/Magic Mouse: The Haozi kit boasts an extremely plug-and-play setup and robust customer support, allowing phishers to conduct campaigns with little-to-no technical knowledge.
- Lucid: Researchers noted that this panel had robust role-based permission settings, allowing phishers to differentiate “between administrators, employees, and guest users.”
YYlaiyu phishing pages
We have observed examples of YYlaiyu phishing pages in the wild since at least September 2024. Like many of the Chinese-developed PhaaS setups, YYlaiyu appears to have templates for a wide variety of different brands, most of which mirror broader trends among Chinese-language smishing activity.
For example, the YYlaiyu kit has some of the “classics,” including shipping companies like DHL, DPD, and FedEx. We have also observed pages phishing credentials for popular cryptocurrency platforms, like Coinbase.
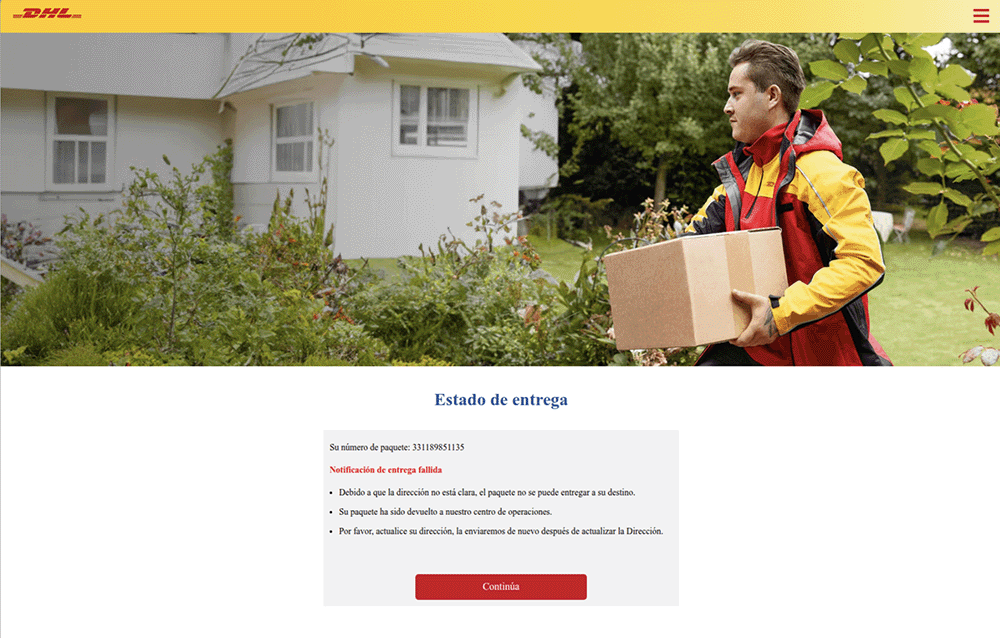
Starting around March 2025, we also started to see this kit apparently offer more bespoke brand templates to its subscribers, including: All Nippon Airways (a major Japanese airline), TikTok, Keeta (a food delivery service), and Qantas (a major Australian airline).
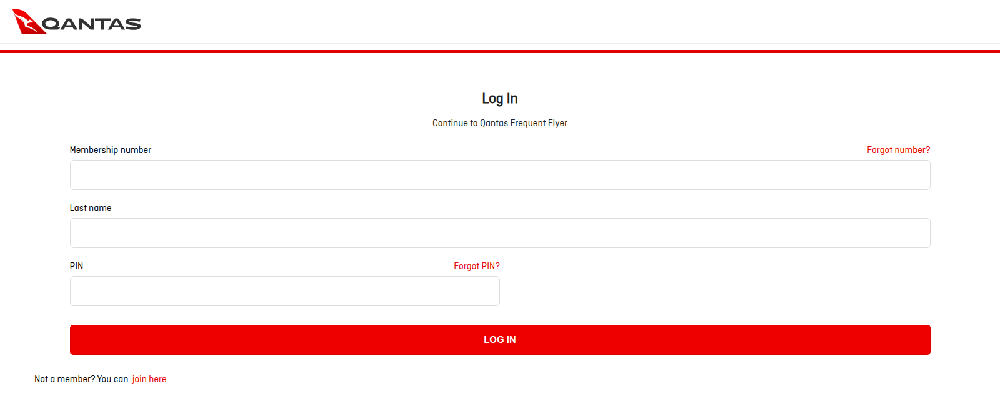
YYlaiyu phishing page impersonating the Qantas airline.
Starting around May 2025, we also began to see heavy deployment of brand templates impersonating investment platforms. These include both Western investment platforms like Fidelity and Schwab, as well as East Asian investment platforms such as Tiger Brokers (a Singaporean trading application), and Futu NiuNiu (a trading platform based in Hong Kong). This demonstrates that these actors are not exclusively focused on financial fraud targeting Western users.
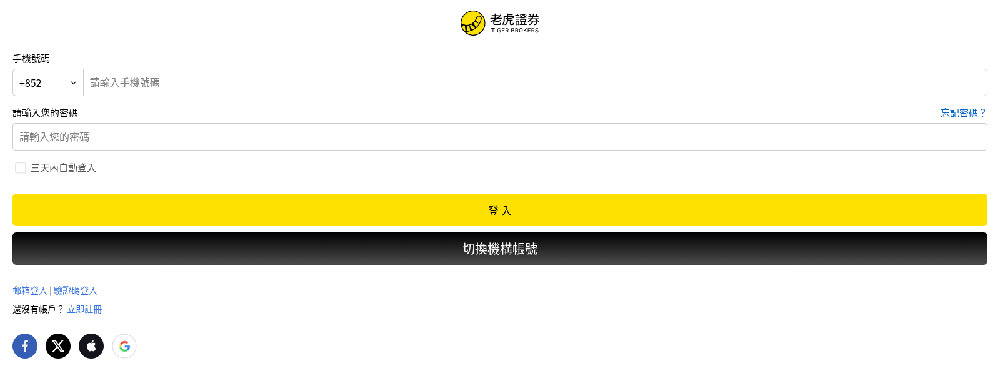
YYlaiyu phishing page impersonating Tiger Brokers, a Singaporean investment platform. The phone number field has auto-populated the +852 country code, which is used for Hong Kong mobile phone numbers.
The YYlaiyu panel
Panel operators can control these phishing pages via the YYlaiyu PhaaS panel. The easy-to-use panel bears many similarities to some of the other Chinese-developed PhaaS offerings that we highlighted above. It also includes more than 90 custom phishing page templates impersonating different brands and an integration with Alibaba that enables phishers to register and manage new domains without ever leaving the panel.
YYlaiyu meaning
The panel is branded with the name YYlaiyu (also spelled YY来鱼). YY is Chinese slang for fantasizing about or desiring, sometimes in a sexually perverse way. It’s derived from the words 意淫 (yì yín). 来鱼 (lái yú) means the act of fishing, or going fishing. So the entire phrase YYlaiyu roughly translates to erotic fantasizing about catching fish.
YYlaiyu panel layout
The YYlaiyu panel itself offers a range of different features for standing up and administering phishing pages. The panel has seven different tabs, including:
Card Information: This tab displays a spreadsheet view of phished credit card information. This shows that the kit supports capturing OTP card verification codes. The operating user column appears to display which panel operator is controlling each victim’s phishing session, and the operational control tab appears to display options for those panel operators to interact with the sessions in-real-time.
Like many of these kits, the YYlaiyu kit has an interactive phishing flow; it alerts operators when one of their pages has a visitor and they can make manual decisions about what to display to the user based on their input, like prompting them for an OTP code.
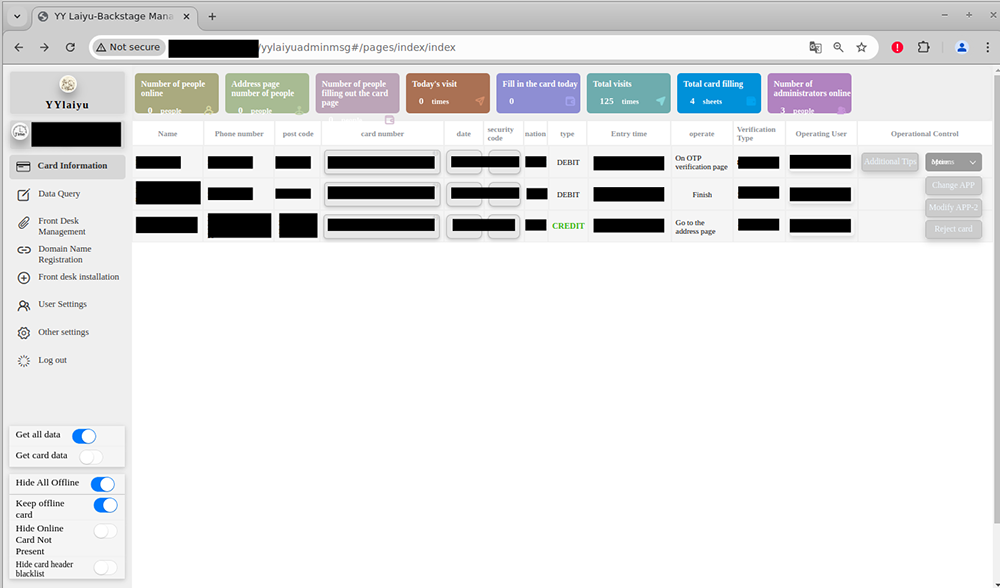
The Card Information tab in the YYlaiyu panel
Data Query: This tab allows phishers to query their successfully phished data – they can filter based on criteria like datetime, domain, card number, and whether or not the phished data contains a credit card number.
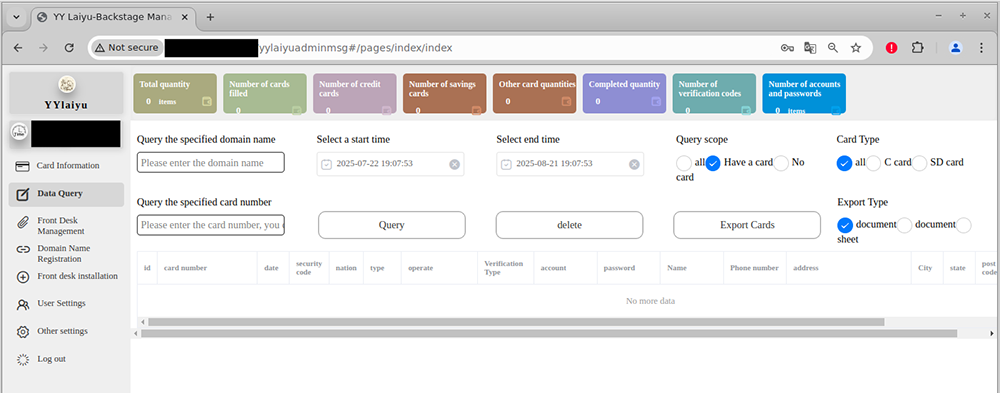
The Data Query tab in the YYlaiyu panel
Front Desk Management: This tab allows phishers to view and edit their active phishing pages as well as add new phishing domains and generate short links for their existing pages. Administrators can assign settings to their pages (such as setting them to filter traffic to mobile-only visitors); they can also temporarily disable their phishing pages when the panel is unattended, so potential victims don’t submit their data while no phishing operators are there to receive and operationalize it.
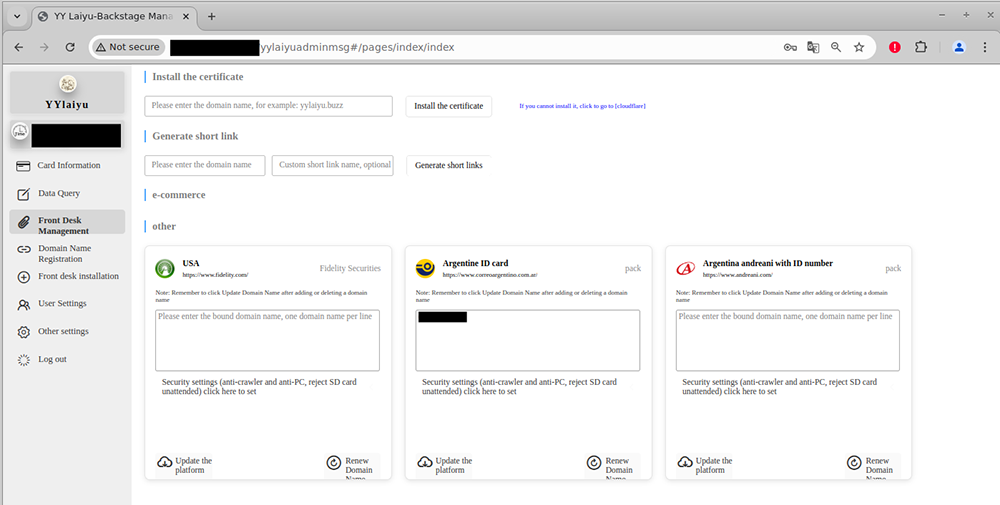
The Front Desk Management tab in the YYlaiyu panel
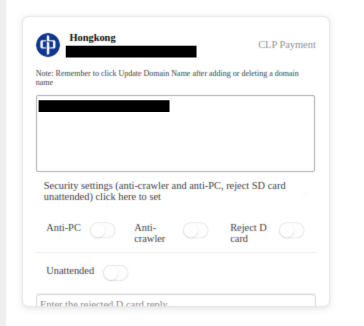
Example of an individual deployed site showing the configuration options. The partly-rendered message at the bottom is “Enter the rejected D card reply.”

Example of an “unattended” phishing page displaying the text {“message”:”Under maintenance and upgrade…”}
Domain Name Registration: This tab is integrated with Alibaba and allows phishers to register and manage new domains for their phishing pages using Alibaba’s domain registration service.
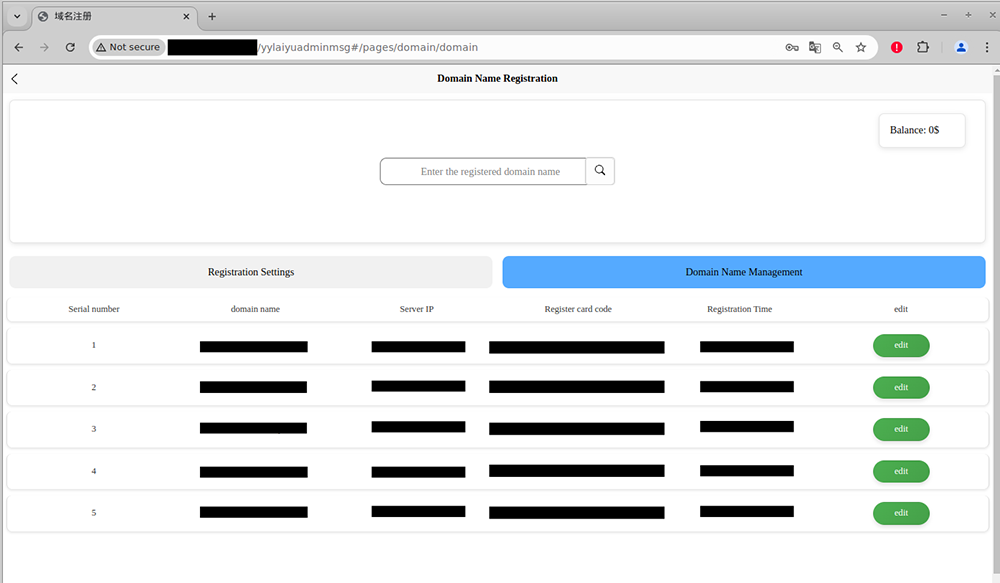
Domain Name Registration in the YYlaiyu panel
Front Desk Installation: This tab lists all of YYlaiyu’s custom templates, allowing phishers to deploy pages impersonating over 90 distinct brands. The page lists all of their template options with the associated country, domain of the impersonated website, and an additional descriptor (this sometimes appears to just contain the brand name, but other times it has a more general descriptor like “Fuel card points” or “Toll 2”).
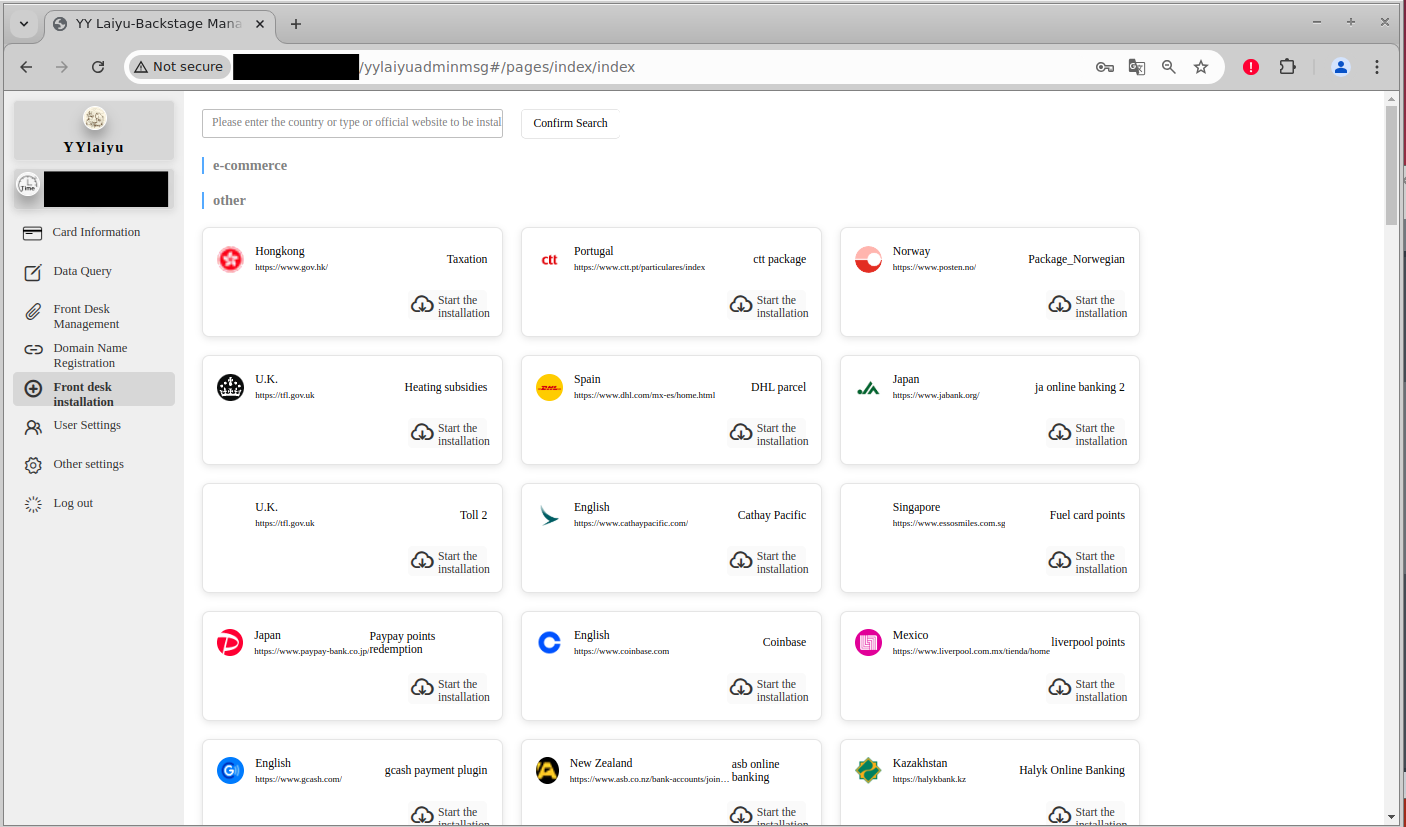
Front Desk Installation in the YYlaiyu panel
User Settings: This tab allows panel administrators to create new operator users and assign them permissions. User permissions get pretty granular here, including allowing administrators to designate which tabs users are allowed to access.
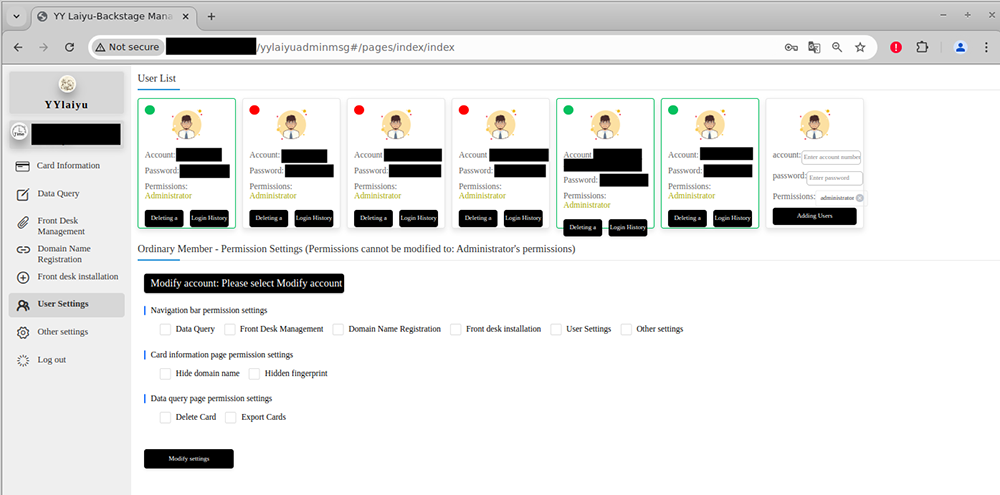
User Settings in the YYlaiyu panel
Other Settings: This tab has options to either blacklist or highlight certain types of cards according to their bin number. It also allows administrators to blacklist certain countries.
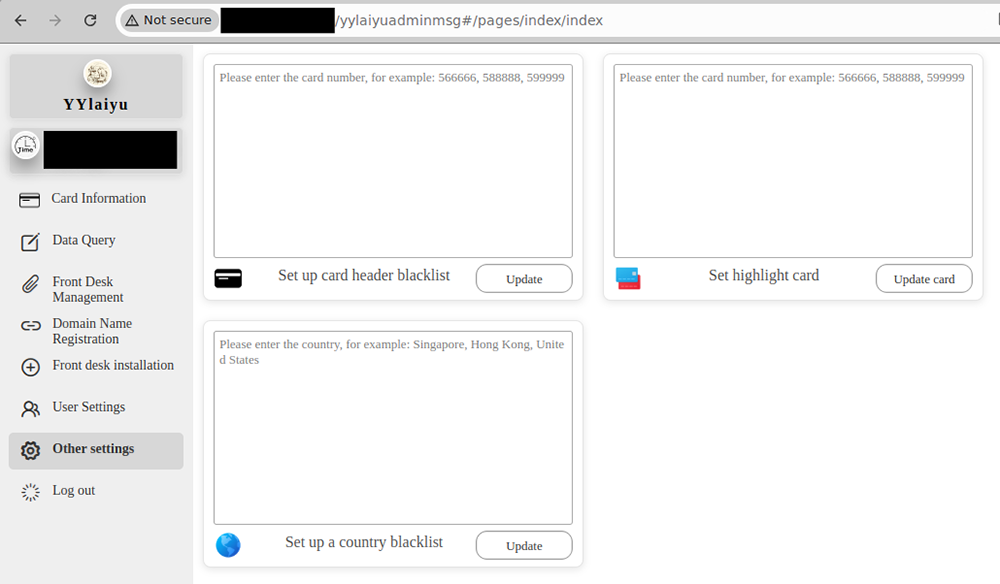
Other Settings in the YYlaiyu panel
There also appears to be numerous HTTP API endpoints that can be used to interface with the YYlaiyu panel. These API endpoints appear to have essentially the same functionality as the panel itself. Some interesting endpoints include:
- /dataexportall – This returns a ZIP file containing successfully phished data captured by the panel.
- /getweball – This returns a JSON containing all the available brand templates that the YYlaiyu panel has available. For a sample output from this command, see the Appendix. For some reason, the command /sousuogetweball also appears to return the same data.
- /getinstallweb – This returns a JSON of all the currently installed templates alongside their currently assigned domain names and page statuses (individual pages can be decactivated, set to mobile only, etc.).
- /getname – This returns a JSON containing all current panel user information.
These kits often share components and language in common with ecommerce management platforms, suggesting that base code for legitimate ecommerce platforms may have been reworked to function as phishing panels instead.
For the YYlaiyu panel in particular, we can see traces of what appears to be an original shop platform in the form of vestigial pages that do not seem to be accessible from the main panel or have any apparent function. These are likely left over from whatever ecommerce management platform the YYlaiyu developers altered to generate their phishing panel.
Key takeaways about this panel & the Chinese-language phishing ecosystem
YYlaiyu is a Chinese-language PhaaS panel used primarily for financial fraud. As noted in the research here, our analysis shows:
- It has been deployed against victims in countries around the world, including Western victims as well as East Asian victims.
- The YYlaiyu panel offers its subscribers access to phishing templates that impersonate over 90 distinct brands. It operates using an interactive phishing flow, in which panel operators are alerted when one of their pages gets a new visitor, and they are able to iteratively administer each user’s session in real time.
- YYlaiyu also allows for granular permissions setting options, has a robust administrative API, and has an integration with Alibaba’s domain registration service.
YYlaiyu is just one phishing panel within a robust and thriving Chinese-language subculture organized around smishing and related financial fraud. These actors share many of the same tools, service providers, and TTPs. While YYlaiyu is an interesting kit, it is also one of literally dozens of different PhaaS kits developed and operated by actors within this unique subculture.
This report was co-authored based on joint research conducted by SpyCloud Labs and the urlscan Research Team. urlscan Pro users can also access a how-to guide on tracking YYlaiyu phishing pages and panels within the urlscan Intel Reports: https://pro.urlscan.io/intel/reports/intel/reports/2025/10/13/YYlaiyu-Phishing-The-urlscan-Perspective/
YYlaiyu is just one phishing panel within a robust and thriving Chinese-language subculture organized around smishing and related financial fraud. These actors share many of the same tools, service providers, and TTPs. While YYlaiyu is an interesting kit, it is also one of literally dozens of different PhaaS kits developed and operated by actors within this unique subculture.
This report was co-authored based on joint research conducted by SpyCloud Labs and the urlscan Research Team. urlscan Pro users can also access a how-to guide on tracking YYlaiyu phishing pages and panels within the urlscan Intel Reports:



