As Cybersecurity Awareness Month kicks off and everything starts to get pumpkin spice flavored, the cybercrime continues. This month we have updates on:
- A new data leak site (DLS) created by COM-affiliated actors that specialize in targeting corporate Salesforce instances
- A massive 500 GB leak from key contractors working on the R&D for China’s Great Firewall
- New research into “internet toilets” – Chinese doxxing communities that frequently rely on insider-acquired data to stalk and harass their victims
- Our in-depth analysis on the Asgard Protector malware crypter, a popular tool that helps infostealer distributors evade detection by antivirus tools
We’re also recapping our newly-released 2025 Identity Threat Report and touching on the two infostealer malware profiles we just added to our collections: pwn stealer and AURA Stealer.
Let’s get into it!
COM kids have a DLS now, but don’t understand government shutdowns
Data leak site
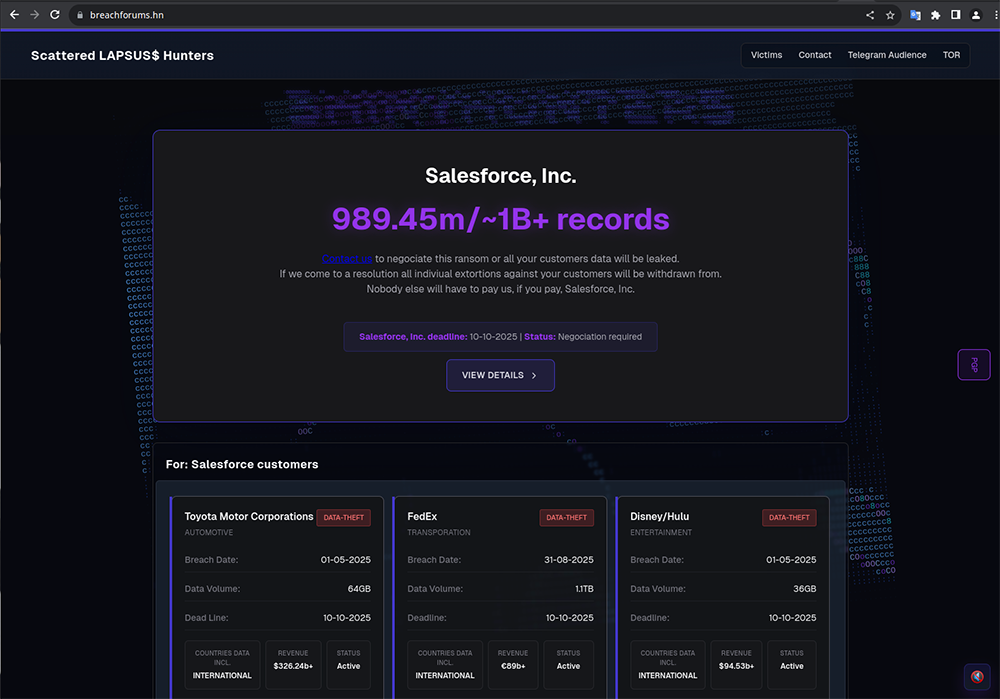
Homepage of the new Scattered LAPSUS$ Hunters DLS
They have already populated the site with quite a few alleged victims, all of which appear to have countdowns for their data to be fully leaked on October 10. Many of them also have substantial samples containing stolen data that appears to have been obtained from a customer relationship management (CRM) software. Scattered LAPSUS$ Hunters are also claiming responsibility for activity previously attributed to two distinct threat activity clusters that targeted Salesforce instances using different techniques:
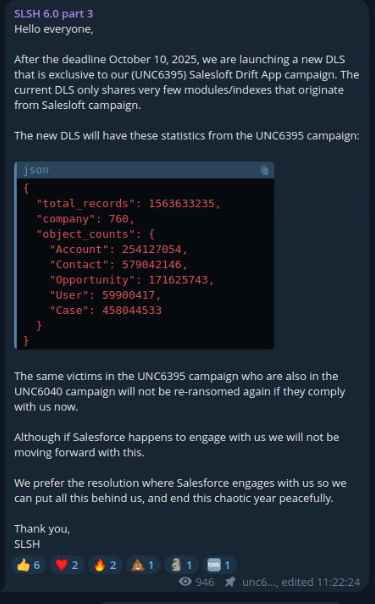
Telegram post from Scattered LAPSUS$ Shiny Hunters (SLSH) claiming responsibility for the two threat activity clusters (UNC6040 and UNC6395) and characterizing them as separate “campaigns” carried out by the SLSH group
On October 5, they also announced a partnership with Crimson Collective, the group behind the recent breach of an internal GitLab instance used by Red Hat Consulting to manage customer engagements. Thus far, the group has leaked file trees which include over 28,000 internal development repositories. Of particular interest is a “consulting engagement reports” (CER) folder that lists what appears to be over 800 customer projects for prominent organizations. Crimson Collective has now leaked additional samples of some of these CER documents on the SLSH DLS and is promising to post the full dataset on October 10.
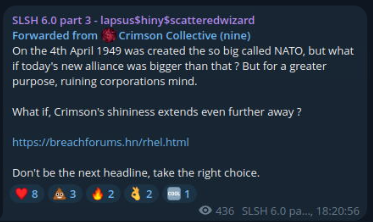
Post from the Crimson Collective on Telegram announcing their use of the SLSH DLS
US government shutdown posts
A few days prior, the scattered LAPSUS$ hunters 5.0 channel account also posted excitedly about the impending U.S. government shutdown, apparently believing that the imminent shutdown would lead to the FBI halting their investigations into cybercriminal activity allowing them to send out “100+ RANSOMS.” These posts also refer to U.S. President Donald Trump as “my king” and imploring him to fire the “FBI agents who are investigating [ShinyHunters].”
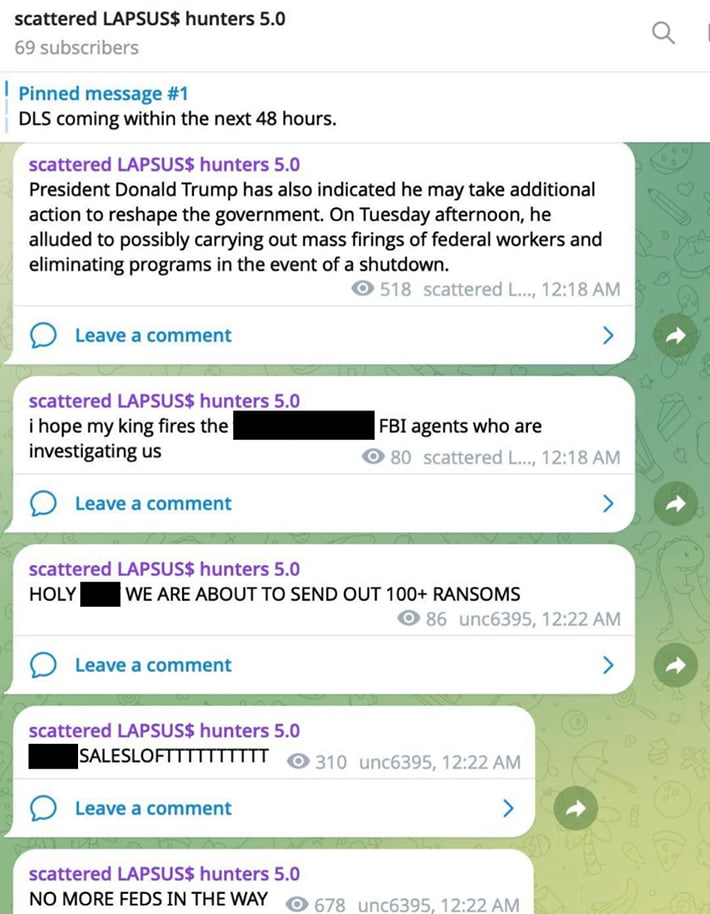
Posts from scattered LAPSUS$ hunters 5.0 on Telegram. Original image shared by journalist Andy Greenberg via LinkedIn.
However, as the former federal employees on our team can attest, ‘essential employees’ continue working in the event of a government shutdown. This essential category includes the vast majority of law enforcement officers and employees in operational national security-related roles, who continue to work but have to wait until the shutdown ends to receive back pay. As a result, any investigations into ShinyHunters or other threat actor groups are unlikely to face significant interruptions.
Secret Service busts SIM farm in NYC
On September 23, the U.S. Secret Service announced that they had discovered and seized equipment from “more than 300 co-located SIM servers and 100,000 SIM cards across multiple sites” in New York City. A SIM server is essentially a specialized device capable of handling a large number of SIMs at once, allowing its operators to control calls and SMS messages for many numbers at once.
In their press release, the Secret Service noted that they had been able to connect these devices to multiple “anonymous telephonic threats” against U.S. government officials. Both the official announcement as well as multiple subsequent articles seemed to speculate significantly about the motivation behind the network, its potential to impact cellular service in the city ahead of the UN General Assembly, and its potential connection to espionage and state-sponsored actors.

SIM server devices discovered in otherwise empty apartments and office spaces. Image shared by the U.S Secret Service.
However, the most likely explanation is that these devices were managed by criminals renting out access to phone numbers as a service to any paying customer. These types of sketchy virtual number services are extremely common, and are often used by spammers to distribute malicious messages like phishing lures. They can also be used for more gray-area activities like registering social media accounts that require a real mobile phone number or to conduct digital marketing ad campaigns. In this case, these numbers were also apparently used to “swat” Congresswoman Marjorie Taylor Greene and Senator Rick Scott, prompting the law enforcement investigation into this SIM farm operation.

Large stacks of MobileX SIM card packaging. MobileX is a low-cost MVNO. Image shared by the U.S. Secret Service.
500GB leak from China’s Great Firewall
China’s surveillance expansion into gateway countries was highlighted in the recent leak of data from Geedge Networks (积至公司). Geedge is a significant R&D contributor to the “Great Firewall of China” – a system of network monitoring, analysis, and controls that allow for the surveillance and censorship of internet traffic in mainland China. Geedge exports this model to China’s neighbors as part of a massive technological expansion project, dubbed the Silk Road of Surveillance. While on the surface, Geedge is presented as simply acting as a service provider of telecommunications monitoring and control capabilities in these gateway countries, it is unlikely that China would be completely orphaned from access to the data being collected.
The leak included over 500 GB of source code, Jira tickets, and other internal chats and documentation from Geedge Networks and MESA Labs, a research lab within the University of the Chinese Academy of Sciences that is closely tied to Geedge. To quickly digest this leak, we used an LLM to aid us in translating and summarizing about 50 GB of documentation and Jira tickets present in the leak.[1]
Tools, teams, and projects
In January of 2023, it appears Geedge united its “DPI team” (deep packet inspection) and “SDN team” (software defined networking) to create a “DPI-SDN” project. This allows for finer controls and detections on interpreting packet behavior to determine what apps their users are using.
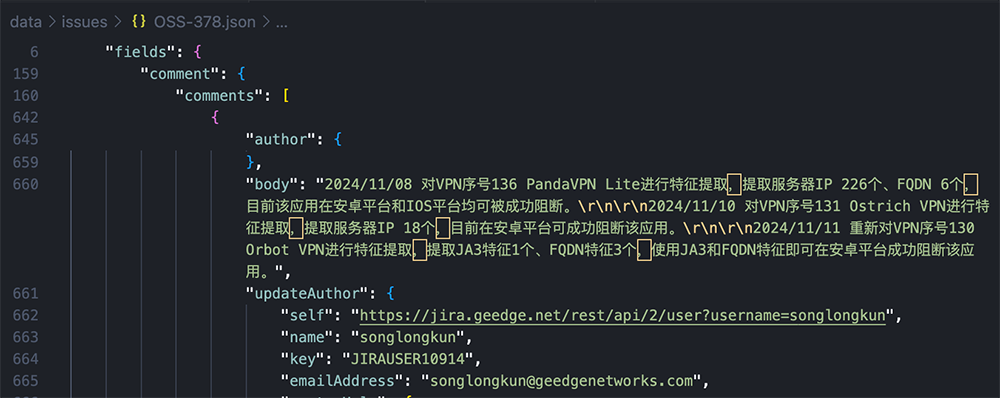
Geedge Issue GIT-493, discussing the union of DPI and SDN
Throughout late 2024, the Geedge team worked on a ticket labelled “VPN Feature Extraction” that allowed them to identify different VPNs that Chinese users were utilizing, including Orbot, Ostrich VPN, Outline VPN, PandaVPN, Pawxy, ProtonMail, and Proxy OvpnSpider. Another ticket discussed configurations for blocking Telegram, TikTok, Facebook, Youtube, and Psiphon3 (a censorship circumvention toolkit that offers VPN, SSH, and HTTP proxy options). A report by WIRED noted that 281 VPNs and 54 apps were marked as high priority for blocking, including Signal – a secure messaging app with end-to-end encryption.
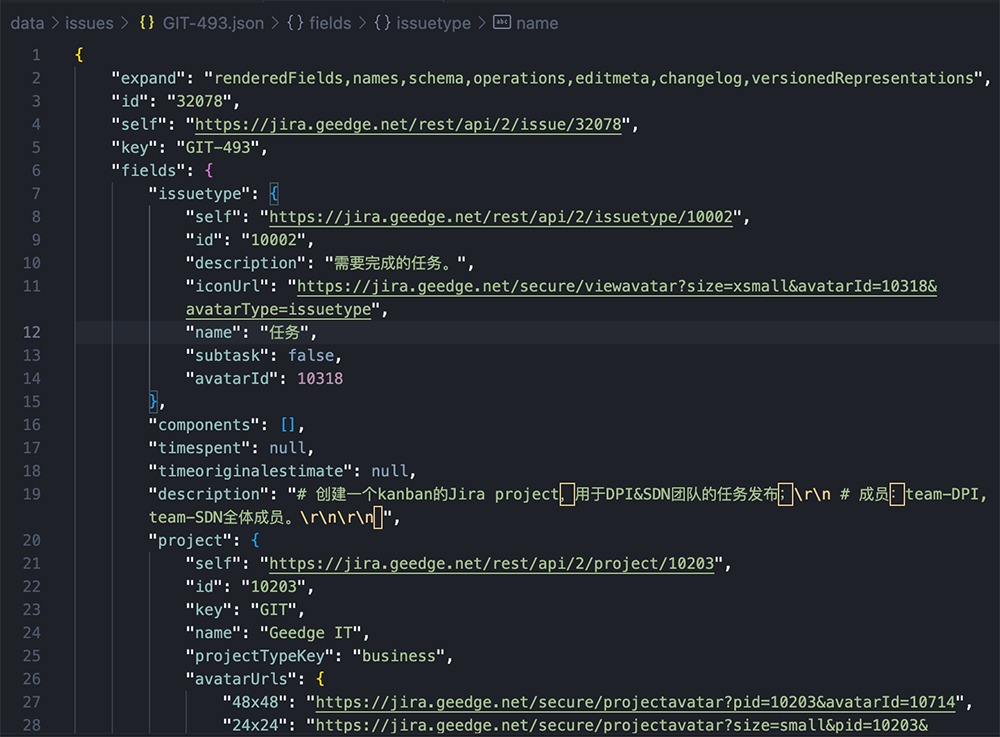
Geedge Issue OSS-378 highlighting VPNs to detect and block
Within the Jira documentation, a variety of tools (some of which appear to be inhouse Geedge creations) were mentioned, including: zeek, Wireshark, Network Zodiac, Bifang, NZ Vsys, and Nezha. All of these products are related to network monitoring, analysis, and reporting.
Gateway countries and their Jira tickets
Gateway countries – also described within the leak as land corridors or trade routes – connect other countries together through trade, infrastructure provision, and land access. A beneficial consequence of this for intelligence collection efforts is that they also provide a collection scope beyond the gateway country itself, allowing countries to expand their collection apparatus into friendly neighboring countries. Gateway countries may even share infrastructure with surrounding countries – including internet infrastructure – allowing sophisticated and well-resourced intelligence collectors like China to significantly expand their signals intelligence collection into neighboring telecommunications networks.
Kazakhstan: European gateway
Gateway countries – also described within the leak as land corridors or trade routes – connect other countries together through trade, infrastructure provision, and land access. A beneficial consequence of this for intelligence collection efforts is that they also provide a collection scope beyond the gateway country itself, allowing countries to expand their collection apparatus into friendly neighboring countries. Gateway countries may even share infrastructure with surrounding countries – including internet infrastructure – allowing sophisticated and well-resourced intelligence collectors like China to significantly expand their signals intelligence collection into neighboring telecommunications networks.
The first mentions of Kazakhstan appear in Jira tickets from 2020, in which it appears eleven cities are being onboarded. Between October 2023 and November 2023, several tickets point to the bifang-api getting updated to support Chinese, English, and Russian languages. These issues were resolved in Jan 2024. On Dec 7, 2023, another ticket reported that the Kazakh Ministry of Trade and Integration requested a time zone change for the Kazakhstan interface.
Map showing Kazakhstan
Pakistan: Middle Eastern and Indian gateway
While not nearly as developed in its role as a Chinese gateway country as Kazakhstan, Pakistan is actively developing to serve as a gateway between China, the Middle East, and India.
On June 26, 2024 at 1pm, a representative from Pakistan named Ammar was scheduled to be picked up from the Geedge office. On August 27th, a ticket was created in the MESA Labs Jira system kicking off the integration of traffic flow from four major Pakistani telecom providers (Jazz, Zong, Ufone, and Telenor).
Additionally, there’s a document suggesting language and symbols to highlight Pakistani-China relationships positively, such as referencing strategic infrastructure projects (including the Gwadar Port and the Thar Coalfield), suggested imagery (Arabian Sea, a parched desert, and snow-capped mountains), and symbolic language (“a testament to the strengths of a relationship that transcends the changes of our time” and “a focal point of our joint efforts”).
Map showing Pakistan

Language and symbolism suggestions for Pakistani-China relations from a document titled CPEC.docx
Myanmar and Ethiopia: Gateways to Southeast Asia and Africa
Myanmar and Ethiopia both represent strategic geographic locations, with Ethiopia already serving as a central African hub and Myanmar serving as a gateway to Southeast Asia. This is true even while Myanmar still struggles to develop its technological capabilities (which are, no doubt, being accelerated under China’s influence).
Ticket mentions of both Myanmar and Ethiopia were minimal, but we did see a few examples:
- In July 2022, a Jira ticket was opened to address a popular VPN in Ethiopia, iTOP VPN, that was bypassing Geedge’s controls. By Aug 2022, new detections were being tested and evaluated.
- In May 2024, Myanmar telecom companies Ooredoo and MYTEL both reported packet losses that required additional configuration by the Geedge DPI team.
Repercussions of the Geedge Networks leak
The significant context available from Jira tickets demonstrate how much information about the people, activities, security posture, infrastructure and relationships of a company can quickly become public knowledge if such a development ticketing system is leaked. Not only do the Geedge leaks stand to erode confidence in China among its key enabling partners, the intimate details of the staff and systems involved make Geedge vulnerable to both social engineering and computer network exploitation attacks enabled by the leaked data.
Additionally, the technical details about their DPI-SDN program open up opportunities for bypassing and undermining that program by individuals living under digital censorship and surveillance regimes. In the face of rising tensions over internet liberties, individuals living within these systems continue to find creative ways to evade both surveillance and censorship.
New research & insights from SpyCloud
While LummaC2 continues to dominate headlines as the leading commodity infostealer fueling account takeover attacks, Asgard Protector has been the silent partner enabling its success by allowing malware distributors to avoid anti-virus protections on victim devices. This crypter-as-a-service operation has turned malware deployment into a point-and-click experience for cybercriminals, complete with anti-VM capabilities, IP logging, and autorun functionality delivered through a simple Telegram bot. Read our analysis for a technical breakdown, including deobfuscated scripts, IOCs, and detection strategies that can immediately strengthen your malware defenses.
SVP of SpyCloud Labs, Trevor Hilligoss, and Manager of Security Research Partnerships, Aurora Johnson, introduced the concept of “internet toilets” at SentinelOne’s LABSCon event in September. They shared findings about how corrupt insiders and digital surveillance systems feed these Chinese communities, as well as how they compare to Western Doxbins, the economic and social incentives driving them, and the implications for people and businesses worldwide.
SpyCloud’s new Identity Threat Report exposes a dangerous paradox at the heart of enterprise security: while 86% of security leaders express confidence in their identity defenses, 85% of organizations were still affected by ransomware incidents last year. The data also reveals phishing as the dominant ransomware entry point and raised awareness of follow-on attacks from the infostealer malware plaguing users.
With AI democratizing sophisticated cybercrime but only a minority of defenders leveraging it for protection, and supply chains expanding the identity attack surface across interconnected vendor ecosystems, the contents of the new report underline the need to shift from perception-based confidence to evidence-based defense.
Get the full report to benchmark your team’s identity security approach against 500+ peers, backed by insights from the 850+ billion identity assets we’ve recaptured from the criminal underground, or check out some quick highlights in this blog. This year’s report is an updated rendition of our prior Malware and Ransomware Defense Report, which we have evolved to reflect the broader identity-based nature of today’s threat landscape.
Recaptured data numbers for September
September monthly total
Total New Recaptured Data Records for September
1,045,483,559
New third-party breach data this month
Third-Party Breaches Parsed and Ingested
605
New Data Records from Third-Party Breaches
67,376,750
New recaptured phished data this month
Phished records
1,730,306
New infostealer malware data this month
Stealer Logs Parsed and Ingested
3,790,622
New Data Records from Stealer Infections
76,929,388
New Stolen Cookie Records
901,177,421
New infostealer malware families added
- pwn Stealer: pwn Stealer is a basic Windows infostealer malware primarily targeting user passwords and authentication cookies. In many of the pwn Stealer logs we have recaptured, the malware appears to specifically highlight any captured cookies for Facebook.com, pulling them out into separate Facebook-Cookie
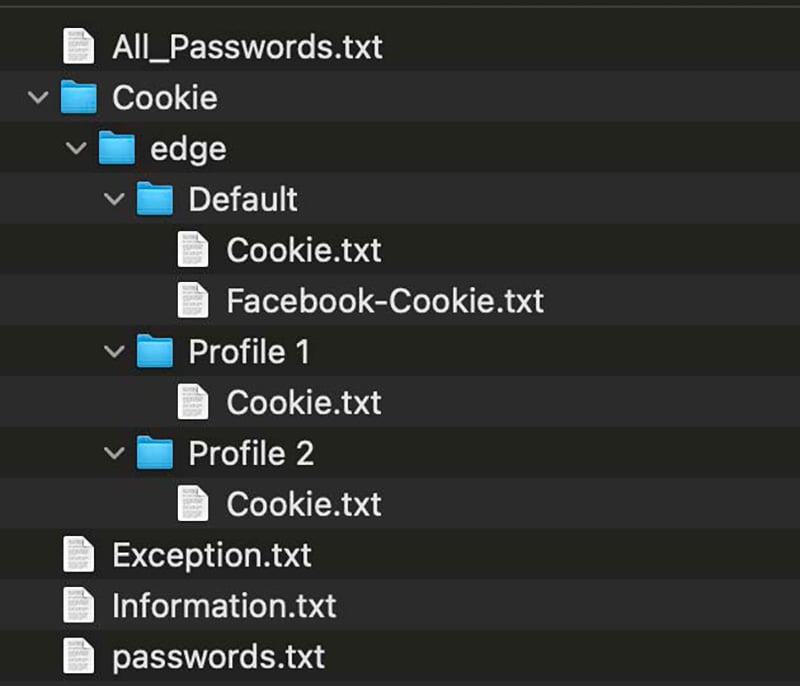
File tree from a recaptured pwn Stealer log showing a separate cookie file containing just Facebook.com cookies.
- AURA Stealer: AURA, another Windows infostealer, appears to be modeled after LummaC2 in terms of its features, but lacks some of LummaC2’s sophistication. Its developers claim that it has the ability to capture credentials from over 110 different browsers, 70 applications, and over 250 browser extensions.
Stay in the loop
Our team at SpyCloud Labs keeps close tabs on the cybercrime ecosystem. Sign up to stay in the loop with our latest research.
[1] To help us quickly understand more context about this very large corpus of documents, we used an LLM to methodically translate and summarize ~50 GB of documentation and Jira tickets, using a similar method to one we used previously to quickly analyze the Black Basta chat leaks. The resulting translated summaries included names, hostnames, countries, technologies, partnerships, and even framed propaganda language throughout Geedge’s development into its current state. These summaries were then reviewed by an analyst, and concrete details of interest were traced back to their source material and explored further.