It’s mid-summer and we’re beating the heat by staying inside on our computers monitoring the latest cybercrime developments, including:
- Part III of what we’re calling the Forum Wars, including insight into what sparked the original BreachForums outage as well as a list of new contenders fighting their way onto the scene,
- Perspective into the cyber side of the Iran-Israel conflict, including hacktivist operations that picked up steam during the recent heightened conflict, and
- Law enforcement actions aimed at disrupting the prevalent and broadly-publicized fraudulent North Korean IT worker scheme.
We’ve also spent time researching developments in the Chinese criminal underground, including the 4 billion-record breach affecting Chinese citizens in June, as well as two other leaked datasets that pull back the curtain on the Chinese hack-for-hire industry, including threat activity tied to Salt Typhoon.
Last but not least, this month we’re sharing our two cents on the “16 billion passwords” breach headline that blew up all of our feeds last month. (Hint: it was mostly hype.)
Without further ado, let’s dig in.
June cybercrime news
The Forum Wars Part III: This time with arrests
BreachForums, the most popular English-language data breach forum, went dark on April 15, 2025 with no clear explanation as to why. Since then, cybercriminals have been clamoring to fill the void with new copycat forums as well as quick moneymaking scams capitalizing on the situation. [For more, see our cybercrime updates from April and May.]
Now, thanks to new reporting by the French newspaper Le Parisien, we have a more complete picture of what happened.
In February 2025, BreachForums administrator IntelBroker was reportedly arrested by French authorities. Fearing exposure, the other forum administrators decided to take the website offline. Despite this last-minute attempt at an OPSEC clean-up, four other cybercriminals heavily involved in BreachForums were arrested by French authorities in June: “ShinyHunters,” “Hollow,” “Noct,” and “Depressed.” As BleepingComputer noted in their reporting on the arrests, the IntelBroker and ShinyHunters accounts acted as BreachForums administrators, while Hollow was a moderator.
As the situation continues to play out, we are continuing to monitor various new forums as they pop up, as well as some more established forums that seem to be gaining popularity in BreachForums’ absence.
Some new developments in the English-language data leak forum ecosystem include:
- Two new BreachForums clones appear to have launched on July 1.
breached[.]ws was created by the threat actor Hasan (aka hasanbroker/sextorts), who appears to have ties to the Com. In the past couple of months, Hasan has been posting extensively to X/Twitter and Telegram claiming to be creating the successor to BreachForums despite having no clear ties with the previous site’s administrators. Another actor with the moniker ‘Pray’ also announced that they would be closing their short-lived forum BittenForums (which had only been active since 4/10/2025) and teaming up to help with Hasan’s version of BreachForums, with Hasan as the administrator and Pray as a site moderator.
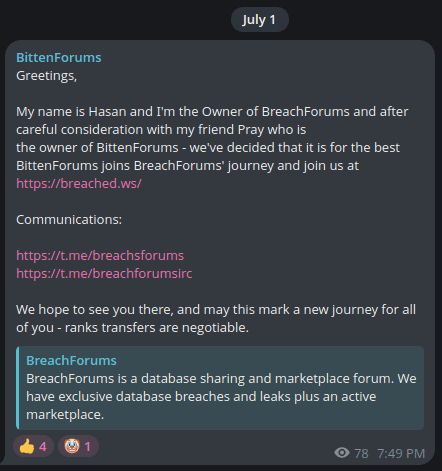
breachforums[.]info is another copycat site claiming to be the new BreachForums. In an announcement to the site, Jaw writes that “ShinyHunters and IntelBroker have been arrested,” and “authorities seized all server infrastructure.” Jaw encourages users to avoid creating new accounts tied to their BreachForums personas due to OPSEC concerns.
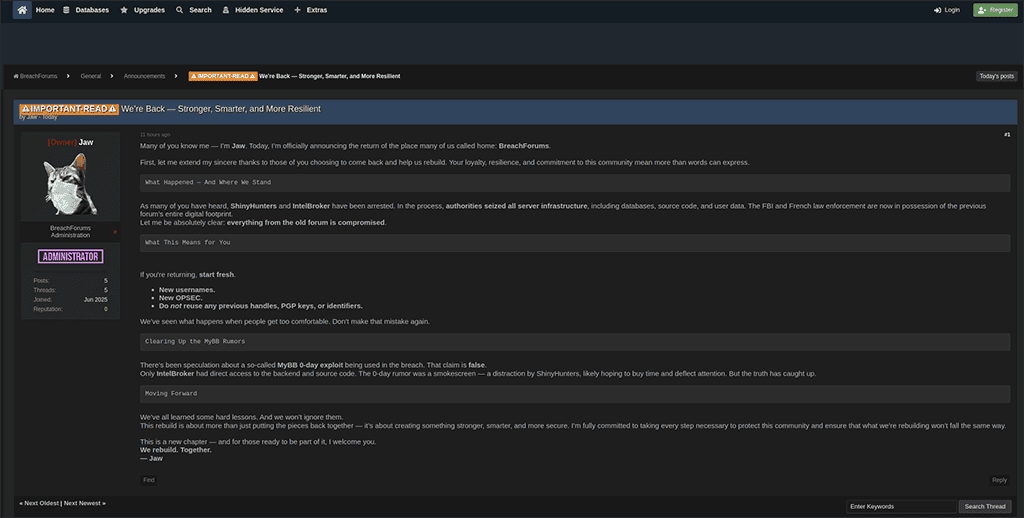
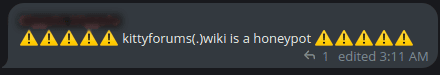
- Another new site called Kitty Forums is also being discussed as a possible successor to BreachForums. Thus far, it appears to be a smaller forum that has been populated mostly with reposts of old data breaches from other sites. General chatter about the site appears mixed (see Images 4 and 5).
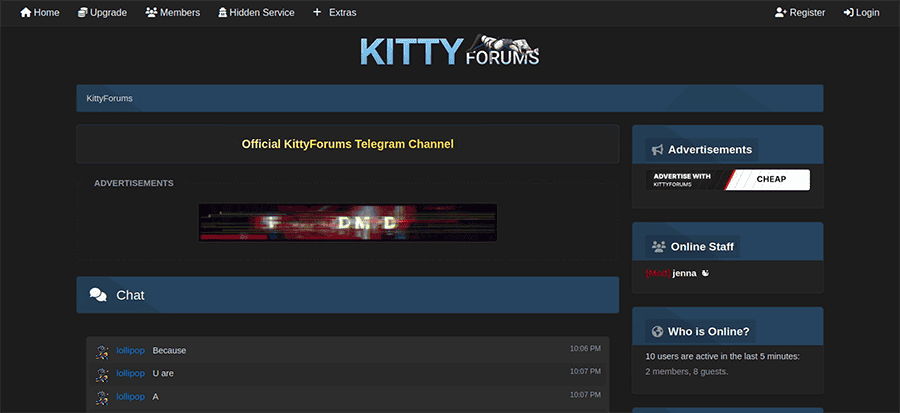
Image 3: Screenshot of the Kitty Forums site.
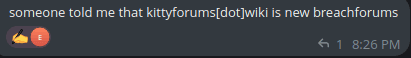
Image 4: Message claiming that Kitty Forums is the new BreachForums.
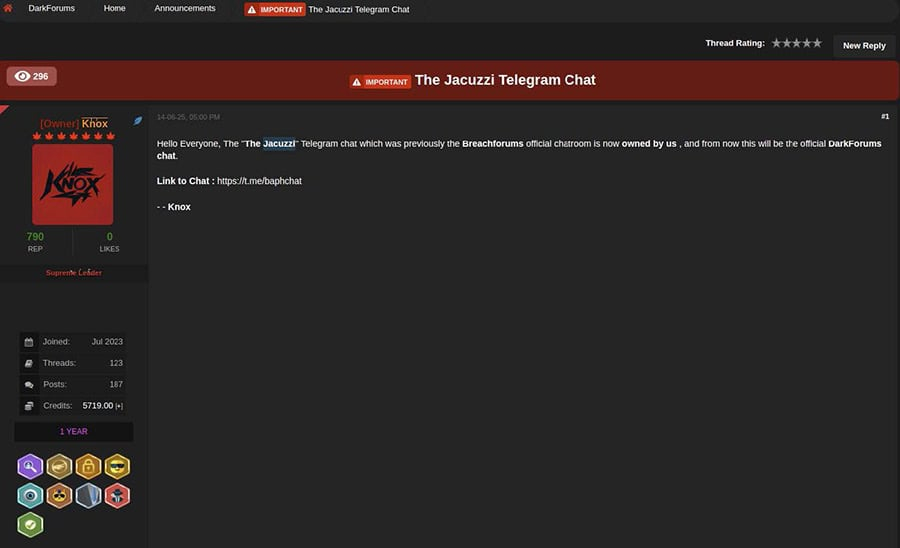
- We also continue to observe a steady stream of posts on both LeakBase and DarkForums, as well as via Telegram channels centered around sharing breached and leaked data. The DarkForums owner, Knox, appears to be making a concerted effort to subsume the BreachForums community into their forum. Notably, Knox appears to have taken control over ‘The Jacuzzi’ – formerly BreachForums’ official Telegram channel – as of June 14.
Hacktivist operations escalate during Iran-Israel conflict
On June 13, Israel significantly ratcheted up tensions with Iran by launching a wave of attacks at Tehran, leading into 12 days of hot conflict between the two nations. In tandem with this kinetic conflict, there was also a marked surge in cyber operations.
In particular, much of the most prominent offensive cyber activity was carried out by suspected “faketivist” groups like Predatory Sparrow, CyberAv3ngers, and Handala Hack Team. Faketivist groups purport to be ideologically motivated, but in reality have direct ties to nation-states. Some significant recent cyber faketivist attacks include:
- Predatory Sparrow (aka Gonjeshke Darande), an Israel-aligned hacktivist group with suspected ties to the Israeli government, hacked multiple Iranian financial institutions. First, they disrupted services and claimed they deleted data at Iran’s state-owned Bank Sepah. Then, they hacked an Iranian cryptocurrency exchange – Nobitex – and stole more than $81 million worth of digital currency. Predatory Sparrow claimed responsibility for their cryptocurrency heist on social media and also proceeded to leak source code from the exchange.

Image 7: Image posted by the Predatory Sparrow group to Twitter boasting about their compromise of Iranian cryptocurrency exchange Nobitex.
- Handala Hack Team, a hacktivist group with suspected links to Iran’s Ministry of Intelligence, also appeared to resume activity over the last week in June. They posted about a series of hack-and-leak operations into Israeli organizations including two large Israeli recruitment and staffing firms: QHR and JobPlace.
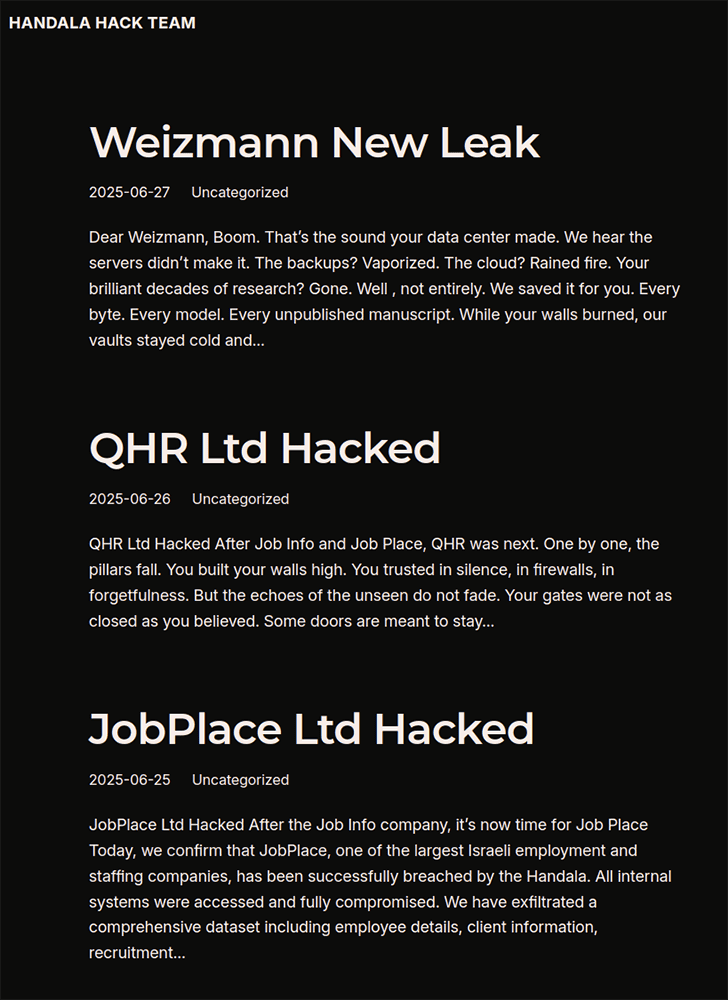
Image 8: Handala Hack Team’s website claiming multiple hack-and-leak operations against Israeli organizations.
On a macro-level, this activity highlights how intertwined cyber and kinetic operations are in modern warfare. The faketivist activity in particular also shows how the lines are blurred between nation-state threat actors, hacktivists, and cybercriminals. Attribution for cyberattacks is hard, but the categorization of cyber threat actors might be even harder, as these actors rarely fit into neat boxes.
Disruption of North Korean IT worker operations
On June 30, the DOJ announced a series of coordinated law enforcement actions aimed at disrupting the DPRK’s fraudulent remote IT worker operations. In these schemes, North Korean individuals work to enrich their regime by deceiving companies in the US (and other Western countries) to hire them for remote IT roles. Often they enlist individuals in the United States to act as logistical middlemen; they do things like receive and forward payments to evade sanctions and suspicion, and set up and host corporate laptops (otherwise known as “laptop farms”).
The announced actions include the seizure of tens of thousands of dollars across 29 seized financial accounts, searches of 29 suspected laptop farms resulting in the recovery of approximately 200 computers, the arrest of one U.S. national, and indictments of a dozen other individuals. According to the DOJ, the individuals named in these cases are responsible for siphoning millions of dollars in fraudulently obtained wages to the North Korean regime.
TL;DR of new SpyCloud Labs research
A newly uncovered data leak – possibly the largest in China’s history – exposed over 4 billion records containing sensitive personal information, including national ID numbers, financial data, and social media accounts. SpyCloud Labs’ analysis suggests the data was organized for use in a “social engineering library” (SGK), a repository of breached data that enables cybercriminals to execute account takeover, financial fraud, and doxxing campaigns targeting Chinese citizens. Read the full analysis.
Two recent data leaks – which we’re calling the VenusTech and Salt Typhoon Data Leaks – have exposed more details of the inner workings of China’s hack-for-hire industry, revealing sensitive documents from firms with government ties. These leaks, surfaced on English-language forums, suggest a trend of insiders monetizing access to state-affiliated data. SpyCloud Labs’ analysis provides a rare glimpse into the evolving tactics of Chinese cyber contractors and the global implications of their activities. Read the blog for a detailed examination of these leaks and their significance.
Current & forthcoming cybercrime research
16 billion passwords leaked, again
On June 18, Cybernews reported a massive new data breach totaling over 16 billion exposed login credentials. This headline quickly caused a stir, but when we reviewed the article to assess the allegedly immense new breach, we quickly realized that the 16 billion passwords weren’t coming from a singular breach. In fact, they were from 30 different exposed datasets, containing tens of millions of records and up to more than 3.5 billion records within a given dataset.
Some background on databases of this nature
In our line of work, it’s fairly common to find exposed databases (DBs) on the internet that do not require authentication to access the data. DBs of this nature are commonly filled with stolen credentials that actors collect over time. At SpyCloud, we usually refer to these DBs as “Stealer Log Credential DBs,” because most of the credentials can usually be connected back to infostealer logs as their original source.
To create these DBs, threat actors parse credentials (usually containing a username/email, password, and login URL) out of infostealer logs en masse, and aggregate them into their own databases. Because the data contained within Stealer Log Credential DBs is originally from individual stealer logs, they are a bit like very large combolists.
Since curators of Stealer Log Credential DBs generally pull from the same source – stealer logs they find on the dark web – there is often overlap between them. We know this to be true, because at SpyCloud, we regularly ingest data directly from infostealer logs, as well as from derived sources including exposed Stealer Log Credential DBs and ULPs/Combolists, and we have observed that there is frequent duplication between these sources.
The duplication occurs for a variety of reasons. For one, stealer logs are often distributed and redistributed via multiple channels over time. Individuals also get re-infected, so multiple infostealers might collect the same set of credentials multiple different times from the same device/person. Then, various actors creating their own Stealer Log Credential DBs and ULP-format combolists compile and redistribute the credentials from infostealer logs again and again over time.
Our takeaways about what happened with this "new breach"
In this particular case, because the original reporters appear to have added together the total number of records from 30 different datasets without deduplicating records, it’s highly likely that the reported total of 16 billion unique credentials is inflated.
As the story has continued to develop, this conclusion appears to be echoed by other security researchers. On June 30, Forbes published a report about an analysis that Group-IB completed on “samples from a repository described as containing 16 billion compromised credentials,” concluding that all of the login‑password pairs in the dataset could be “traced back to public stealer‑log leaks.”
While it’s unclear whether the dataset that these researchers analyzed is the same set of databases originally reported on by Cybernews, it still underscores the point that there are many databases of stolen credentials compiled from darknet-sourced stealer log data sitting unsecured on the open internet. However, an exposure of these compiled databases doesn’t constitute a new breach, as they are not the original source of the exposed credentials.
SpyCloud has been and will continue to ingest Stealer Log Credential DBs like these to ensure that our customers are protected to the highest fidelity possible for these derived sources of infostealer credentials. Stealer Log Credential DBs and ULP combolists usually contain credentials that we have already ingested from the original source: infostealer logs. However, it’s still useful to ingest data from these derived sources because it allows us to verify coverage within our infostealer log collections as well as track how credentials propagate through the cybercriminal ecosystem after they are captured by infostealer malware.
June monthly total:
Total New Recaptured Data Records for June
4,424,956,266
New third-party breach data this month
Third-Party Breaches Parsed and Ingested:
536
New Data Records from Third-Party Breaches:
3,403,186,026
New recaptured phished data this month
Phished records:
1,731,177
New infostealer malware data this month
Stealer Logs Parsed and Ingested:
1,685,228
New Data Records from Stealer Infections:
21,103,968
New Stolen Cookie Records:
1,000,666,272
New infostealer malware families added:
Acreed Stealer: Acreed Stealer (aka ACR) is a Windows-targeted stealer designed to grab form data such as system information, saved passwords, files, and other device and browser information from infected devices. Acreed has recently gained notoriety because threat actors have been flooding Russian Market with listings for Acreed infostealer logs for sale. This stealer may have evolved from GrMsk Stealer, a private malware observed since July of 2023.
Stay in the loop
Our team at SpyCloud Labs keeps close tabs on the cybercrime ecosystem. Sign up to stay in the loop with our latest research.





