- Another update in what we’re calling the Forum Wars – BreachForums is back, but now XSS is experiencing some takedown woes of their own,
- A cyberattack on Aeroflot, Russia’s largest airline, and
- A massive data leak of user data from the controversial Tea app, exposing thousands of photos of women’s ID cards.
We also published new research analyzing the victimology of the prevalent Tycoon 2FA phishing-as-a-service (PhaaS) panel, as well as explored the different types of data embedded in Chinese national ID numbers.
Last but not least, we’re sharing the details of capability enhancements to our Investigations solution, which is built to help analysts and investigators detect suspicious patterns and surface attribution signals to better combat cybercrime.
Let’s get into it.
Cybercrime news and updates
The Forum Wars Part IV: Now with Russian forums
In mid-April, BreachForums – the most popular English-language data breach forum – went dark, leaving a void in the cybercriminal underground that multiple threat actors attempted to fill. Last month, French authorities announced that they had arrested key figures running the BreachForums site: IntelBroker was arrested in February and individuals behind the monikers ShinyHunters, Hollow, Noct, and Depressed were arrested in June. [For more, see our cybercrime updates from April, May, and June.]
In July, we saw a few more key developments in the forum ecosystem:
- BreachForums appears to be back after over three months of being offline.
- XSS, a major Russian-language cybercrime forum, was seized by law enforcement agencies and taken offline, but the site administrators appear to have quickly pivoted to new infrastructure.
Breachforums is back
On July 25, the .onion site for BreachForums appears to have come back online with all of the original accounts, credits, posts, and other forum data restored. They also appear to have moved to a new domain for their clearnet mirror of the forum.
Since the site came back online, some of the other forums vying to fill the BreachForums vacuum have been scrambling. A threat actor who goes by the moniker Hasan (aka hasanbroker/sextorts) created a clone of BreachForums at breached[.]ws. He had been marketing this site as the next iteration of BreachForums, but after the BreachForums site came back online, Hasan announced that he was going to change the name of his forum. He also accused the newly revived BreachForums of being “extremely federalized” and “a honeypot.”
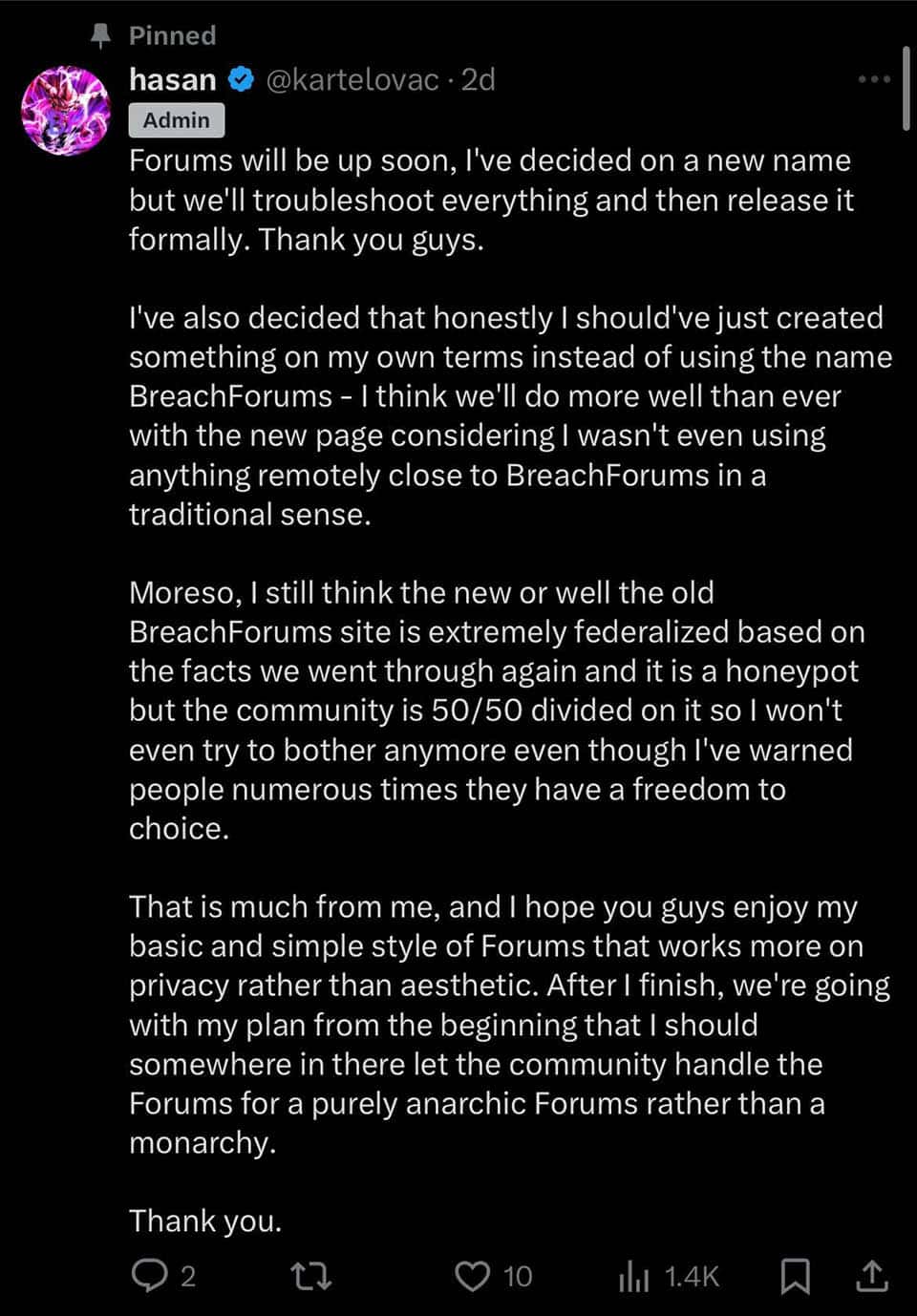
Post to Twitter/X by Hasan regarding the resurfacing of BreachForums.
There also appears to be some rivalry between the revived BreachForums and DarkForums, a smaller darknet forum that gained an influx of active users while BreachForums was offline. In June, DarkForums’ owner, Knox, also took control of the official BreachForums Telegram channel, The Jacuzzi. Current BreachForums administrators have been posting disparaging comments about DarkForums, and even created a new version of the Jacuzzi, The Jaccuzzi.
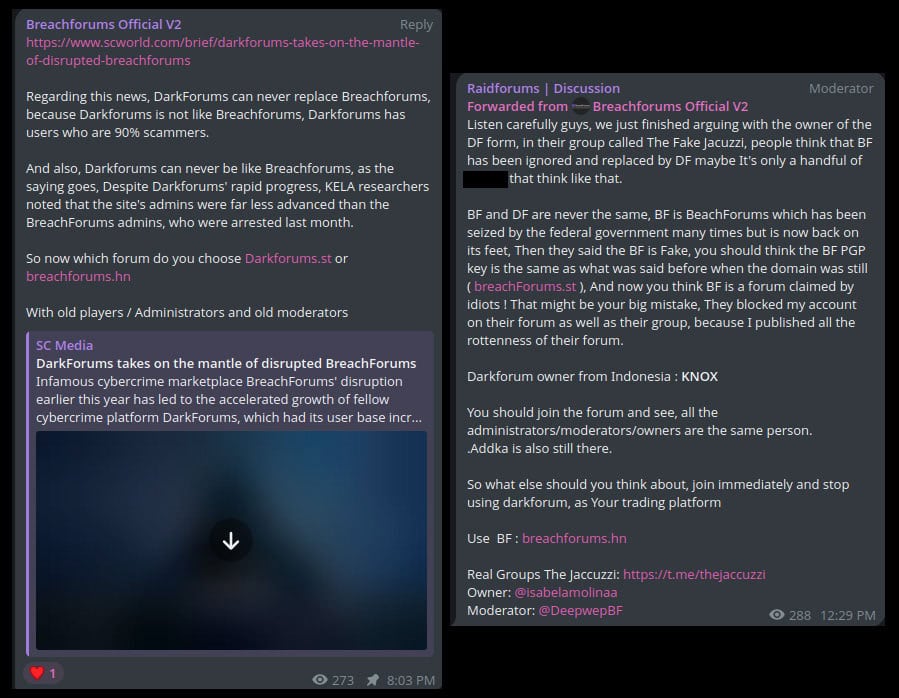
Telegram messages from a BreachForums-affiliated account stating that DarkForums is filled with scammers and urging users to go back to exclusively using BreachForums.
Additionally, rumors have been circulating about the discovery of a cross-site scripting (XSS) bug in the DarkForums website. Knox addressed these rumors in a post on July 29, stating that the issue had been identified and patched, and claiming no user accounts or personal data had been leaked. A DarkForums staff member also allegedly went radio silent in the middle of a recent escrow transaction where they were providing middleman services, apparently absconding with the money.
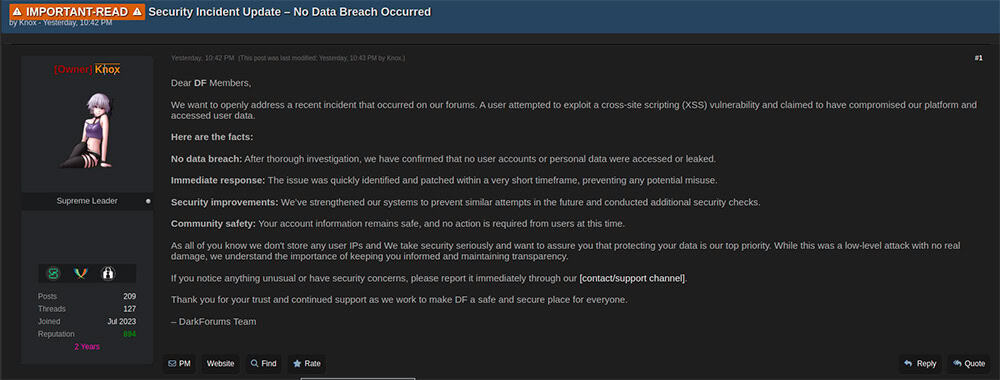
Announcement from DarkForums owner Knox about the XSS bug found on their forum
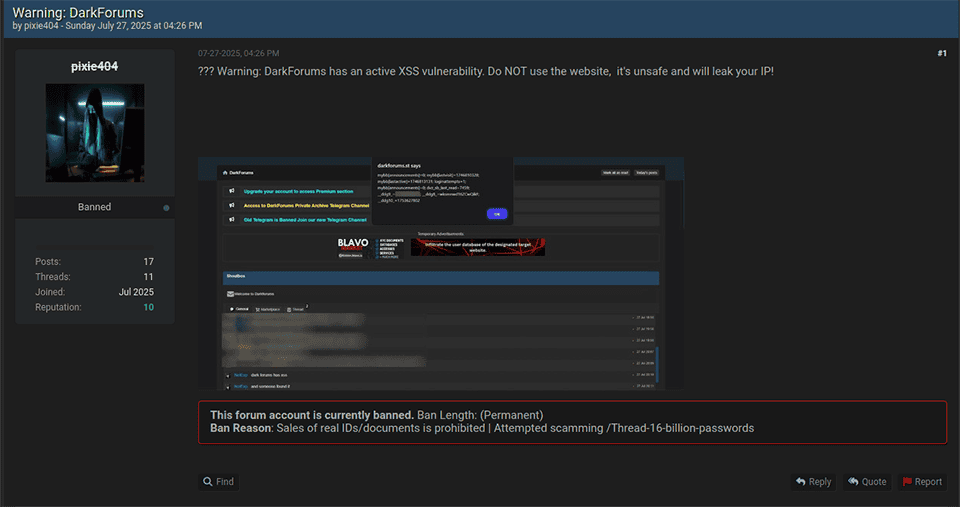
Post on BreachForums about an XSS vulnerability in the DarkForums website.
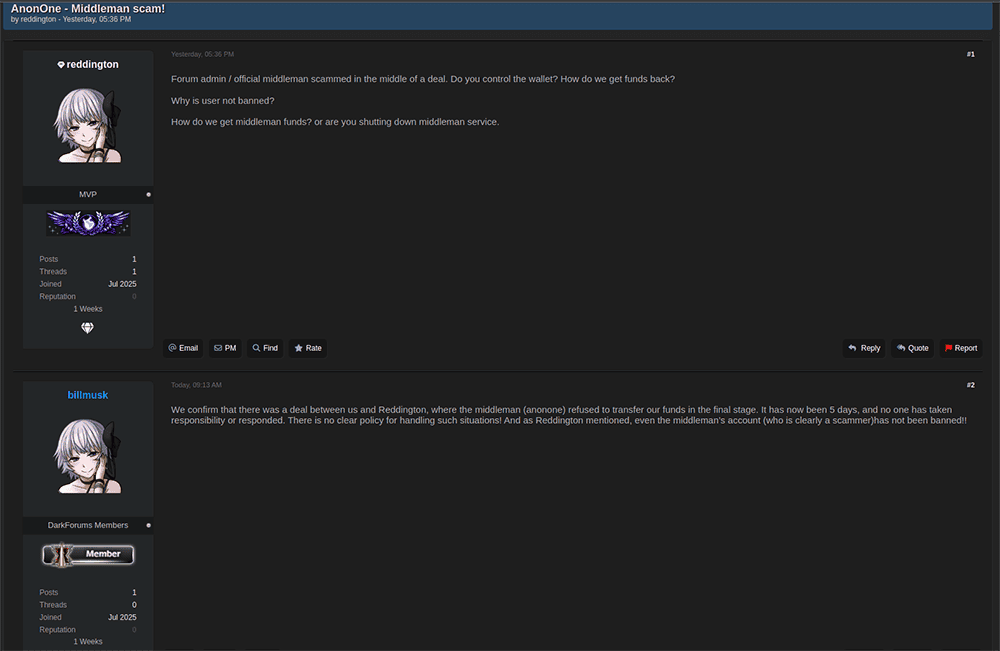
Post accusing AnonOne of stealing money while acting as the middleman in a transaction on DarkForums
XSS disrupted by law enforcement
On July 22, authorities arrested one of the XSS administrators in Ukraine. They also seized the domain for the forum’s clearnet website and carried out other disruptive actions. However, other forum administrators appear to have acted quickly to respond to the takedown, redirecting the existing .onion site to a new .onion domain and keeping the forum mostly operational for the next couple of weeks, with some short disruptions to certain features like deposits and transactions. They also appear to have moved to a new clearnet domain: xss[.]pro.
Despite this quick pivoting, other threat actors still took the opportunity to use the takedown to siphon users from XSS, advertising their own hacking forums as XSS alternatives.

Takedown notice posted to the XSS clearnet website.
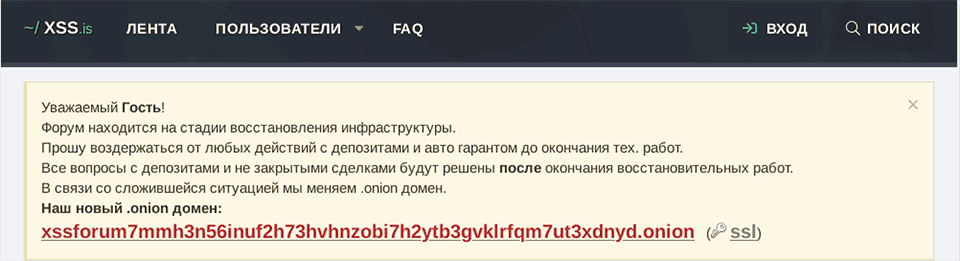
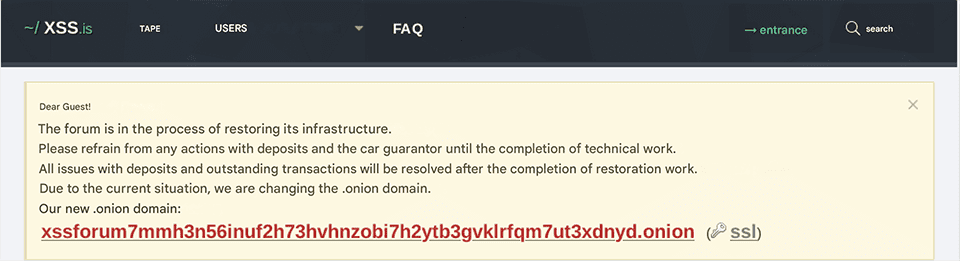
XSS announcement about their website restoration after their website was seized by law enforcement.
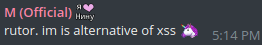
Telegram post apparently capitalizing on the XSS takedown to drive users to another alternative forum, RuTOR.
Nearly two weeks later, the new .onion and clearnet sites all appear to be offline. A new forum, DamageLib – apparently created by former XSS moderators – has popped up. DamageLab (with an a) was the original name of the XSS forum. In introductory posts on this new site, they claim that XSS was compromised by the law enforcement and urge users to use totally different monikers and accounts on the new site.
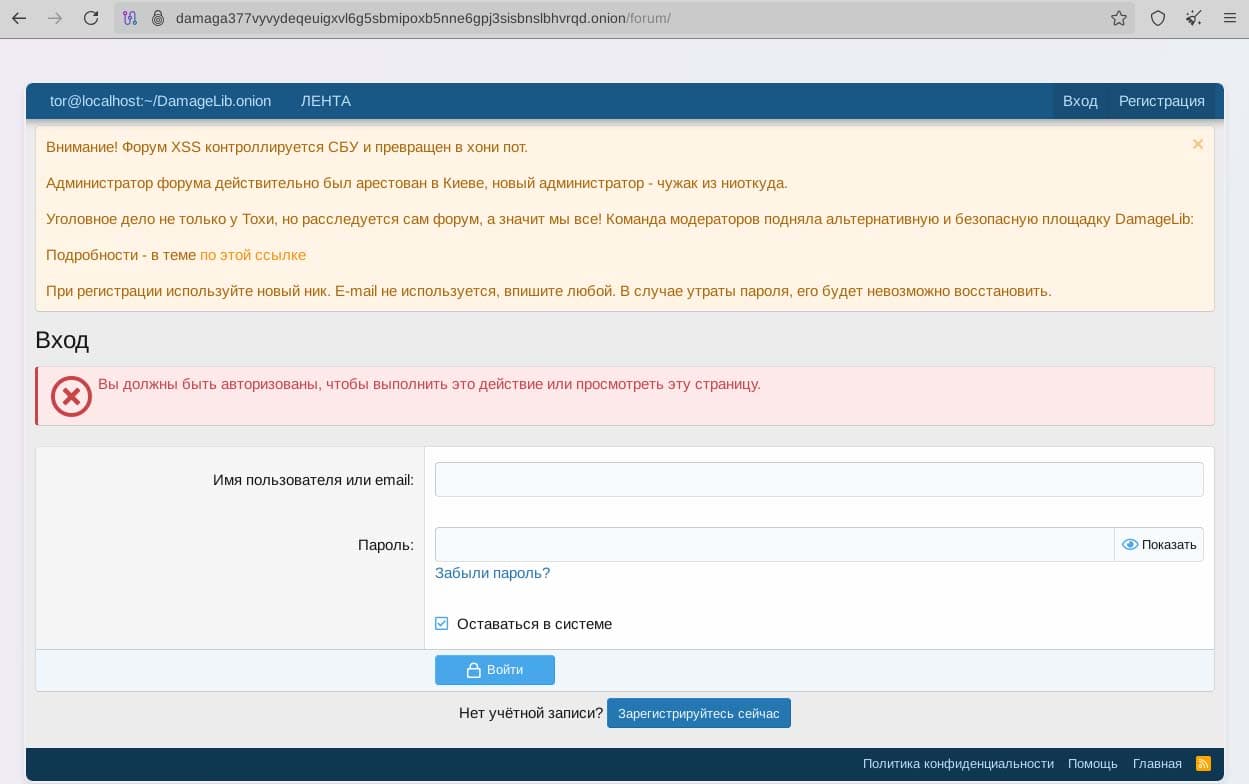
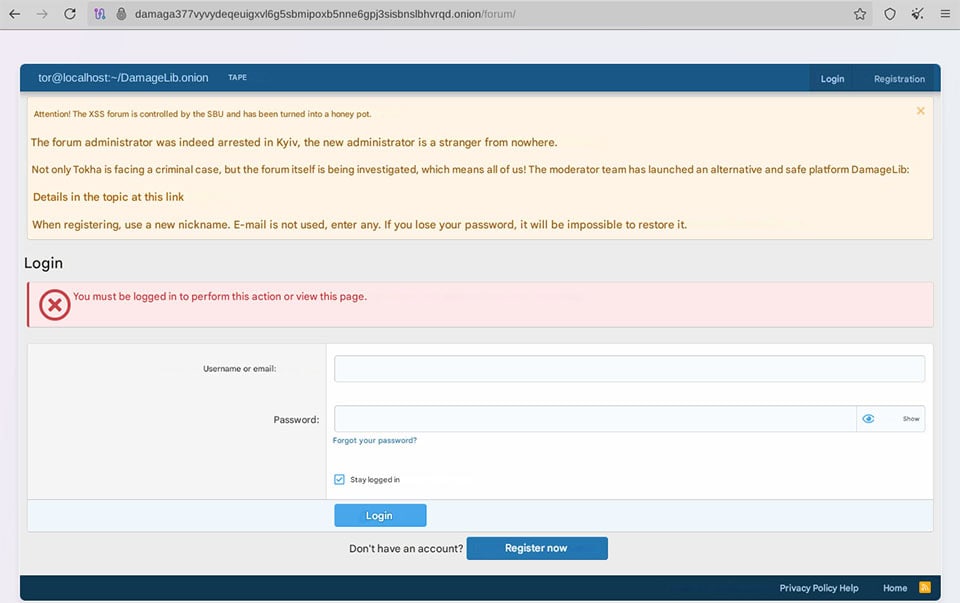
Login portal for the new DamageLib website including a message that XSS is controlled by the SBU and is now a honeypot. The message urges users to use a new nickname for their accounts on this new forum.
With these major shifts in the forum ecosystem, our team is continuing to monitor the constantly evolving situation. Only time will tell the ultimate fates of both XSS and BreachForums, and we will see whether they can weather the recent wave of law enforcement disruptions and challenges with shifting user communities.
Aeroflot attacked
Aeroflot, Russia’s largest airline, experienced a massive cyberattack on July 28, forcing them to cancel dozens of flights. Two pro-Ukrainian hacktivist groups – Silent Crow and Cyberpartisans – claimed responsibility for the attack. In a post to their website, Cyberpartisans claimed that during the attack they destroyed seven thousand servers and workstations, erased critical databases, and exfiltrated data. They also promised data leaks from this compromise to come in the future.
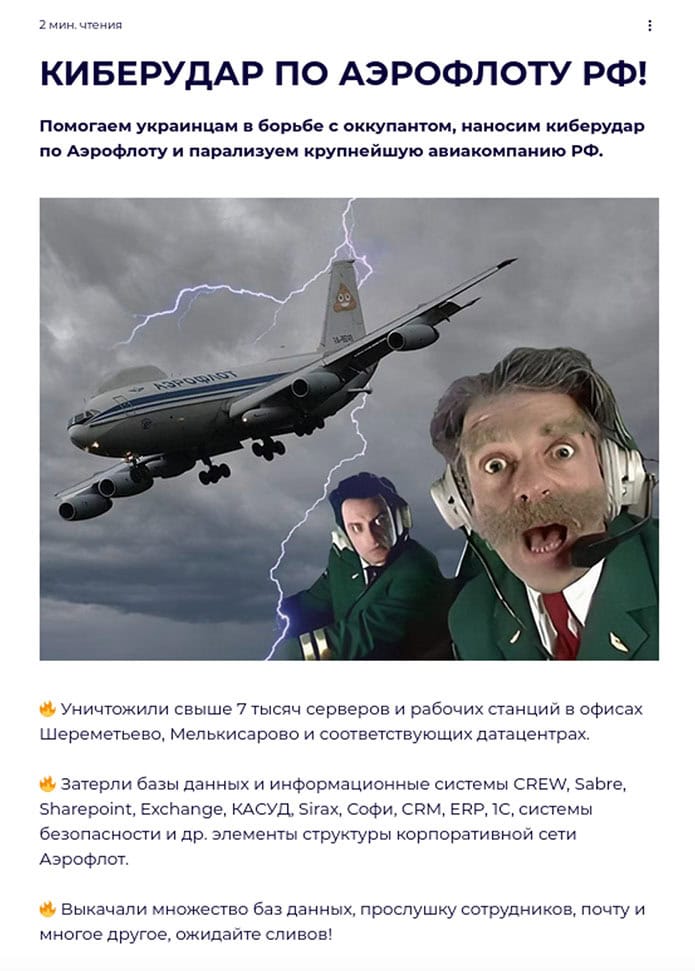
Cyberpartisans website post about the attack on Aeroflot.
In Silent Crow’s Telegram post about the incident, they claim to have maintained access to the airline’s internal networks for an entire year, gathering data and prepositioning for the destructive portion of their attack.
This attack on Aeroflot is emblematic of a lot of modern cyberwarfare: destructive and disruptive cyber operations, often conducted by hacktivist and faketivist hacking groups, are carried out alongside kinetic operations. Throughout the Russia-Ukraine conflict and recent hot conflicts in the Middle East, we have observed this same dynamic continue to play out. Often these computer network attack operations also lead to significant intelligence-gathering opportunities, as appears to have been the case in this Aeroflot attack.
Tea data leak: App in hot water for thousands of leaked photo IDs
Tea is an anonymous dating-advice app that aims to allow women to share information about men, including anonymously warning other women about their negative experiences with specific men. Their website claims that you can use the app to “avoid red flags” and “swipe safely.” Part of their user onboarding process includes submitting photo identification so that the app can verify that users are real people and “verified women,” before allowing them to create an anonymous account for their platform.
On July 25, an anonymous 4chan user posted information about an unsecured firebase storage bucket to the /pol/ board. The post claimed that this cloud storage bucket belonged to an app called Tea App, which appeared to be uploading all of the photos that they collected for user verification, including many photos of driver’s licenses, to the unsecured bucket. They also posted a link to a script to enumerate through all of the photo links and download all of the data.
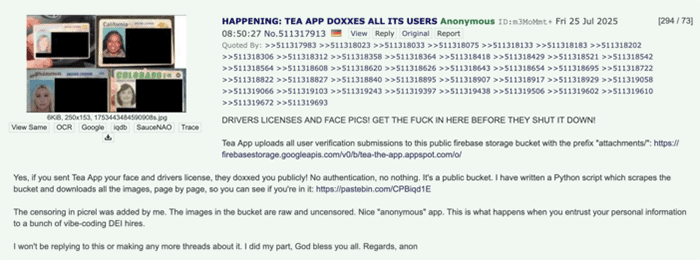
Post on 4chan /pol/ imageboard about the Tea app data leak.
Tea responded by locking down the exposed cloud storage bucket and issuing a statement, but that didn’t stop 4chan users from continuing to reshare links to torrent scraped versions of the exposed data. The most complete dataset currently circulating appears to be a torrent for about 55GB of image data including photo IDs used for verification, as well as a variety of other images shared in messages within the app.
According to Tea, approximately 72,000 image files in total were stored in the exposed firebase storage bucket. In their official statement, Tea also claimed that the photos had all been uploaded by users prior to February 2024. The 55GB torrent being reshared on 4chan and other websites appears to contain about 57,000 scraped image files – so about 80% of all of the image data that was reportedly exposed in total.

Snippet from Tea’s official statement regarding the security incident.
As with any major event on 4chan, lots of unsubstantiated rumors have been circulating about this breach. In particular, we have seen significant chatter about 4chan users creating a map of the image data using location data embedded in the images. As far as we can tell – based on the most complete dataset available – this is likely untrue.
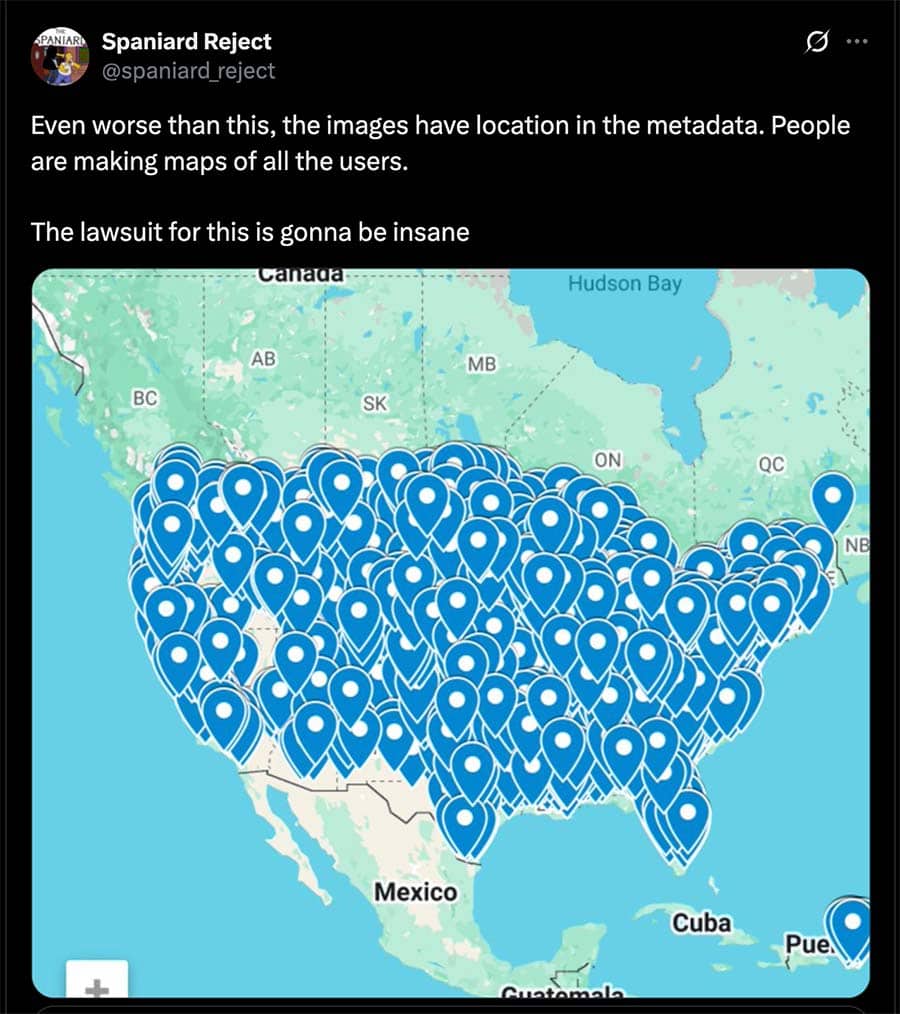
Post to Twitter/X claiming that people are making maps of Tea users using location data embedded in the leaked images.
We found that only 330 of the image files contained any location information in their EXIF data. Of those 330, only about two-thirds appeared to actually be for valid locations. Sensitive user location information was definitely exposed in this breach, including both the limited amount of files with embedded location data that actually were leaked as well as all of the addresses visible in the thousands of photos of users’ drivers licenses. However, we think that the specific claims that 4chan users were able to map Tea users using GPS coordinates embedded in the leaked images are probably at least partially fabricated. In some of the screenshots of these supposed Tea user maps shared online, there were even clear impossibilities, such as location marker pins on uninhabited Aleutian Islands in Alaska.
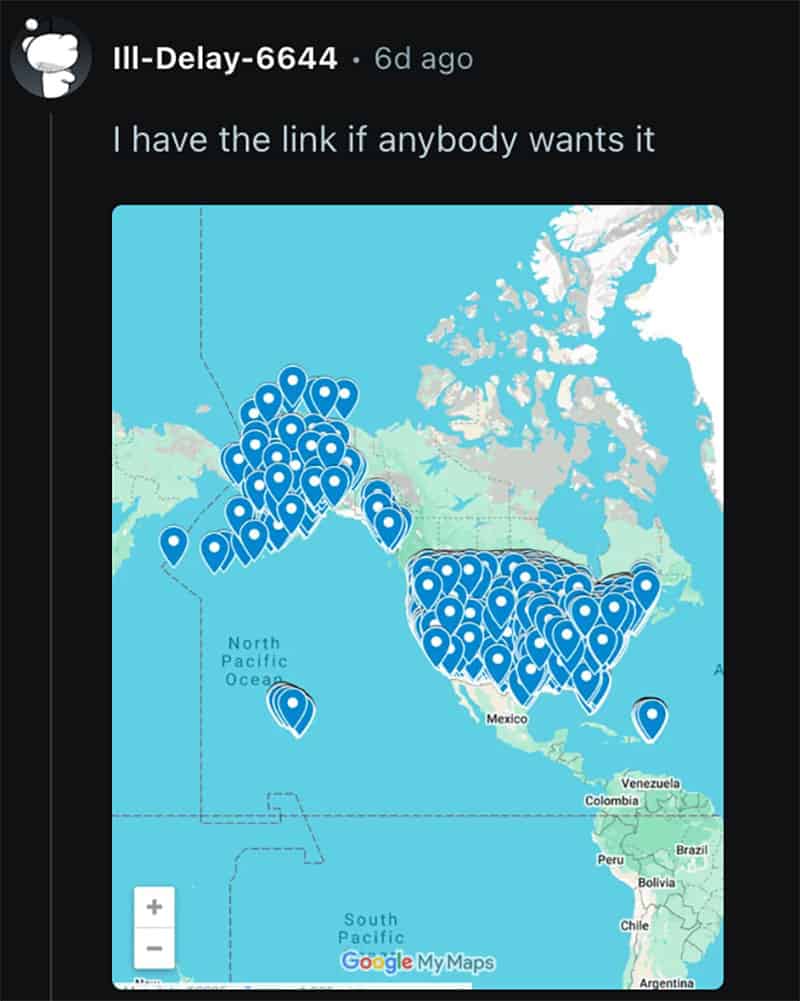
Comment in a Reddit thread about this map that appears to show location marker pins on uninhabited Aleutian Islands in Alaska.
New research & insights from SpyCloud
Tycoon 2FA is a sophisticated PhaaS platform that specializes in stealing users’ email and cloud productivity portal credentials and bypassing multi-factor authentication (MFA) protections. Our team analyzed stolen data from successful Tycoon phishes to document related victimology and exposure trends. Here’s what defenders should know.
SpyCloud Labs analyzed one of the larger Chinese data breaches ever recorded – the Shanghai National Police database leak containing almost 1 billion national ID numbers.
National ID numbers serve as persistent identifiers that follow individuals throughout their lives. When exposed, they become powerful tools for cybercriminals conducting social engineering attacks and building comprehensive victim profiles across multiple data sources. The nature of this breach makes it comparable to major US breaches like the National Public Data (NPD) Breach – see what we found in our analysis.
IBM’s latest Cost of a Data Breach Report is here – and the numbers in this year’s report reveal a paradox: while average global breach costs dropped slightly to $4.44 million, the United States hit a record-breaking $10.22 million per breach. The 2025 report offers a clear view into how credential-related attacks, supply chain compromise, and malicious insiders are driving up costs. It also highlights a notable difference between organizations using AI and automation to detect and respond to threats and those relying on manual processes. Get the highlights here.
Product update: SpyCloud Investigations with AI Insights
According to our recent survey of CISOs and security practitioners, 56% of organizations experienced an insider threat incident in the past year despite most having formal insider threat programs.
Investigating cybercrime and insider threats has never been more urgent – or complex, which is why we’ve just released a major enhancement to SpyCloud Investigations: AI Insights, built on the tradecraft and expertise of our team of seasoned cyber investigators.
SpyCloud Investigations with AI Insights leverages the power of IDLink™, SpyCloud’s proprietary identity correlation technology, to automatically analyze exposure data from breaches, malware, and phishing records to surface actionable, finished intelligence – enabling analysts to:
- Rapidly piece together relationships between fragmented identities
- Uncover hidden insider threats (including North Korean operatives)
- Summarize findings in seconds (saving hours of analyst time per investigation)
Whether you’re proactively threat hunting, responding to a malware incident, or analyzing patterns of digital behavior, this upgrade brings the intuition of a seasoned investigator to every case – no matter your team’s experience level. Request a demo to see how it works.
Recaptured data numbers for July
July monthly total
Total New Recaptured Data Records for July
919,595,979
New third-party breach data this month
Third-Party Breaches Parsed and Ingested
1,162
New Data Records from Third-Party Breaches
134,116,928
New recaptured phished data this month
Phished records:
2,565,751
New infostealer malware data this month
Stealer Logs Parsed and Ingested:
1,829,975
New Data Records from Stealer Infections:
15,622,321
New Stolen Cookie Records:
769,856,730
Stay in the loop
Our team at SpyCloud Labs keeps close tabs on the cybercrime ecosystem. Sign up to stay in the loop with our latest research.