The Future of Threat Intelligence is Not Traditional
Why SpyCloud?
SpyCloud turns the tables by making darknet data work for you. We detect when employee and customer data is in the hands of cybercriminals and automate the remediation to reduce your risk of cyberattacks.
Action-driven analytics
Get alerts that you actually want more of. Save time on tedious discovery and manual correlation with rich context in every alert to support triage, investigation, and remediation.
Deeper, darker, better
Unlock fast access for swifter action. SpyCloud’s security researchers recapture data from the deepest layers of the darknet within days of a breach or malware infection so you can act before criminals do.
Enterprise extensibility, seamless automation
SpyCloud scales not only with business needs but also with the threat landscape, allowing for fluid interoperability and robust coverage of gaps from legacy tools.
Richer Data, Better Intelligence, Empowered Teams
Quality data, ready for action
Traditional threat intel offerings are broad and can be collected from generally available darknet resources and forums. SpyCloud has the largest recaptured dataset of stolen credentials (30B+) and malware records (1B+) from the deepest layers of the dark web, and provides the shortest time-to-discovery, so you can stop attacks before criminals operationalize stolen data.
Enriched data insights and analytics, built-in
With SpyCloud, you don’t have to validate exposure or do further analysis to know whether or not exposed credentials put your organization at risk. We give you the needle, without the haystack, so you can proactively protect your employees’ digital identities, and your critical corporate data and IP.
Automated prevention and remediation
SpyCloud solutions continuously monitor for and detect exposures and enable automated remediation to reduce your risk of ransomware, account takeover, session hijacking, and online fraud.
Comparison
SpyCloud vs. Traditional Threat Intel
SpyCloud delivers the quickest evidence of compromise, with all the tools you need for immediate action and remediation to protect what matters most.
| SpyCloud | Legacy Threat Intel Provider | |
|---|---|---|
| What it’s good for | Actionability | Broad context |
| Time to remediation | Automated | Manual |
| Data collection sources | Sourced from from communities that require specialized expertise to infiltrate | Scraped with automated scanners primarily from public darknet forums and pastebin sites |
| Total passwords | 25B+ cracked, plaintext passwords enabling exact matches | No focus on password cracking, delivering data that’s not actionable |
| Email addresses | 35B+ | They don’t want you to know |
| Total PII assets | 80B+ | They don’t want you to know |
| Malware-Infected User Records | Billions, with millions recaptured each month | They don’t want you to know |
| Stolen cookies | Billions recaptured every month | They don’t want you to know |
Level-up by Layering on SpyCloud
Threat intelligence can be valuable – but it’s difficult to cut through the noise of what you need to act on. SpyCloud automatically gives you actionable evidence of compromise – saving your team time and resources by curating the data for you, giving you value out of the box, without needing to uncover it yourself.
01
Traditional threat intel gives you plenty of information, but puts the work on you to dig through it and figure out what’s worth your time and what isn’t. We do the hard part for you by only surfacing high-fidelity alerts that matter, in real-time.
02
The old way of doing things focuses on device-centric remediation of exposures and compromise. At SpyCloud, we recognize that modern threat protection extends to a user’s full digital identity – including applications, while also detecting compromised session cookies that can lead to session hijacking.
03
Modern security shouldn’t suck all your resources dry. With SpyCloud, take advantage of enriched insights and automated workflows that help your team – instead of burdening them further. With a robust ecosystem of out-of-the-box integrations, SpyCloud makes acting on the high value data easy and tailored to your preferred tech stack.
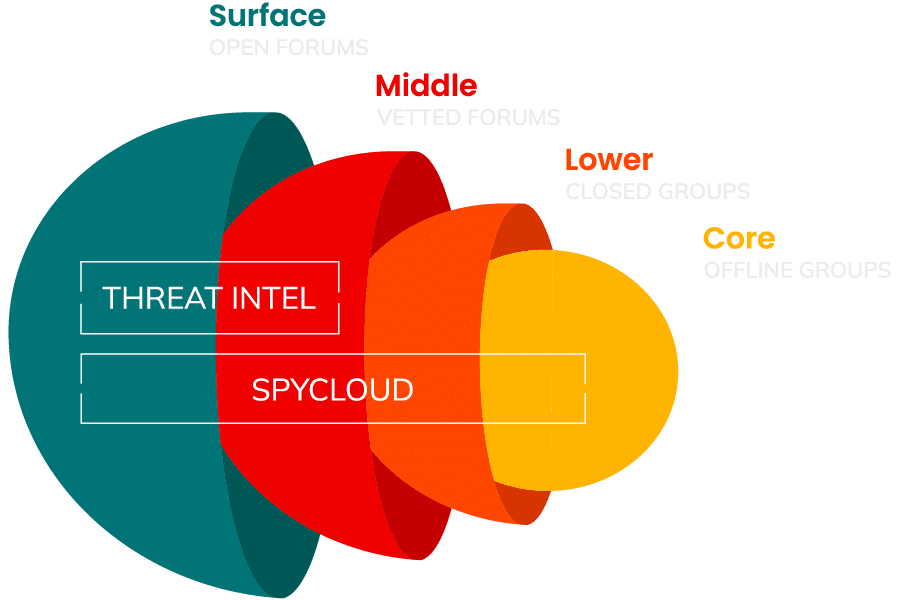
Focusing on the Deepest Layers of the Darknet
Without access to the data being shared in the lower and core layers of the darknet – closed, offline forums and small circles of criminals – security teams are flying blind. What data makes you a target? And what can you do about it if you can’t see what’s out there?
The truth is, the biggest risks to your business are in the places you don’t have access to – but SpyCloud does.
TRUSTED BY HUNDREDS OF MARKET LEADERS
“We’ve easily saved 1,000+ hours. Getting those hours back mean our security analysts can work on other valuable projects.”
– EBSCO Information Services
“SpyCloud’s amazing API allows us to automate the entire process. We are able to process 14,000 unique credentials per month. This scalability allows us to use our resources efficiently.”
– Atlassian
“We discover anywhere from 3,000 to 11,000 direct matches per hour. Every one of those exposed accounts could have led to account takeover.”
– Top 10 Booking Site
The SpyCloud commitment to customer success:
Success from day 1
Our technical account managers work with you for a smooth onboarding process to align on your desired outcomes.
Ongoing optimization
Your dedicated customer success manager will provide ongoing support at regular cadences to maximize your investment and discuss SpyCloud’s ability to help with other security initiatives.
Online chat
We offer global support and responses within 24 hours for any issues that arise during navigating our portal, calling our APIs, or responding to recapture data.
Make the Switch to SpyCloud
See the breach and malware exposures we’ve recaptured for your domain, and discover why SpyCloud is the trusted partner for 500+ global organizations.