Stop Impersonators in Their Tracks with Consumer Risk Protection
When up against account takeover attacks, you need to take fast action on compromised accounts, malware-infected users, and vulnerable web sessions. Stop criminals from using stolen passwords and cookies to bypass your robust security measures – including MFA – with the help of SpyCloud:
- Identify compromised users at account creation & login
- Prevent authentication sidestepping using stolen session cookies
- Automate ATO prevention to save time for more valuable activities
See SpyCloud in Action
Experience the new way to fight cybercrime
Your Customers Are NOT Who They Used To Be
The average user has 200+ online accounts that require a password, compared to 25 online accounts in 2007. As users create more accounts, they increasingly use poor cyber hygiene (re-used, easy to guess, and already compromised passwords). Cybercriminals are profiting while your customers’ exposures are impacting your productivity and bottom line.
New Accounts Create New Risk
Customers' Poor Hygiene is Your Problem
Cybercriminals are Becoming More Sophisticated
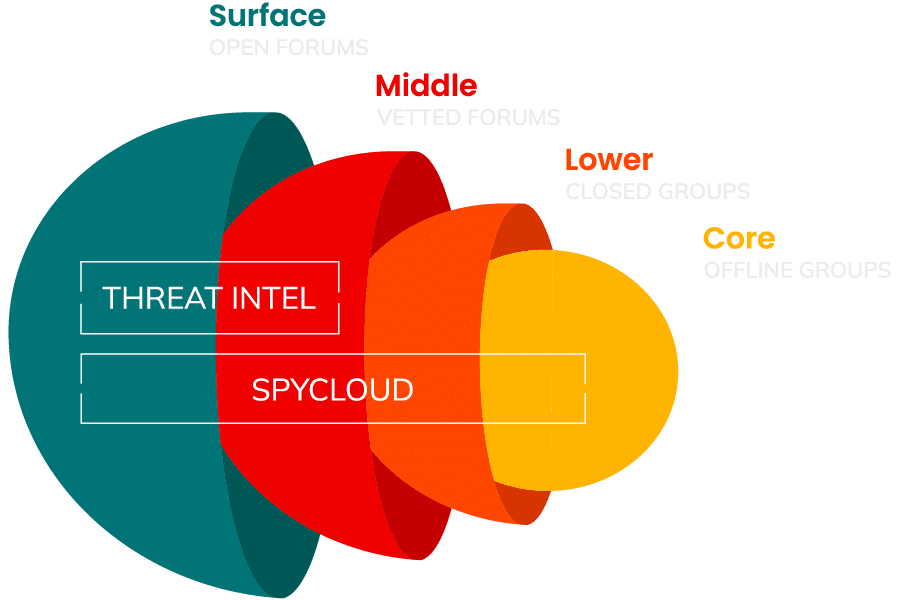
Focusing on the Deepest Layers of the Darknet
Without access to the data being shared in the lower and core layers of the darknet – closed, offline forums and small circles of criminals – security teams are flying blind. What data makes your consumers a target? And what can you do about it if you can’t see what’s out there?
The truth is, the biggest risks to your business are in the places you don’t have access to – but SpyCloud does.
Focusing on the Deepest Layers of the Darknet
Without access to the data being shared in the lower and core layers of the darknet – closed, offline forums and small circles of criminals – security teams are flying blind. What data makes your consumers a target? And what can you do about it if you can’t see what’s out there?
The truth is, the biggest risks to your business are in the places you don’t have access to – but SpyCloud does. We share what criminals are using today to perpetrate account takeover, data breaches, ransomware attacks, and online fraud. We enable you to react quickly to the data that’s being used against you. It’s finally possible to put an end to the cycle of cybercrime.

Surface layer
Most widely available data through pastebin sites or publicly posted breaches. This information is of low value and has typically been available in the darknet world for quite some time (most threat intelligence feeds stop here).
Middle layer
Where darknet data is distributed through vetted forums and where that data has been available for extended time periods. Often, the data has been cleaned and updated to make it easier to purchase and use in follow-on cyber-attacks.
Lower layer
Data is traded among closed groups of criminals and typically it’s hard to locate and access. Therefore it’s highly valued.
Core layer
Robust solutions for any use case
A simple check against the world’s largest repository of recaptured dark web data can save your customer – and by extension your business – from fraud losses.
Secure Account Creation
Enforce strong password policies and prevent new customers from reusing exposed credentials combinations at account creation to reduce the risk of credential stuffing attacks and improve their overall security hygiene.
Mitigate ATO Risk
Check for exposures tied to your user’s email address, username, password, or phone number. Balance security and user experience by taking action based on how many times a user has appeared in a breach, and if their plaintext password for your site matches one previously compromised.
Identify Malware Infections
Identify and flag victims of infostealer malware, prioritizing these high-risk accounts for monitoring or action such as requiring enhanced authentication, resetting passwords, or blocking transactions.
Prevent MFA Bypass
SpyCloud monitors malware logs for stolen session cookies tied to your domain that were exfiltrated from an infected device so you can invalidate still-active sessions, preventing criminal access that sidesteps MFA.
Experience the new way to fight cybercrime
Discover what cybercriminals know about your customers – and how those insights help you prevent cyberattacks and protect your bottom line.