ACT ON WHAT CRIMINALS KNOW
(...before THEY do)
SpyCloud levels the playing field by using the exact data cybercriminals have against them — enabling security teams to take immediate action on the users whose exposure in breaches and infostealer malware infections put their business at risk.
Check Your Exposure
On the next screen, you will see your company’s exposure from breaches & malware infections:
research SAYS: LOOK DEEPER AT Infostealers
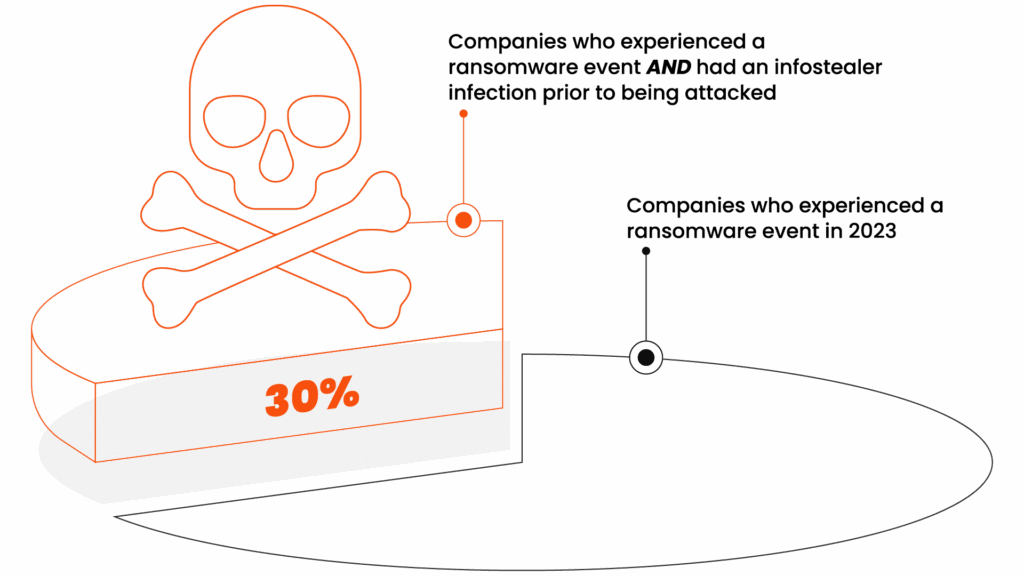
Our 2023 Ransomware Defense Report found that ransomware prevention remains at the top of the priority list. But most aren’t prioritizing the remediation of authentication data exfiltrated by infostealer malware. This is a big problem, since our analysis shows nearly one-third of companies who experienced a ransomware event had at least one infostealer infection before being attacked.
Why SpyCloud?
SpyCloud turns the tables by making darknet data work for you. We detect when employee and customer data is in the hands of cybercriminals and automate the remediation to reduce your risk of cyberattacks.
Action-driven analytics
Deeper, darker, better
Extensibility & automation
Focusing on the Deepest Layers of the Darknet
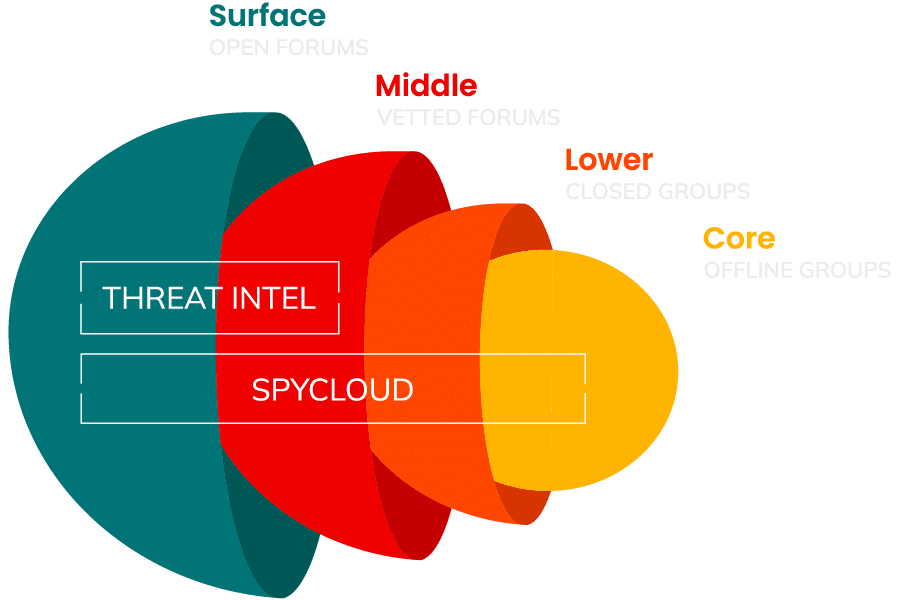
Without access to the data being shared in the lower and core layers of the darknet – closed, offline forums and small circles of criminals – security teams are flying blind. What data makes you a target? And what can you do about it if you can’t see what’s out there?
The truth is, the biggest risks to your business are in the places you don’t have access to – but SpyCloud does.
Focusing on the Deepest Layers of the Darknet
Without access to the data being shared in the lower and core layers of the darknet – closed, offline forums and small circles of criminals – security teams are flying blind. What data makes you a target? And what can you do about it if you can’t see what’s out there?
The truth is, the biggest risks to your business are in the places you don’t have access to – but SpyCloud does.

Surface layer
Most widely available data through pastebin sites or publicly posted breaches. This information is of low value and has typically been available in the darknet world for quite some time (most threat intelligence feeds stop here).
Middle layer
Where darknet data is distributed through vetted forums and where that data has been available for extended time periods. Often, the data has been cleaned and updated to make it easier to purchase and use in follow-on cyber-attacks.
Lower layer
Data is traded among closed groups of criminals and typically it’s hard to locate and access. Therefore it’s highly valued.
Core layer
Robust solutions for any use case
SpyCloud empowers security teams to take action – with dynamic insights on malware-infected devices, compromised users, and exposed applications, enterprises can proactively prevent ransomware, ATO and other targeted attacks, while efficiently remediating points of compromise.
Post-Infection Remediation
Augment malware incident response protocols to close entry points for ransomware attacks
Ransomware Prevention
Enterprise-ready protection from targeted attacks tied to malware
Automated ATO Prevention
Continuously detect and remediate compromised credentials
Session Hijacking Prevention
Prevent unauthorized access of consumer sessions and critical workforce applications
Threat Actor Attribution
Efficiently de-anonymize threat actors and tie them to their crimes
Fraud Prevention
Preserve account integrity throughout consumer digital experiences
Penetration Testing
Improve outcomes with accurate, enriched data from the criminal underground
Dark Web Monitoring
Experience the power of recaptured data to protect consumers & employees from dark web threats
Experience the new way to fight cybercrime
Discover what cybercriminals know about your business and your customers – and how those insights help you protect digital identities and prevent targeted attacks.