In the past 12 months, 75% of organizations have been hit by at least one cyber attack that caused real, material damage. Right now, 67% of Chief Information Security Officers (CISOs) say that the threat landscape is worse than it was a year ago. That’s according to “The CISOs Report: Perspectives, Challenges and Plans for 2022 and Beyond,” which outlines the biggest challenges for cybersecurity leaders and how they plan to defend their organization from an increasingly hostile threat landscape. The report, based on a survey of 400+ CISOs, identified several key issues facing security leaders and how they plan to address them.
Ransomware is Top of Mind for CISOs
Ransomware is one of the “most concerning” issues in cybersecurity today, with CISOs ranking it the highest out of the significant cybersecurity attack methods. That’s not a big surprise, with the average downtime from ransomware coming in at 23 days and the average loss racking up to $1.85 million. Ransomware is a global crisis, with over 600 million attempted attacks last year.
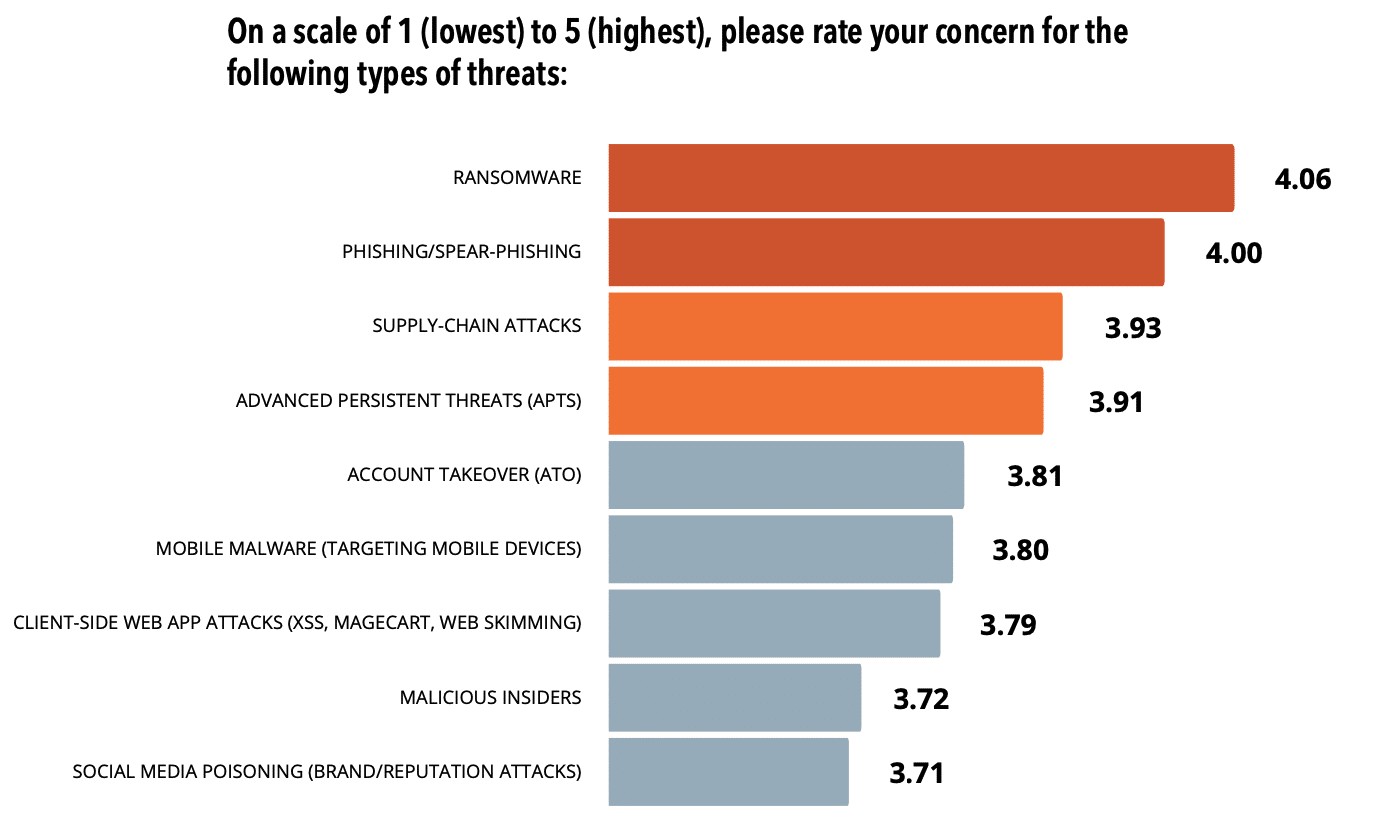
Weak or stolen credentials make a very common entry point for ransomware attacks and are considered one of the top riskiest vectors involved in security incidents, according to the SpyCloud Ransomware Defense Report. With Verizon’s 2022 Data Breach Investigations Report showing ransomware was present in 25% of breaches last year, remediating stolen passwords for users in your network makes them useless to criminals who seek easy entry into your systems.
Identifying these compromised user accounts and locking them down early helps you get in front of not only the ransomware threat, but also malware as a whole, as cybercriminals are increasingly using malware to siphon user information and use it for ransomware attacks. Having the ability to thwart ransomware and remediate infected users helps organizations prevent financial loss and brand damage.
CISOs are Going All In on Zero Trust
Zero Trust models have moved from hype to a critical priority, with CISOs rating the Zero Trust model as their top security investment for the next 12 months . In fact, 79% of CISOs indicated that they are already underway with their Zero Trust implementation and another 18% are actively planning it.
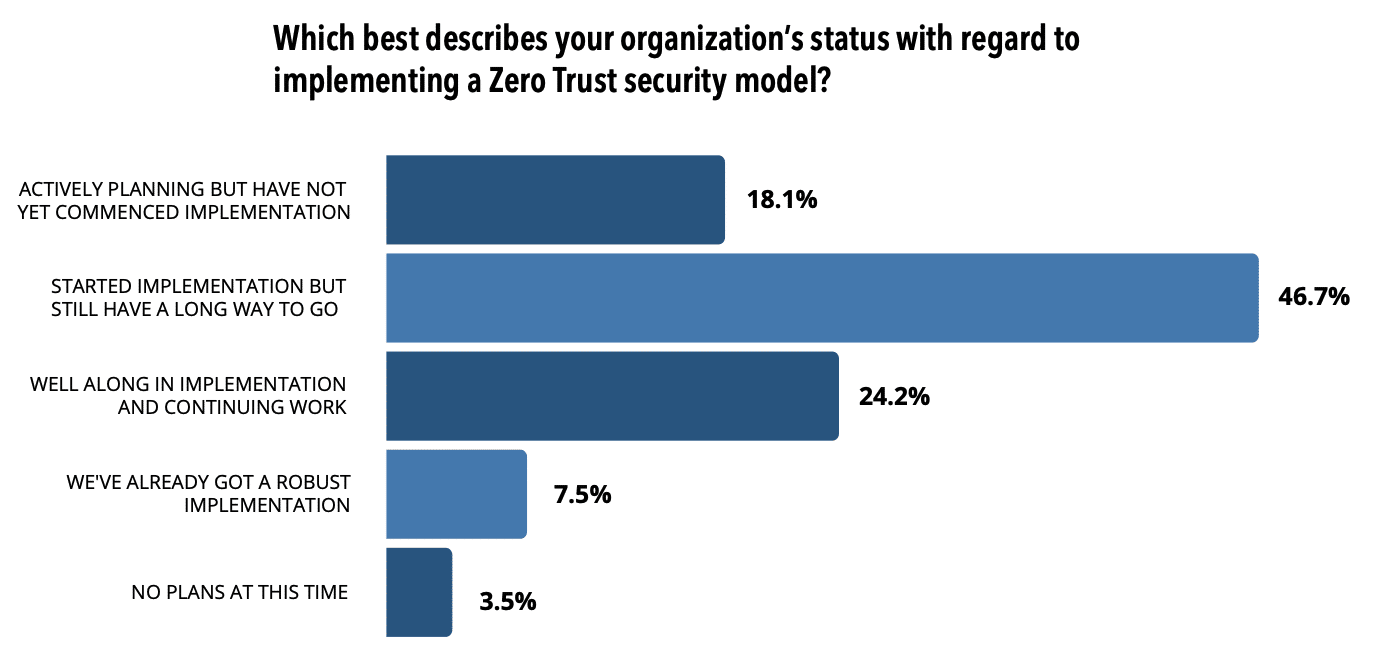
Older cybersecurity frameworks tended to assume that known networks were safe, threats came from outside the perimeter, and that knowing the location of a network or provider was enough to make it trustworthy. With its motto being, “Verify everything. Trust nothing,” the Zero Trust model understands that threats can come from anywhere and instead focuses on strictly controlling access through authentication for every device, user, and network flow.
Zero Trust continuously verifies the identities of users both inside and outside the perimeter – essentially making identity the new perimeter. With identity at the forefront of Zero Trust, data and insights into compromised identity information recaptured from the criminal underground are crucial for a successful Zero Trust implementation.
CISOs Seek Automated Solutions with Actionable Data
According to the survey, 41% of CISOs consider automation to be one of their top three goals, a statistic that has been steadily climbing over the past few years. Automation is valuable to these leaders as it allows for predetermined actions to be approved or denied and with a proactive lens on prevention and protection while minimizing the impact on security teams and other resources.
Automation is especially important because one of the major hindrances to getting the Zero Trust security model up and running is that there aren’t enough skilled cybersecurity professionals available. And the ones organizations have are frequently overwhelmed with constant alerts, irrelevant data, and labor-intensive tools. In fact, the top priorities when buying new security technology – ease of deployment, ease of use, high fidelity alerts and analysis, and automation – all focus on simplifying and streamlining cybersecurity.
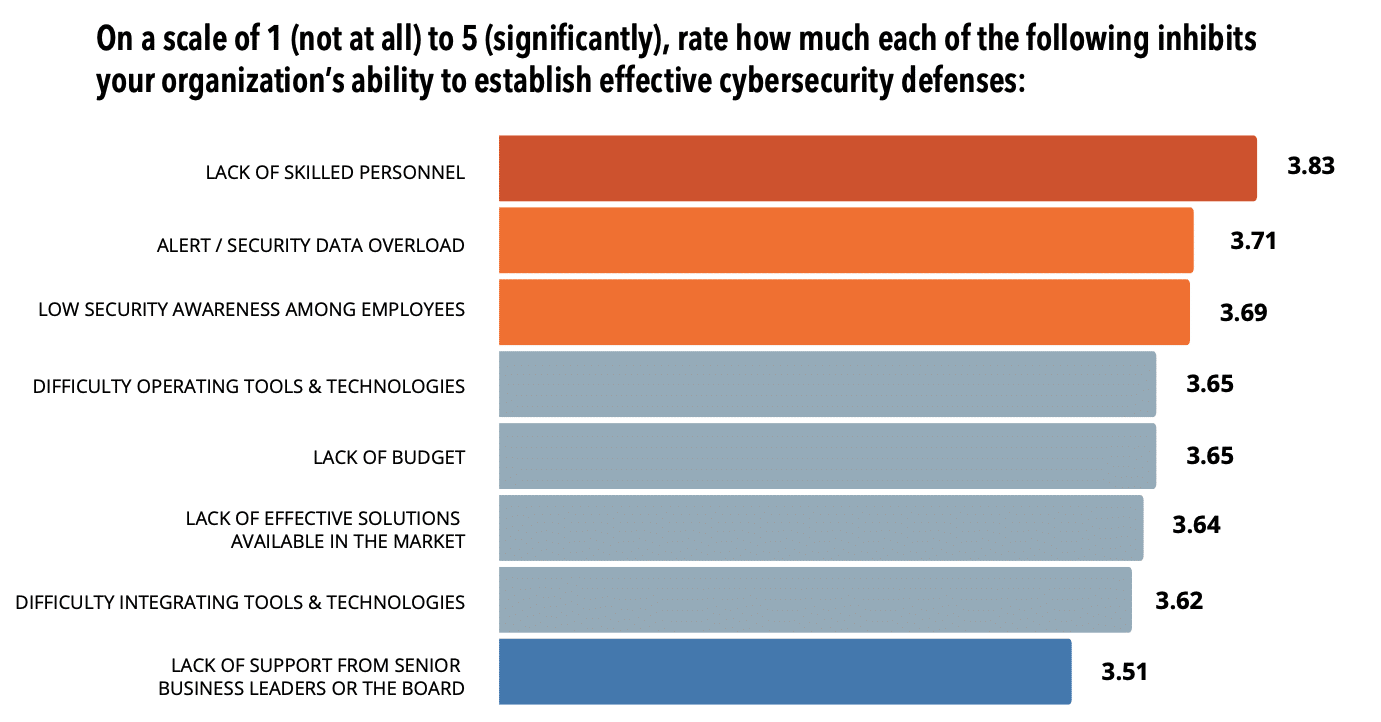
The problem isn’t just the people or the tools. Some aren’t accessing truly actionable data when they need it most. The earlier security practitioners and decision makers can get access to data recaptured from the criminal underground (the same data fraudsters have access to), the more likely it is that they can get ahead of cyber attackers before they get too far. One of the things many CISOs find they need is a security solution that can provide the tailored security data that they actually need to have a proactive, automated response.
Conclusion
From increasing cyber attacks to the seemingly endless number of cybersecurity solutions on the market, CISOs have a lot that keeps them up at night, but there is hope. As bad actors continue to threaten organizations with ransomware, CISOs recognize the need to take a proactive approach to defending against it, and we find the best way to do that is by stopping precursor attacks like data breaches and account takeover, which stem from the use of stolen data (including compromised credentials). The implementation of Zero Trust models will help address concerns about defending identity as the perimeter while the use of automated solutions that offer actionable intelligence will alleviate the talent shortage challenge.
In addition to these key priorities, the survey found that CISOs are also focused on the following in the next 12 months:
- Ensuring the privacy of customer data
- Better addressing partner risk
- Measuring their security program’s effectiveness

