Stealer[Info]
Everything you need to know about the infostealer malware behind today’s biggest identity-based threats
See recent malware exposures that could impact your organization.
Identity is the new perimeter, infostealer malware is the bad guy that sneaks in
If identity is the new perimeter in cybersecurity, infostealers are the gate-crashers that slip past defenses and dismantle that perimeter from the inside out.
Infostealer malware siphons the very artifacts that form a user’s digital identity, from credentials, session cookies, and browser fingerprints to autofill data. With these assets in hand, attackers can impersonate employees and sidestep MFA, EDR, and other defenses to launch ATO, session hijacking, ransomware, and online fraud campaigns.
The stealthiest stealers that are causing enterprises the biggest headaches
Ninety-five percent of identity teams are “extremely or significantly concerned” about data siphoned from malware-infected devices being used for more harmful attacks, and rightfully so.
About 1 in 2 corporate users have already been infected on their professional or personal devices. See the latest infostealer exposure data in this year’s report.
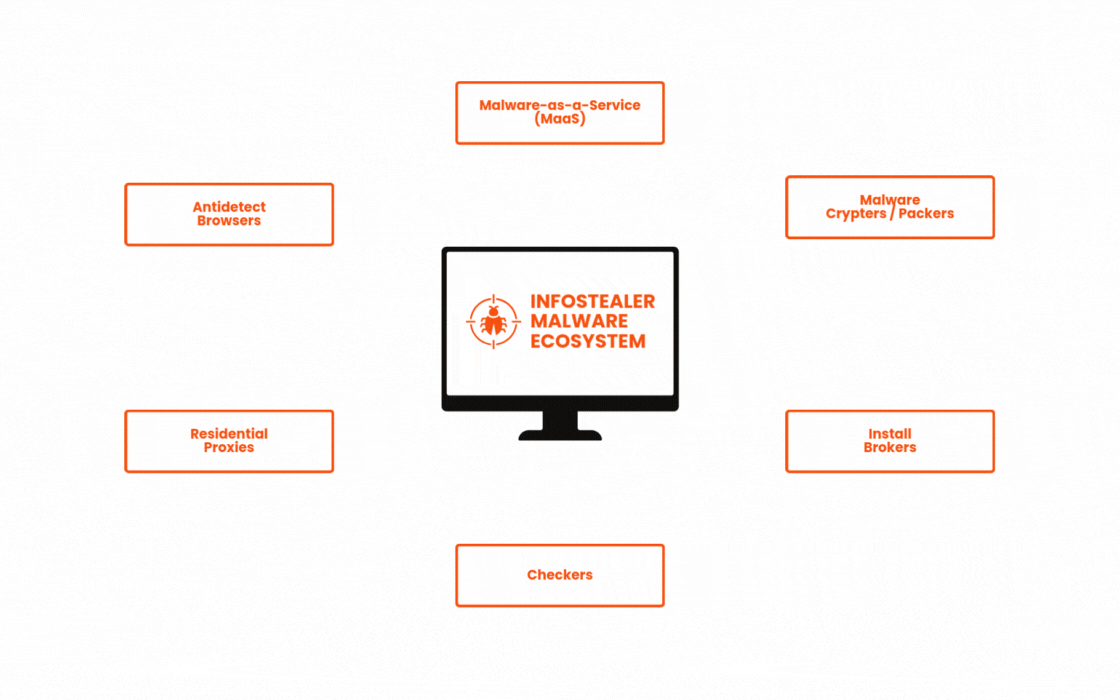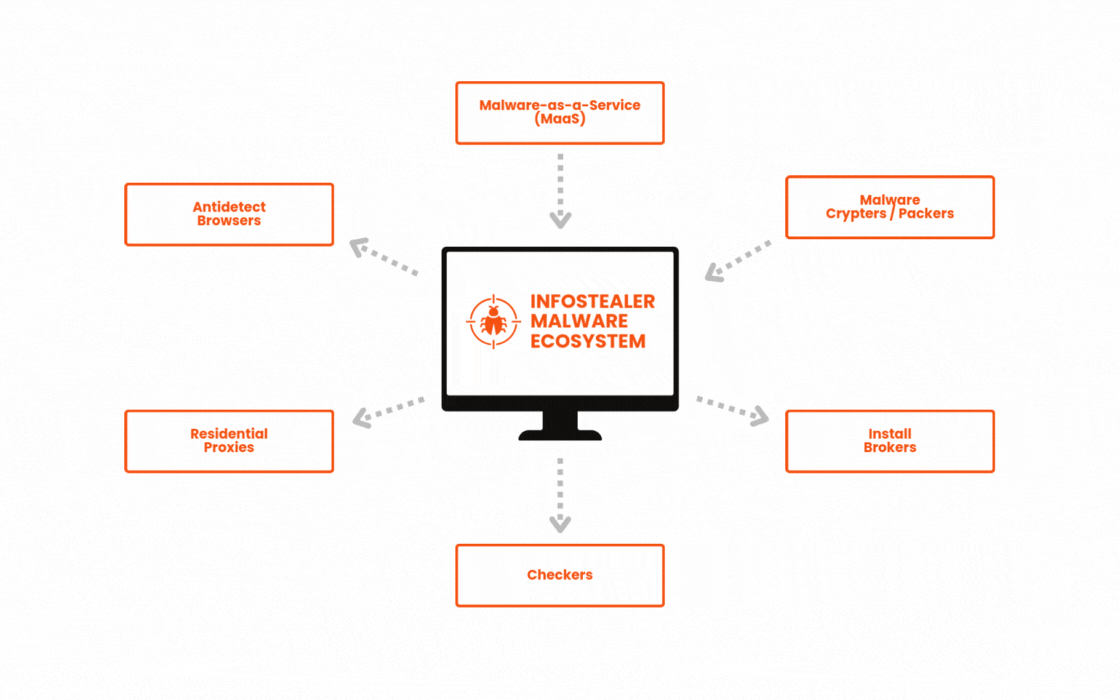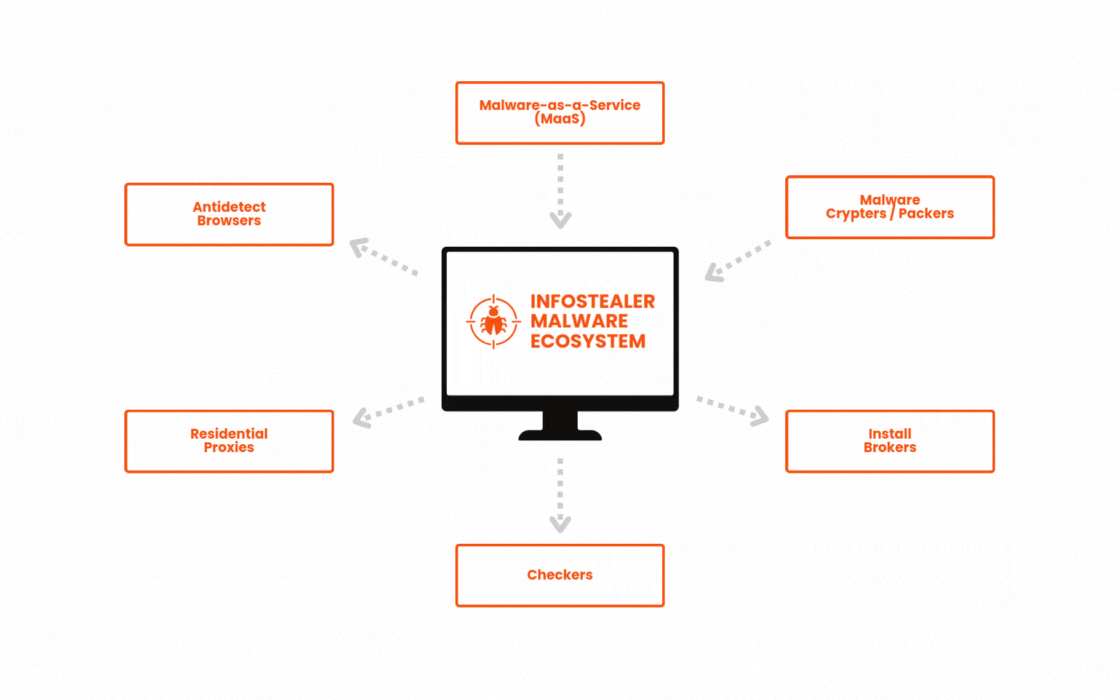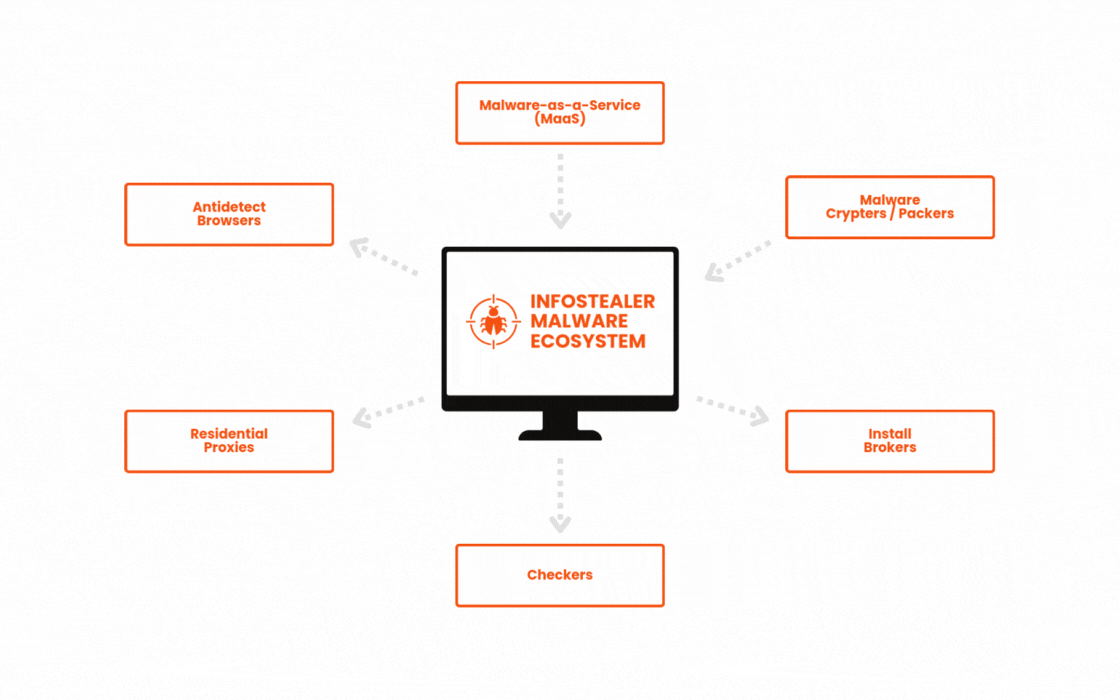
What else goes on behind the scenes: MaaS and cybercrime enablement services
Cybercrime has evolved from a DIY operation for highly-skilled threat actors into a sprawling $9 trillion industry where even low-skilled criminals can succeed. Where threat actors once needed technical sophistication, they can now easily outsource through an ecosystem of cybercrime-as-a-service offerings. In this landscape, criminals quickly and easily deploy infostealers at scale.
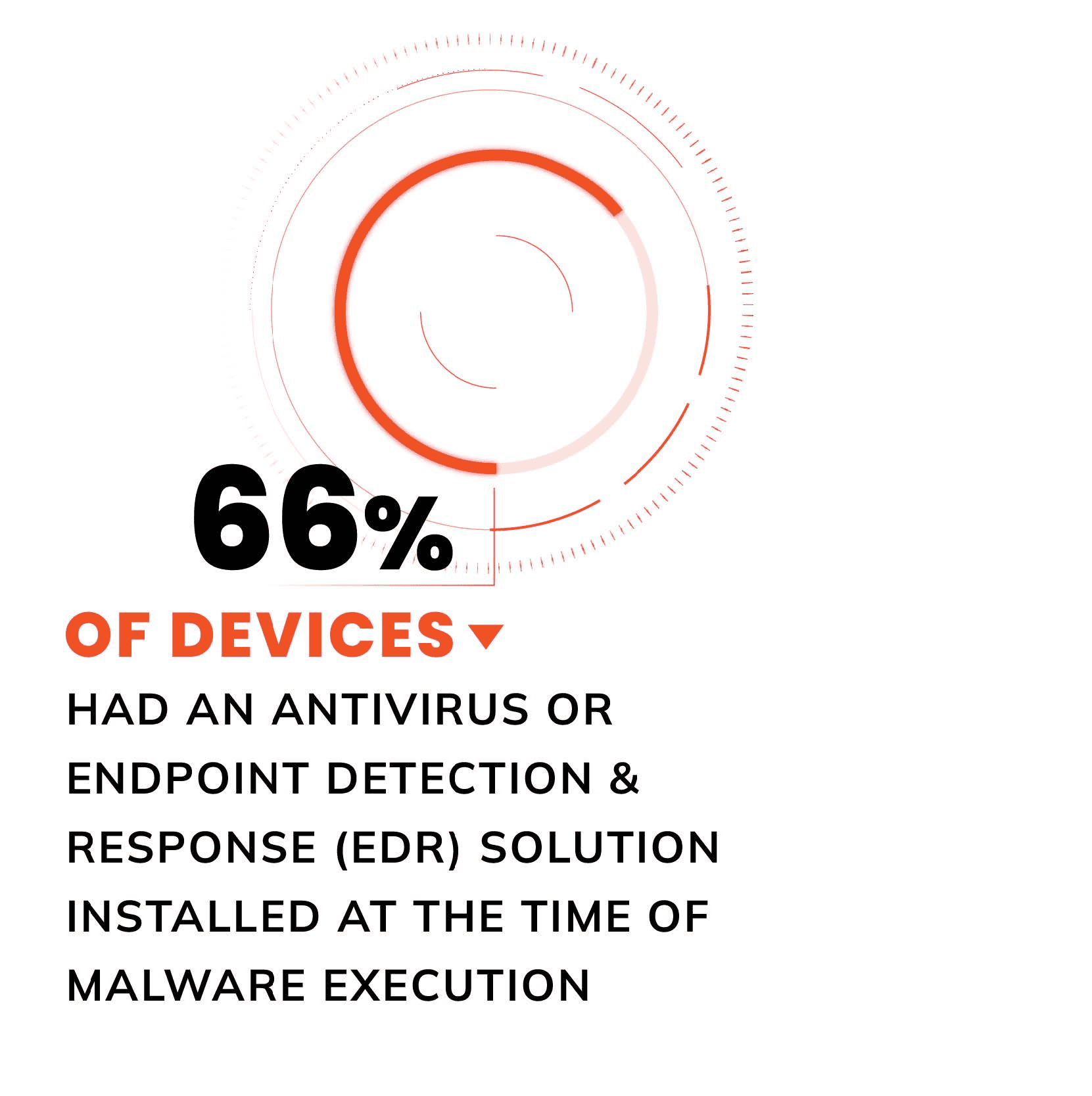
What AV & EDR tools miss – and you should know
When you get down to it, infostealers are fueling identity attacks more than you probably think. Since the start of this year, our researchers have positively identified that at least 66% of infostealer-infected devices had an antivirus or EDR solution installed at the time of a successful infection – highlighting a critical gap in endpoint protection.
Tips and best practices: Post-infection malware remediation
While identity represents the frontline of modern security – what you know, what you are, and what you have – malware is the tool attackers use to quietly and effectively erode trust in those identities. And because the compromised data lives on after the infection is gone, the threat doesn’t end when the device is wiped.
Post-infection remediation is your best defense for making sure that stolen identity data can’t be weaponized by attackers for account takeover, fraud, session hijacking, or ransomware.
Other new & emerging malware research
Our team at SpyCloud Labs keeps a concentrated focus on the infostealer malware ecosystem, tracking and analyzing existing threats, new trends, and evolving tactics. Here’s some of our latest work.