2022 Ransomware Defense Report Insights
The looming threat of ransomware has become a “fact of life” for organizations of all sizes, and the continuing escalation of this threat means security teams can’t become complacent. SpyCloud’s new 2022 Ransomware Defense Report shows that organizations are losing ground to threat actors – and they still have gaps in their security controls.
One of the most surprising findings from our survey of more than 300 security leaders from the US, Canada and the UK was that organizations are still leaving gaps in their layered defenses. Survey participants ranked common tactics such as data backup and user awareness and training as the most important countermeasures, while other critical defenses, such as monitoring for malware-stolen cookies that enable session hijacking, were ranked as less important.
Yet, as the findings clearly show, the typical defenses aren’t stopping the bleed. Survey respondents plan to upgrade and invest in even more solutions, but may not realize what they’re missing from the equation – our thoughts on that below.
The Missing Defensive Layer
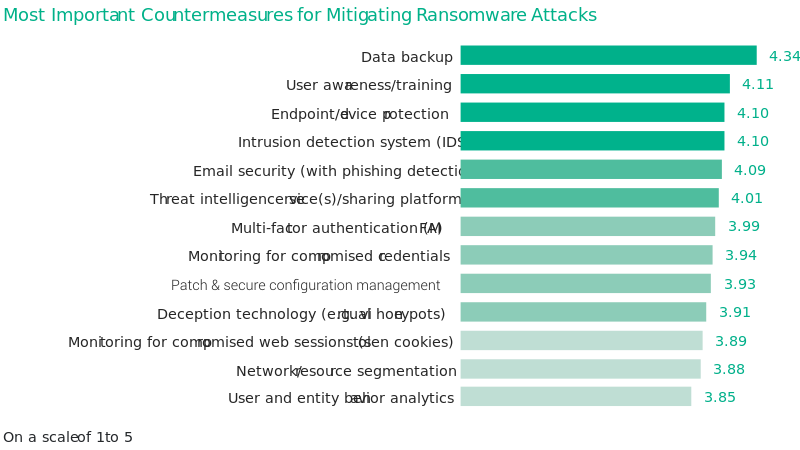
Cybersecurity practitioners have long understood that effective defenses against threats require a broad range of controls. Among our survey respondents, the most valued defensive measures are:

Data
backup

User awareness
and training

Endpoint
security

Intrusion detection systems

Email
security
This approach is not surprising, as it provides blanket coverage for the most important and highly targeted assets: data, people, network and email. However, these common technologies are no longer sufficient to keep up with ransomware escalation, as our data shows. Nor do they defend against hidden threats.
One of your biggest hidden threats – and greatest risks – is devices infected with infostealer malware. Designed for harvesting data including credentials, web session cookies and soon, passkeys, from the infected device, infostealers are a favorite tool of malicious actors whose job is to find entry points into organizations. Ransomware operators typically hire specialized groups called initial access brokers to provide them access to their targets. With the prevalence of malware infections, the success rate of infiltrating a target is exponentially greater because the freshly harvested data directly from an infected machine is current and accurate.
Stolen session cookies pose a huge risk because ransomware attackers can use the cookies to highjack a session (even SSO instances), impersonate an employee, and bypass multi-factor authentication. That’s a primary reason why malware infections are often a precursor to ransomware attacks. But, according to our survey, security teams’ perception of stolen cookies is that they’re one of the least riskiest entry points for ransomware.
The risk is even greater for unmanaged devices because security teams have no visibility into those endpoints – and a single infected device could expose access to dozens of your corporate applications. In fact, analysis of botnet data recaptured by SpyCloud this year found up to 26 applications compromised from a single malware infection.
Also Missing in Action: Post-Infection Remediation
Given that endpoint protection is high on the priority list and monitoring for compromised web sessions is low, it’s safe to assume organizations are overlooking a critical step in the fight against ransomware: post-infection remediation. Endpoint detection and response (EDR) and application security management (ASM) tools may help you detect malware and eradicate it from your environment, but they don’t provide a full picture of your ransomware risk, such as visibility into exposed third party applications or unmanaged devices. Based on SpyCloud research, up to 75% of compromised assets are invisible to organizations.
On top of that, these tools don’t offer full protection against ransomware in the long term. For instance, wiping an infected device does nothing to protect from risks stemming from compromised applications. By the time your endpoint or application security software alerts your security team about a malware infection, the stolen credentials, cookies, and other data is already in the hands of perpetrators and could have been for months before the infection was detected and remediated.
Your employee’s freshly harvested data could be weaponized against your organization to launch ransomware attacks. But without the right visibility and data about each exposed device, application, and user, you won’t find out about your exposure until malicious actors leverage the stolen data against your organization.
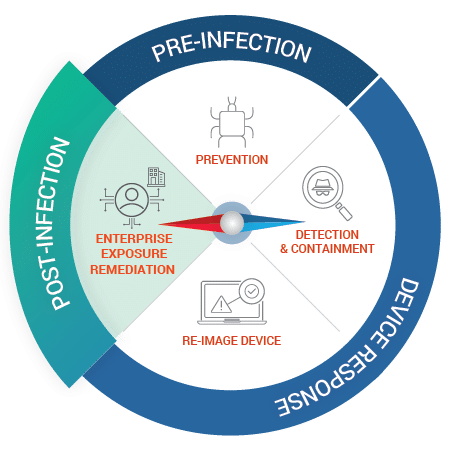
Focus on Prevention
We’ve seen ransomware operators grow savvier and more prolific in the past year, and this trend is reflected in the decreased optimism among our survey respondents:
- Despite organizations increasing security budgets to defend against ransomware, 90% of those surveyed were affected by ransomware at least once in the past year, up from 72.5% the previous year. We also saw a big jump in the number of those affected more than once: 78% vs. 52% in last year’s survey.
- Across the board, organizations are feeling a lot less confident in their various security solutions and more are implementing “Plan B” – which indicates that they realize an attack is inevitable. For example, 72% purchased cyber insurance to pay for damages related to a ransomware attack (compared to 50% the previous year) and 45% retained a crypto account (compared to 36% in 2021).
- Respondents ranked all potential entry points for ransomware as more concerning, compared to the previous year. Unpatched vulnerabilities, phishing emails with infected attachments or links, and unmanaged devices are the top three concerns.
But it’s not all doom and gloom. We did find some silver linings in this year’s ransomware survey. For instance:

Inadequate budgets and lack of board support are no longer barriers in fighting ransomware. Board support actually grew compared to the previous year.

Organizations now realize that credentials are at the forefront of employee identity protection – we observed a 71% jump in the number of organizations using multi-factor authentication and a 65% increase in monitoring for compromised employee credentials.
While these are positive developments, organizations need to work on the missing key component in the ransomware fight: prevention through early detection of malware-infected devices.
Learn More
Understanding the hidden risks and threats is the best way to gain an upper hand in the fight against ransomware. Get more insights about the current ransomware trends and the weaknesses that are impacting your peers in the 2022 Ransomware Defense Report, and don’t miss our webinar that breaks down key findings from the report.
