SpyCloud Integrations
Maximize efficiency and streamline workflows with out-of-the-box integrations that enable enterprises to leverage their existing tech stacks to centralize data and make informed, actionable decisions.
Seamlessly integrate into your preferred technology solutions & business-critical applications.
SpyCloud surfaces darknet exposures specific to your users, with continuous collection and dynamic correlation that reveals risks previously unseen. Take action to prevent cyberattacks, secure business data, protect both employee and consumer credentials, and accelerate cybercrime investigations.
SpyCloud’s API integrations work with top technology vendors across SIEM, SOAR, XDR, TIPs and more – delivering Cybercrime Analytics at scale to automate:
- Triage and escalation
- Ops and incident response workflows
- ATO and ransomware prevention
- Post-Infection Remediation
- Investigate anomalous activity
- Centralize intelligence collection
Anomali Threatstream
Improve your view of overall security risk with SpyCloud’s cybercrime analytics layered into Threatstream threat intel.
Ingest SpyCloud breach and malware records into Anomali Threatstream to view exposed credentials for your enterprise domains. Accelerate your incident response process to prevent targeted follow-on attacks using information in the hands of criminals.
USM Anywhere
Detect and remediate compromised passwords exposed from malware and third-party breaches.
SpyCloud AlienApp enables you to seamlessly integrate SpyCloud’s breach and malware exposure alerts into USM Anywhere – delivering actionable recaptured darknet data to protect your business from cyberattacks.
With the AlienApp for SpyCloud you can:
- Get alerts and take action when user credentials are exposed on the darkweb.
- Safeguard your executives personal accounts and privileged users accounts (e.g. IT admins).
- Prevent bad password hygiene.
The AlienApp for SpyCloud is available to all USM Anywhere users and the API will feed into your existing workflow.
Chronicle SOAR By Siemplify
Incorporate SpyCloud’s powerful Cyber Analytics Engine to access darknet data.
Easily integrate SpyCloud’s Cyber Analytics Engine of 500+ billion recaptured darknet assets into your Chronicle SOAR By Siemplify to enrich the data available to you during your incident response workflows. This will empower your teams to maximize efficiency and make informed decisions with confidence.
Cisco SecureX Threat Response
Cloud-native SecureX integrates the Cisco Secure portfolio with the entire security infrastructure – speeding detection, response, and recovery.
Cisco SecureX delivers a consistent, built-in experience across your products. Get unified visibility, intuitive automation, and robust security for your entire security portfolio. The SecureX Threat Response SpyCloud Module empowers users to initiate an investigation into a SHA256. The module adds context around a compromised email and username associated with that email and context about a user for an environment. If the Cisco Secure Email module is enabled, then it returns that this SHA256 has been sent to, for example, these email addresses have been seen in the data breaches.
Devo
Integrate SpyCloud consumer records into Devo’s workflow to strengthen account security and reduce ATO.
Stay ahead of customer ATO by detecting and resetting exposed consumer passwords early in the breach lifecycle, heading off account takeover attempts. SpyCloud’s recaptured data illuminates risks you didn’t even know you had across your enterprise, vendors, and customers - so you can take immediate action.
Jupyter Notebook
Enhance your instance of SpyCloud investigations with pre-built Jupyter Notebook templates. View potential trouble spots and filter the data to highlight the most actionable records and optionally export those records into a CSV for sharing or use in other tools.
Maltego Enterprise
Pivot using SpyCloud’s extensive dataset of breach and malware data.
SpyCloud Investigations Integration for Maltego enables analysts to efficiently piece together decades-worth of criminals’ digital breadcrumbs to de-anonymize specific threat actors engaging in cybercrime, financial fraud, and other illegal activities. With this powerful integration, you can:
- Access high-volume darknet data
- Shorten the timeline of your investigations
- Discover previously unknown and anomalous connections between entities
Active Directory, Microsoft
Detect and reset Active Guardian passwords automatically.
Automate Active Directory protection out of the box using SpyCloud Active Directory Guardian. It includes two components that can be used together or separately to prevent, detect, and reset weak or compromised passwords automatically.
- The password filter prevents employees from setting weak passwords that could put corporate resources at risk. When an employee sets a new Active Directory password, the password filter automatically screens their choices for repeated or sequential characters, up to 50,000 custom dictionary words, and any previously-exposed passwords that SpyCloud has recaptured from the dark web.
- The scanner checks employee credentials for exposures on an ongoing basis. Security teams can schedule automated scans to check for compromised credentials, custom banned passwords, 1,000 “fuzzy” variations of banned and exposed passwords, and any previously-exposed passwords.
Together, they provide prevention (password filter) and detection (scanner). The password filter prevents employees from setting weak or compromised passwords in the first place, and the scanner detects and resets additional exposures as new exposures occur over time.
PingOne DaVinci
Secure employee identities by checking for exposed credentials within SpyCloud’s dataset.
Corporate account takeover via exposed credentials poses a substantial risk to enterprises. Prevent an employee from choosing an exposed password within Ping DaVinci. Check to see if an email/username and password are exposed when building a new user, updating passwords, or other identity flows.
Polarity Platform
Knowledge and data is spread across disparate systems and fuses them into one unified view.
Polarity isn’t just another tool teams can add to their toolkit. It’s a unified view of all the tools, data, and knowledge that they use every day, and follows users throughout their workflow, eliminating the need to switch between endless tabs or search through chat/email history to complete a task. Polarity revolutionizes how teams work, what they spend their time doing (completing tasks, not searching for context), and how informed their day to day decisions are. Mutual customers can operationalize SpyCloud’s database of nearly 500B recaptured darknet assets.
ShadowDragon Horizon
Prioritize remediation efforts with ShadowDragon’s vulnerability intelligence.
Gain better understanding of threats facing your organization and dramatically increase the accuracy and speed of investigations within ShadowDragon. SpyCloud provides the context and insights to help prioritize your investigations, identify the root cause of security incidents, and remediate any vulnerabilities. This powerful combination helps analysts identify the identities of criminals and stop any targeted cyberattacks and follow-on attacks.
Splunk Enterprise and Cloud
Access and download SpyCloud apps and add-ons to your Splunk instance.

Swimlane
Streamline security operations and build automated flows with SpyCloud’s breach data.

Ingest SpyCloud breach data into Swimlane playbooks to prevent employee ATO. Develop playbooks for complicated security operations workflows, using a simple drag-and-drop action. Get breach data for your watched domains to call by domain, email, IP, password, username, or other SpyCloud identifiers.
ThreatConnect
SpyCloud is proud to be one of ThreatConnect’s Data Enrichment Partners. With this integration, users can:
- Operationalize SpyCloud’s powerful Cyber Analytics Engine that contains billions recaptured darknet assets.
- Automate logging and remediation tasks when an exposure is detected by SpyCloud.
- Leverage additional ThreatConnect integrations for further enrichment or triage.
Synapse Enterprise
Query, ingest, and visualize data for SpyCloud Investigations with the Synapse-SpyCloud Power-Up.
Enhance your investigations and attribute cybercrime faster by enriching your existing threat intelligence sources. Synapse Enterprise customers can use the Synapse-SpyCloud Power-Up to query, ingest, and model indicators found in SpyCloud’s comprehensive breach database.
Custom Integrations
We have options if there is not a pre-built integration for your specific toolset or use case.
SpyCloud provides custom, high-volume APIs with simple configuration to help you integrate our Cyber Analytics Engine to use in with your current tech ecosystem. Contact us to to become one of our Technology Partners.
The SpyCloud API was super easy to integrate. It took a day and a half for our engineers, and then it was just up and running. We’ve had the integration in place for a year now and had zero issues, zero downtime. On the technology side, it’s an enterprise-grade API for us.
FINTECH
SpyCloud Enabled a Global Fintech Company to Protect Thousands of Vulnerable Accounts Representing Tens of Millions of Dollars
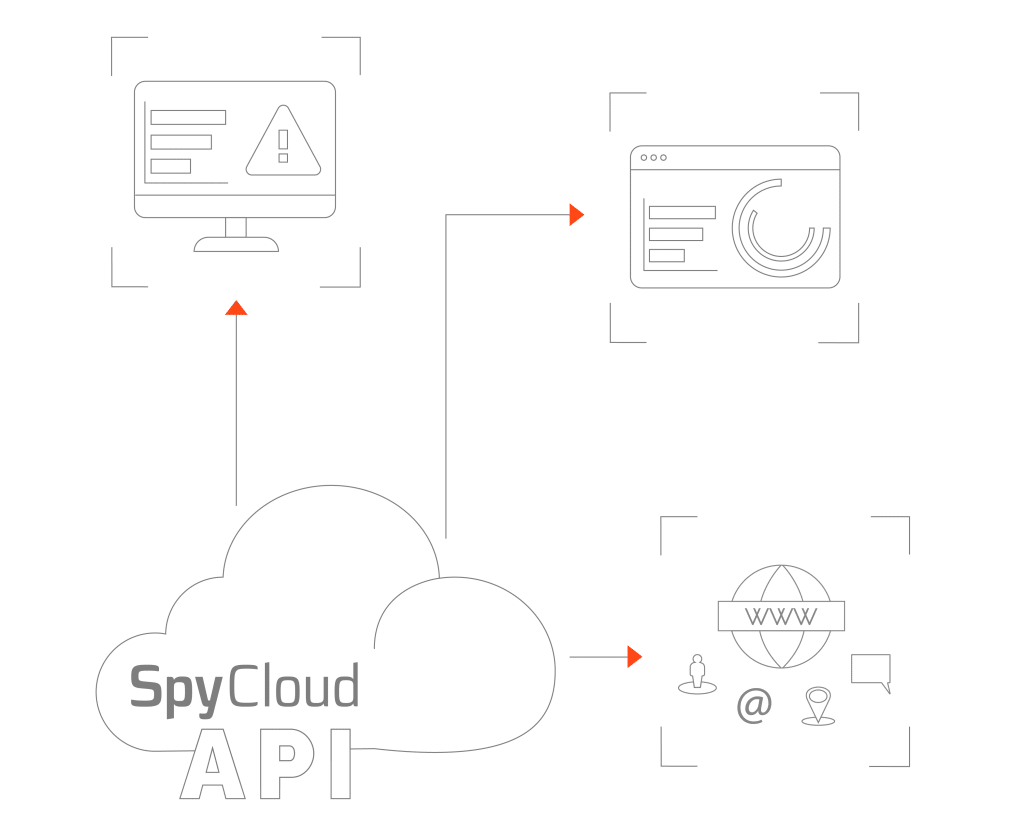
How It Works
SpyCloud’s Cybercrime Analytics engine ingests and analyzes 25B+ darknet assets per month and delivers automated insights via REST-based APIs. Our APIs include easy-to-understand, resource-oriented URLs, and use HTTP response codes to indicate API errors. All API responses return JSON, including those with errors.
Any application with the ability to query an external API endpoint can integrate SpyCloud data. Once the application has been configured to query the SpyCloud API within appropriate parameters, such as providing an email or target domain, the results will be mapped to appropriate fields within your solution.
You might like:
Cybercrime Analytics
Discover why market leaders across all industries are choosing Cybercrime Analytics over threat intelligence – so they can move beyond context and take action.

2024 Annual Identity Exposure Report
Each year, SpyCloud analyzes the billions of identity assets we recapture from the darknet and shares data breach, malware & identity threat insights in this report. Here’s what we found.

Malware-Infected User Response Guide
Handy guide to decipher what it means when employee or consumer information appears on a botnet log, and how to contact infected users with an action plan.
Account Takeover 101
You can’t stop ATO until you understand it. Get this plain-English primer on the latest attack methods, bad habits that increase ATO risk, and strategies for prevention.
Don’t see your preferred technology vendor?
SpyCloud’s solutions aim to support a vendor agnostic technology ecosystem that maximizes enterprise extensibility. Contact us to learn more about custom integrations.

