With an increase in online fraud threats, accelerated by consumers’ digital adoption during pandemic shutdowns, businesses need confidence that the users interacting with their websites are legitimate. Given the constantly-shifting nature of criminal activity, even the most sophisticated fraud prevention programs struggle to separate good users from bad actors, particularly when criminals use stolen data to sidestep traditional fraud prevention measures.
Today, we’re expanding SpyCloud’s offerings with a new solution to help enterprises prevent criminals from using stolen data to create false identities and get away with fraud. SpyCloud Identity Risk Engine is a fraud prevention tool that draws on data from the criminal underground to assess user risk – something no other solution on the market can offer. It can be layered into an existing control framework to help fraud teams make more accurate decisions, enabling them to prevent more fraud and let more good business through uninterrupted.
Identity Risk Engine delivers actionable analytics that help organizations:
- Predict fraud tied to malware – Detect when consumers have had their personal data stolen by malware, putting them at elevated risk of fraud
- Detect synthetic identities – Spot irregularities in a user’s information suggesting that the identity has been stolen or created using persona data available to criminals
- Anticipate account takeover – Identify warning signs that consumers are at high risk of account takeover, such as high rates of password reuse across their accounts
Check out our video to learn more about how Identity Risk Engine helps enterprises stop hard-to-detect fraud.
How SpyCloud Identity Risk Engine Can Strengthen Your Fraud Control Framework
SpyCloud Identity Risk Engine can help enterprises make more confident fraud decisions for a variety of different scenarios. Here are just a few examples.
Scenario #1: A surge of new account enrollments come in. How can you tell which ones are legitimate?
A common challenge we’ve heard from customers since the onset of the pandemic is understanding how to handle an influx of new account signups. While many of the new enrollments come from real users expanding the services they use online, many also come from cybercriminals. The problem is significant: one in every 11 new account creations is potentially fraudulent, according to Lexis Nexis.
Fraudulent account creations are often difficult to detect because criminals enroll using legitimate data stolen from real users, typically combined into synthetic identities. The firehose of new registrations exacerbates the challenge of weeding out bad actors without slowing down the enrollment process for legitimate new users.
Identity Risk Engine helps enterprises detect risky account creations by flagging when a new user’s information includes anomalies that suggest the identity has been stolen or constructed. Enterprises can call the API during the account creation process to support other identity verification processes such as Know Your Consumer (KYC). In addition to a score indicating the user’s risk level, Identity Risk Engine also returns reason codes that explain why the account has been flagged as suspicious.
One in every 11 new account creations is potentially fraudulent.
Scenario #2: A customer transacts via guest checkout. Should you let the purchase go through?
Guest checkout reduces friction for casual shoppers, but can provide limited information to support fraud decisions. Without an account to provide historical information, it can be difficult to determine how to proceed with the transaction. Fraud prevention controls can help, but typically offer limited protection if a bad actor has recycled stolen data that belongs to real users.
Identity Risk Engine takes some of the guesswork out of evaluating guest checkout transactions by enriching the data available to your fraud team with insights drawn from recaptured underground data. SpyCloud distills billions of data points into a clear risk signal by correlating identity information and analyzing factors such as the recency and scope of previous exposures, password hygiene, evidence the user’s data has been collected by malware, and other key risk indicators. With the risk score and reason codes SpyCloud delivers, you can make a confident decision about whether to let the order go through, prompt the user for additional identity verification, or reject the transaction.
Using recaptured underground data to assess fraud risk can help you not only reduce fraud, but also reduce manual review rates. One retailer in the beta for this product found that they could have avoided manual review for 76% of the orders they tested with Identity Risk Engine.
“We could have avoided manual review for 76% of the orders we tested with Identity Risk Engine.”– Large Retailer
Scenario #3: Some of your customers unknowingly use devices infected with malware. How can you prevent criminals from using their data for fraud?
It’s a silent threat: a user logs in with their usual browser, location, and credentials, or perhaps even a stored cookie. No alarms are raised and nothing seems amiss – until weeks later, when the real account holder issues a chargeback or reports other fraudulent activity. After the fact, the fraud team may or may not discover that the reason the fraudulent transaction slipped past their defenses was because the original user’s data had been siphoned by malware and was used to steal their accounts and identity.
Data collected by credential-stealing malware makes it easier for criminals to bypass anti-fraud measures. Each consumer whose data has been collected by malware is at significant risk of account takeover, identity theft, and other forms of online fraud.
Unlike any product on the market, Identity Risk Engine can identify high-risk users ahead of time, helping to prevent fraud losses tied to malware infections. Across the customer beta tests we performed during this product’s development, Identity Risk Engine revealed that about 1% of tested consumer accounts had been affected by malware. By identifying that criminals have access to customers’ browser fingerprints, exact credentials, and sensitive information, you can proactively flag their account or take action before ATO and fraud can occur.
According to our customer beta tests, Identity Risk Engine revealed that about 1% of tested consumer accounts had been affected by malware.
Scenario #4: An existing account holder logs in and changes their address. Did they move, or was their account taken over?
Account takeover represents a huge problem for enterprises, and a lucrative opportunity for criminals. Last year alone, SpyCloud recaptured 1.7 billion credentials from the criminal underground, and 70 percent of users with more than one password in our database had reused them. Criminals test these passwords against online accounts, which they use to drain funds, steal loyalty points, make fraudulent purchases, resell, and monetize in any other way they can think of.
For years, SpyCloud has been a leader in account takeover prevention because we enable enterprises to detect and reset compromised credentials – but with the addition of Identity Risk Engine, fraud teams can enrich their risk models with enough new information to tailor the customer journey based on individual user risk. Understanding users’ exposure on the criminal underground can not only help enterprises take action to protect vulnerable accounts, but also avoid unnecessary friction for customers who are at exceptionally low risk.
Exposure type, severity, and timing can all influence the user’s risk. For example, if a user’s password has appeared in a combolist, it means their credentials are circulating widely in a format that’s easy for unsophisticated criminals to use in automated attacks. Their account is likely to be hit with credential stuffing attacks. In contrast, a user whose credentials have recently appeared in a fresh third-party breach is at higher risk of targeted account takeover attacks, which can include creative, manual efforts by an attacker. (According to SpyCloud customers, targeted attacks represent just 10 percent of account takeover attempts and account for 80 percent of losses.)
In either case, the user’s own password history is a critical factor. If the user has a high rate of password reuse across their other exposed logins (including passwords associated with their other email addresses), there’s a good chance those attacks will be successful at some point. It may be valuable to take an additional step to verify that the user is legitimate and not a threat actor, such as triggering multi-factor authentication or making them re-enter their stored credit card number. On the other hand, strong password hygiene across other accounts means that criminals most likely don’t have the tools to steal this user’s account. In this case, you can let the user proceed with their account update without disrupting the customer journey.
“I would include Identity Risk Engine anywhere immediately after inputting an email address. If we executed SpyCloud prior to some of the other checks that didn’t catch this activity, you become a cost-saver because those other steps are usually more expensive.”– Financial Services Institution
How It Works
SpyCloud Identity Risk Engine analyzes billions of data points and distills what’s important into summarized statistical elements you can use to drive action for your application. It can serve as a complement to your existing solutions, with the flexibility to be layered into a customer journey at high risk points of your choice (account creation, transaction, etc.).
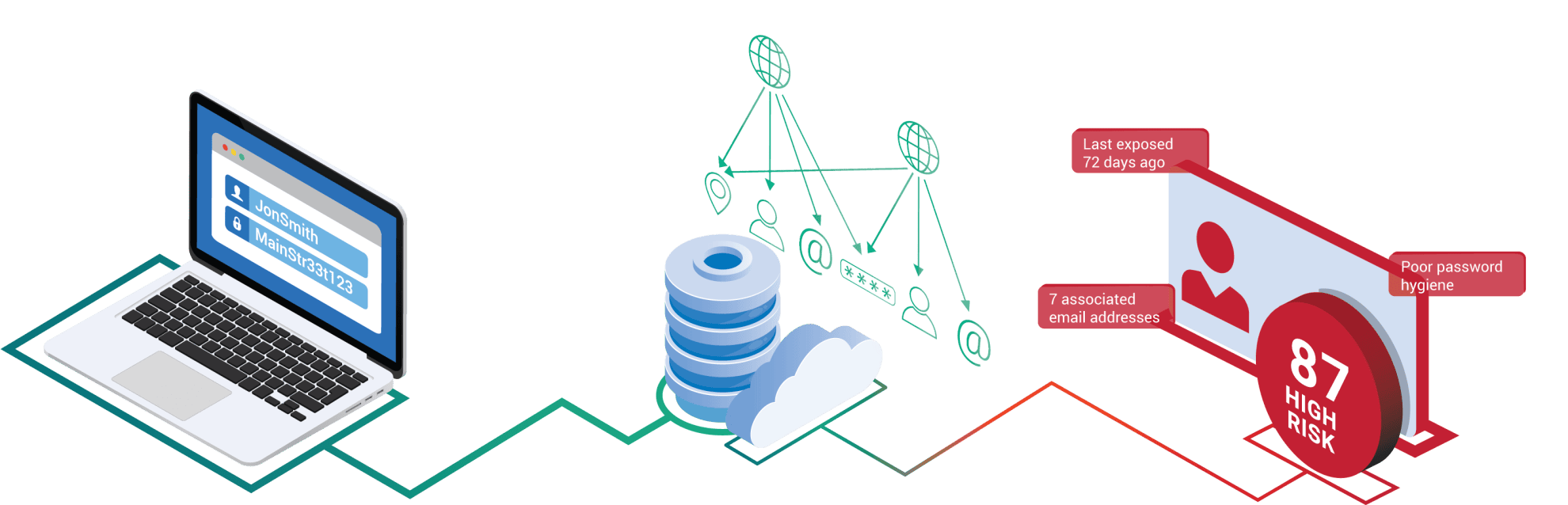
By querying the Identity Risk Engine API with as little as an email address or phone number, you’ll have access to a risk score and 20 reason codes – analytical elements that provide context for the risk score – both of which can help your organization make better fraud decisions and protect your bottom line from fraud.
To learn more about how SpyCloud Identity Risk Engine can help limit fraud and customer friction, schedule a demo today.