The security community is already painfully aware of the threat of business email compromise (BEC), which has been used to defraud business and organizations of over $3 billion.
How BEC happens
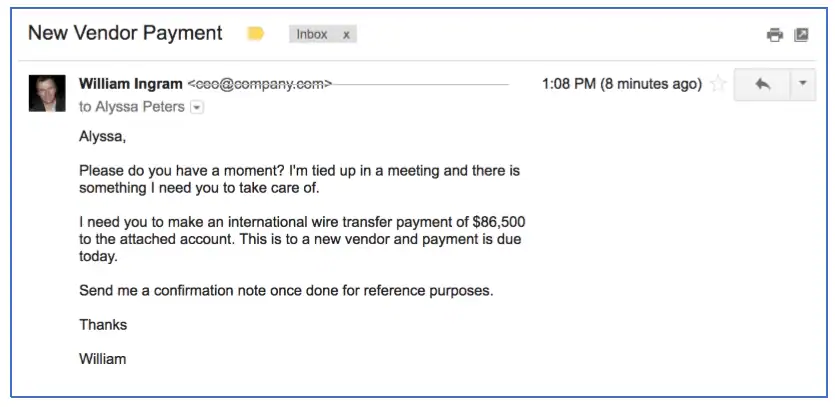
These schemes start off simply enough. Threat actors craft convincing-looking phishing e-mails using publicly-available information about their targets. And attackers don’t just try to fool their targets with this information alone. More sophisticated attackers can spoof a targeted organization’s email domain. This can trick victims into thinking the phish is a legitimate email from an executive or one of their assistants.
Once the e-mail is convincing enough, the attacker needs only to stipulate his or her instructions for account takeover so that they can cash out.
French industrial equipment manufacturer Etna Industrie fell victim to a BEC scheme in 2016. The company’s CEO, Carole Gratzmuller, returned to work to find that her accountant had wired $542,000 to foreign banks–at the direction of an email from a criminal pretending to be her.
How cybercriminals use stolen data from BEC
Sometimes attackers use the information obtained from open source intelligence gathering and social engineering to craft a convincing phish targeted to an executive. Stolen credentials are particularly valuable here, especially if they can be used to take over the e-mail account of an executive assistant and use it to send the email. Attackers can instruct the recipient of the e-mail to siphon funds into threat-actor controlled mule accounts. Or, they can place a link in the e-mail which leads to an attacker-controlled phishing page. By entering their credentials, attackers obtain an extremely high-value set of credentials, especially if the targeted executive tends to reuse passwords between accounts. Attackers may also manipulate lower-ranking employees into initiating a bank transfer on behalf of an executive (“CEO fraud”) or to make certain adjustments from within an organization to make fraudulent wire transfers less detectable.
Such was the case with the Olympic Vision BEC campaign. The campaign, detected by security researchers from TrendMicro in March 2016, targeted companies in the U.S. and Asia in the real estate, manufacturing and construction sectors. The emails crafted by those behind the campaign contained a keylogger now dubbed “Olympic Vision” which was contained in attachments. Once opened, the attachments installed a backdoor through which the attackers were able to log keystrokes and take screenshots for the purpose of stealing personal information and performing network reconnaissance.
What you can do about BEC
Defending against schemes that use sophisticated social engineering methods are easier said than done. Experts agree that humans could very well be the weakest link in any organization’s security posture.
According to the FBI, BEC has seen a 1,300% increase in exposed losses since January 2015, totaling over $3 billion. Furthermore, undetected attackers may use their tactics to obtain access to an organization, taking note of its billing systems, vendors, and even the communication styles of employees. Once inside, attackers may spend months studying their environment before launching an attack. Olympic Vision, for example, gathers its target’s computer name, saved browser credentials, FTP clients, IM clients, email clients, keystrokes, network information, screenshots, clipboard information, and text. This is extremely valuable information, especially for coders who are able to tweak existing exploits which are already designed to leverage those vulnerabilities.
Luckily, more advanced BEC and phishing campaigns with technical components can be defended against through keen awareness of the malware they leverage. Malware like the type used in Olympic Vision can gather information that makes this type of compromise quieter. E-mails containing billing information can be valuable in making sure staff aren’t alerted when a fraudulent transaction is initiated. Organizations can be proactive in patching their network defenses for IoC’s associated with malware used in BEC campaigns, such as Olympic Vision and HawkEye.
But what happens when criminals already have stolen credentials?
When passwords are reused between employee and personal accounts, credentials that have already been breached through credential stuffing techniques are fair game for use in BEC campaigns.
Criminals able to match personal accounts to corporate accounts using an employee’s personal information are more likely to breach the corporate account for the purpose of crafting a fraudulent e-mail. If such an email address is linked to someone who regularly corresponds with executives, such as an executive assistant, the phish becomes that much more convincing.
Unfortunately, the largest vulnerability for any organization is also the hardest to patch. Patching the human factor can only be done through ambitious and effective education of each and every employee who needs need technology to do their job. Organizations can also update acceptable use policies to implement mandate security best practices for all employees.
Use SpyCloud as your early warning system to prevent ATO
Beyond education and patching, large organizations and SMBs alike can benefit from SpyCloud’s early warning solutions. Publicly available credentials make your organization even more vulnerable to actors performing reconnaissance before sending a phishing e-mail. Limiting your exposure can be a valuable countermeasure against attackers who are looking for something to pivot off of during the reconnaissance phase.
In order to prevent account takeover, you need to think like an attacker. And until you know your exposure, you don’t have the entire picture – whether your adversary is a member of a cracking community or an organized crime ring.
Check your exposure using our free tool and find out what criminals know about your business.
