
AI INSIGHTS
AI-Powered Identity Threat Protection
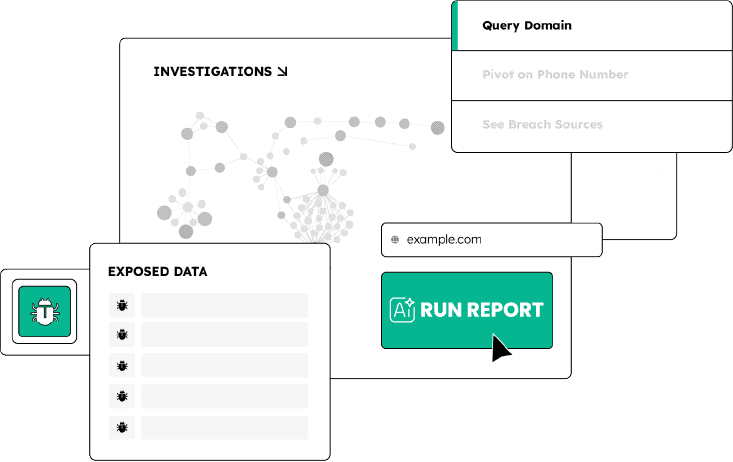

What makes SpyCloud AI fundamentally different
Automated protection that’s only possible after a decade of infiltrating the criminal underground..
SpyCloud AI is powered by hundreds of billions of real identity artifacts recaptured from breaches, malware logs, phishing campaigns, and closed criminal sources from 10+ years – the exact artifacts attackers use in targeted attacks.
No equivalent data = no equivalent AI.
SpyCloud AI encodes the intuition and methodologies of veteran cybercrime investigators, mirroring how expert analysts correlate fragmented identity data across time and identify meaningful patterns.
The result: accurate, contextualized, finished intelligence in seconds.
SpyCloud’s platform is laser-focused on real identity risk. We understand, surface, and act on real-time exposures, credential reuse, and the personal-corporate identity overlap that other solutions aren’t built to detect.
It’s specialization that changes the outcome.
SpyCloud’s AI is designed to do something about the imminent identity threats to your workforce and customers via your existing IdP, SIEM/SOAR, and EDR.
Intelligence without action is trivial. SpyCloud delivers defense.
SpyCloud is a cheat code – from one data point to the answer.
HOW IT WORKS
How SpyCloud’s AI manifests within our platform
Attacks don’t start in your environment – they start with exposed identity data circulating in the underground. SpyCloud’s AI is built to monitor that reality continuously, then correlate fragmented identity signals across time and context, and automatically trigger protection before identities are abused.
This isn’t alerting; it’s a closed-loop system that turns raw criminal data into preventive action at machine speed.
AI-POWERED INGESTION
We continuously ingest actionable identity artifacts from the criminal underground, malware logs, phishing campaigns, and breach sources – including sources only SpyCloud can access.
AUTONOMOUS IDENTITY CORRELATION
FINISHED INTELLIGENCE
We turn a single selector into accurate, transparent, and verifiable analysis that augments analyst workflows and eliminates time-consuming manual work.
AUTOMATED RESPONSE
We trigger protective workflows for high-risk identities across your existing security and identity tools.
Next steps
Your most targeted people are already exposed. Find out who – and fix it with SpyCloud. Get a demo today.