Attackers will use any exposed user identity they can get their hands on to log into your systems, whether it belongs to your employee or the workforce of a third-party vendor you onboarded years ago.
We all know this is happening. As unfortunate as it is, your vendors’ exposed employees are now your issue to deal with.
Their phished credentials, malware infections on their devices, bad password hygiene – all of it can be repurposed by bad actors to gain access into your organization’s environment.
Static, posture-based vendor risk scores break down very quickly in the fast-moving realm of modern supply chain threats, which is why teams need better visibility, earlier.
And it can feel like an unfair game for defenders, which is why we built something to level it.
SpyCloud has revolutionized our approach to reducing third party risk with suppliers and distributors. The product’s insights have driven our partners to make big improvements to their cybersecurity practices, which has gone a long way to reduce our exposure to domain risks while also enhancing our overall security posture.
Why static vendor risk scores aren’t enough when it comes to modern supply chain risk management
This isn’t about replacing your vendor risk management program. It’s about augmenting it with timelier, necessary data.
Vendor assessments and risk scores were built for an era where the biggest threat was a misconfiguration or an unpatched public asset. But attackers have evolved. They’re targeting identities, not servers, and they’re stealing them through malware infections, phishing campaigns, breaches, and combolists at staggering scale and speed.
Most third-party risk management tools on the market today can’t tell you about the identity data attackers already have in their hands. Instead they generally rely on:
- Reviews that are outdated before they’re submitted
- Opaque security scores with unclear methodology
- External infrastructure scans that miss identity exposures
- Static breach data that can’t show active risk
Attackers are busy assembling stolen credentials, tokens, and access paths around the clock – and they’ll use yours or your vendors’, whichever gets them in first.
SpyCloud gives you the lens you’ve been missing: identity-centric, continuously updated exposure intelligence that reflects what criminals could use against you right here and now.
Most vendor risk management tools rely on static assessments that fail to detect active identity exposures. These tools can’t surface compromised credentials, infostealer malware infections, or credential reuse across vendor environments, leaving organizations vulnerable to supply chain attacks.
Introducing SpyCloud Supply Chain Threat Protection for your third-party ecosystem
Your attack surface doesn’t end with your employees. However, until now, your visibility probably did.
SpyCloud Supply Chain Threat Protection gives you something your existing vendor risk management, threat intel, and vendor scorecard tools can’t: continuous, evidence-based visibility into the identity exposures affecting third-party partners and vendors in your ecosystem.
No black-box scores or “just trust us.” No having to wait for an annual review cycle for peace of mind.
It’s as simple as it sounds – add your vendors, and any active exposures surface in the SpyCloud console instantly.
The second you add a vendor, SpyCloud retrieves both current and historical exposures tied to their domains – malware-infected employees, phished credentials, exposed plaintext passwords, reused credentials circulating in combolists, and more.
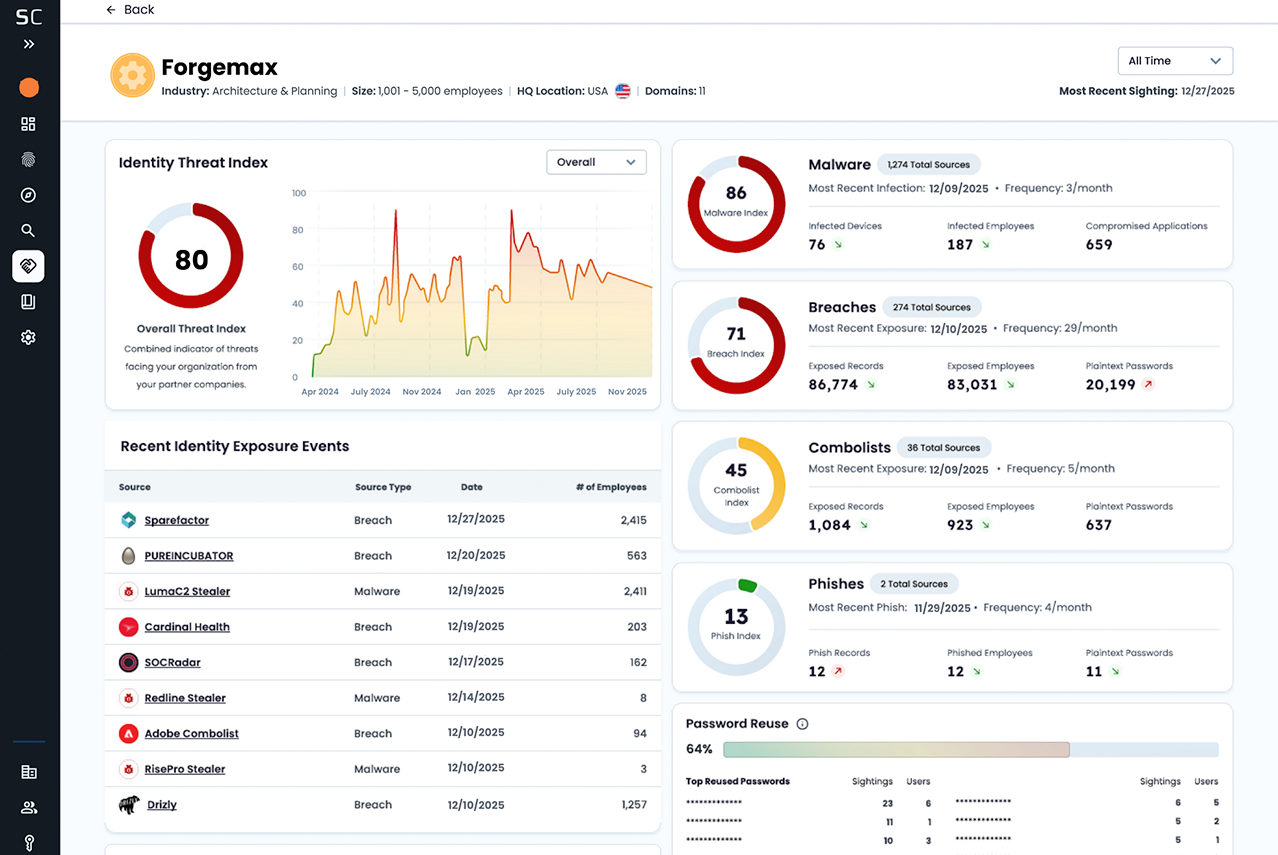
The product leverages the world’s largest repository of recaptured identity data – the same SpyCloud data our customers already rely on to protect employees, contractors, and high-value targets inside organizations – and extends your visibility outward, across your entire vendor ecosystem.
You get:
- Continuous monitoring across thousands of vendors
- At-a-glance Identity Threat Index trend analysis
- The top applications exposed by your suppliers
- Patterns into specific data sources affecting vendor risk
SpyCloud Supply Chain Threat Protection takes the same rigor you apply to your workforce and applies it to your vendors. Because if a vendor’s employee with an active infostealer infection logs into a shared portal, that becomes your incident. And if their reused credentials unlock one of your SaaS apps, attackers get your data.
See every exposed app & potential entry point
Even when suppliers run EDR and antivirus solutions on their devices, infostealer malware still sneaks through two-thirds of the time. When a supplier’s device gets infected, criminals get access to rich authentication data including saved credentials, autofill data, session cookies, and app tokens for every application that employee accessed.
SpyCloud surfaces exactly which applications were exposed on infected supplier devices – both internal apps you host and extend privileged access to, and the external SaaS tools that keep your business running. This means you can see if criminals have access to:
- SSO platforms that could unlock multiple systems at once
- Shared collaboration tools where your teams exchange sensitive data
- VPN clients that bypass security controls
This transparency lets you know exactly which entry points exist so you can take targeted action to close them before attackers exploit them.
SpyCloud’s Supply Chain Identity Threat Index, decoded
In our new Supply Chain Threat Protection product, every vendor is modeled against SpyCloud’s Identity Threat Index, which takes into account the volume, source, and severity of identity exposures across your vendors and weighs data across four threat vectors:
Phish Index
Credentials stolen through successful phishing attacks
Malware Index
Apps, cookies, and accounts exposed via infostealer malware
Breach Index
Plaintext passwords appearing in third-party datasets
Combolist Index
Aggregated reused credentials that amplify downstream risk
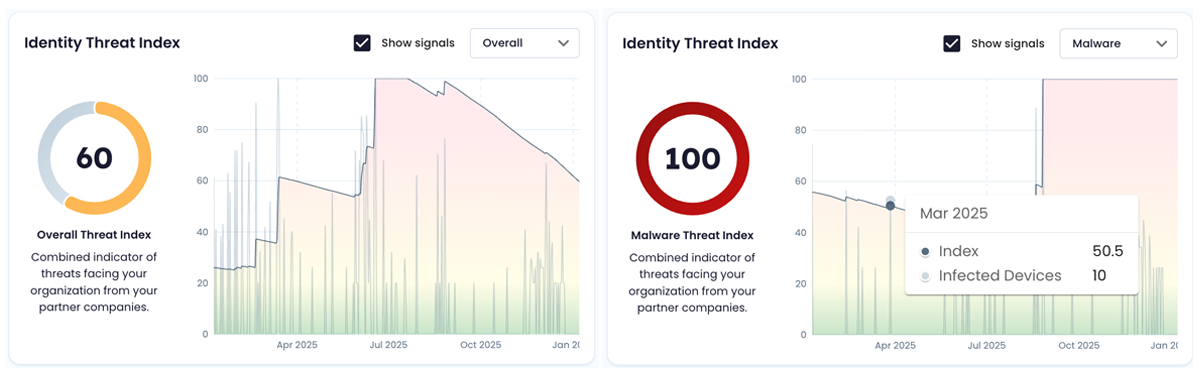
If a vendor suddenly shows a spike in malware infections, you’ll see it. If their exposure decreases as their hygiene improves, you’ll see that too. Unlike other vendor risk ratings, the threat index isn’t a black box. It’s based on actual evidence of compromise, refreshed continuously, and configurable by timeframe so you can spot upward or downward trends.
How SpyCloud's supply chain exposure data supports decision making
SpyCloud Supply Chain Threat Protection gives you the clarity to act on your vendors’ exposures rather than simply accept risk. You can use it to help your SOC and TPRM teams actually prevent identity threats. Here are a few examples of how that could look for your organization:
If SpyCloud shows a vendor has numerous malware-infected employees and exposed application access, you can ask:
- Could exposed authentication data or session cookies be used to access our systems?
- Do we need to adjust privilege or limit data integrations?
- Has this vendor fallen short of their managed device policy?
If SpyCloud reveals that a vendor’s employees are repeatedly targeted by phishing campaigns, ask:
- Could phishing open up session hijacking or lateral movement into the applications shared with our supplier?
- Should we reassess how our own employees interact with this vendor – do we need to reinforce training or adjust privileges based on their elevated risk?
- Given the link between phishing and ransomware, should we need to escalate this vendor’s risk tier?
If SpyCloud illuminates repeated credential reuse and exposed plaintext passwords from breaches and combolists for a given vendor:
- Is this a systemic issue with how their employees manage passwords?
- Do our own employees appear in these exposures, and do we need to reset credentials tied to sensitive SaaS applications?
- Is this pattern a signal that stronger password policies or user education are needed?
These insights replace “concerns” with verified compromise indicators at your suppliers so you can take immediate action.
Our customers have often reported that when they’re evaluating doing business with a new vendor, their legal and compliance team need evidence-based decision making resources and tools. That’s where SpyCloud stands out – we give you that evidence.
Building better protection beyond your perimeter
If you’re feeling increased pressure around vendor-related identity threats, you’re not alone. Over 75% of organizations we surveyed are highly concerned about compromised supply chain partners triggering damaging attacks. And let’s be real, your attack surface now includes every identity with a foothold in your systems – whether you pay their salary directly or not.
SpyCloud Supply Chain Threat Protection offers:
- Smarter procurement decisions
- Security-informed vendor onboarding
- Continuous monitoring instead of annual surprises
- Early warning of degrading vendor security hygiene
- Integrated response for SOC, TPRM, procurement, and compliance teams
You’ve invested heavily in protecting your company’s user identities and preserving authorized access within and across your corporate network. With SpyCloud, you can now extend that same protection for your workforce to the identities in your supply chain.
Ready to see your vendors the way attackers do?
Your supply chain is already part of your security perimeter – it’s time your visibility caught up. See what’s possible with SpyCloud.
Key Takeaway:
Today’s attackers exploit exposed vendor credentials, malware-infected supplier devices, and reused passwords to render traditional vendor risk assessments obsolete. To prevent supply chain attacks, security teams need continuous, identity-based visibility into third-party risk, not annual scorecards.
FAQs
Most vendor risk management tools rely on static assessments that fail to detect active identity exposures. These tools cannot surface compromised credentials, infostealer malware infections, or credential reuse across vendor environments, leaving organizations vulnerable to supply chain attacks.
Unlike BitSight and SecurityScorecard, which score vendor security posture based on external scans, configurations, and questionnaires, SpyCloud reveals the actual compromise reality: which vendor identities are compromised, which credentials and identity data have been stolen, and when.
- Continuously monitor for vendor identity exposures
- Track both historical and current exposures – attackers reuse old credentials made available to them on the darknet
- Detect compromised vendor credentials before access is abused
- Identify malware-infected supplier endpoints to see which applications have exposed credentials
- Identify vendor identities exposed in phishing campaigns, breaches, or combolists
- Reset credentials across shared SaaS applications you control
- Review credential reuse rates across vendor employees to identify poor security hygiene
- Respond to changes in vendor risk levels using evidence of credential compromise, not assumptions