New Year, new threats, as they say. Right?
We’re back with another cybercrime update – and this month we’re covering:
- The unfortunate connection between OpenClaw ‘skills’ and Atomic macOS Stealer infections
- More drama from BreachForums admins in the latest “Forum Wars” (or should we say Clone Wars?) update
- The alleged takedown of RAMP, a Russian-speaking cybercrime forum popular with ransomware groups and initial access brokers
- Other ransomware developments, including Black Basta member arrests and a new flurry of activity from Cl0p
Let’s dig in.
OpenClaw can download Atomic macOS malware for you
OpenClaw (formerly called Clawdbot and Moltbot) is an open-sourced AI-based personal assistant that has been generating a lot of buzz since it was first released in November. It is designed to run locally on a user’s machine and access an online LLM for reasoning. It also requires significant permissions and a variety of user credentials in order to function as intended, raising significant red flags from both security researchers and AI experts.
OpenClaw has gone somewhat viral and rapidly amassed a large user base that are keen to share tools – one of the ways to do this is by sharing “skills” on ClawHub. In the context of OpenClaw, skills are basically markdown files that contain detailed instructions for an agent on how to execute a task, and ClawHub is the official registry for users to publish OpenClaw skills.
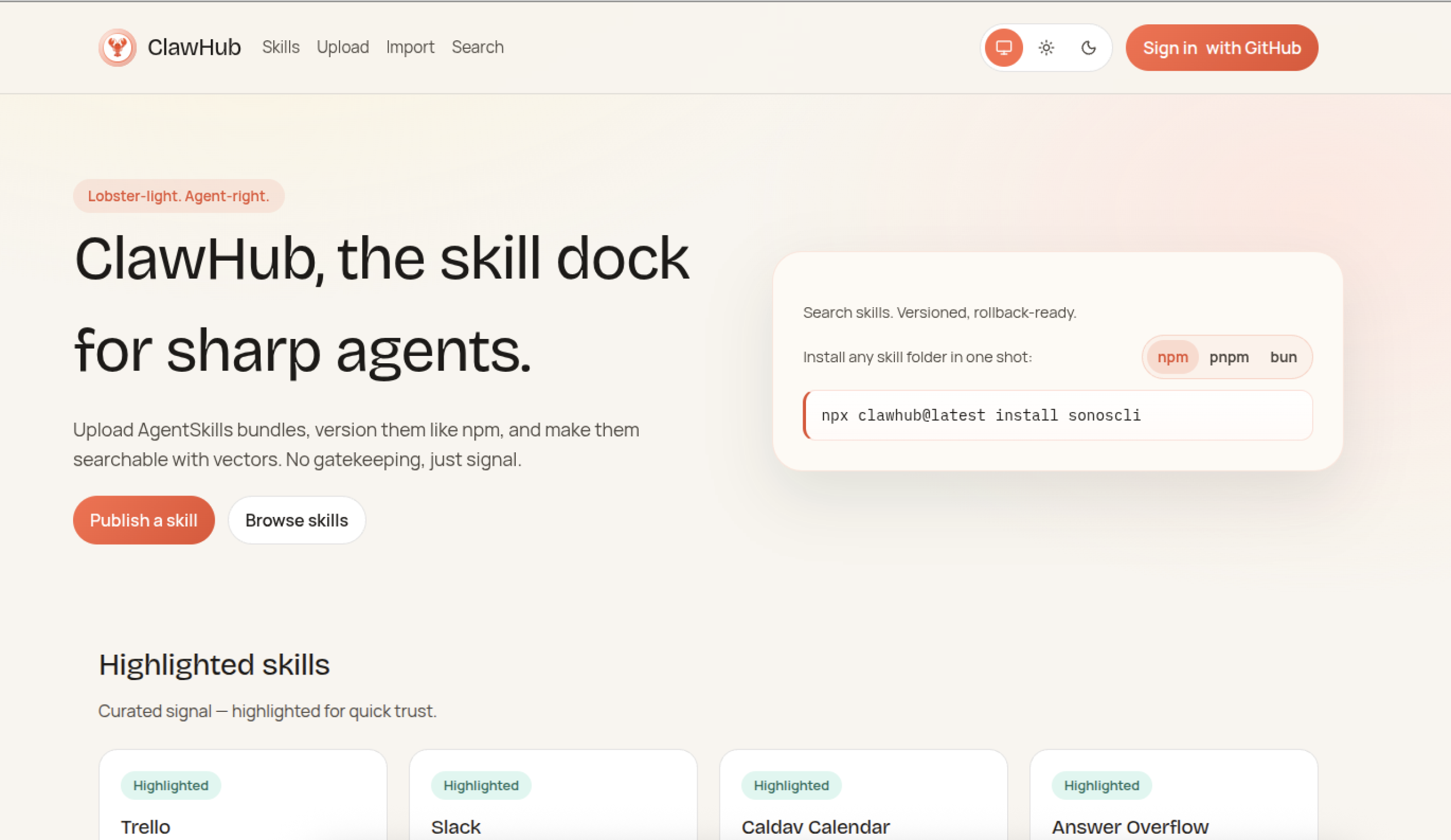
Earlier this week, a few different security researchers appeared to simultaneously notice a wide variety of seemingly innocuous “skills” on ClawHub which actually contained instructions prompting agents to download Atomic macOS (AMOS) infostealer malware.
A researcher at 1Password noticed that the top downloaded skill on ClawHub, ostensibly related to a Twitter-related task, actually led to an install of Atomic Stealer. Researchers at Koi did a more wide-ranging analysis connecting 335 different seemingly harmless skills on ClawHub to downloads for AMOS malware and at least six others to different malicious results. (A preliminary analysis by our team shows an uptick of AMOS infections starting on January 22, 2026.) Finally, researchers at OpenSourceMalware identified malicious OpenClaw skills distributed across ClawHub as well as Github with the concealed purpose of distributing both macOS and Windows infostealer malware.
Some of these researchers correctly pointed out that this attack chain is functionally similar to past campaigns that trojanized extension or package marketplaces (like PyPi or npm). However, the fact that these tactics are popping up in marketplaces intended to be used for tasking autonomous agents feels like an escalation – the humans tasking these agents are likely optimizing for speed and ease-of-use and are almost certainly being less careful and taking less notice of small details. Additionally, it stands to reason that agents in some cases will probably be enabled to download their own new skills from skill marketplaces, completely removing any possibility of human review if these skills continue to frequently be trojanized.
The Forum Wars: The Clone Wars
Breachforums – the most popular English-language data breach and hacking forum – went down in April 2025. Since then, we have been tracking the chaotic aftermath, as a community of criminal hackers remains without a centralized forum to gather while a few opportunistic threat actors have attempted to fill the power vacuum.
Let’s dive into some of the latest developments in the “Forum Wars” saga:
- The two main Breachforums “clones” are fighting with each other. Hasan’s version of BreachForums, which claims to be aligned with ShinyHunters, is in an escalating battle with the other BreachForums, which is managed by some of the admins and moderators from the “original” pre-2025 BreachForums like Loki, Tanaka, and 888.

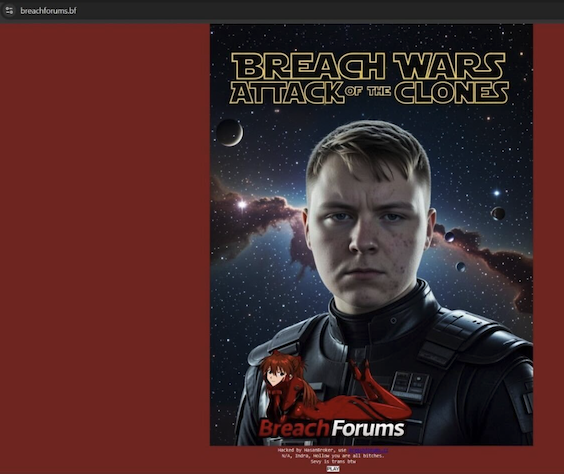
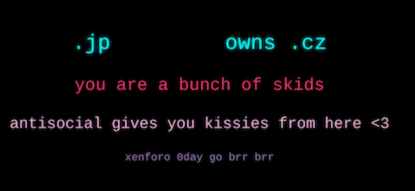
In the same week, both of these websites defaced each other – first Hasan defaced the revived “original” BreachForums site posting an image of his own face with the text “Breach Wars: Attack of the Clones” in the Star Wars font and a link to his own site. Then, the other BreachForums struck back, defacing Hasan’s site (allegedly through a cross-site scripting vulnerability in the XenForo forum management software) and leaving a message on their homepage that called them “a bunch of skids.”
- BreachForums isn’t the only former criminal forum with multiple warring copycat clones – there are also two revived versions of RaidForums currently active. The “original” revived RaidForums domain now appears to be up for sale, while a new site raidforums[.]wtf appears to be currently active, displaying the same art as the RaidForums that was disrupted by law enforcement back in 2022.
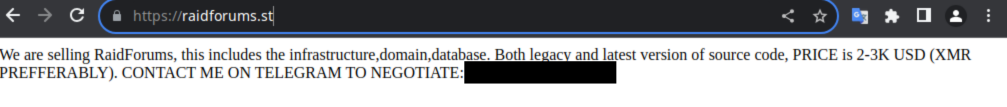
The “original” restored RaidForums is now for sale.
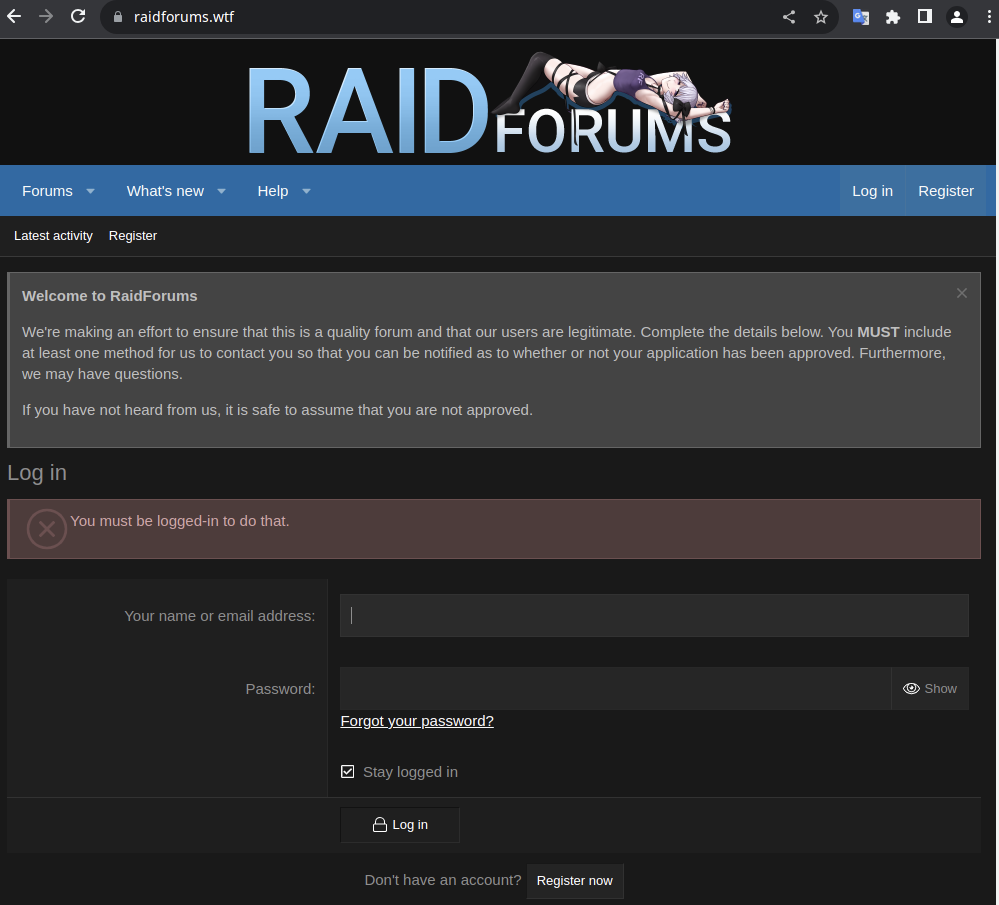
Another RaidForums clone is currently up and running.
- Many of the other popular data breach forums also seem to be going through a rough patch. Knox’s clearnet DarkForums domain was suspended, so they had to move it to a new domain. Chucky’s Leakbase Forum has been down for a few days (as of the time of this writing) and he announced that he’s looking for a new hosting provider.
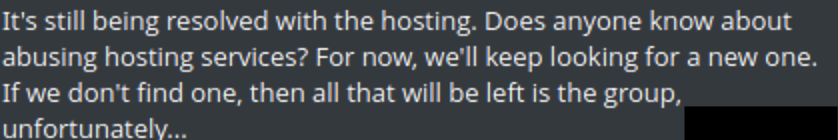
Leakbase’s most current announcement regarding their forum.
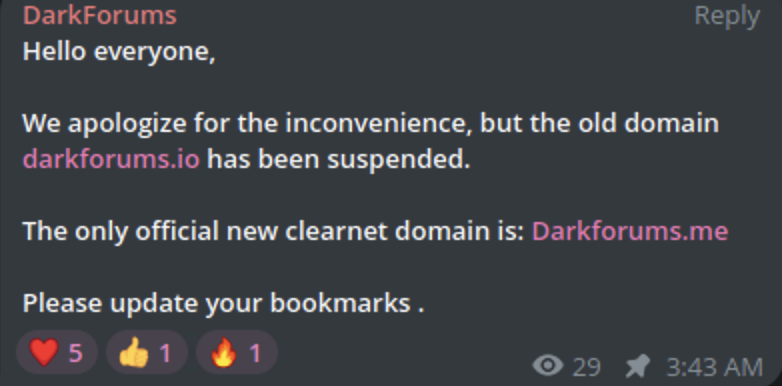
DarkForums’ announcement regarding their new domain after members noticed that their domain was unavailable.
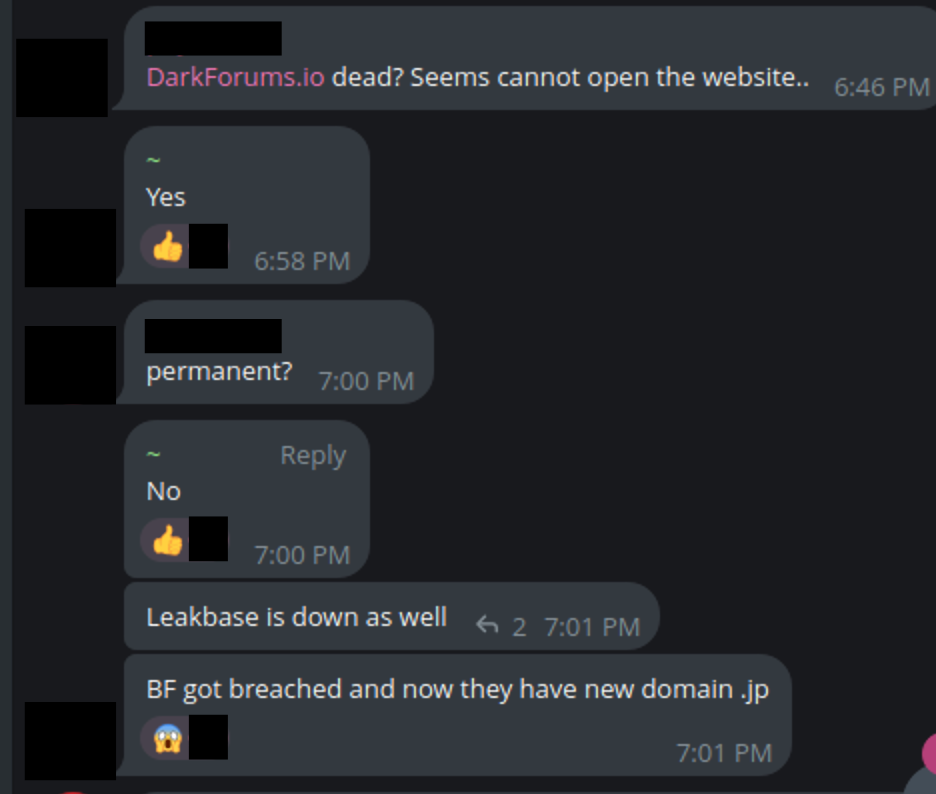
Members of the cybercrime community discussing all of the various forum outages.
RAMPwn
On January 28th, the threat actor going by the moniker stallman reported on two separate Russian-speaking forums that his passion project, RAMP (ramp4u[.]io) – a Russian-speaking cybercrime forum popular with ransomware groups and initial access brokers – had been seized by the FBI. Visiting the RAMP site itself led to a splash screen claiming such, alongside DNS redirection of the domains to the FBI’s seized name servers (fbi.seized.gov).
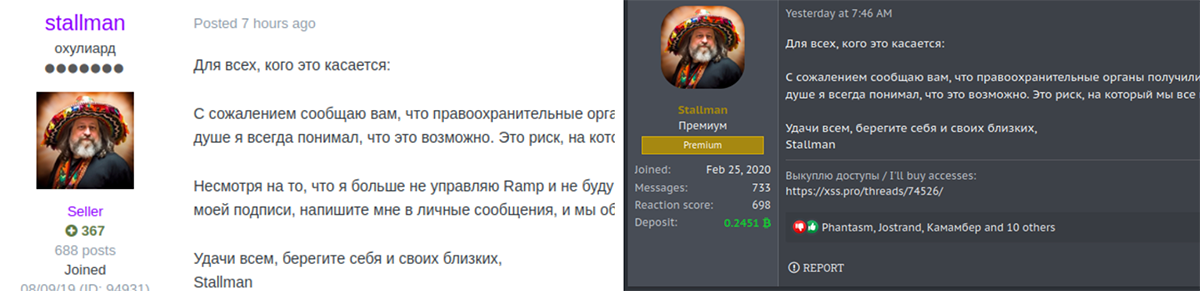
Stallman’s posts announcing a RAMP disruption.
The posts were met with both panic and skepticism, with one member pointing out that stallman had previously mentioned he has full physical control of the server. Cybersecurity analysts and news outlets have noted that while the splash page had the FBI’s logo, the U.S. Department of Justice has not yet made any public announcements about any enforcement actions targeting RAMP, causing some skepticism as to the authenticity of the takedown.
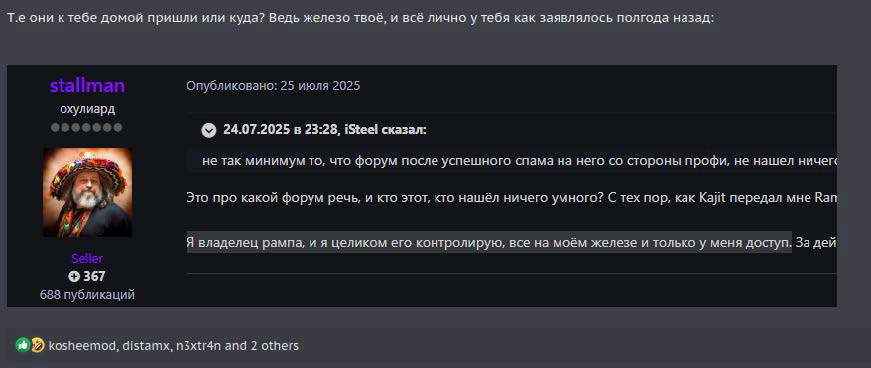
A post skeptical of stallman’s claims. It includes a screenshot of an older stallman post in which he stated he had full physical control over his server hardware.
Shortly after these takedown announcement posts were made, the administrator of Tor Zireael, a Telegram channel focused on anonymity, posted screenshots of data allegedly leaked from RAMP, again causing paranoia and moral panic. This Tor Zireael Telegram channel is linked to a YouTube channel of the same name which purports to be operated by a former Ukrainian cyber officer who now educates people on anonymity practices. It’s unclear whether the RAMP databases posted are real or in any way linked to the alleged law enforcement takedown action.
Messages from the Tor Zireael Telegram channel
Tor Zireael YouTube profile
Other forums also took notice of the RAMP takedown, with Hasan even going so far as to invite former RAMP users to his forum with open arms.
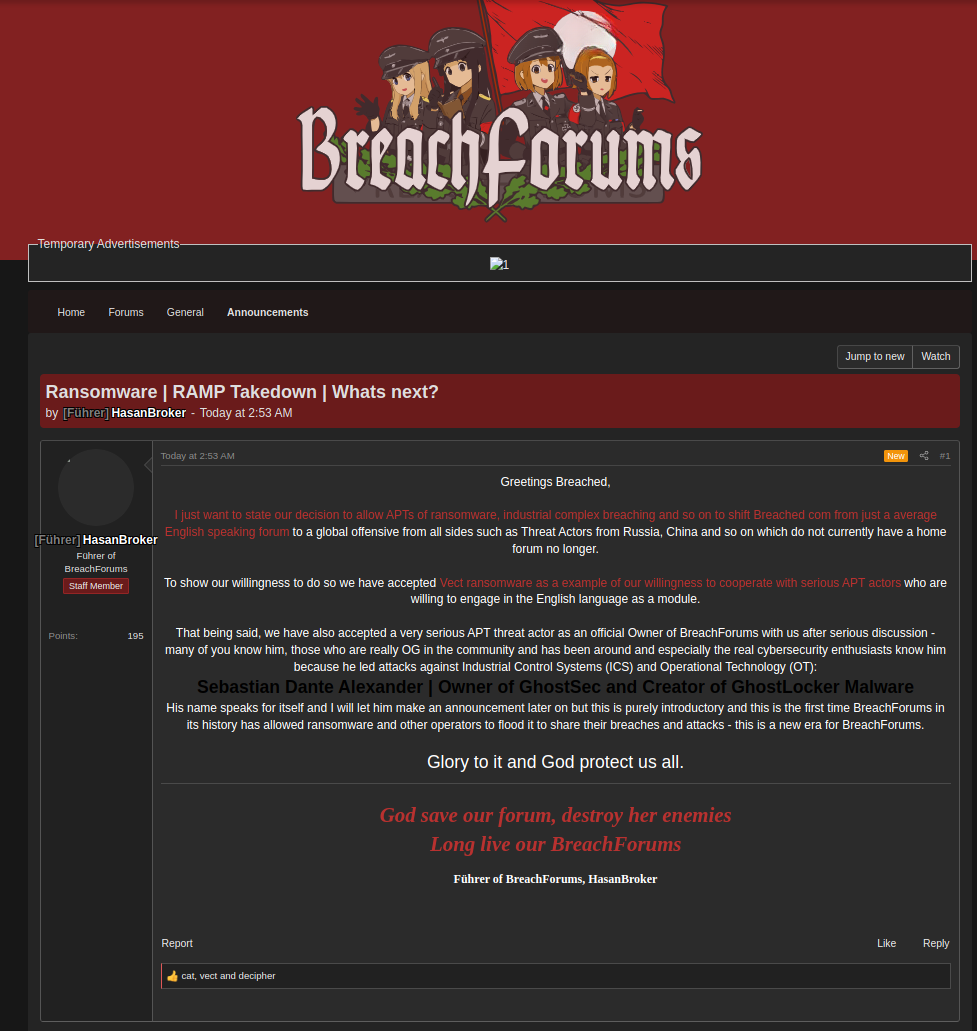
Hasan’s post about the RAMP takedown which welcomes ransomware actors to post on his version of BreachForums.
More Cl0p activity (likely from CentreStack victims)
Cl0p is a ransomware group known for their very effective pattern of mass exploitation of a zero-day vulnerability to compromise a specific internet-facing appliance en masse and then follow up with data theft extortion over the course of the next few months. In late January, they began posting a large volume of new claimed victims to their website, signaling the imminent release of stolen data from their newest batch of victims. Based on timing, many researchers suspect this newest round of victims is likely a result of their campaign against Gladinet CentreStack servers in mid-December.
Arrests of former Black Basta ransomware operators
Ukrainian and German officials raided the homes of two former members of the Black Basta Ransomware group and publicly identified a third – Oleg Evgenievich Nefedov – as tramp, the leader of the group. Black Basta was a prolific Ransomware gang made up of former members of the Conti Ransomware group. After Conti’s splintered in 2022, Black Basta was one of a few Russian Ransomware gangs made up of former Conti members. In early 2025, Black Basta appeared to cease activities after some internal strife and a large dataset of their internal chat logs leaked, a series of events that echoed the end of Conti just 3 years prior. It’s suspected that Black Basta members pivoted to other ransomware (such as CACTUS) following the dissolution of the Black Basta brand.

Wanted notice for Oleg Evgenievich NEFEDOV on EUROPOL’s ‘Most Wanted’ website.
New research and insights from SpyCloud
Chinese-speaking cybercriminals have developed scams, fraud, malware, and money laundering schemes tied to the Lunar New Year ‘red envelope’ tradition.