February 2021 Update: What is Combolist 3.2b? A few major combolists have been re-released as the COMB (Combination of Many Breaches) combolist. This appears to be a sorted and deduped version of previously leaked combolists, not new information. That said, this is a good reminder that old data can still be useful to criminals; threat actors are no doubt running credential stuffing attacks with the COMB list, so any accounts using the same logins and passwords could still be in jeopardy.
There’s been a lot of buzz over a recent so-called “superbreach” collectively referred to as Collection #1. Containing over 772,904,991 unique email addresses and over 21 million passwords, this incident already stands out in terms of its sheer magnitude of exposure. It certainly doesn’t help that the data was reportedly posted to a publicly-accessible online forum. A sampling of a few news articles about the combolist breach gives you an idea how this event spread like wildfire through both social media and mainstream news outlets:
Was this really a new “Monster” breach?
In short, no. This collection was comprised of “combolists.” In other words, a rehash of old breaches.
What is a combolist?
The proliferation of stolen or leaked databases has given rise to credential stuffing, a fairly simple technique in which criminals load lists of previously breached credentials (from Linkedin, MyFitnessPal, MySpace, etc.), called combolists, into automated brute-forcing tools to test credentials en masse. These tools test stolen passwords against thousands of targeted websites and applications until there is a match.
To understand it better, check out this step-by-step and video demo of a successful credential stuffing attack that we put together: The Anatomy of Credential Stuffing
Combolists are usually not that interesting from a security standpoint because they are full of duplicate records. In many cases, duplicates of duplicates of duplicates. It’s also important to note that these old passwords still matter. SpyCloud analysts published content on this subject in light of the epidemic of password reuse. As increasingly more websites and applications require account creation, people simply can’t recall the many unique passwords they use between accounts. To make things easier, they reuse passwords amongst multiple sites, recycle old passwords and/or make only slight modifications to existing passwords. For criminals, this makes account takeover easier than ever – especially with the help of massive combolists such as the one recently disclosed.
What was actually shared?
The combolists were initially shared via the hosting service MEGA. The “Collection #1” list was actually only part 1 of 7 totaling more than 8B username and password records:
- Collection #1 1,013,050,906
- Collection #2 3,040,689,677
- Collection #3 69,747,990
- Collection #4 1,835,141,695
- Collection #5 540,972,614
- AntiPublic #1 1,737,991,372
- AntiPublic #2 517,524,658
Combined List Totals:
- 19,144,865,944
Total non-unique & non-deduplicated records - 8,755,118,912
Total unique per file, non-deduplicated records - 3,051,257,458
Total unique, deduplicated records - 114,993
Files
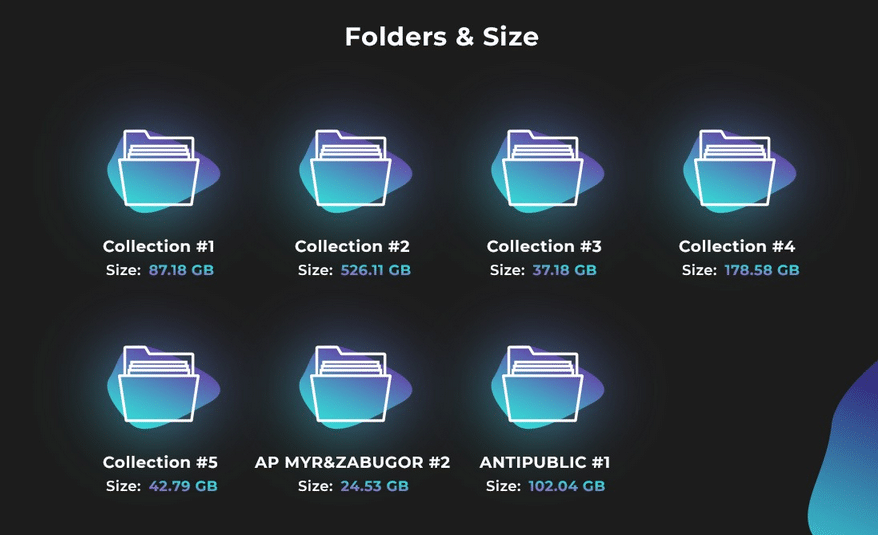
TOTALING 1043.42GB
Collection #1
87.16GB of data, located in 40 folders across 12,368 files totaling 2,692,818,238 credentials, 1,013,050,906 of them unique.
TOP SOURCED BREACHES
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| Combolist of 1.4 Billion Credentials | 54.6% | 557,033,337 |
| Exploit.in combolist | 33.54% | 342,242,366 |
| Anti-Public Combolist | 26.61% | 271,487,883 |
| Jadid List from Pemiblanc.com | 11.02% | 112,428,204 |
| MySpace | 10.99% | 112,129,808 |
| Pemiblanc.com | 8.14% | 83,072,632 |
| Badoo | 5.95% | 60,739,773 |
| Zoosk | 5.00% | 51,001,545 |
| Evony | 2.73% | 27,837,949 |
| 2.48% | 25,311,057 | |
| Gmail Combolist | 1.80% | 18,380,128 |
| Last.fm | 1.46% | 14,892,975 |
| Chinese/Japanese Combolist | 1.36% | 13,922,272 |
| NetEase | 1.33% | 13,568,773 |
| Fling | 1.31% | 13,350,260 |
| 1.20% | 12,196,329 | |
| Mate1 | 1.19% | 12,128,369 |
| Russian Bitcoin Security Forum Account Dump | 0.93% | 9,495,814 |
| Neopets | 0.88% | 8,958,608 |
| LifeBoat Network | 0.83% | 8,505,854 |
| LSGB.net | 0.83% | 8,417,669 |
| 000webhost | 0.82% | 8,338,620 |
| VK | 0.82% | 8,316,066 |
| Gamigo AG | 0.79% | 8,090,839 |
| Online Shopping Combolist | 0.70% | 7,136,783 |
| Gaming Account Combolist | 0.70% | 7,104,830 |
| Onliner Spambot Credentials | 0.70% | 7,101,327 |
| BTC-E | 0.65% | 6,638,226 |
| Gaming Combolist | 0.65% | 6,605,114 |
| Netlog | 0.63% | 6,5,165 |
| Youku | 0.62% | 6,33,283 |
| Aipai | 0.49% | 4,953,090 |
Top affected email domains
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| yahoo.com | 20.58% | 209,948,106 |
| hotmail.com | 13.23% | 135,005,359 |
| mail.ru | 11.470% | 117,027,547 |
| gmail.com | 10.31% | 105,207,188 |
| aol.com | 2.34% | 23,898,357 |
| bk.ru | 1.76% | 17,967,891 |
| yahoo.co.uk | 1.55% | 15,843,691 |
| hotmail.co.uk | 1.51% | 15,416,948 |
| hotmail.fr | 1.31% | 13,368,990 |
| list.ru | 1.21% | 12,387,052 |
| live.com | 1.11% | 11,322,952 |
| qq.com | 1.04% | 10,557,793 |
Collection #2
528.1GB of data, located in 127 folders across 24,921 files totalling 7,442,265,404 credentials, 3,040,689,677 of them unique.
TOP SOURCED BREACHES
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| Combolist of 1.4 Billion Credentials | 39.00% | 1,198,031,731 |
| Collection #1 Combolist | 32.12% | 986,733,705 |
| Exploit.in combolist | 18.20% | 558,943,984 |
| Anti-Public Combolist | 16.43% | 504,813,202 |
| Jadid List from Pemiblanc.com | 10.81% | 331,973,029 |
| MySpace | 9.16% | 281,312,439 |
| Pemiblanc.com | 3.36% | 103,165,531 |
| Badoo | 3.07% | 94,240,322 |
| Rambler.ru | 2.94% | 90,365,488 |
| VK | 2.62% | 80,376,623 |
| 1.97% | 60,429,960 | |
| Zoosk | 1.67% | 51,375,989 |
| Fling | 1.30% | 39,896,635 |
| Last.fm | 1.06% | 32,478,455 |
| Active Account Cracking List | 1.02% | 32,329,128 |
| NetEase | 0.98% | 29,982,806 |
| Neopets | 0.92% | 28,347,001 |
| Evony | 0.91% | 28,041,079 |
| Mate1 | 0.86% | 26,550,966 |
| 0.81% | 24,990,114 | |
| Tianya | 0.77% | 23,662,666 |
| Gmail Combolist | 0.63% | 19,226,272 |
| Chinese/Japanese Combolist | 0.45% | 13,917,735 |
| Onliner Spambot Credentials | 0.39% | 12,000,260 |
| 000webhost | 0.39% | 11,990,669 |
| Russian Bitcoin Security Forum Account Dump | 0.31% | 9,501,017 |
| Netlog | 0.31% | 9,396,206 |
| Youku | 0.30% | 9,063,630 |
| Online Shopping Combolist | 0.29% | 8,815,288 |
| LifeBoat Network | 0.28% | 8,500,595 |
| LSGB.net | 0.27% | 8,422,575 |
| BTC-E | 0.27% | 8,256,465 |
| Gamigo AG | 0.26% | 8,094,050 |
Top sourced email domains
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| mail.ru | 13.464% | 413,616,269 |
| yahoo.com | 12.63% | 387,858,799 |
| hotmail.com | 9.82% | 301,642,370 |
| gmail.com | 8.41% | 258,332,308 |
| rambler.ru | 6.27% | 192,601,652 |
| yandex.ru | 5.17% | 158,735,410 |
| bk.ru | 2.59% | 79,497,252 |
| aol.com | 2.39% | 73,499,662 |
| list.ru | 2.14% | 65,773,840 |
| inbox.ru | 2.08% | 64,027,090 |
| qip.ru | 1.02% | 31,462,518 |
Collection #3
37.18GB of data, located in 11 folders across 1,284 files totalling 276,931,143 credentials, 69,963,948 of them unique.
TOP SOURCED BREACHES
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| Combolist of 1.4 Billion Credentials | 40.63% | 56,682,114 |
| Collection #1 Combolist | 27.06% | 37,747,154 |
| Exploit.in combolist | 26.37% | 36,790,546 |
| 24.06% | 33,564,270 | |
| Anti-Public Combolist | 14.91% | 20,795,029 |
| Jadid List from Pemiblanc.com | 7.89% | 10,998,869 |
| Russian Bitcoin Security Forum Account Dump | 6.80% | 9,487,226 |
| Gmail Combolist | 4.66% | 6,503,302 |
| Pemiblanc.com | 3.33% | 4,642,283 |
| Active Account Cracking List | 2.01% | 2,801,989 |
| VK | 1.94% | 2,705,590 |
| Origin | 1.84% | 2,568,187 |
| MySpace | 1.75% | 2,447,194 |
| Gaming Account Combolist | 1.33% | 1,860,541 |
| Onliner Spambot Credentials | 1.33% | 1,857,224 |
| Yandex | 0.85% | 1,186,528 |
| 0.83% | 1,156,535 | |
| Last.fm | 0.82% | 1,141,550 |
| Zoosk | 0.74% | 1,033,159 |
| Mate1 | 0.74% | 1,026,261 |
| Nulled.io Combolist | 0.73% | 1,021,460 |
| Gaming Combolist | 0.73% | 1,016,470 |
| Netlog | 0.55% | 772,050 |
| Brazzers | 0.55% | 765,190 |
| Active Combolist | 0.53% | 739,118 |
| Online Shopping Combolist | 0.49% | 684,280 |
| Badoo | 0.47% | 661,366 |
| 700K PayPal Combolist | 0.47% | 653,926 |
| Evony | 0.45% | 620,595 |
| Comcast | 0.42% | 590,235 |
| ClixSense | 0.41% | 575,221 |
Top email domains
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| gmail.com | 9.69% | 13,520,737 |
| yahoo.com | 6.26% | 8,727,610 |
| hotmail.com | 5.98% | 8,335,071 |
| mail.ru | 3.82% | 5,332,807 |
| rambler.ru | 3.06% | 4,263,833 |
| yandex.ru | 1.95% | 2,719,125 |
| aol.com | 1.026% | 1,431,043 |
| outlook.com | 0.86% | 1,202,887 |
| comcast.net | 0.77% | 1,068,243 |
| msn.com | 0.35% | 481,349 |
| yahoo.co.uk | 0.34% | 474,243 |
Collection #4
228.89GB of data, located in 16 folders across 57,255 files totalling 3,425,900,836 credentials, 1,835,141,695 of them unique.
TOP SOURCED BREACHES
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| Combolist of 1.4 Billion Credentials | 45.56% | 836,160,449 |
| Collection #1 Combolist | 43.20% | 792,790,090 |
| Exploit.in combolist | 26.72% | 490,429,612 |
| Anti-Public Combolist | 17.41% | 319,429,445 |
| Jadid List from Pemiblanc.com | 8.84% | 162,152,918 |
| MySpace | 7.44% | 136,532,696 |
| Pemiblanc.com | 4.96% | 91,028,726 |
| Badoo | 3.80% | 69,761,461 |
| VK | 3.45% | 63,351,699 |
| Zoosk | 2.79% | 51,198,843 |
| 2.22% | 40,690,000 | |
| Last.fm | 1.67% | 30,665,474 |
| Evony | 1.53% | 28,025,404 |
| Mate1 | 1.38% | 25,300,197 |
| 1.30% | 23,823,952 | |
| Tianya | 1.27% | 23,306,957 |
| Active Account Cracking List | 1.21% | 22,295,540 |
| NetEase | 1.02% | 18,781,188 |
| Gmail Combolist | 0.76% | 14,017,298 |
| Chinese/Japanese Combolist | 0.76% | 13,912,430 |
| Neopets | 0.72% | 13,277,226 |
| Fling | 0.66% | 12,170,227 |
| Russian Bitcoin Security Forum Account Dump | 0.52% | 9,444,118 |
| 000webhost | 0.46% | 8,908,367 |
| LifeBoat Network | 0.46% | 8,466,485 |
| LSGB.net | 0.46% | 8,394,233 |
| Gamigo AG | 0.44% | 8,093,098 |
| Online Shopping Combolist | 0.44% | 8,086,511 |
| Netlog | 0.43% | 7,929,149 |
| Onliner Spambot Credentials | 0.43% | 7,921,993 |
| Gaming Account Combolist | 0.43% | 7,895,059 |
| BTC-E | 0.40% | 7,377,639 |
| Youku | 0.38% | 7,032,534 |
Top email domains
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| mail.ru | 17.75% | 325,775,839 |
| yahoo.com | 13.40% | 245,808,067 |
| hotmail.com | 11.07% | 203,067,172 |
| gmail.com | 9.63% | 176,701,801 |
| yandex.ru | 2.91% | 53,452,417 |
| bk.ru | 2.90% | 53,264,022 |
| aol.com | 2.49% | 45,656,931 |
| list.ru | 2.41% | 44,233,972 |
| rambler.ru | 2.34% | 42,962,356 |
| inbox.ru | 2.17% | 39,747,932 |
| web.de | 1.03% | 18,982,748 |
| hotmail.fr | 0.88% | 16,181,028 |
Collection #5
40.56GB of data, located in 45 folders across 16,022 files totalling 1,282,149,565 credentials, 546,046,140 of them unique.
TOP SOURCED BREACHES
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| Collection #1 Combolist | 62.29% | 336,950,930 |
| Combolist of 1.4 Billion Credentials | 44.79% | 242,320,804 |
| Exploit.in combolist | 24.14% | 130,607,874 |
| Anti-Public Combolist | 24.09% | 130,300,314 |
| Jadid List from Pemiblanc.com | 11.73% | 63,439,994 |
| MySpace | 8.93% | 48,301,150 |
| Pemiblanc.com | 7.09% | 38,337,691 |
| Badoo | 5.87% | 31,745,354 |
| Evony | 5.13% | 27,743,386 |
| Active Account Cracking List | 2.93% | 15,837,166 |
| 2.43% | 13,167,364 | |
| Chinese/Japanese Combolist | 2.36% | 12,756,046 |
| Zoosk | 2.14% | 11,587,605 |
| Last.fm | 1.88% | 10,153,099 |
| LifeBoat Network | 1.53% | 8,285,221 |
| LSGB.net | 1.52% | 8,233,652 |
| Gamigo AG | 1.50% | 8,090,443 |
| 1.41% | 7,614,039 | |
| Gaming Combolist | 1.212% | 6,577,747 |
| Fling | 1.15% | 6,210,287 |
| NetEase | 1.13% | 6,088,551 |
| Onliner Spambot Credentials | 1.11% | 5,995,176 |
| VK | 1.05% | 5,679,875 |
| BTC-E | 1.05% | 5,675,719 |
| Youku | 1.02% | 5,509,458 |
| Gmail Combolist | 0.91% | 4,916,990 |
| Aipai | 0.89% | 4,825,959 |
| Russian Bitcoin Security Forum Account Dump | 0.85% | 4,574,582 |
| Neopets | 0.80% | 4,329,638 |
| Gaming Account Combolist | 0.77% | 4,185,604 |
| Cupid Media | 0.65% | 3,500,595 |
| Mate1 | 0.64% | 3,463,105 |
Top email domains
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| yahoo.com | 16.23% | 87,774,653 |
| gmail.com | 11.05% | 59,756,314 |
| hotmail.com | 10.321% | 55,835,653 |
| mail.ru | 7.55% | 40,853,067 |
| yandex.ru | 4.24% | 22,936,274 |
| aol.com | 2.79% | 15,112,001 |
| rambler.ru | 2.06% | 11,137,254 |
| hotmail.fr | 1.07% | 5,766,713 |
| qq.com | 1.07% | 5,761,870 |
| web.de | 1.00% | 5,429,255 |
| bk.ru | 0.97% | 5,241,275 |
Antipublic #1
102.04GB of data, located in 1 folders across 303 files totalling 3,357,024,659 credentials, 1,750,879,665 of them unique.
TOP SOURCED BREACHES
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| Combolist of 1.4 Billion Credentials | 61.34% | 1,066,113,758 |
| Collection #2 Combo List | 53.18% | 924,311,303 |
| Collection #1 Combo List | 37.91% | 658,901,716 |
| Exploit.in combolist | 30.02% | 521,733,918 |
| Anti-Public Combolist | 28.90% | 502,337,232 |
| MySpace | 15.89% | 276,147,474 |
| Jadid List from Pemiblanc.com | 11.23% | 195,139,016 |
| Rambler.ru | 5.18% | 90,098,886 |
| Badoo | 5.15% | 89,495,410 |
| Pemiblanc.com | 4.92% | 85,515,628 |
| VK | 4.418% | 76,791,789 |
| 3.10% | 53,947,214 | |
| Zoosk | 2.94% | 51,029,988 |
| Active Account Cracking List | 1.85% | 32,134,781 |
| Fling | 1.56% | 27,018,773 |
| Mate1 | 1.50% | 26,063,474 |
| Neopets | 1.48% | 25,745,619 |
| 1.34% | 23,244,569 | |
| Last.fm | 1.20% | 20,784,007 |
| Gmail Combolist | 1.06% | 18,413,499 |
| 000webhost | 0.61% | 10,540,792 |
| NetEase | 0.583% | 10,136,099 |
| Onliner Spambot Credentials | 0.58% | 10,030,475 |
| Russian Bitcoin Security Forum Account Dump | 0.55% | 9,496,887 |
| Gaming Account Combolist | 0.44% | 7,575,398 |
| Netlog | 0.43% | 7,566,811 |
| Online Shopping Combolist | 0.43% | 7,550,468 |
| Evony | 0.42% | 7,354,689 |
| BTC-E | 0.36% | 6,237,555 |
| Gamigo AG | 0.34% | 5,817,239 |
| Tianya | 0.33% | 5,807,534 |
Top email domains
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| yahoo.com | 16.53% | 287,355,806 |
| hotmail.com | 11.54% | 200,627,856 |
| mail.ru | 9.49% | 164,910,297 |
| rambler.ru | 8.35% | 145,191,716 |
| gmail.com | 8.08% | 140,346,073 |
| yandex.ru | 5.93% | 103,122,437 |
| aol.com | 2.89% | 50,157,274 |
| bk.ru | 1.52% | 26,456,441 |
| list.ru | 1.34% | 23,247,075 |
| inbox.ru | 1.24% | 21,580,101 |
| hotmail.fr | 1.08% | 18,742,062 |
| web.de | 0.92% | 15,996,159 |
Antipublic MYR and Zabagor #2
19.49GB of data, located in 1 folders across 2,840 files totalling 667,776,099 credentials, 532,975,653 of them unique.
TOP SOURCED BREACHES
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| Jadid List from Pemiblanc.com | 63.10% | 326,572,962 |
| Collection #2 Combolist | 40.22% | 208,169,675 |
| Combolist of 1.4 Billion Credentials | 38.13% | 197,328,290 |
| Collection #1 Combolist | 30.72% | 158,980,550 |
| Exploit.in combolist | 17.35% | 89,794,881 |
| Anti-Public Combolist | 12.24% | 63,349,482 |
| Fling | 7.19% | 37,232,553 |
| Pemiblanc.com | 6.98% | 36,130,489 |
| MySpace | 2.80% | 14,465,565 |
| NetEase | 2.28% | 11,775,608 |
| VK | 2.19% | 11,308,046 |
| Neopets | 1.22% | 6,333,700 |
| Russian Bitcoin Security Forum Account Dump | 1.2% | 6,236,377 |
| Taobao | 1.17% | 6,064,128 |
| 17173 | 1.16% | 6,002,891 |
| Badoo | 0.96% | 4,983,317 |
| 0.96% | 4,970,450 | |
| Active Account Cracking List | 0.88% | 4,565,422 |
| Zoosk | 0.87% | 4,494,328 |
| 0.84% | 4,342,875 | |
| Last.fm | 0.82% | 4,266,588 |
| LifeBoat Network | 0.76% | 3,940,683 |
| LSGB.net | 0.76% | 3,925,897 |
| Dodonew | 0.70% | 3,611,533 |
| Gmail Combolist | 0.69% | 3,559,567 |
| 7k7k | 0.65% | 3,360,341 |
| Gaming Account Combolist | 0.60% | 3,107,004 |
| UUU9 | 0.58% | 2,981,890 |
| Gaming Combolist | 0.52% | 2,672,002 |
| Yue | 0.46% | 2,354,049 |
| 000webhost | 0.45% | 2,314,054 |
| Sprashivai | 0.44% | 2,279,753 |
| Ask RU | 0.44% | 2,279,441 |
| Youku | 0.41% | 2,095,699 |
| Mate1 | 0.41% | 2,093,663 |
Top email domains
| Source of Breached Data | Frequency | Number of Records |
|---|---|---|
| mail.ru | 23.11% | 119,604,468 |
| yahoo.com | 9.60% | 49,686,353 |
| rambler.ru | 8.75% | 45,267,319 |
| gmail.com | 6.89% | 35,666,828 |
| hotmail.com | 6.75% | 34,935,775 |
| yandex.ru | 6.68% | 34,576,801 |
| bk.ru | 5.53% | 28,590,872 |
| inbox.ru | 5.08% | 26,291,251 |
| list.ru | 4.72% | 24,443,179 |
| aol.com | 2.36% | 12,193,502 |
| qq.com | 1.41% | 7,297,787 |
| comcast.net | 1.39% | 7,194,809 |
Each of these files were hosted on popular hosting site MEGA, which allows anyone to download ephemeral files for short time periods These lists have since been copied and shared across numerous public forums and downloaded through numerous torrents.
Screenshot of files as shown on “MEGA.”
How can I determine if my email and password was in Collection 1-5 and the two new Antipublic lists?
If you would like to see if your credentials are in a user/pass combolist, you can activate a free individual account on our website. SpyCloud provides free, fully-automated and secure subscriptions to individuals.
In addition, SpyCloud empowers you with the ability to click on “sightings” so you can see just how many times the credentials have been sighted in prior breaches and where they more than likely originated from.
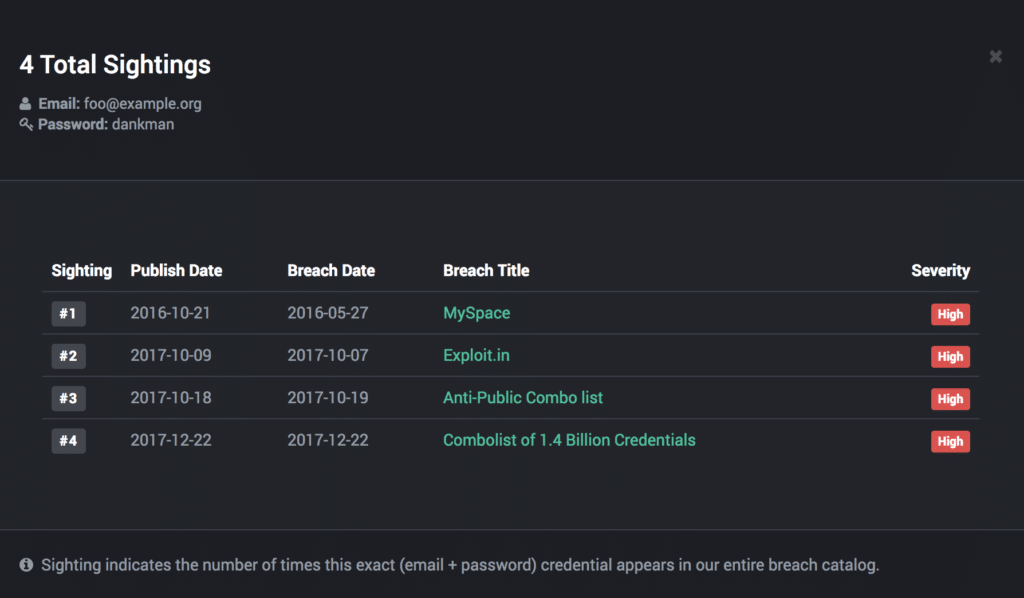
Screenshot of SpyCloud dashboard showing sightings of example credentials in our database.
What are best practices for protecting my individual passwords?
We highly recommend the use of a password manager so that all of your passwords are unique and easily managed. We also recommend that you enable two factor authentication (2FA) for all of your accounts – both professional and personal.
How can I protect my employees from credential stuffing?
At SpyCloud, we aim to empower our customers through actionable and proactive solutions by automating ATO prevention and letting them know their exposure so that they can remediate potential problems before they occur. Our researchers have deep expertise in the tactics, techniques and procedures (TTP’s) leveraged by criminals dealing in account takeover. We routinely see credentials along with a victim’s PII for sale on dark net markets and within private communities. This information translates directly to account takeover, which can be automated to scale attacks to massive levels.
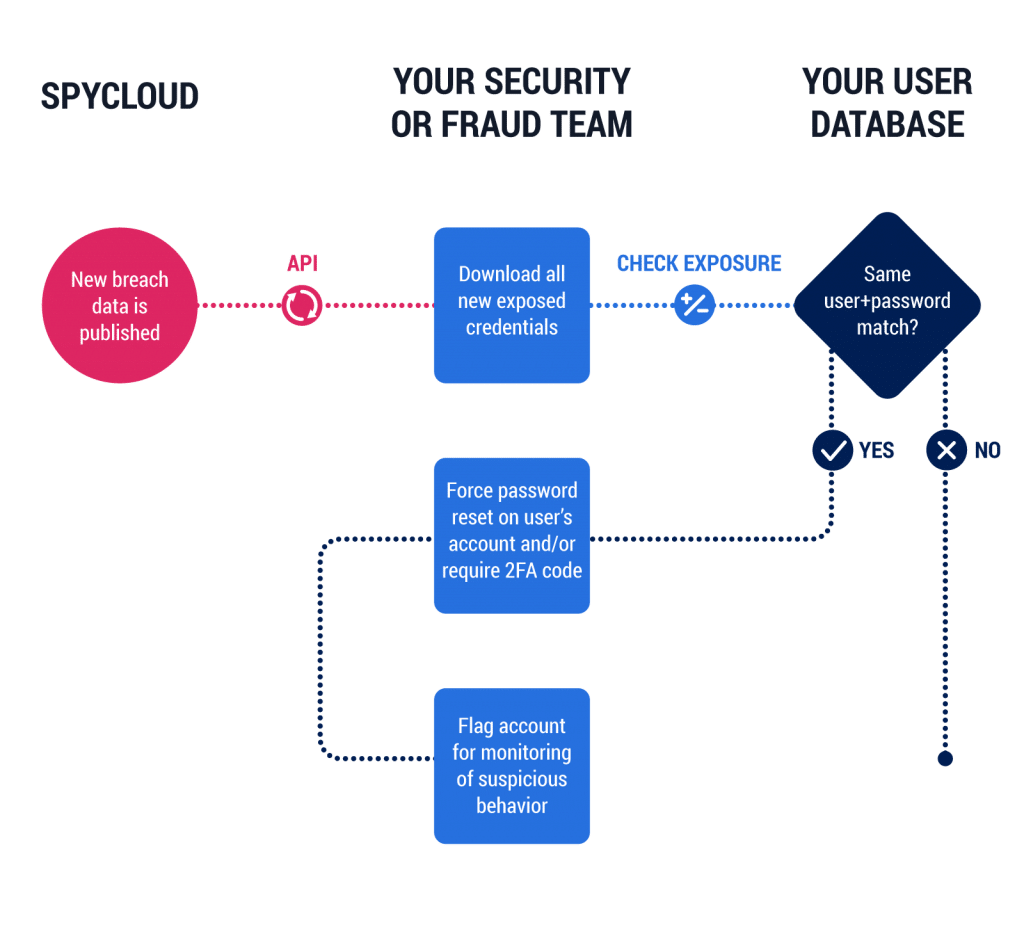
How SpyCloud analyzes credential theft attempts in near real-time
It’s easy to integrate SpyCloud’s API into your current application orActive Directory, to identify when your users’ credentials have been exposed and reset their passwords proactively when there is a match. Additionally, our solutions can empower your employees and users not to pick a password that has already been exposed with our NIST password screening capabilities.
In light of this news about the Collections combolist and the COMB combolist 3.2b dark web release, it’s important to remember that, regardless of the size of any active combolist, the prescription is the same: 1) don’t reuse passwords and 2) enable multi-factor authentication. For organizations, remember that behavioral changes across organizations take time. A safety net such as SpyCloud can, if anything, provide peace of mind for business leaders and individuals alike.