Let’s talk about the elephant in the room.
The number one challenge SOC teams faced this year was “too much data, not enough information” according to a 2023 report from Tines.
And a large culprit of the problem is legacy threat intel.
As threat actors pivot to new tactics at a quicker pace, traditional threat intelligence alone is no longer sufficient to safeguard critical assets and data.
We have to start thinking about next-generation approaches if we hope to keep pace – let alone outpace – cybercriminals. To do this, we have to look at the big picture, which today requires us to think “beyond the device” and look at digital identities as whole. It’s a necessary shift if we want to really be able to safeguard employees and customers.
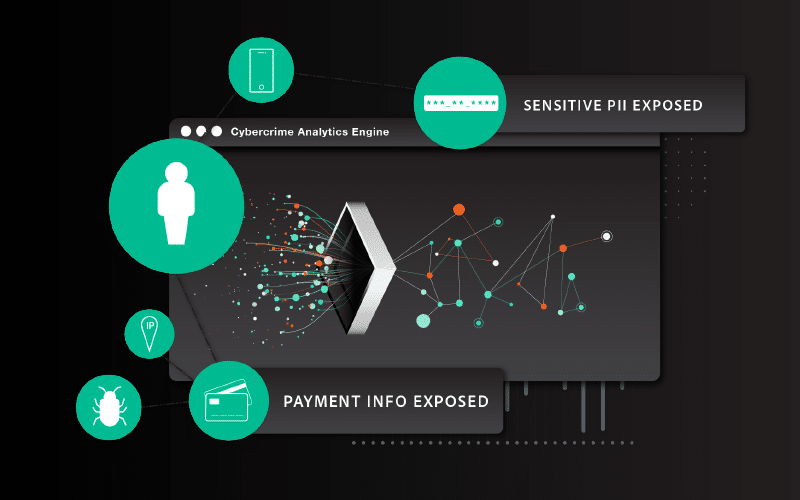
And the same shift needs to happen with the data we use to inform our prevention and protection strategies. With recaptured threat intel data, we have to pivot from focusing on quantity to quality. Ingesting quality darknet data from both breach and malware infections is necessary to actually understand risk. We need that data to be normalized, deduped, enriched, and analyzed before it is even delivered to security teams in order for it to be useful, which will in turn help teams cut down on manual work associated with MTTD and MTTR while achieving better outcomes.
But first things first. Let’s back up a step and revisit the limitations of traditional threat intelligence. Then we can explore the concept of next-gen threat intel and get thinking about how to adapt to combat evolving criminal tactics.
Traditional threat intel: What it is and what it’s good for
Historically, threat intelligence has been about using high-volume data to help determine organizations’ security approach. It generally involves collecting, and disseminating information about malicious actors, tactics, and techniques.
These are all good things for teams to have a pulse on. And traditional threat intelligence is really good at providing some valuable, broad context that can help us better understand threats and inform certain strategies to mitigate risks.
But when we talk about traditional threat intelligence, we’re really talking about big ol’ data feeds. Those feeds include things like Indicators of Compromise (IoCs) including malware signatures, IP addresses, and domain names associated with malicious activities; insights into threat actor profiles and their tactics, techniques, and procedures (TTPs); details about exploit methods; historical attack data; and other contextual information for understanding the threat landscape.
Again, it’s all useful, but not holistically useful enough if we think about everything we’re up against in today’s threat landscape.
Where traditional threat intel falls short
While traditional threat intelligence has its benefits, it also has several limitations.
- The first issue we run into with traditional threat intel is what we started with at the beginning of this article: data overload. Typically, threat intel feeds scrape pretty much everything and anything, with little work put into curating and enriching the output. A lot of data may be good for getting the big picture, but quickly becomes a hurdle when teams try to come to resolutions without negatively impacting team workflows or increasing the burden on existing resources. If you happen to have a large team with advanced resources who can spend a lot of time manually sorting and sifting through data to uncover meaning and correlate risk, it’s less of a problem…but still not ideal.
- The next major issue is with fidelity. Traditional threat intel leaves heavily on OSINT, or publicly sourced data that is easy to scrape in mass quantity. It’s not an efficient way to pinpoint definitive evidence of compromise since it can be difficult to verify sources, and the data is commoditized.
- Traditional threat intelligence tends to focus on known threats and known attack techniques. Cybercriminals, however, are continuously evolving their tactics and employing sophisticated techniques, including advanced malware and exfiltration methods. Traditional threat intelligence may struggle to keep up with these rapidly changing tactics.
- Some threat intelligence solutions are free (or practically free), to which we say: you get what you pay for. Free sources are a great starting point, but they only give you the haystack without the needle.
- Traditional threat intelligence is also often retrospective in nature. It relies on historical data and known signatures or indicators of compromise (IOCs) to identify threats. This reactive approach means organizations may only become aware of an attack after it has already occurred, or are wasting cycles sorting through old, useless data.
- Finally, traditional threat intel tends to be just that: intelligence, or information. Analysis is left to security teams, as is prioritization and actioning of response.
Obviously, we’re a bit biased, because our entire mission is around fixing the legacy threat intel problem. We believe in deeper, cleaner, more actionable data – because we know it’s the only way to better position security teams against modern and evolving threats.
The next-gen threat intel challenge: Malware-exfiltrated data
Our research team spends a lot of time looking at data, and there’s no denying the biggest threat trend we’re seeing: the uptick and evolution of malware for exfiltrating sensitive data. Many threat intel vendors aren’t yet collecting malware records, but it’s clearer than ever that next-gen prevention strategies have to account for monitoring and remediating exposures tied to malware-exfiltrated data.
Infostealer malware
Newer malware-as-a-service technology like LummaC2 stands out because it can steal extremely sensitive data – like browser-based 2FA, remote desktop software configs, and passwords saved in browser-based or locally-stored vaults. These features are in addition to its ability to exfiltrate local files, steal saved credentials and cookies, and parse local cached browser data like autofills.
Mobile malware
Mobile malware technology is advancing, giving bad actors new ways to exploit vulnerabilities and steal personal data, passwords, and financial information. Mobile malware infections and the rise of personal device use for transmitting corporate data increases the risk of follow-on attacks.
macOS malware
Stolen session cookies and session hijacking
Malware siphons everything from an infected device, including credentials and web session cookies. Leveraging malware-siphoned web and device session cookies, bad actors can perpetrate session hijacking, which bypasses the need for credentials, multi-factor authentication (MFA) and even passkeys altogether. Session hijacking is an increasingly prevalent precursor to fraud, and even more detrimental to the enterprise, ransomware attacks.
Stolen API keys
Infostealer malware is also one of the most prevalent ways criminals get access to API keys. Often the theft of an API key for an administrator or service account can enable a criminal to directly access and control your application. Applications that support customer access through API keys can leave customer personally identifiable information (PII), sensitive data, or even access to financial resources at high risk when the API key is stolen.
How to start thinking about next-gen cyberattack prevention
When we think about today’s landscape and effective prevention, it’s really about:
- Strategy, and what it’s informed by; and
- How it gets done, which ideally involves a heavy automation component
The identity-centric vs. device-centric approach…plus zero trust
There is a new perimeter in security, and it’s composed of the digital identities of users and customers. An identity-centric security approach concentrates on protecting user identities and the data associated with them, regardless of where the user is located or what device they are using.
Identity-first security is also a key component and front line of defense in achieving zero trust. Verifying everything, and trusting nothing is an effective and proactive strategy in the overall security program that needs to be adopted to reduce the risk of cyberattacks. An identity-first security approach assumes that all users are potential targets for threat actors who are finding ways to exploit any weakness possible, even bypassing modern authentication technology to gain access to user accounts.
In order to protect the new perimeter successfully, security teams need timely, definitive evidence of vulnerable digital identities exposed in data breaches and malware infections.
This is a shift we collectively have to make to be successful in combating cybercrime.
Automation
The other key pivot we need to make is to automate, automate, automate. At SpyCloud, our researchers recapture data early in the breach and malware infection timeline to decrease organizations’ exposure and stay ahead of follow-on attacks.
In order to move fast enough, teams need to leverage exposure information in automated SOAR and SIEM workflows. Once known exposures have been identified, these automated workflows should be used to remediate and shut doors on attackers are key to keeping your lead. Automation not only improves your response times, but also frees up resources for more critical tasks.
Moving beyond traditional threat intel
We – and more importantly, cybercriminals – have outgrown traditional threat intel. For decision-making and actionability, security teams have to have reliable, definitive exposure data – regardless of the data exfiltration techniques being used by criminals – and be able to do something about it before attackers do.
It’s not easy, but it’s a simple idea. You have to know what criminals already know about your business to be able to prevent future attacks.
SpyCloud levels the playing field by using the exact data cybercriminals have against them — enabling security teams to take immediate action on the users whose exposure in breaches and infostealer malware infections put their business at risk.
Stop guessing. Start protecting.