USE CASE: ZERO TRUST
Continuous Zero Trust
SpyCloud constantly reevaluates and checks employee identity exposures, giving you definitive evidence when an identity is compromised by malware, phishing, and third-party breaches. Our enriched telemetry powers dynamic access decisions, so you can trust every user, every time.
Power Zero Trust with continuous identity verification
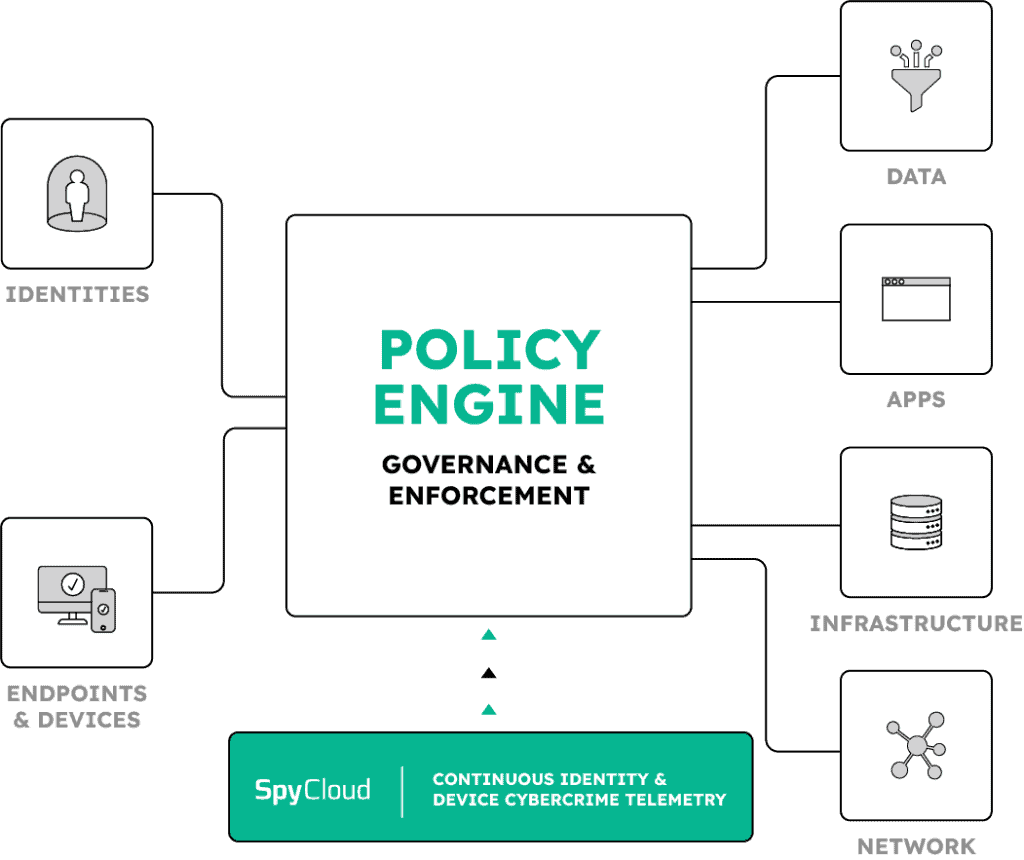
A mature Zero Trust strategy requires more than login checks – it demands continuous visibility into identity risk. With SpyCloud, accelerate your Zero Trust initiatives with policy decision points that continuously evaluate employee identities for compromise using real-time identity exposure insights. SpyCloud enhances Zero Trust maturity by delivering pre-auth and mid-session compromise intelligence other tools miss.
How SpyCloud solves the modern Zero Trust challenge
As organizations shift to a continuous authentication model, identity exposure monitoring becomes a critical piece of the puzzle. Unfortunately, most organizations’ Zero Trust implementations don’t continuously input high-fidelity darknet telemetry into their policy engine. In those cases, you leave an open door for cybercriminals to sidestep MFA and SSO in session hijacking attacks. Zero Trust policies must adapt to evolving user identity footprints, especially as attackers exploit identity compromise between login events.
The majority of Zero Trust implementations are missing a key input. Here's how SpyCloud is closing the gap. Traditional Zero Trust policy engines only test the validity of users and devices when they first access the network. This approach doesn't take into account the vast amount of identity, device, and access information criminals already have in hand. Beating bad actors is a relentless cycle made more challenging by digital Zero Trust implementation should mirror that reality. Continuous Zero Trust means your identity protection never sleeps, constantly verifying user identities and endpoints for exposures. Truly mitigating risk hinges on the ability to make informed decisions around the clock. Spy Cloud feeds your Zero Trust engine with actionable breach and malware data, keeping your policies always informed and one step ahead. Harnessing cybercrime telemetry, SpyCloud integrates with your existing identity and security tools and gives you the power to make informed decisions about whether a user account should be allowed access based on real evidence of compromise. Cybercrime doesn't take a break, and neither do we. Protect your organization against next -gen identity threats with Continuous Zero Trust powered by SpyCloud.
EXPLORE PRODUCTS
Add Zero Trust depth with these SpyCloud products for enhanced identity threat protection
Stop identity-based attacks by preventing the use of stolen credentials and other authentication artifacts
Uncover and act on malware- infected devices leaking sensitive identity data that puts you at risk
Continuously monitor and remediate exposed identity data across directory services like Active Directory, Entra ID, and Okta Workforce
EXPLORE WHO USES SPYCLOUD
Defenders
we help
Identity & access management teams
SOC & incident responders
Surface active exposures and respond to identity-driven threats across employee devices and sessions
Compliance teams
Fulfill identity security mandates across Zero Trust and regulatory frameworks
Integrations






Next steps
Ready to close the Zero Trust gap attackers exploit?