PLATFORM SOLUTIONS
Holistic Identity Threat Protection
SpyCloud empowers businesses to prevent, remediate, and investigate cybercrimes – now in one unified SpyCloud Console
Our holistic identity approach illuminates and eliminates hidden darknet exposures across employees, contractors, customers, and non-human accounts – and allows analysts and investigators to achieve deeper insights and faster outcomes than ever before possible.
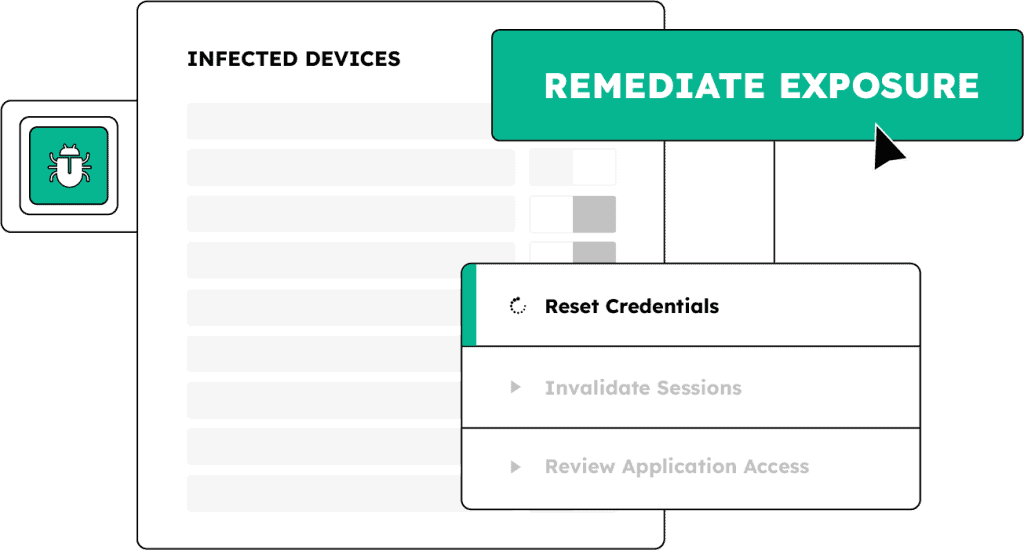
About the SpyCloud platform
Our solutions are built on curated, enriched, and correlated darknet data insights – delivering automated solutions for enterprise-level identity threat protection. Start protecting employee identities, safeguarding consumer identities, and powering your cybercrime investigations with better data today.
Uncover hidden relationships between identity assets – improve outcomes of investigations into financial crimes, insider risk, ransomware attacks, and more.
Access comprehensive breach, malware, and successfully phished data to add value to security and fraud detection products and services.
Protected by patents: https://spycloud.com/legal/patents/





SpyCloud offers out-of-the-box API integrations with top technology vendors across SIEM, SOAR, EDR, TIPs and more to power analysis, detection, and remediation via automated workflows.
INDUSTRY SOLUTIONS
Solutions for every sector
SpyCloud is the secret weapon for security leaders, practitioners, and service providers.
SpyCloud is the edge you need to make stolen
identity data useless to bad actors
At the root of the cyberattacks most costly to businesses are identity exposures that give attackers a way into your enterprise. SpyCloud takes the advantage away from criminals and gives it back to you.
WITHIN
5
minutes
Up to
60%
SOC TEAM TIME AND RESOURCES SAVED
12x
MORE IDENTITY RECORDS
GET MORE ANSWERS WITH HOLISTIC IDENTITY MATCHING
875B+
RECAPTURED ASSETS
200+
DATA TYPES
RECAPTURED breach, malware and phishED data
3.5
MONTHS
AVERAGE PAYBACK PERIOD FOR SPYCLOUD CUSTOMERS
TEAMS WHO USE SPYCLOUD
Powering security and identity teams worldwide
SpyCloud is the secret weapon for security leaders, practitioners, and service providers.
Next steps
Start here
Uncover threats to your organization like malware-infected employees, stolen session cookies, and recency of breach exposures