Webinars

An Inside Look at Game-Changing Threats in 2024
In this webinar, we cover top trends from the SpyCloud 2024 Identity Exposure Report. Learn about the identity threats putting organizations everywhere at risk.

From Zero to Hero: What Your Security Team Can Unlock with Actionable Data
Learn how actionable data analytics from SpyCloud helps your security team scale, use resources more efficiently, and shorten investigation time.

The Illicit Chinese “Pantsless Data” Trade
Hear from SpyCloud Labs researchers how Chinese cybercriminals are accessing, exfiltrating, and trading vast amounts of PII, with international impact.

Ransomware Reality Check: The New Landscape
This webinar breaks down the most important findings from SpyCloud’s 2023 Ransomware Defense Report, and what your organization can do to get ahead of emerging cyber threats.

Access Granted – The reality of compromised credentials in a passwordless world
On-Demand Webinar: Explore the evolution of authentication and scrutinize common myths around passwordless technology.

Don’t Play Footsie with Cybercriminals
On-Demand Webinar: Unveil the top darknet exposure trends for London’s FTSE 100 companies, including insights on password reuse, stolen session cookies and cloud app exposures

Top Identity Exposure Trends from the Criminal Underground
On-Demand Webinar: We break down the latest trends related to identity exposure in the criminal underground and how this data puts organizations and consumers at risk of cybercrime.

Insane in the Membrane: Why Old Tactics Fail for Ransomware Prevention
On-Demand Webinar: Learn about a new, more complete and more effective approach to preventing ransomware called Post-Infection Remediation.

Shining a Light Into the Dark Web
On-Demand Webinar: Learn how stolen data makes its way from small circles of bad actors to the dark web and how to identify legitimate consumers interacting with your site vs. criminals leveraging stolen data.
Mind the Gap: Closing Ransomware Risk Visibility Gaps
On-Demand Webinar: Benchmark your ransomware preparedness & discover proactive strategies to solve your defense blindspots.
Combating Fraud from Stolen Cookies: Introducing SpyCloud Session Identity Protection
On-Demand Webinar: A detailed look at how anti-detect browsers + malware-stolen data put consumers at risk of fraud, and how Session Identity Protection helps protect your bottom line by offering early warning of malware-infected consumers with compromised web session cookies.
The Fraudacity of Cybercriminals: How 15.5B Recaptured Data Assets Shine a Light on the Criminal Underground
On-Demand Webinar: Analysis of the 15+ billion assets we recaptured in 2021 and what we can learn from patterns we’ve observed in the criminal underground over the last 12 months.

All Criminals Want for the Holidays is You(r Data): An Inside Look at How Cybercriminals Profit Off the Holiday Season
On-Demand Webinar: SpyCloud researchers share an inside look at 2021 holiday shopping trends on popular cybercriminal communities, including botnet logs for sale that allow bad actors to impersonate your consumers.
The Ransomware/Stolen Credentials Connection
On-Demand Webinar: We break down the ransomware ecosystem, adversary groups’ latest tactics, and strategies to mitigate your risk and avoid paying millions to ransomware gangs.
Surviving a Data Breach – On-Demand
Security leaders who have been through worst-case scenarios offer real-world advice for stronger breach prevention & response. Get the audio file or watch the panel webinar on-demand.
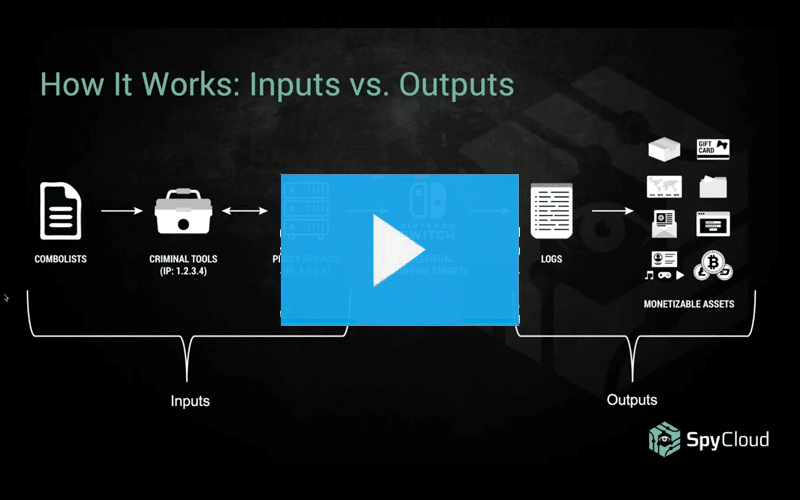
How Credential Stuffing Tools Are Made
Learn how credential stuffing works and get insights into the tools of the trade (including some very sophisticated custom Nintendo crimeware). Discover why stolen accounts that don’t have obvious monetary value can be profitable for cybercriminals.
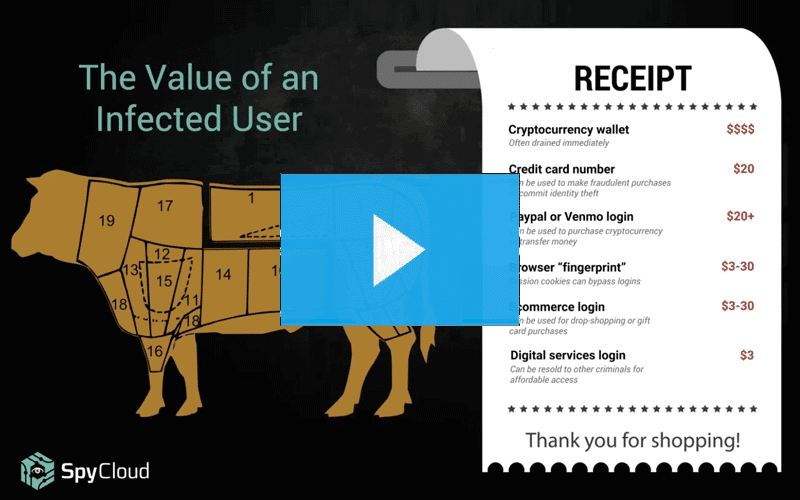
I Put a Keylogger On You, and Now You’re Mine: What Cybercriminals See When They Infect a Host with Malware
See malware from the criminal perspective, including how the data collected from infected machines gets monetized. Learn how to shield your organization from the damage caused by credential-stealing malware.
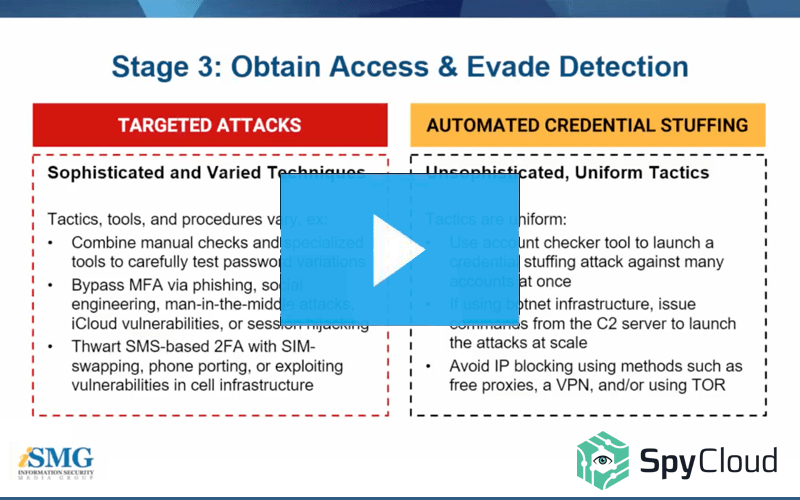
Targeted Attacks: How Sophisticated Criminals Bypass Enterprise Security Measures
If your account takeover prevention program primarily focuses on automated credential stuffing attacks, you may be leaving your organization exposed to serious losses. Learn more in this webinar we hosted with ISMG.
Hard Truths About ATO & Strategies To Defend Your Enterprise
Protecting your enterprise from breaches and account takeovers has never been a bigger challenge.
