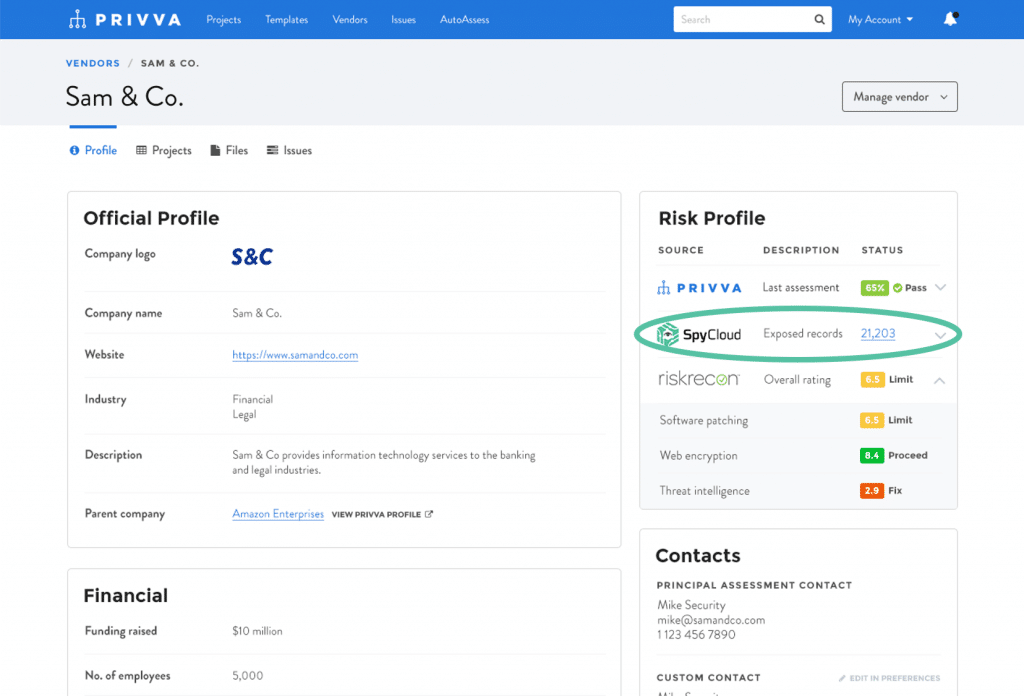
Privva & SpyCloud
Through our integration with Privva, you now have access to high-level details about your breach exposure.
Get access to all of your domain’s compromised data with SpyCloud.
The SpyCloud Data
Employees often use their corporate email address to sign up for third-party websites. They’re not intending to cause harm; they’re simply trying to minimize the number of login credentials they have to remember. When those websites are breached, the employee’s information is exposed to cybercriminals, and if they have reused their corporate passwords, your organization is at risk. Criminals can easily exploit the exposed credential pairs to gain access to corporate systems – jeopardizing customer information, funds, IP, and sensitive employee personally identifiable information (PII).
The SpyCloud data you see in Privva represents:
Corporate Records Exposed
A corporate breach record is the set of data tied to a single corporate email address within a data breach. One employee whose information appears in three different breaches would result in three distinct breach records. Each exposed record may contain information that a criminal can use to take over the employee’s accounts or commit fraud, such as passwords and PII.
Potential Executives Exposed
Corporate credentials that have appeared in a data breach and are tied to employees with high-ranking titles, putting them at increased risk of targeted account takeover attempts, business email compromise (BEC) fraud, and extortion.
Date of Last Exposure
Represents the date of the most recent data breach containing employee email addresses from your corporate domain.
Protecting your users from corporate account takeover requires that they reset their compromised password to a strong, unique password not used for any other account. Get the details on your users’ exposed passwords and PII by contacting SpyCloud.
With SpyCloud, you get enterprise-level, automated account takeover and ransomware prevention powered by Cybercrime Analytics based on actionable darknet insights.
SpyCloud offers the largest collection of recaptured darknet data in the world, combined with the earliest possible recovery. Our proprietary engine quickly ingests data from breaches, malware-infected devices, and other underground sources, then cleanses and enriches the data – adding context to the records so you understand the severity of the exposures (the source, breach description, and the actual password in plaintext). Our customers get notifications of compromised accounts and passwords far sooner with SpyCloud than any other provider.
Assets
Total
Passwords
Email
Addresses
Data Types
How Account Takeover Happens
With hundreds of online accounts to keep track of, it’s inevitable that people will reuse their favorite passwords between corporate and personal accounts. When a data breach exposes those passwords to criminals, every account that shares the same login becomes vulnerable to account takeover as criminals systematically test stolen credentials across many sites.
Without visibility into which passwords criminals have access to, it’s challenging for security teams to prevent account takeover for their users. SpyCloud helps busy security teams stay a step ahead of cybercriminals by checking user logins against the largest database of recovered breach assets in the world.
Recommendations to Prevent Account Takeover
Everyone has a part to play:
The security org should:
- Grant access to a password manager as an employee benefit for work & personal use
- Enable Multi-Factor Authentication
- End 90-day forced password rotation policies (it encourages users to recycle passwords)
- Implement automated credential monitoring so you can detect compromised passwords early
Users should:
- Use a unique password for every online login & get old, weak passwords out of your rotation
- Turn on Multi-Factor Authentication for all accounts that offer it
- Use a VPN to work over public WiFi
- Don’t download attachments or click links in emails from unknown or untrusted sources (they could contain malware)