Automatically detect and remediate passwords exposed on the dark web within 5 minutes
For the criminal underground, getting access to systems and networks is a primary objective, and over the past several years, we’ve seen adversaries move towards automation and advanced cybercrime enablement services to increase their chances of success.
Criminal tactics are evolving. Bad actors are experimenting with technology like automation, AI, and custom-made tools for the sole purpose of evading detection. That innovation changes how (and how fast) they collect passwords and other valuable data. It also alters how they check the validity of stolen credentials, and the ways they programmatically distribute stolen information to their other criminals.
As criminals turn to automation, so have defenders. SpyCloud’s Active Directory Guardian – powered by our proprietary identity analytics – gives teams an important competitive advantage in the race against the clock. With Active Directory Guardian, you can remediate exposed credentials faster than it takes to get through your inbox at the start of the day, or to walk to Starbucks for a coffee – within 5 minutes.
How Active Directory Guardian protects your employees – and your business – around the clock
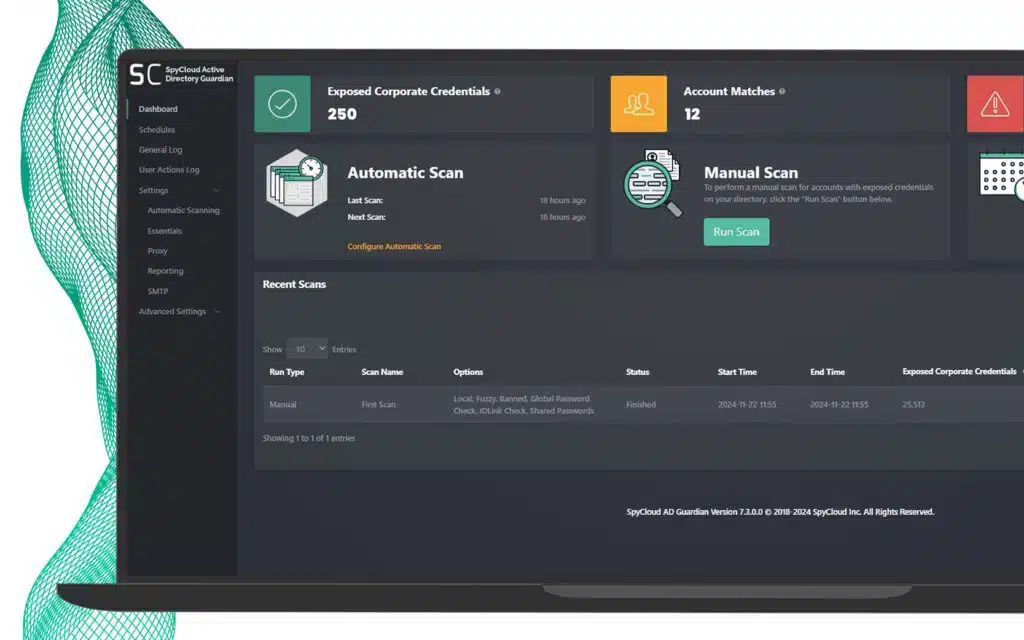
Active Directory Guardian automatically detects and remediates exposed passwords
Security teams used to look at alerts and manually check to see if the exposed passwords were in use by employees. Adversaries responded by checking stolen passwords faster after getting them from breaches, malware, or phishing attacks, and then automating attacks using the freshly exposed data. Without a low latency, high-fidelity system to automate that workflow for defenders, the chances of protecting against identity-based attacks goes down dramatically.
SpyCloud’s Active Directory Guardian automates the remediation of stolen credentials – and now offers enhanced enterprise protection with a variety of scanning options to detect exposed identities. It automatically scans SpyCloud’s database for any recently published credentials that match an employee email and Active Directory password in use, and offers additional scanning to identify more exposed employee passwords, including:
- Exposed passwords actively in use
- Exposed passwords used in past roles
- Exposed passwords associated with personal accounts
For extra assurance, Active Directory Guardian only compares password hashes against SpyCloud’s full database of stolen credentials, offering unmatched protection.
AUTOMATIC SCAN
Automatically look for exact matches of Active Directory credentials in SpyCloud’s database to reset automatically.
This detects and resets exposed passwords within 5 minutes.

MANUAL SCAN
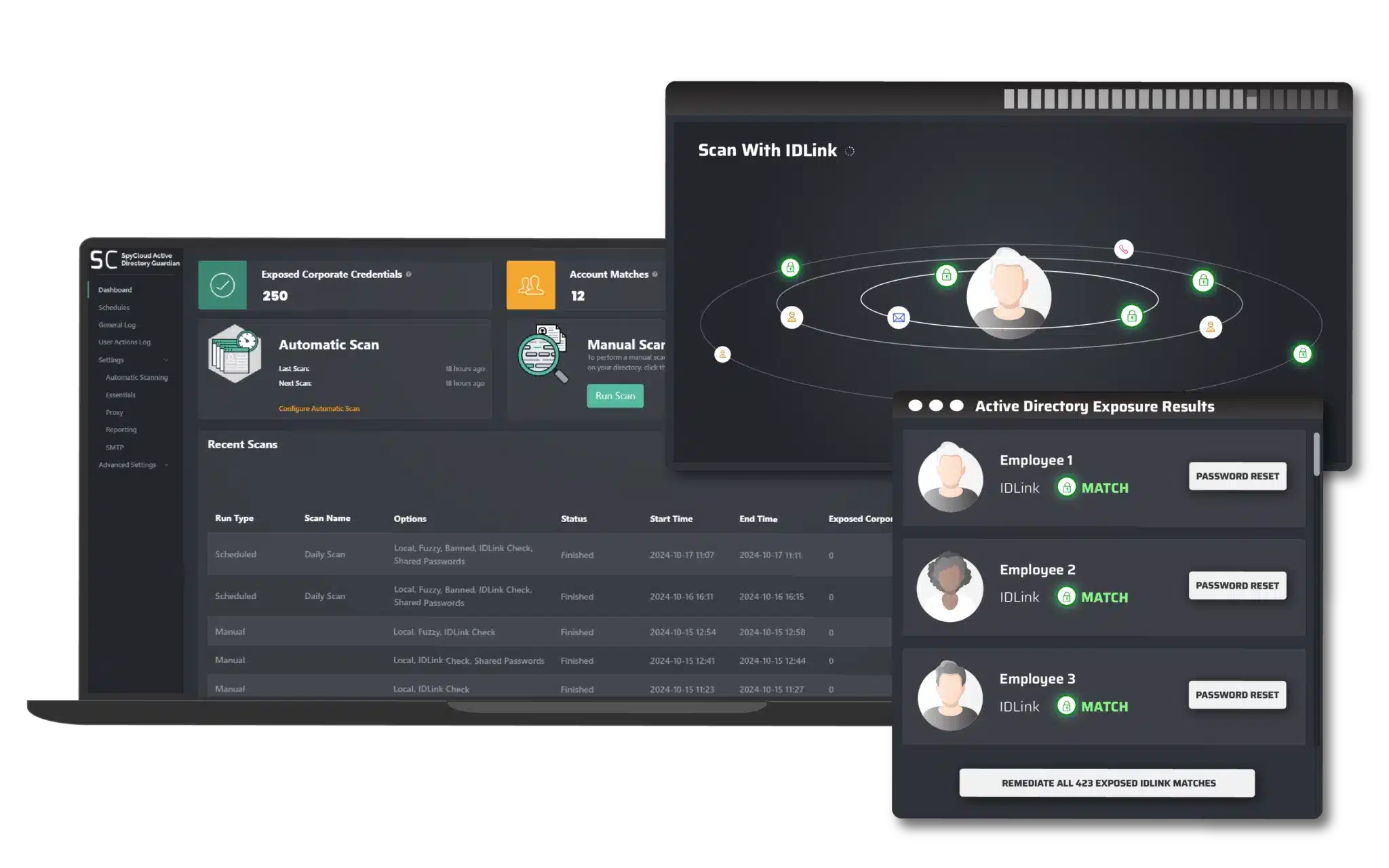
Configure scanning options for timing and depth to match your workforce’s behavior, including IDLink analytics to detect hidden exposures.
This finds up to 14x more passwords per user.
With the latest version of Active Directory Guardian, you can:
- Quickly and automatically scan SpyCloud’s database every five minutes to detect any recaptured credentials that match an in-use pair
- Conduct deeper scans with SpyCloud’s proprietary IDLink identity analytics to detect exposures tied to an employee’s digital identity - past or present, personal or professional - identifying hidden compromised credentials in use
- Dynamically generate and test 1,000 common variations of exposed credentials using “fuzzy matching” - similar to how criminals automate stuffing attacks - to detect compromised credentials even if they’ve been slightly modified
- Automatically apply remediation policies for exposed passwords, depending on the type of exposure or source of the matched password, and remediate within 5 minutes
Here are some common scenarios that Active Directory Guardian is able to automate for your team.
01
Employee reuses Active Directory credentials on third-party sites
People reuse passwords to make their lives easier. Unfortunately, that’s also the easiest way for criminals to take over employee access. It’s also become one of the easiest things to automate for adversaries. When they get an email with a password from a third party database breach, they already know the email it belongs to and can try it to see if it works.
Active Directory Guardian enables you to check Active Directory passwords that have been exposed and are tied to employee emails and then automatically force a password reset.
02
Employee accidentally infects device with infostealer malware, exposing sensitive identity data
Perhaps an employee accidentally clicked on a malicious ad for a legitimate piece of software and downloaded malware. The infostealer malware ran its executable and stole all the employee data – sensitive identity information, the machine details, their session cookies, and, of course, their set of application credentials, including Active Directory. Criminals are most likely to automate their follow-on attacks using this stolen data, so time is of the essence.
With SpyCloud’s latest improvement for automatic scanning, as soon as SpyCloud collects this high-value information from the darknet and confirms it matches the in-use credential pair of an active employee, you control the next step. Defenders can automatically detect and reset the password within 5 minutes, before criminals can take action.
Active Directory Guardian is always scanning for high-priority malware-exfiltrated records that match your employee. Speed helps protect your enterprise.
03
Employee reuses their work password – this time, with their personal accounts
Some employees think that, so long as they aren’t using their work email address, reusing a password for an account registered under their personal email address is perfectly safe. In reality, it’s easy for an attacker to connect the employee’s personal alias, jsmith@gmail.com, to their work email, jsmith@employer.com. It’s much harder for your security team to do the same, especially for hundreds or thousands of Active Directory users.
Active Directory Guardian helps you monitor for this type of scenario at scale in two ways:
- The first is by configuring deeper scans with SpyCloud’s IDLink identity analytics to detect if an employee’s current credentials match a hidden compromise spanning their holistic identity - personal and professional, past and present. This gives Active Directory Guardian a powerful way to automatically protect employee accounts by knowing the broader context of their password use and exposure
- The second way Active Directory Guardian can protect employees from shared passwords is by checking your users’ Active Directory passwords against the entire SpyCloud database at a customized frequency. This ensures compliance with NIST’s recommendation to prevent the use of compromised credentials by detecting if a user’s Active Directory password has ever been detected in a third-party breach, malware infection, or successful phishing attack, whether or not it was combined with their Active Directory username.
04
Your employee switches up their favorite password for ‘extra security’
Sometimes your employee switches things up with a few trivial changes to a favorite password, whether to get around password complexity requirements or to create a “more secure” password that they can still remember. The passwords in your employee’s arsenal include sprinkles, Sprinkles, Spr1nkles, Spr!nkles, and (for extra-extra-important accounts), Spr!nk13s.
Your employee doesn’t think of these “fuzzy” variations as password reuse because they’re not exact matches. In reality, they may as well be. Unsophisticated criminals have access to advanced crimeware that can check for common password variations like these, making fuzzy password reuse a security risk for your enterprise.
Active Directory Guardian helps here, too. If your employee uses a fuzzy variation of a password that has been exposed in a third-party breach, malware infection, or successful phishing attack, you can detect and automatically reset with Active Directory Guardian.
For even stronger identity threat protection, you can run daily Active Directory scans with both IDLink analytics and fuzzy matching to catch hidden threats. IDLink analytics detects all known exposed passwords across an employee’s holistic identity, while SpyCloud’s fuzzy logic checks 1,000 variations on each. This combination delivers the best of both worlds, flexibility and coverage working hand in hand to protect access. Active Directory Guardian eliminates the scale of identity exposures in one click.
The risk one identity poses to your organization:
Corporate Credential
Found with IDLink Advanced Analytics
Found with SpyCloud Fuzzy Matching
With SpyCloud’s Active Directory Guardian
05
Your employee chooses a common password, like the name of their favorite sports team or the name of your company.
Your employee shapes up and stops reusing passwords. Thanks to some inspiration from their favorite sports team, they come up with password they’ve never used before on any site: Longhorns#1.
Unfortunately for your employee, they’ve chosen the same password as many other Longhorns fans, several of whom have been included in third-party breaches. Luckily, Active Directory Guardian offers the option to check your users’ passwords against every password in our recaptured database, independent of username. Even though your employee has never been involved in a breach using this specific password, Active Directory Guardian can flag this password to help you identify weak, expected, or compromised passwords in accordance with NIST’s recommendations.
Active Directory Guardian also includes a banned password list that your team can add to, enabling you to detect and reset passwords that an attacker might expect users at your organization to choose. Using context-specific passwords like the name of your company is such a common approach that the NIST password guidelines specifically recommend checking for it.
06
Your company runs a hybrid environment with Active Directory and Okta.
If your organization uses Okta as the primary identity provider while maintaining an on-prem Active Directory environment, you’re in good company. Many enterprises rely on a hybrid setup and need a way to remediate exposed credentials automatically – across both environments.
SpyCloud’s Active Directory Guardian is designed to work with your existing identity setup. When it detects an exposed credential in use by an employee, it can initiate a reset through Okta – your system of record – rather than triggering a reset directly in Active Directory. This approach ensures remediation actions respect your policies and prevent follow-on attacks.
Whether you’re fully cloud-native or operating in a hybrid AD and Okta environment, Active Directory Guardian integrates into your identity workflows to support secure, automated password resets that don’t disrupt daily operations.
Automation wins when powered by holistic identity matching
Ultimately, as defenders, our goal is to do our best to protect our users and the organization. The most effective way to do that is to use the best available data and to automate where appropriate, as much as possible. The more we can let machines do what they do well, the more bandwidth we have to move the needle on security in other parts of our organizations.
Combining the speed of SpyCloud’s automatic scanning, comprehensive coverage with proprietary identity analytics, and ease of use with automated remediation, your workforce is in good hands, and you can prevent criminals from taking over your accounts.
Interested in learning more about Active Directory Guardian?
Download the Active Directory Guardian datasheet to learn more about scanning and remediation options.
Using a different directory store? Learn more about our other Identity Guardian offerings including Entra ID Guardian or Okta Workforce Guardian.
Check for exposed employee data
Use our dark web exposure tool to identify exposed employee data that could be putting your business at risk.