How does password cracking work? Considering SpyCloud’s industry-wide expertise in building and maintaining the breach database with the most plaintext passwords possible, it’s a question we get asked a lot.
Much of the cryptography terminology we are familiar with in the industry is different from what is used by criminals in the underground. Below is a primer explaining the terms used within online “cracking communities,” and what they mean for us as defenders.
Cryptography Basics
Cracking & Cracking Communities
As you could have guessed, “cracking” refers to cracking passwords, and online cracking communities are where those who profit from low-stakes credential stuffing tend to converge. In our recent blog post Discord’s Dark (Web) Side, we explored some of the darker offshoots of the popular chat platform Discord, including channels dedicated to cracking specifically. Although expressly against Discord’s user agreement, several such channels continue to exist. Many well-established cracking communities are accessible via the clearnet and don’t require access to the dark web
Figure 1: Screenshot of the homepage of popular online cracking community “Cracking King.”
Figure 2: Screenshot of the online cracking community Kleoz.
Password cracking refers to the process of recovering passwords (or stealing them) from data that has been stored or transmitted. Today, passwords are almost always encrypted, and the common brute-force attack approach utilizes dictionaries that contain some of the most commonly-observed character sequences for passwords. Passwords that are “easily crackable” take less time to decrypt using common password cracking techniques.
Speaking of brute force attacks, since you likely work in the security space, you’re probably familiar with them. These are the attacks that repeatedly guess passwords until a match is found. These cryptanalytic attacks test many character combinations at once, and success is much faster when the password being guessed is a shorter one. This is why, in our testing, passwords that were shorter in length and easy to guess were cracked almost instantly. For longer passwords, dictionary attacks are more effective because they have many more possible values to guess. This is where dictionaries come into play.
Dictionaries, Combolists and Rainbow Tables
In cryptography, dictionaries refer to lists of common words, passwords, character sequences and/or phrases that can be used to “guess” passwords in credential stuffing attacks. Dictionaries are also sometimes called “wordlists.”
The image below, which was obtained from an online cracking forum, advertises a free dictionary containing 1,493,677,782 words. As described, this dictionary contains “every wordlist, dictionary, and password database leak” the seller could find, including words compiled from Wikipedia databases, and even books from Project Gutenberg. This robust, catch-all technique was implemented directly by those involved in credential stuffing to be able to guess a multitude of words – especially those that some of us may use to make passwords that are easily remembered.
Figure 3: Advertisement for a Password Cracking Dictionary from an online cracking forum.
“The list is responsible for cracking about 30% of all hashes given to CrackStation’s free hash cracker. Using the list, we were able to crack 49.98% of one customer’s set of 373,000 human password hashes to motivate their move to a better salting scheme.”
It’s important to note that not all credential stuffing attacks require dictionaries. Credential stuffing is nearly synonymous with brute-forcing, the act of testing sets of previously breached credentials and username/password combinations until a match is found.
Rather than “mindlessly” guessing every possible value, rainbow tables compress hashes to reduce the amount of disk-space required to store the hash results. They also don’t require the exact password string to be known. If there is a match for the hash, it will be authenticated whether or not the matching string contains the password itself. This is why, from the defender’s perspective, it is important not only to hash passwords but to salt them.
In our blog post Would You Like Pepper on That Hash? we explored the concept of salts and peppers. In that piece, we break down the importance of storing hashed passwords so they cannot be easily cracked using a rainbow table attack, which makes use of a table of commonly-used hashes to crack passwords stored within a breached database. To prevent this, random strings of data, called “salts” are appended to passwords before they are hashed and stored in a database. In doing so, rainbow table attacks are rendered useless.
As such, rainbow table attacks can be prevented using salts, which ensure that every stored password has a unique generated hash. This way, rainbow table attacks (which operate upon the principle that two or more passwords can share the same hash value) can be effectively prevented.
Combolists and Combolist-as-a-Service (CaaS)
Combolists, a hot commodity within online cracking communities, are essentially email and password combinations (“combos”) that can be easily loaded into automated credential stuffing tools. The screenshot below shows advertisements for several combolists from various breached services within a clearnet online cracking community. Several popular services such as Spotify, Netflix, Amazon, Fortnite, Minecraft, Hulu and others are included here.
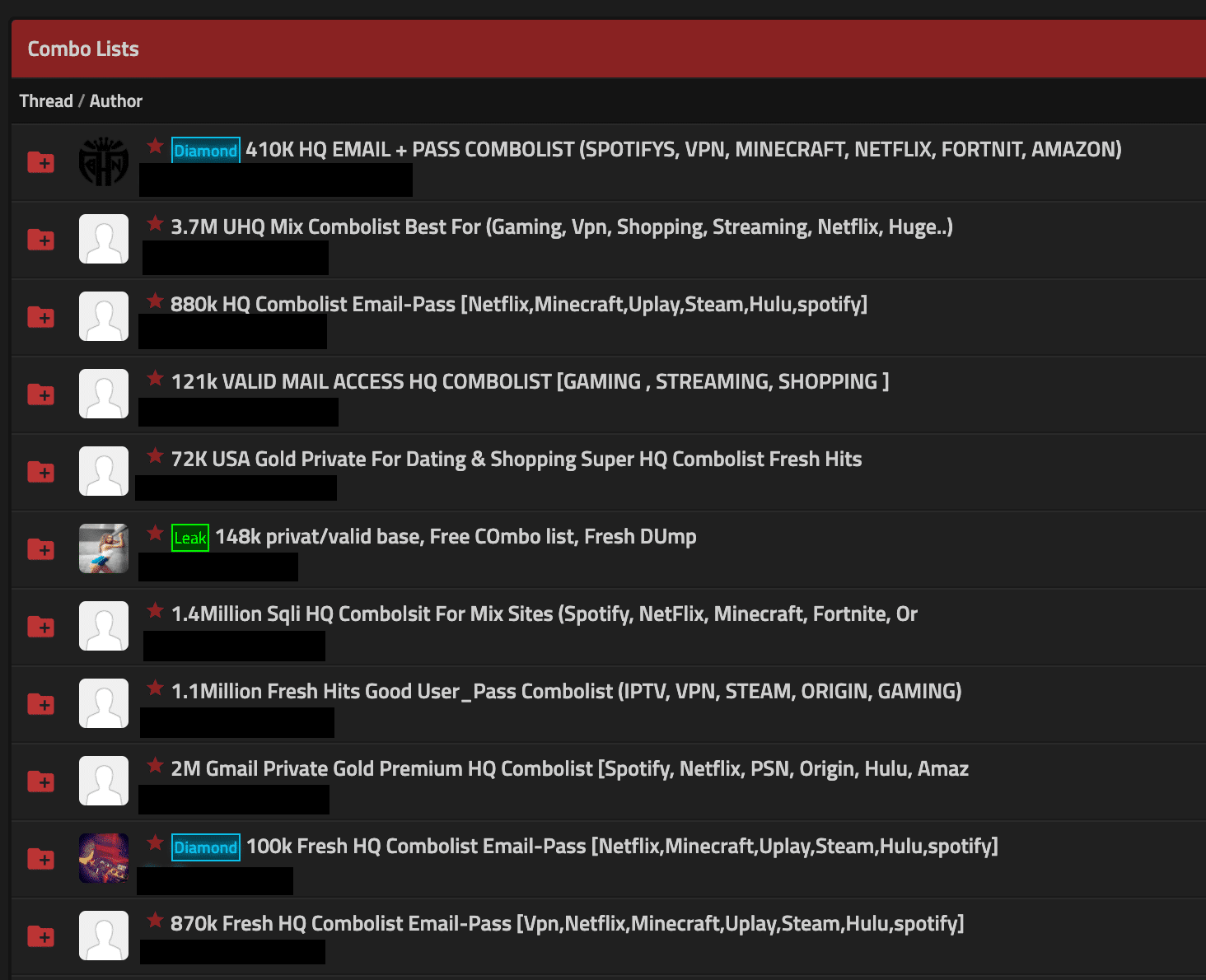
Figure 4: Screenshot of advertisements for combolists from an online cracking forum.
A member of an online cracking community described what a combolist is in a thread dedicated to explaining cracking topics to novices:

Figure 5: A member of an online cracking community explains the concept of combo lists to a novice.
We have covered credential stuffing tools, configuration files, and how credential stuffing tools utilize configuration files and combolists in many of our blog posts, such as The New Cracking Tools That Automate Credential Stuffing & Account Takeover and The Anatomy of Credential Stuffing.
New research of online cracking communities reveals that some threat actors are now profiting off combolists-as-a-service. Rather than selling combo lists directly, these criminals are developing automated cloud-based tools that can generate combo lists and databases automatically. And, rather than charging per combolist, the criminals hawking these tools advertise them on a subscription basis, charging clients a monthly subscription fee for a token which can be used to operate the tools – hence the cheeky shorthand CaaS.
Hash Type, Password Length, and Time to Crack
SpyCloud’s password cracking experiment tested four different hash types (MD5, MD5 salted, Vbulletin and BCrypt) against three levels of password complexity: easy, medium, and hard. The easy category included passwords like “qwerty” and “password” that are often included in rudimentary dictionaries. Passwords of “medium” complexity included at least eight characters as well as user-typical password improvements such as adding a special character or two, but are still easily remembered. This category included passwords such as “1qwertyuiop!” and “one1Juanwonder.” Lastly, our strongest passwords contained random letters, numbers and characters, and were at least 16 characters in length.
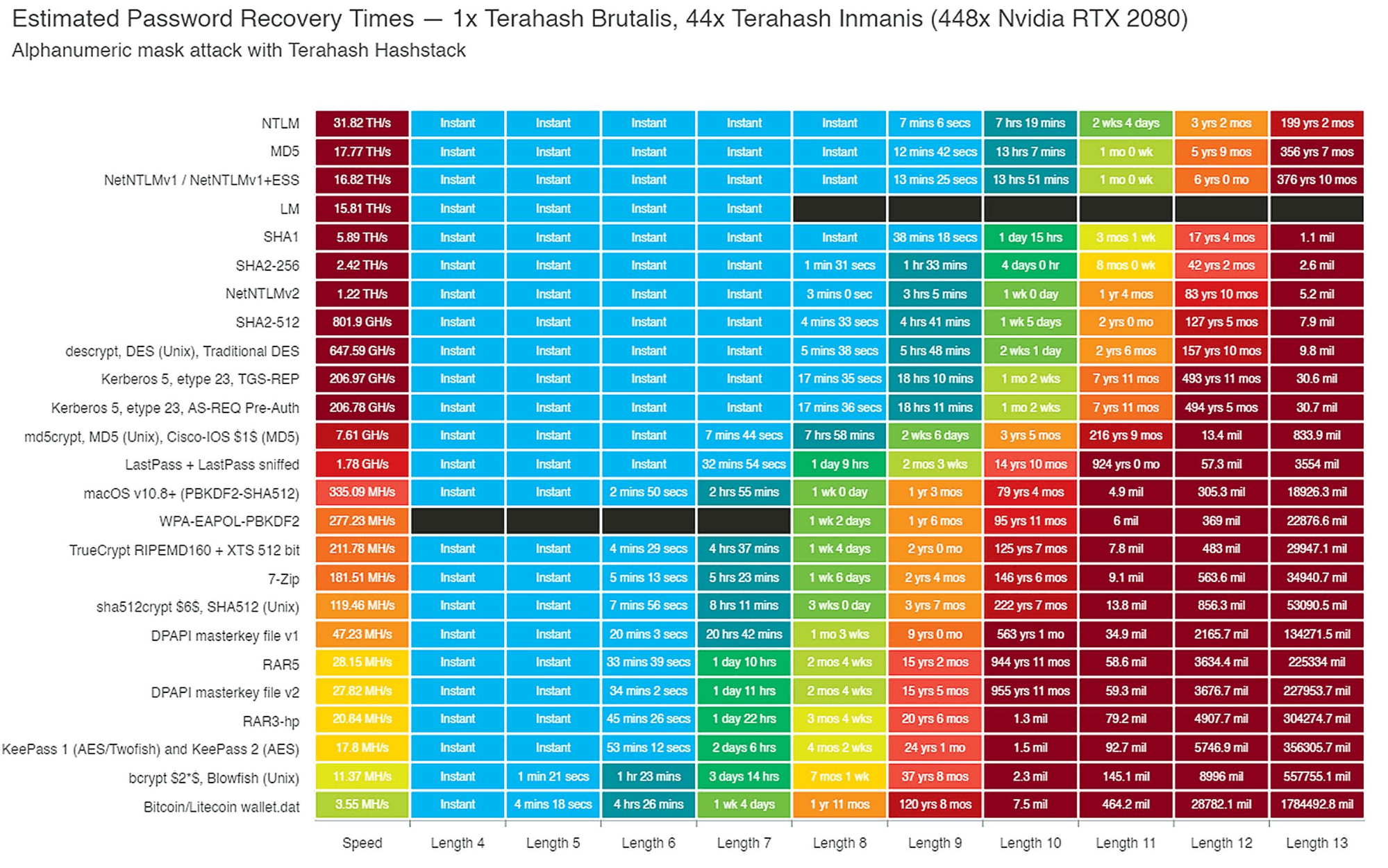
The results spoke for themselves. But what about a more granular analysis? An experiment done by Terahash, a manufacturer of purpose-built password cracking clusters such as the Brutalis password cracking appliance, shows that every character counts when it comes to password strength.
Ranging in character length from 4 to 13, the results of Terahash’s cracking experiment show that, regardless of hashing type, longer passwords are stronger passwords.
Terahash included 25 hash types in their experiment, ranging from the most rudimentary NTLM to bcrypt. All passwords with 13 characters took a substantial amount of time to crack. Even a 13-character password hashed with NTLM took over 199 years to crack, while a password of 4 characters was cracked instantly, even when hashed with Bcrypt.
Figure 6: Results from Terahash’s cracking experiment.
Unlike our analysis, the Terahash experiment did not consider password complexity factors other than length, but the results are still clear. Longer passwords are always better than shorter ones, and strong hashing alone cannot protect you from account takeover. Even a password of length five, when encrypted with KeePass, could be cracked in under an hour.
Current innovations on the underground are making it easier than ever for criminals to automate account takeover, but they don’t necessarily speed up the cracking process. Combolists-as-a-service improve criminal convenience, but not the strength of their password cracking capabilities.
Now as ever, the best defense is a password that is complex, long, and hard to guess. As SpyCloud’s own research has shown, we recommend strong passwords with random letters, numbers, characters, and at least 16 characters in length. Regardless of the hashing algorithm used, these passwords would require centuries to crack.