Dark web monitoring for consumers and enterprises
Experience the power of recaptured data + automated remediation for unrivaled protection from dark web threats

Visibility and action on exposures at scale, fueled by the world's largest collection of breach and malware data
Go beyond traditional dark web monitoring. Only SpyCloud illuminates the darkest corners of the criminal underground to deliver the earliest possible notification of exposed consumer and employee data, and offers easy integration into applications – as well as common security tools – for proactive response.
Early detection
Stop threats by accessing stolen dark web data months – and often years – before other providers even know it’s exposed
Actionable data
Benefit from true evidence of compromise, not false positives – so you deliver only the information that needs remediation urgently
Beyond alerts
Notify users of their dark web exposures and help them take action or deploy automated remediation, depending on your use case
Protect consumers from dark web identity exposures
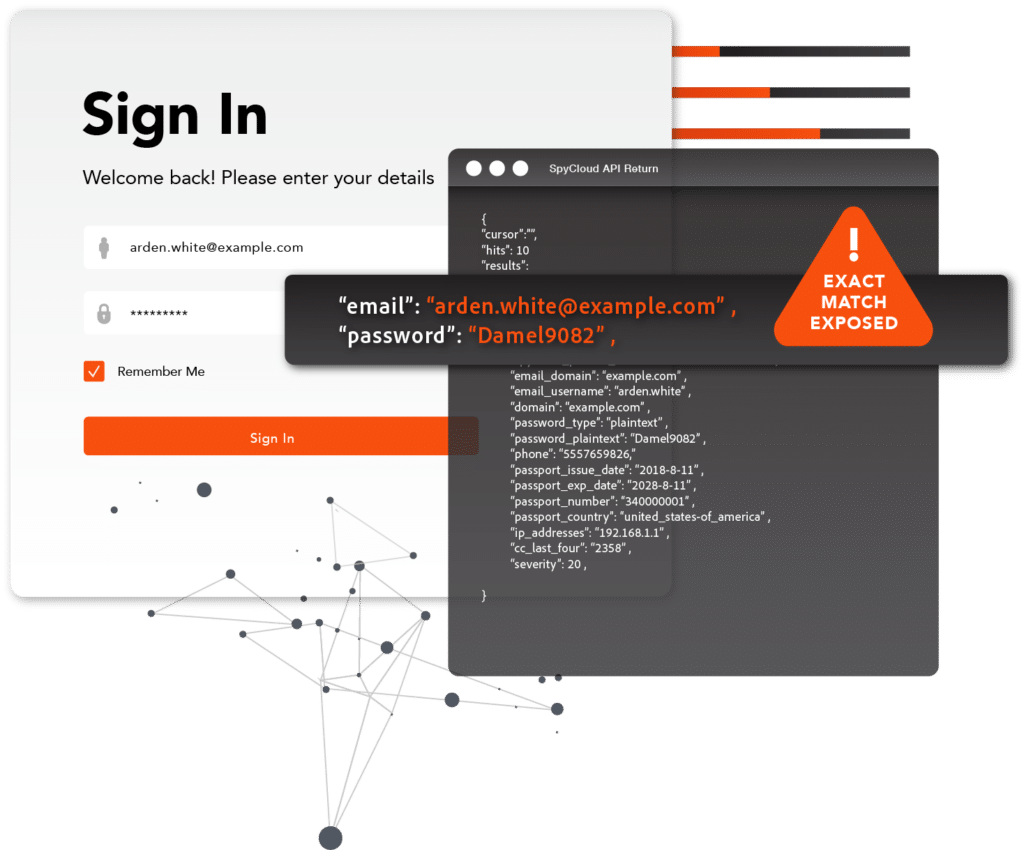
Whether you’re adding value to an existing product to drive revenue and customer loyalty or charged with proactively stopping account takeover in your application, SpyCloud is your expert partner to protect your consumers’ accounts, your bottom line, and the integrity of your brand.
Enjoy flexibility at every turn
Choose from multiple implementation options and require action on exposures according to your users' tolerance for friction. When using SpyCloud's recaptured data for consumer alerts, choose what data points to share for education and action.
Streamline the user experience
Check for exposed credentials or payment info seamlessly. Clear credit card data or require step-up authentication when exposures are detected, and accelerate revenue by moving low-risk users through your site without friction.
Mitigate the riskiest users
Block more fraud with SpyCloud's malware data. Flag consumers using infected devices whose plaintext credentials, authentication cookies, auto-fill data, and payment methods make them a priority target for cybercriminals.
Drive revenue from premium services
Optimize your consumer dark web monitoring product offering with premium alerts containing more detailed information and steps to take when identity data has been discovered online.
Remediate dark web exposures to protect your enterprise
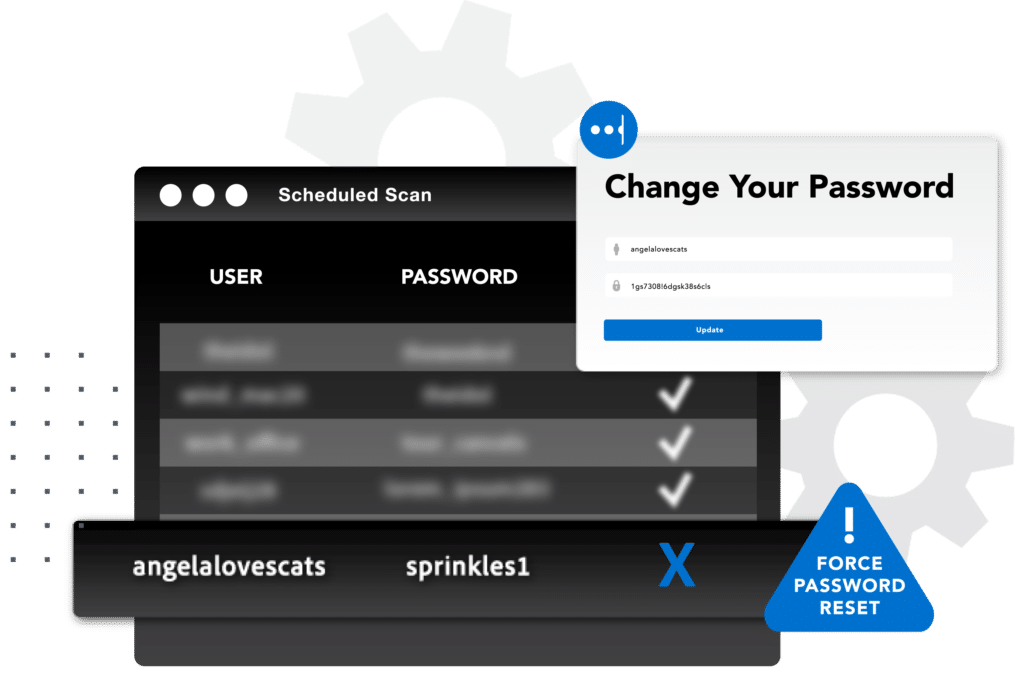
Focus on what makes your business tick, not dark web data collection, investigation and manual remediation. With SpyCloud, you’re alerted to compromised authentication data and it’s rectified without lifting a finger.
Resolve exposures instantly
Optimize account takeover prevention with automatic matching of employee and contractor credentials to data in the criminal underground. Resecure vulnerable accounts through Active Directory and SOAR integrations.
Reduce manual work
Spend time on greater-value activities and leave the heavy lifting to SpyCloud. We handle dark web data collection, curation, and analysis, enable password resets, and prove value with executive reporting.
Reduce the risk of targeted attacks
Negate entry points for ransomware by responding to stolen access for corporate credentials and authentication cookies for SSO, cloud applications and shadow IT.
Extend protection to vendors & VIPs
Protect vendors logging into corporate systems as well as the personal accounts of senior executives, board members, and employees with privileged access.
How It Works
SpyCloud’s Cybercrime Analytics Engine analyzes and ingests data from third-party breaches, malware-infected devices, and other underground sources well before they make their way to the “dark web.” By that point, it’s too late; months or years after the data is actually stolen and monetized by cybercriminals, it’s repackaged and sold to a broader audience on the dark web. This is when most dark web monitoring data providers pick up the data through automated scanning.
That’s not how SpyCloud operates.
Our security researchers gain access to the same data the fraudsters are using to target your business and your customers. Through our proprietary technology and tradecraft, we surface this “recaptured data” – including credentials, PII, credit card numbers, bank account info and more – before it is used to cause harm.
The earlier that breaches and malware-exfiltrated data are discovered, the faster you can mitigate the risk and prevent collateral damage to your employees and consumers – but it all depends on the quality and quantity of data you have at your fingertips
FOR SERVICE PROVIDERS
Consume SpyCloud’s data in your product or service to deliver alerts when users’ email and/or password become exposed, revealing details of the breach or malware infection and steps to remediate.
FOR
ENTERPRISES
Proactively monitor data from users on your domain and automatically remediate breached and malware-compromised passwords in Active Directory – including where Okta is the identity broker.
Explore SpyCloud
Enterprise Protection
Reduce your risk of ransomware and other critical attacks – acting on known points of compromise
Learn more
Consumer Risk Protection
Take a proactive approach to combating account takeover and stop high-risk attacks tied to malware
Learn more
Investigations
Efficiently piece together criminals’ digital breadcrumbs to reveal the identities of specific adversaries engaging in cybercrime
Learn more
Data Partnerships
Access comprehensive breach and malware data to add value to security and fraud detection products and services
Learn more
SecOps
Efficiently secure employee identities and safeguard corporate data and critical IP from cyberattacks.
Learn more
Threat intel teams
Investigate and stop threats with insights well beyond raw data and IOCs
Learn more
Cybercrime Analytics
Learn about the new way to disrupt cybercrime with automated analytics that drive action
Learn more
Test our data
We’re confident you’ll get more matches with SpyCloud – let’s do a match rate test
Learn more
Check your exposure
Uncover threats to your organization like malware-infected employees, stolen session cookies, and recency of breach exposures
See your results
SpyCloud Dark Web Monitoring FAQs
Our data is easily consumed by product teams through a high-volume API. We supply documentation and best practices so you can begin using it right away.
The speed of our collection efforts, accuracy and actionability of our data, and ease of use set us apart. SpyCloud boasts the largest database and the highest match rate of accounts being sold on underground markets, with data recaptured 9+ months ahead of other providers. And in a recent study of users after trialing a dark web and identity monitoring service built using SpyCloud’s data, 100% of users said they’d be willing to subscribe, 66% said they’d would leverage the service at least every 3 months, and 100% said they would recommend the service to friends or relatives. Just one example of the value we can deliver together.
We have built best practice email and app communications based on what prompts customers to reset passwords, without creating unnecessary fear. Check out our guide here. You can expect this type of guidance when you choose SpyCloud as your dark web data partner.
It may scare users – whether employees or consumers – to know that their device has been infected with malware and their identity data and credentials have been siphoned and shared on the dark web. Doing so is an urgent priority for enterprises, since these exposures open doors for ransowmare and other targeted attacks. For service providers, informing consumers requires a delicate hand. We provide best practices and communication templates for these scenarios. Check out one of our guides here for more information.
Cyber protection requires more than dark web monitoring – it requires action.
See the trends
Get insights from our 2024 Identity Exposure report, where we break down the data we recaptured last year.
Learn how we recapture data
Discover the difference our Cybercrime Analytics Engine makes.
