Last week, Cybernews reported a large data leak affecting MC2 Data, a company that offers background check services. SpyCloud Labs recaptured and analyzed the data, which fits into two main categories:
User account data from customers of MC2’s services including payment information and password hashes
Public records data – including detailed PII – on US persons who appear to have been looked up through one of MC2’s services
This blog provides a breakdown of the exposed data from the MC2 breach, as well as advice for those who may have been impacted.
Wait, didn’t this already happen? The MC2 breach vs. the NPD breach
In August, data from a different background check service, called National Public Data (NPD), was posted online. The NPD breach contained 2.7 billion exposed records including names, dates of birth, addresses, social security numbers, and phone numbers for hundreds of millions of US persons. This new MC2 data leak is different, but very similar to the NPD breach in that it is also a breach of a background check company that stores data on US persons.
How the two breaches are similar
Because we’re talking about breaches of background check companies, there is personally identifiable information (PII) in both of these breaches pertaining to individuals that never interacted with NPD or MC2, but whose data was stored by these companies in the service of supplying data for background checks and people lookups.
…and how they’re different
The MC2 leak contains fewer total records than the NPD breach, but those records – particularly the data on individuals investigated through the service – contain a significantly greater level of detail and variety of data asset types ranging from criminal history to domain registration history. Unlike the NPD data, the MC2 dataset also includes data on users of the MC2 service.
What’s in the MC2 breach?
Compromised user account data
As Cybernews reported, MC2 operates multiple background check and public records search services including: PrivateRecords.net, PrivateReports, PeopleSearcher, ThePeopleSearchers, and PeopleSearchUSA.
Images 1-3: Screenshots of the homepages from three of the background check and public records search websites operated by MC2.
These services are not advertised for enterprise use cases such as credit checks, but instead appear to be targeted towards consumers who want to find information about themselves or their acquaintances. Each of the websites also appears to have a disclaimer stating that they are not Fair Credit Reporting Act (FCRA) compliant, and as a result cannot legally be used for certain use cases including “consumer credit, employment, insurance, [and] tenant screening.”
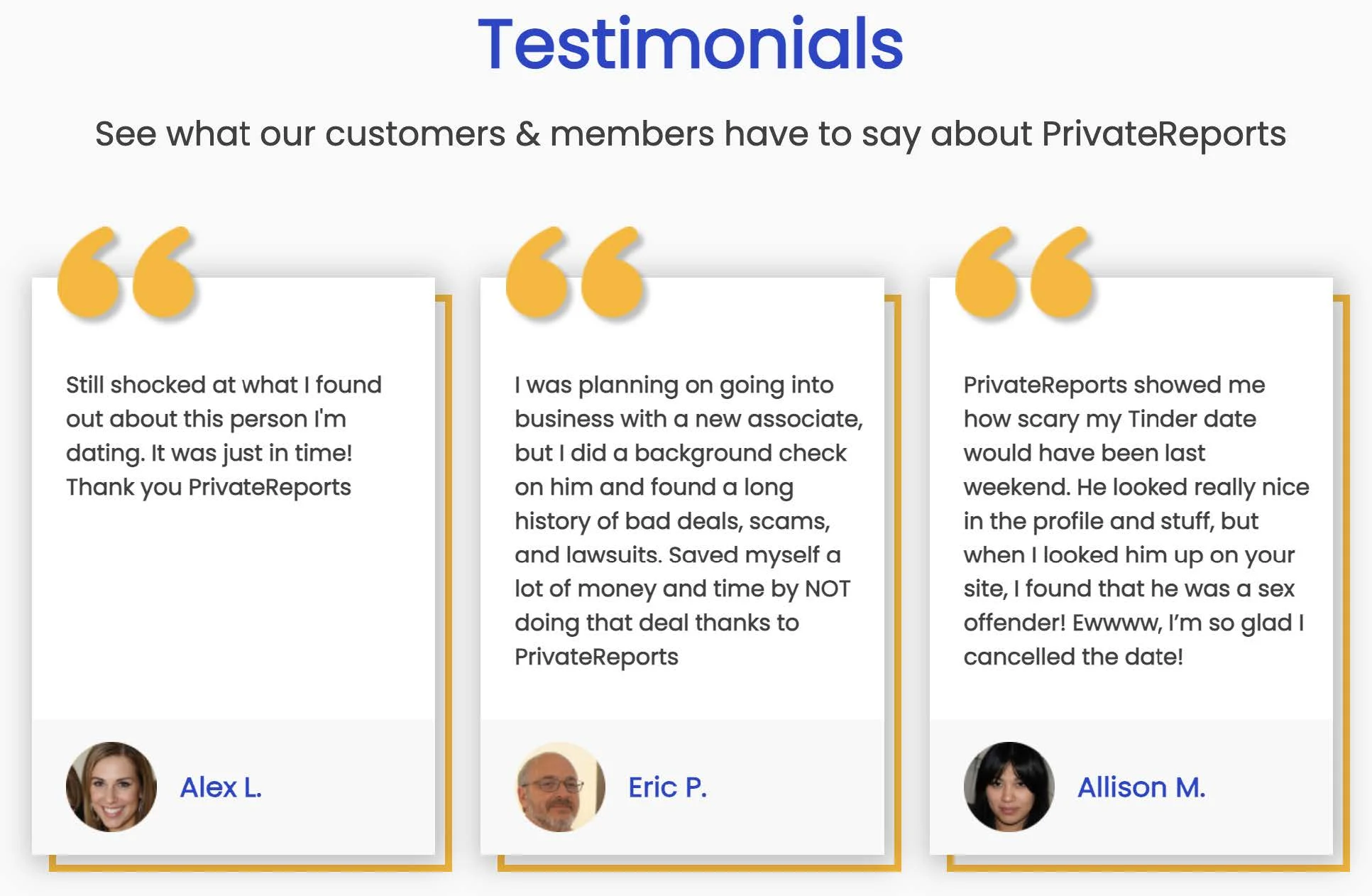
Image 4: Testimonials from the PrivateReports website showing consumer use cases such as looking up romantic interests.
The user account data in the leaked ‘users’ table appears to contain data on customers of MC2’s consumer background check services and people lookup services, including their:
- full name
- email address
- hashed password and password salt
- phone number
- IP address
- device and browser information
- payment information including partial credit card numbers
- account information such as account ID, account status, and which of MC2’s services they appear to have used
Compromised MC2 public records data
The leaked MC2 data also contains a table called ‘raws’ which appears to contain extensive data on individuals whose information was looked up using MC2’s services. It includes basic PII such as:
- full names and aliases
- email addresses
- phone numbers
- addresses
- dates of birth
- partial social security numbers
The data also includes extensive background information about individuals. On average, each record in the data table contains 27,728 lines of nested json. Each record contains the available data on an individual across a number of categories, including:
- eviction records
- foreclosure records
- bankruptcy records
- criminal history (including misdemeanors)
- death certificates
- marriage records
- divorce records
- property records (assessor information)
- business ownership records
- professional license records
- income and net worth records
- employment history
- domain registration records
- information on family members and known associates (including their names, email addresses, and phone numbers)
We also noticed that a lot of the data in each record is not necessarily about the individual being queried in the top level of each record. Instead, a large portion of the data appears to pertain to their known associates, neighbors, and family members whose PII – like phone numbers and email addresses – are also present.
Additionally, the matches appear fuzzy to accommodate individuals’ nicknames and aliases, so many records appear to actually contain data about multiple distinct individuals with similar names.
We also assess with high confidence that at least a portion of the data in this ‘raws’ table was obtained through the data intelligence provider Enformion using one of their APIs. Each record appears to include:
- a meta object that lists the data provider as “Enformion”
- an input object that appears to contain query search criteria for an individual US person such as first and last name and zip code, &
- an output object which contains the bulk of the data in the record.
The formatting and data in the input and output fields appear consistent with the API documentation for some of Enformion’s data lookup products. In particular, we found that the uniquely named keys “tahoeID” and “poseidonId” which appear in this data set are also present in the API documentation for both the Endato and Tracers data lookup products. Both Endato and Tracers are Enformion products, and they appear to offer multiple different search APIs under each of these brand names.
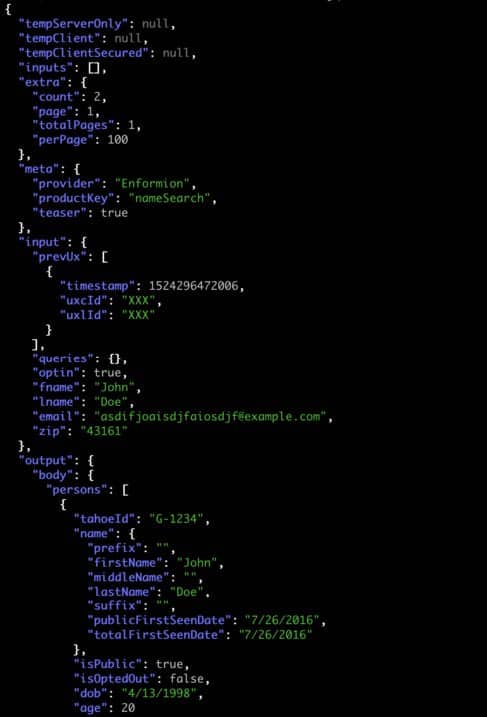
Image 5: Screenshot showing an example of the ‘meta’ and ‘input’ objects as well as a portion of the ‘output’ object from one of the records in the ‘raws’ table. We have replaced any potentially sensitive PII with dummy data.
Based on the formatting shown in image 5, we suspect that MC2 may have obtained the data in the input objects from data lookup requests that their customers made and at least some of the data in the output objects from querying Enformion’s API products. The results appear to include the results of various search queries. We hypothesize that MC2 makes multiple requests against various data search APIs for each person that plausibly matched the search term.
How to protect yourself following the MC2 breach
To find out if your email address appeared in either of the data sets in this breach, you can use SpyCloud’s free tool to check if your email was exposed.
If you have used one of MC2’s background check services and believe your user account data has been exposed, you can:
Change your passwords
Change your password for the service as well as any other accounts where you may have reused the same or a similar password.

Stay alert:
Watch out for emails, text messages, and phone calls that you receive at the phone number or email address you used to sign up for the MC2 service. In particular, be vigilant about scams which reference the data exposed in this leak, including your payment details.
Freeze your credit
If you’re not planning a big purchase in the near future, consider freezing your credit. Don’t pay a fee to a company to do this, it’s easy enough to do yourself and (for most people) can be done entirely online. Check out this guide from usa.gov.

Get a copy of your current credit report:
Obtain a free copy of your credit report as a baseline. Sign up for free weekly credit reports and make sure there isn’t anything new on it that you didn’t authorize

Stay alert:
Be extra cautious about emails, text messages, and phone calls you receive in the coming months. Scammers can use personal details like those in the MC2 and NPD breaches to craft more believable scams. If you have elderly parents or relatives, make sure you talk to them about the types of scams – like tech support and fake IRS audits – that are rampant these days, and ensure they never transfer money without verifying the claims with a trusted party. You can also set up transaction monitoring and threshold alerts to receive notifications about suspicious credit card and bank account activity.
How to protect your organization following the MC2 breach
Cybercriminals may attempt to leverage stolen data from this breach to target individuals in account takeover attacks, phishing campaigns, and other scams that could put your business at risk. You can use our free tool to check your domain’s exposure to this and other recent leaks, as well as your company’s personalized risk stemming from malware infections.



