What Is ATO and Why Should You Care?
Because of widespread password reuse, Account Takeover (ATO) attacks have become an extremely lucrative business for cybercriminals. Organized crime rings are performing ATO attacks on a massive scale by leveraging botnet-infected armies to attempt credential stuffing attacks against various web and mobile applications.
Cyber-criminals exploit compromised customer accounts for financial gain by pilfering financial or personally-identifiable information (PII) directly or by selling access to these accounts on underground markets. Once breached, these accounts can cause immeasurable damage and many are discovered only after the harm has been done.
Fortunately, there are steps and technologies companies can implement to protect themselves from ATO. What are the most common ATO attack vectors and best practices for mitigating them in your online application?
Account Takeover 101
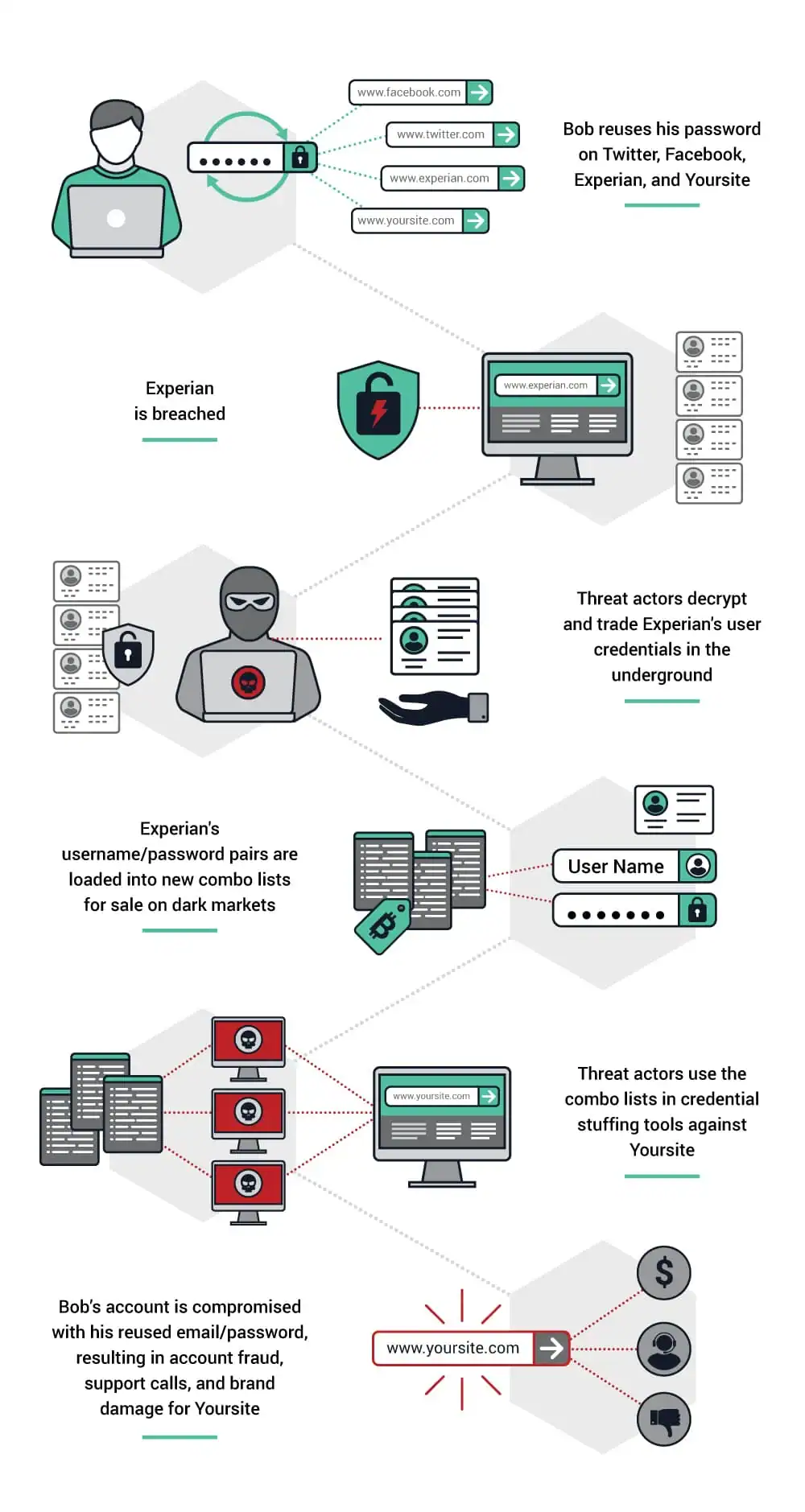
Credential Stuffing is a simple technique in which criminals load lists of stolen credentials from 3rd party sites into automated brute-forcing tools. The tools then test these stolen passwords against thousands of commercial web or mobile applications and sites.
Using stolen credentials to break into sites is not particularly new or sophisticated, but it works.
Because people often use the same usernames and passwords for multiple accounts and recycle them over and over again, it doesn’t take long for one breach to lead to many.
The hackers don’t stop there. They may eventually sell all of these stolen credentials to larger underground hacker communities, often months or even years later.
The following chart illustrates the chain of events that often leads to secondary mass-account compromises on a variety of other sites:
3 Steps to Protect your Users’ Accounts from ATO
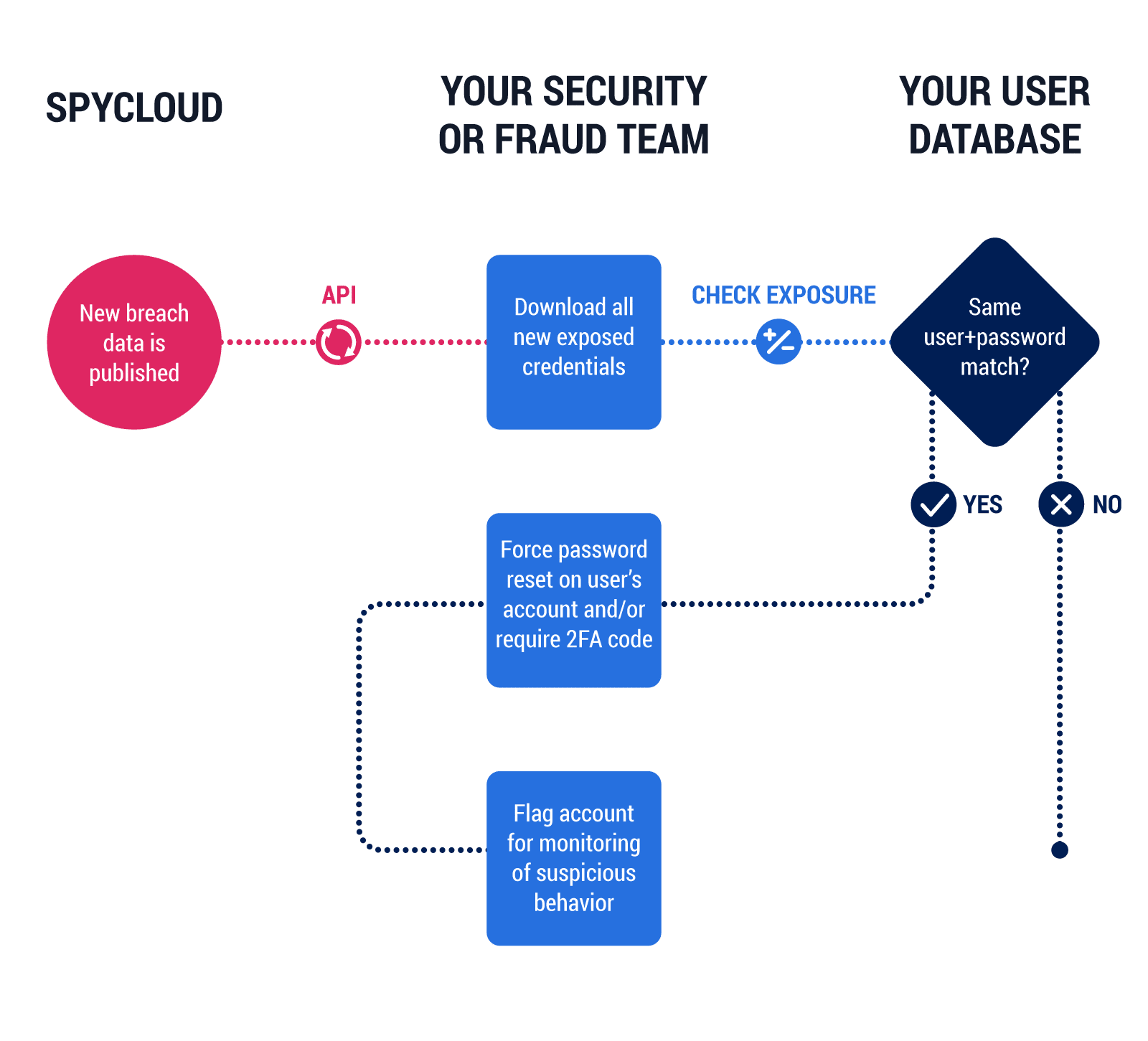
Best Practice 1 – Mitigate exposure of reused passwords from 3rd party breaches
For the company that suffers a data breach, the financial, reputational, and cleanup costs can be immense. However, the collateral damage that occurs to their users can be even worse.
A recent password-use study of roughly one billion leaked user accounts concluded that 20 percent of users were reusing passwords and 27 percent of users used a password that was nearly identical with other account passwords.
Because password reuse is so rampant across all industries, threat actors can usually expect a decent return on their investments when purchasing fresh credential dumps on the black market.
By implementing an automatic check against your application’s user accounts against known 3rd party database leaks, your organization can head off a large percentage of credential stuffing attacks at the pass.
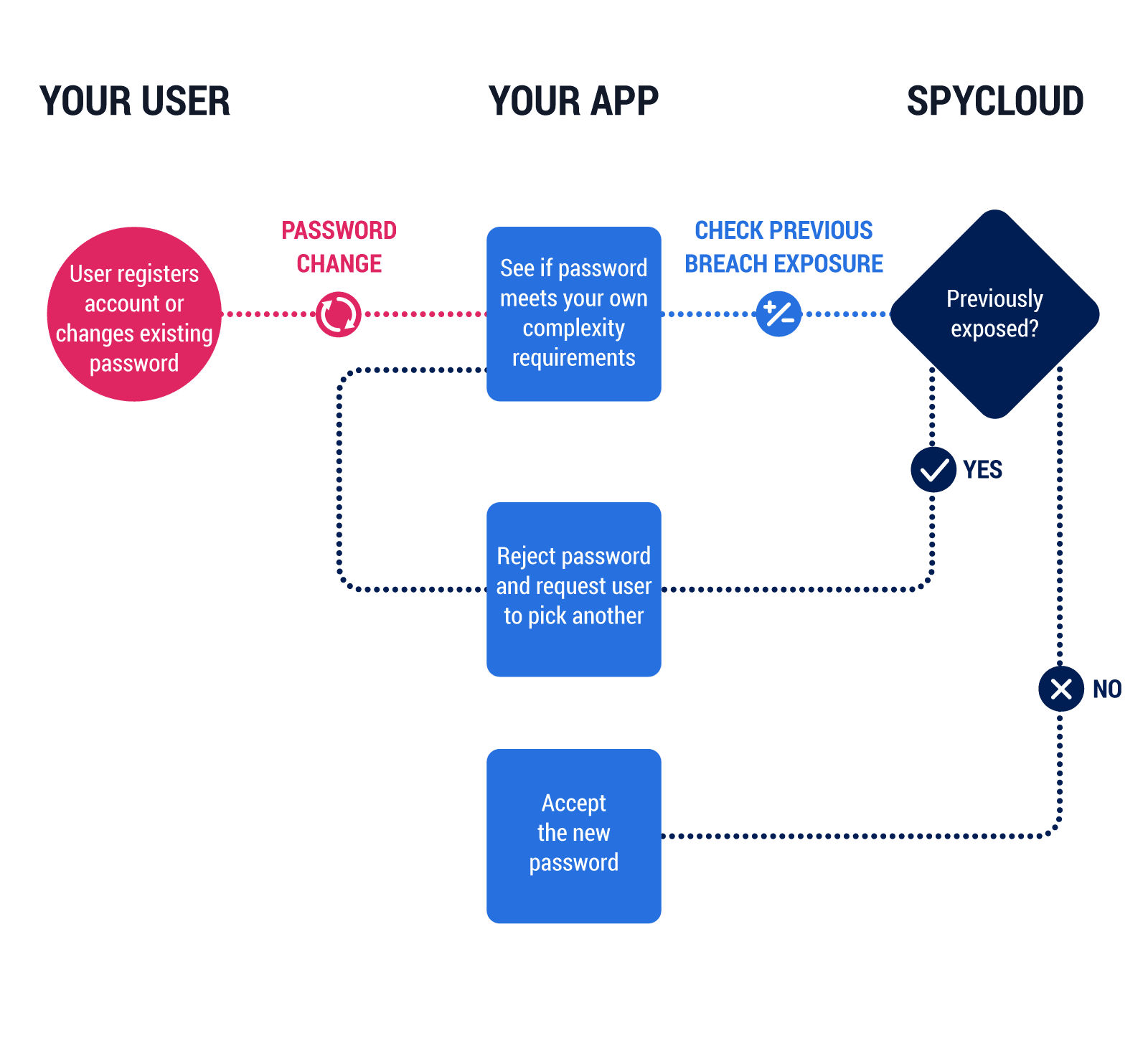
Best Practice 2 – Prevent users from picking unsafe passwords
Ensuring your users are picking healthy passwords that aren’t already exposed gives you a leg up on ATO. Employees need to be educated that while it may be convenient to choose easy or repeated passwords, it puts them and the company at a high risk for security breaches. Education, however, should not be the end of it. Companies can take preventative steps that make it impossible for employees to circumvent the recommendations.
We suggest implementing within your App the functionality to follow NIST’s new password guidelines. Preventing users from picking passwords known to be easily guessable can make a big difference in preventing ATO.
The system automatically checks each attempted password creation against previously exposed passwords. It also rejects passwords that are too simple. In both circumstances, the user is prevented from registering their account until they choose a healthier password.
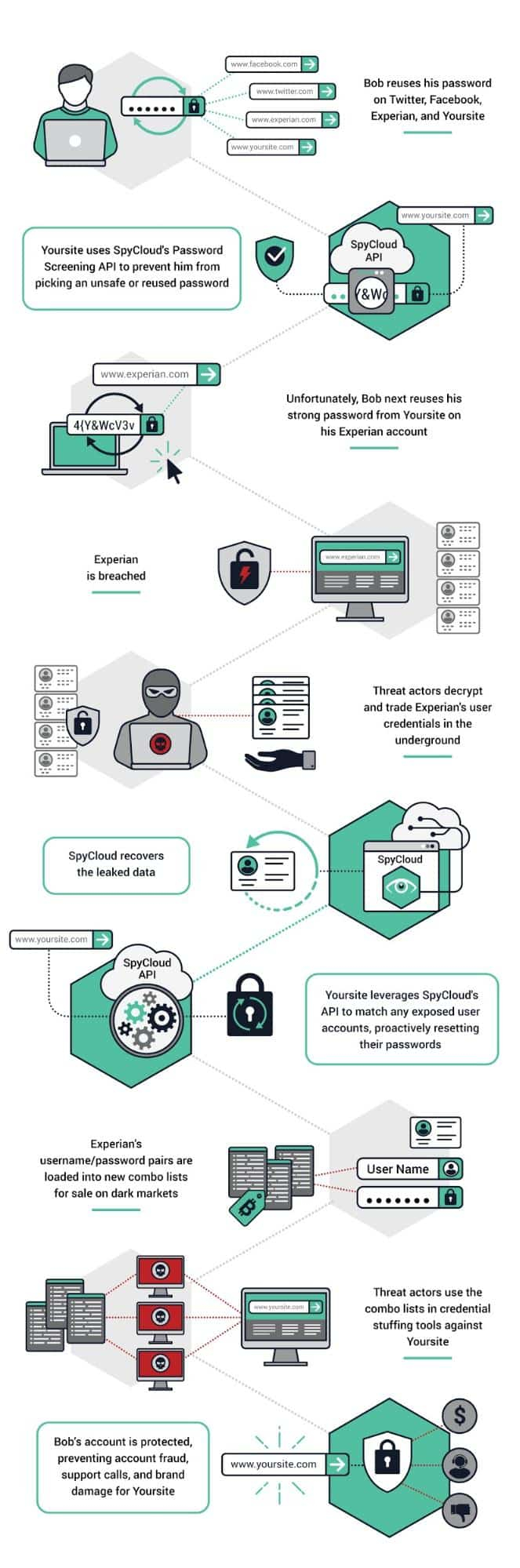
Best Practice 3 – Combine both approaches for a comprehensive ATO solution
Full ATO protection coverage requires both of the previous approaches incorporated into your existing security workflows. With SpyCloud, users are guided to choose the healthiest passwords, those that have not been previously used on other sites, those that have not already been compromised, and those that are not too basic or easy to hack. Until the user chooses a new, strong, uncompromised password, they are kicked back to the login registration screen of the app.
While users may find this protocol annoying or time-consuming, it ensures both the employee and company are safe, thereby preventing breaches to trickle down to customers. Again, it is important to educate employees as to why these measures are in place. Many simply do not understand the risk of weak passwords or password reuse. They aren’t aware that these two threats are the number one attack vector for bad actors.
Get Control of Passwords before the Criminals Do
Third-party breaches have impacted the most sophisticated users of top technology companies – all due to simple password reuse. Passwords are the easiest point of entry for criminals and they don’t take a technology genius to figure them out. Credential leaks will likely continue in frequency and volume, therefore, exacerbating the problem. Now is the time to protect your company, employees and customers. A “wait and see” perspective is dangerous and negligent, particularly since there are solutions like SpyCloud that immediately mitigate your risk.
By following the best practices above and implementing the right technology, companies are proving to their shareholders and stakeholders that they take data privacy and personal identities seriously. Beyond building respect, the initiative also wards off the threats that can cause immense financial and reputational damage.
The objective is to always stay one step ahead of the criminals. Taking a proactive stance against ATO is not only smart, it is vital to the health of the business.
